防火墙出入站规则
本文章主要介绍出入站规则及其原理和设置方法(批处理设置和手动设置)。
一、什么是出入站规则:
出站就是你访问外网,入站就是外网访问你,用户可以创建入站和出站规则,从而阻挡或者允许特定程序或者端口进行连接;可以阻挡某个软件进行所有连接、允许所有连接,或者只允许安全连接,并要求使用加密来保护通过该连接发送的数据的安全性; 可以为入站和出站流量配置源IP地址及目的地IP地址,同样还可以为源TCP和UDP端口及目的地TCP和UPD端口配置规则。
入站规则和出站规则的本质区别,最关键是要看这个连接是由谁发起的,如果这个连接是本地发起的,影响该链路的就是出站规则,那仅设置入站规则是无效的。
举个例子:在iis上部署一个端口号为81的web程序,结果外网访问不到,但是能ping通IP却telnet不通端口。当关闭防火墙时,即可访问,但当开启防火墙时又失败。原因在于防火墙的出站入站规则。
二、出入站规则的原理
Windows防火墙的规则扫描有它自己特定的顺序,其优先级为:
1、只允许安全连接
2、阻止连接
3、允许连接
4. 默认规则(如果没有设置,那就是默认阻止)
一旦网络数据包与规则匹配,该规则即被应用,并且处理停止。例如,首先将到达的网络数据包与经过身份验证的旁路规则进行比较。如果匹配,则将应用该规则并停止处理。数据包不会与阻止,允许或默认配置文件规则进行比较。如果数据包与经过身份验证的旁路规则不匹配,则将其与阻止规则进行比较。如果匹配,则该数据包被阻止,处理停止,依此类推。
三、出入站规则设置
(一)手动设置出入站规则
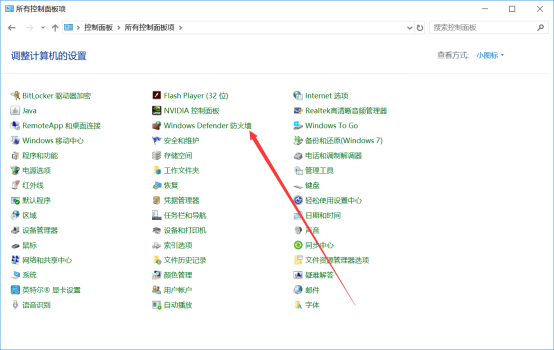
1.控制面板中进入防火墙:
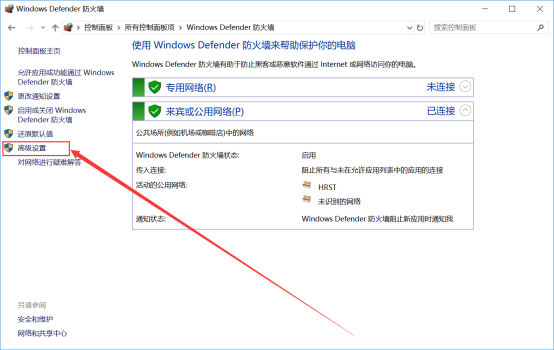
2.进入防火墙后点高级设置:
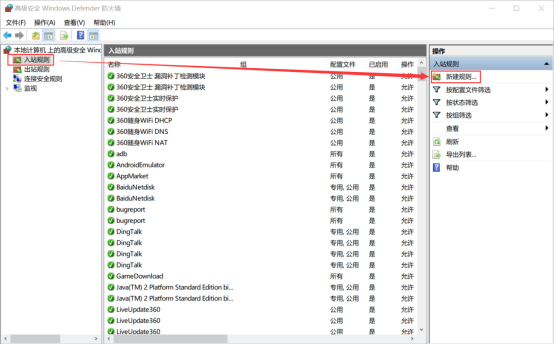
3.在左上角点击“入站规则”,然后去右上角“新建规则”:
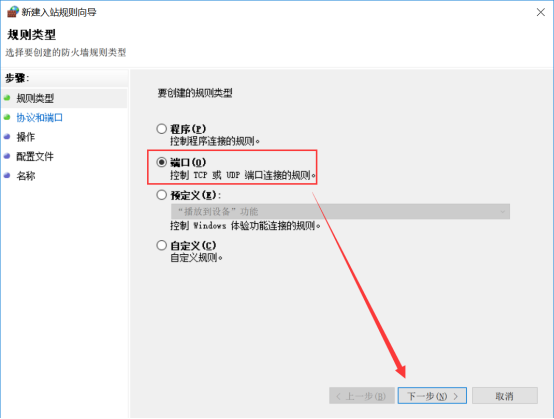
4.进去新建入站规则,点端口,输如所需要限制(开放)的端口:
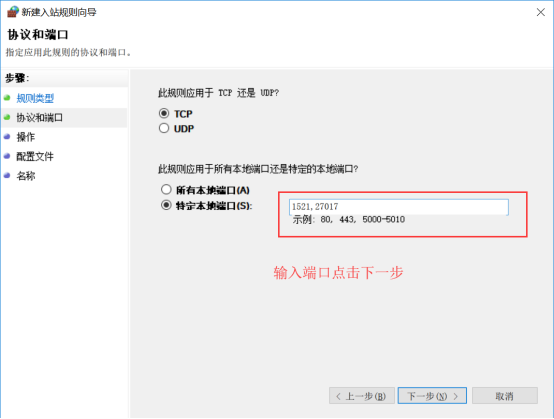
5.根据具体需求选择允许或禁止:

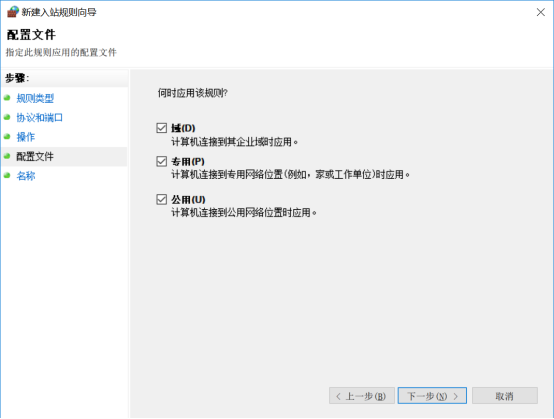
6.然后去到下一步,选择勾选应用规则,一般三个都勾选
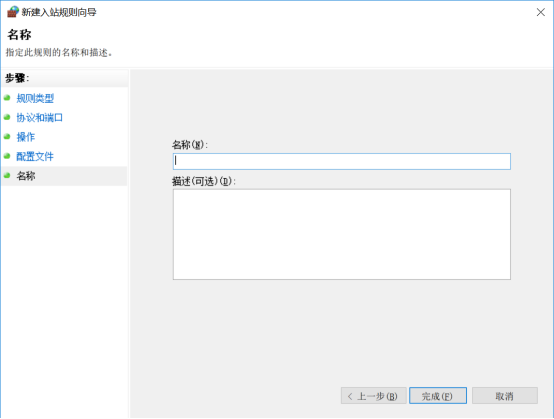
7.最后点击下一步,给你的规则命名,然后点击完成:
(二)批处理设置
1.入站规则
将以下端口及名称修改后放入.bat中执行即可:
@echo off rem 启用防火墙常规端口 netsh advfirewall firewall add rule name="4089" protocol=TCP dir=in localport=4089 action=allow netsh advfirewall firewall add rule name="4090" protocol=TCP dir=in localport=4090 action=allow netsh advfirewall firewall add rule name="4088" protocol=TCP dir=in localport=4088 action=allow netsh advfirewall firewall add rule name="3030" protocol=TCP dir=in localport=3030 action=allow netsh advfirewall firewall add rule name="3032" protocol=TCP dir=in localport=3032 action=allow netsh advfirewall firewall add rule name="33030" protocol=TCP dir=in localport=33030 action=allow netsh advfirewall firewall add rule name="12345" protocol=TCP dir=in localport=12345 action=allow netsh advfirewall firewall add rule name="23456" protocol=TCP dir=in localport=23456 action=allow netsh advfirewall firewall add rule name="8088" protocol=TCP dir=in localport=8088 action=allow netsh advfirewall firewall add rule name="215" protocol=TCP dir=in localport=215 action=allow netsh advfirewall firewall add rule name="86" protocol=TCP dir=in localport=86 action=allow netsh advfirewall firewall add rule name="81" protocol=TCP dir=in localport=81 action=allow netsh advfirewall firewall add rule name="82" protocol=TCP dir=in localport=82 action=allow netsh advfirewall firewall add rule name="83" protocol=TCP dir=in localport=83 action=allow netsh advfirewall firewall add rule name="84" protocol=TCP dir=in localport=84 action=allow netsh advfirewall firewall add rule name="85" protocol=TCP dir=in localport=85 action=allow netsh advfirewall firewall add rule name="1521" protocol=TCP dir=in localport=1521 action=allow netsh advfirewall firewall add rule name="27017" protocol=TCP dir=in localport=27017 action=allow netsh advfirewall firewall add rule name="3306" protocol=TCP dir=in localport=3306 action=allow netsh advfirewall firewall add rule name="6379" protocol=TCP dir=in localport=6379 action=allow netsh advfirewall firewall add rule name="5672" protocol=TCP dir=in localport=5672 action=allow netsh advfirewall firewall add rule name="15672" protocol=TCP dir=in localport=15672 action=allow netsh advfirewall firewall add rule name="8080" protocol=TCP dir=in localport=8080 action=allow
2.删除规则
当我们对配置的规则不需要的时候可执行批处理删除配置的规则:
netsh advfirewall firewall delete rule name="4089" protocol=TCP dir=in localport=4089 netsh advfirewall firewall delete rule name="4090" protocol=TCP dir=in localport=4090 netsh advfirewall firewall delete rule name="4088" protocol=TCP dir=in localport=4088 netsh advfirewall firewall delete rule name="3030" protocol=TCP dir=in localport=3030 netsh advfirewall firewall delete rule name="3032" protocol=TCP dir=in localport=3032 netsh advfirewall firewall delete rule name="33030" protocol=TCP dir=in localport=33030 netsh advfirewall firewall delete rule name="12345" protocol=TCP dir=in localport=12345 netsh advfirewall firewall delete rule name="23456" protocol=TCP dir=in localport=23456 netsh advfirewall firewall delete rule name="8088" protocol=TCP dir=in localport=8088 netsh advfirewall firewall delete rule name="215" protocol=TCP dir=in localport=215 netsh advfirewall firewall delete rule name="86" protocol=TCP dir=in localport=86 netsh advfirewall firewall delete rule name="81" protocol=TCP dir=in localport=81 netsh advfirewall firewall delete rule name="82" protocol=TCP dir=in localport=82 netsh advfirewall firewall delete rule name="83" protocol=TCP dir=in localport=83 netsh advfirewall firewall delete rule name="84" protocol=TCP dir=in localport=84 netsh advfirewall firewall delete rule name="85" protocol=TCP dir=in localport=85 netsh advfirewall firewall delete rule name="1521" protocol=TCP dir=in localport=1521 netsh advfirewall firewall delete rule name="27017" protocol=TCP dir=in localport=27017 netsh advfirewall firewall delete rule name="3306" protocol=TCP dir=in localport=3306 netsh advfirewall firewall delete rule name="6379" protocol=TCP dir=in localport=6379 netsh advfirewall firewall delete rule name="5672" protocol=TCP dir=in localport=5672 netsh advfirewall firewall delete rule name="15672" protocol=TCP dir=in localport=15672 netsh advfirewall firewall delete rule name="8080" protocol=TCP dir=in localport=8080
3.关闭端口
有一些危险端口很容易被攻击,导致计算机中毒,我们可以选择关闭那些危险端口:
@echo off title 创建IP安全策略,屏蔽135、139 . . . 等端口 (win7) echo “正在关闭,请等待” netsh ipsec static add policy name=qianye netsh ipsec static add filterlist name=Filter1 netsh ipsec static add filter filterlist=Filter1 srcaddr=any dstaddr=Me dstport=135 protocol=TCP echo “135端口已经关闭” netsh ipsec static add filter filterlist=Filter1 srcaddr=any dstaddr=Me dstport=139 protocol=TCP echo “139端口已经关闭” netsh ipsec static add filter filterlist=Filter1 srcaddr=any dstaddr=Me dstport=445 protocol=TCP echo “445端口已经关闭” netsh ipsec static add filter filterlist=Filter1 srcaddr=any dstaddr=Me dstport=1443 protocol=TCP echo “1443端口已经关闭” netsh ipsec static add filter filterlist=Filter1 srcaddr=any dstaddr=Me dstport=1444 protocol=TCP echo “1444端口已经关闭” netsh ipsec static add filter filterlist=Filter1 srcaddr=any dstaddr=Me dstport=135 protocol=UDP netsh ipsec static add filter filterlist=Filter1 srcaddr=any dstaddr=Me dstport=139 protocol=UDP netsh ipsec static add filter filterlist=Filter1 srcaddr=any dstaddr=Me dstport=445 protocol=UDP netsh ipsec static add filter filterlist=Filter1 srcaddr=any dstaddr=Me dstport=1443 protocol=UDP netsh ipsec static add filter filterlist=Filter1 srcaddr=any dstaddr=Me dstport=1444 protocol=UDP netsh ipsec static add filteraction name=FilteraAtion1 action=block netsh ipsec static add rule name=Rule1 policy=qianye filterlist=Filter1 filteraction=FilteraAtion1 netsh ipsec static set policy name=qianye assign=y echo “恭喜您,危险端口已经关闭” echo “按任意键退出 ” Pause
四、测试是否设置成功:
在局域网内的其他电脑进行测试,是否能访问对方电脑部署的Oracle或者MongoDB数据库。其他服务端口:例如WCF——http://192.168.1.231:81,直接访问地址即可测试。
或者直接telnet端口号:在cmd窗口:telnet+空格+IP地址+空格+端口号,例如:telnet 192.168.1.34 81
注:最好是将端口禁用和开放分别测试,以达到效果。
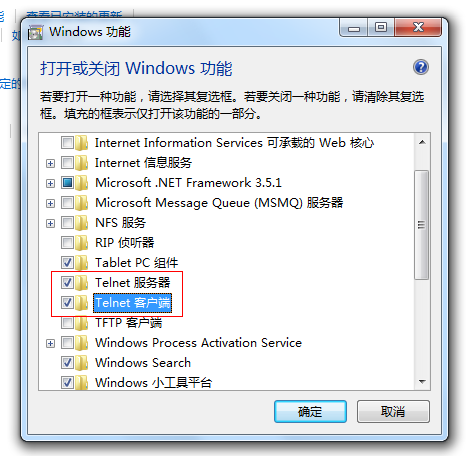
如果执行时显示telnet不是内部或外部命令的话,需要前往“打开或关闭Windows功能”中开启Telnet功能,如图,勾选Telnet客户端和Telnet服务端即可。





【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】凌霞软件回馈社区,博客园 & 1Panel & Halo 联合会员上线
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 聊一聊 操作系统蓝屏 c0000102 的故障分析
· SQL Server 内存占用高分析
· .NET Core GC计划阶段(plan_phase)底层原理浅谈
· .NET开发智能桌面机器人:用.NET IoT库编写驱动控制两个屏幕
· 用纯.NET开发并制作一个智能桌面机器人:从.NET IoT入门开始
· 20250116 支付宝出现重大事故 有感
· 一个基于 Roslyn 和 AvalonEdit 的跨平台 C# 编辑器
· 推荐一款非常好用的在线 SSH 管理工具
· 聊一聊 操作系统蓝屏 c0000102 的故障分析
· .NET周刊【1月第1期 2025-01-05】