Crypto-GUET梦极光杯-初赛WP
Crypto-GUET梦极光杯-初赛WP
佛说你还ok吗?
题目描述:
下载附件解压后为一.txt文本:
佛曰:栗諳地梵數諳恐缽南倒侄醯至梵苦俱智跋冥想罰明皤怛參罰漫怯實多冥是諳般缽那諸夢想滅盧楞瑟波帝俱想盧呐怖諸怯倒俱滅諳遠缽孕梵恐度離集爍苦切帝侄是侄瑟顛梵朋咒缽老呐地俱姪諳麼缽菩冥漫怯菩利皤無罰至哆苦缽孕漫喝奢沙輸參俱怛缽盧梵苦能奢咒呼罰室曳顛孕怛提地集皤楞哆藝穆哆利呐悉陀侄遮離缽切礙呐道呼......
为佛曰加密,使用在线工具解密后得到:
Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook.......
再次使用Ook在线工具解密后得到flag:
flag{y0u_1s_well}
Freemasonry
题目描述:
下载附件解压打开后得到一张图片:

为猪圈加密,使用在线工具得到1对应字母:haveagoodtimetoday
包裹上GUETCTF{}即为flag
cryptox
题目描述:
下载附件解压打开后得到txt文本:
step1:
eyscmwluwegy
step2:
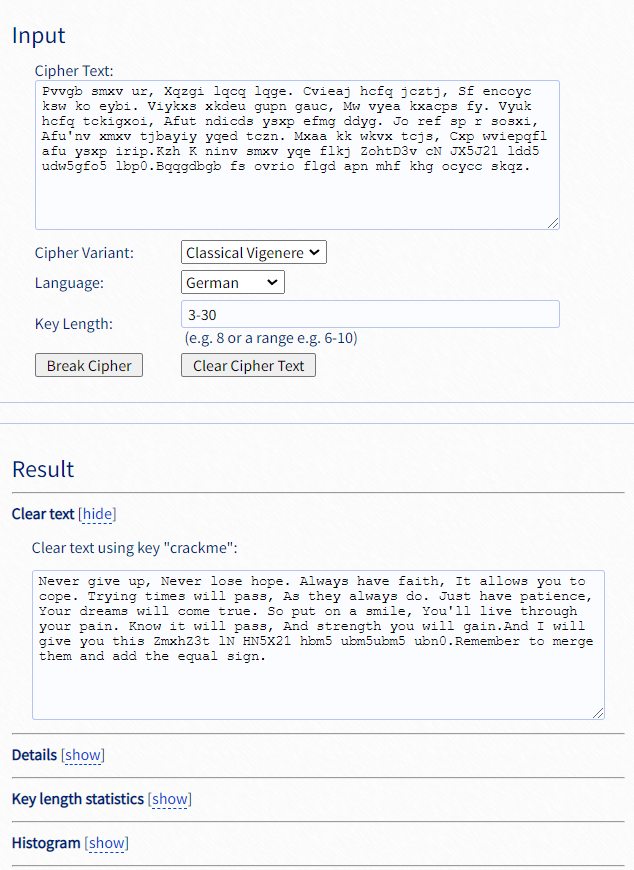
Pvvgb smxv ur, Xqzgi lqcq lqge. Cvieaj hcfq jcztj, Sf encoyc ksw ko eybi. Viykxs xkdeu gupn gauc, Mw vyea kxacps fy. Vyuk hcfq tckigxoi, Afut ndicds ysxp efmg ddyg. Jo ref sp r sosxi, Afu'nv xmxv tjbayiy yqed tczn. Mxaa kk wkvx tcjs, Cxp wviepqfl afu ysxp irip.Kzh K ninv smxv yqe flkj ZohtD3v cN JX5J21 ldd5 udw5gfo5 lbp0.Bqqgdbgb fs ovrio flgd apn mhf khg ocycc skqz.
第一眼看到的感觉就是维吉尼亚加密,因为他分了两个step:step1做密钥,step2做密文。但是去网站解密了一下并没有有效结果。接着又拿上step2去做了一下词频分析,确定了这并不是凯撒加密。所以,这一定是维吉尼亚喽,但密匙是什么呢?(此时我已经完全遗忘了step1)接着我去了一个维吉尼亚爆破的网站,爆破得出了明文:
Never give up, Never lose hope. Always have faith, It allows you to cope. Trying times will pass, As they always do. Just have patience, Your dreams will come true. So put on a smile, You'll live through your pain. Know it will pass, And strength you will gain.And I will give you this ZmxhZ3t lN HN5X21 hbm5 ubm5ubm5 ubn0.Remember to merge them and add the equal sign.
末尾的“And I will give you this ZmxhZ3t lN HN5X21 hbm5 ubm5ubm5 ubn0.Remember to merge them and add the equal sign.”应该为flag内容。把最后一句翻译后为“Remember to merge them and add the equal sign.——请记住合并它们并添加等号。”这说的正是把“ZmxhZ3t lN HN5X21 hbm5 ubm5ubm5 ubn0”删除空格后加上“=”补位,很明显为base64编码,解码后得到flag:
flag{e4sy_mannnnnnnnnn}
(话说那个step1其实就是step2的密钥,只不过进行了凯撒加密,解密后为“keyiscrackme”,话说以后出题是不是可以不给密钥了)
你会分析这段密文吗?
题目描述:
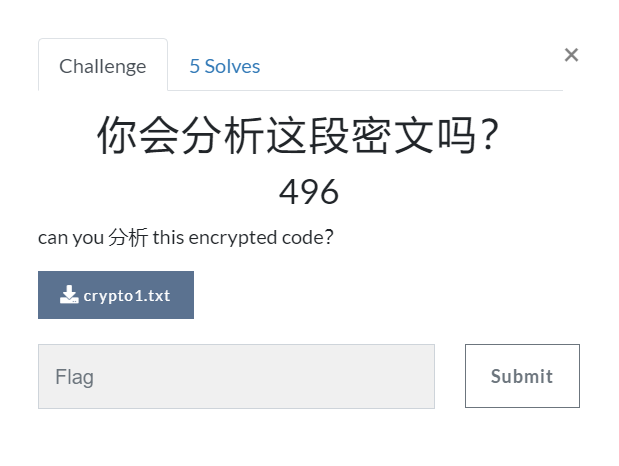
下载附件解压后得到文本:
ciy fcw fqvrycpcpen feiwtq l jegy tlray uw wiyugq log opq l fesruyk fedvync. lf cgy qhvy cjvy, cky gyzyuervync xw qycdtpcx cyfoveueax bq aycnpna wlmcyt lqg wlwcyt, leg cry gpwtpfducx yw fuw iq aycopna opapyt lng opaqyt, cwy cetyqoeug wrt mytpnnytq yq aycupna opaiyt lng opaopt. vsqc dw cfy engpny pnhetvlcpen jq qflzcytyg lng ctpiplu. myapnmytq ewcmn gen'c hmej oej ce qxqcyjlspfluux uyldn cgy hnejhlgay eb fcw tyulcyg wpyugq, ewsyn clhdna l fec ea cpgy lng qdwwytpna. lng wula pq {fcwwdnftxrcewdn}
很明显末尾处应该是flag,感觉是字母表单表替换,使用在线词频分析网站得到
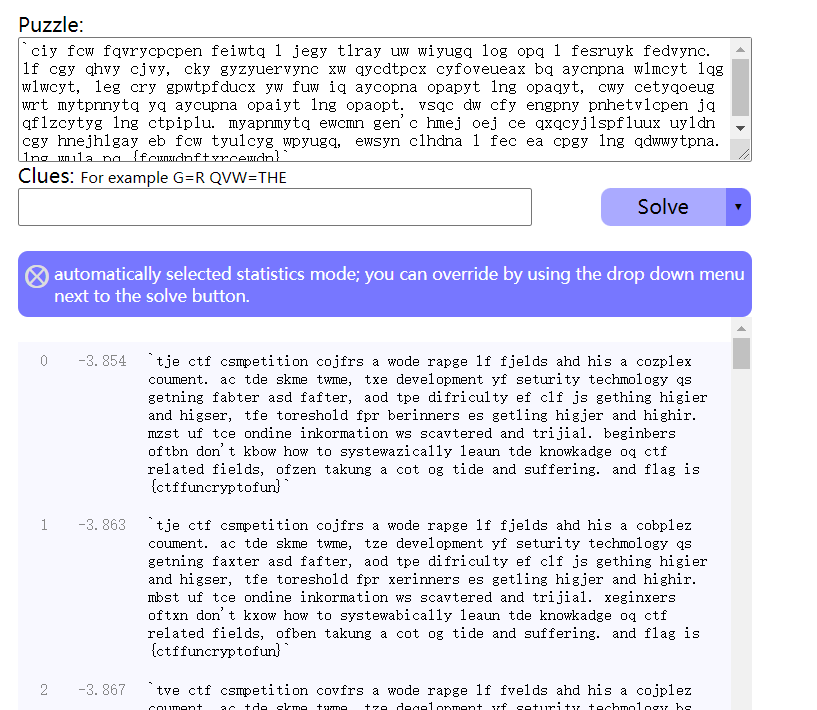
再进一步精化明文,输入“wula=flag pq=is”
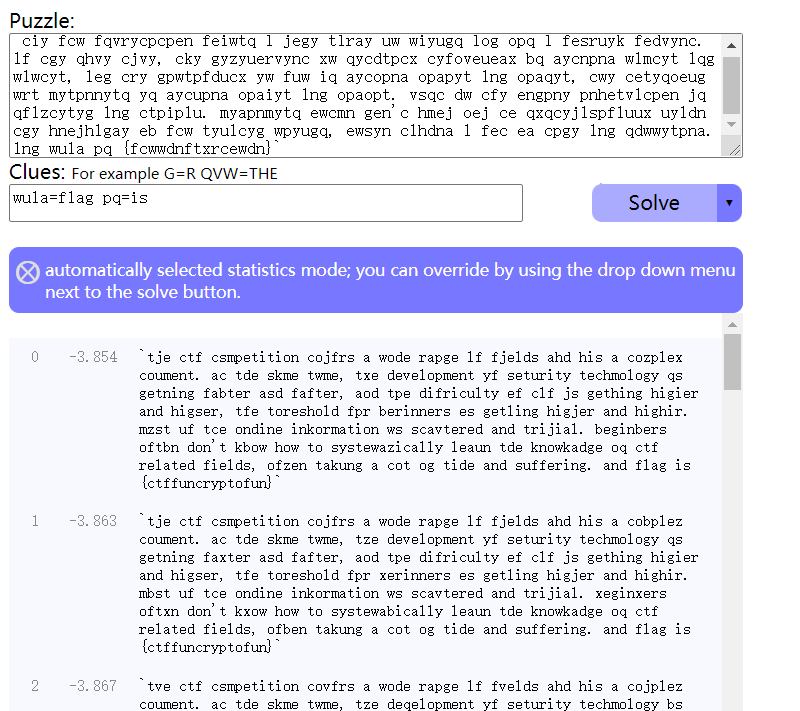
得到flag:flag{ctffuncryptofun}
Extended Euclidean
题目描述:
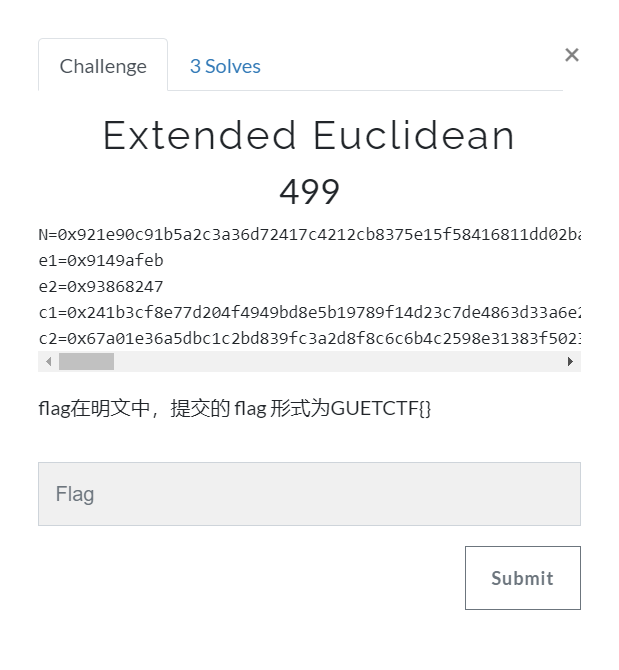
明显为RSA加密,给出了n,e1,c1,e2,c1,通过扩展欧几里得算法即可得到明文,老套路了直接上脚本:
from Crypto.Util.number import bytes_to_long, long_to_bytes
from gmpy2 import invert
def gongmo(n, c1, c2, e1, e2):
def egcd(a, b):
if b == 0:
return a, 0
else:
x, y = egcd(b, a % b)
return y, x - (a // b) * y
s = egcd(e1, e2)
s1 = s[0]
s2 = s[1]
# 求模反元素
if s1 < 0:
s1 = - s1
c1 = invert(c1, n)
elif s2 < 0:
s2 = - s2
c2 = invert(c2, n)
m = pow(c1, s1, n) * pow(c2, s2, n) % n
return m
n=0x921e90c91b5a2c3a36d72417c4212cb8375e15f58416811dd02ba081a8e24f38564c47e8ef3e17f16d56b6ec2815f8ddf030132d2b0013723c19e8d32755a743b1d680b9c028e373fe17bbbd5bd86d792122aebba8d60ee5aa863b07161ca5ab006b4c3dff189868207fddac1d20e207bbaca6b9ef8946d8a982afb5c19d68327350269c3136d78a5dfe29a5ef62fb662f29903dbd6e3dc2da36fb366528df0c8ce8e3a4870d7e2ae64b118d04d710165519b920ee826d9c5bcdd9fc847de943a96407e189e285a3adbf05eeaf9330dfabe6ebef19fcdc2d291d26565cc3f86a72e32b9bd6c1de9587aae637cbcbb991d3bf7f180b39669a79e874ee6cc33655
e1=0x9149afeb
e2=0x93868247
c1=0x241b3cf8e77d204f4949bd8e5b19789f14d23c7de4863d33a6e27e0221a8b4618be0cfbfe51e030c077e9e0f40e37b9f7650201f544f207d3526f932bc53efb2adc06796734a9f8b60ed733cdd60f3f5c875d0b604f7322ba678b6ba1435e77ef0b06e7a7db7c3d7c3dd63f1192588da1ae9f328e62498e1881b72ef4bfa1d82d4957a2dcecc66deb89b69ebedce867ca6e33efd361373db390f2a6d0dbd039d6220ef08299030983c8295519b550b16e9c420e60062beb7a01745171f050b1fc7b72632e0e676cb6e43a046d12968debc4571bbb209bc97560c9bc687cef74ad3894fc1cbac73bc8d7a4729091ee686ef37f3ac2bd8324f3f1465805a1dccdb
c2=0x67a01e36a5dbc1c2bd839fc3a2d8f8c6c6b4c2598e31383f50232715c67c6c82b82bedbad25ff226945b9f47604e24f177fce1e4d0783368e2fc2acd83d8676120ddb1233f63737f82deca8d29aeea309dcf9fb504b97cb96ef95390fbbcaeded6512d8d2c31aa682bdc6b97257e58c607190c2c60d3ef58c22ce0f9e4b1f22374b07d93be79f7d31e3b32315696d2007a14c393bb9cda1779bdb4c2143f1ccf321f3c2ea9547cb7e2352f16adbb59513c14febfdbe576173d7334eff93df349b23ffa4ff4d8ef732643d50f4486e6570d4943e64bc453c9f7079faa6a4095b0912fc4c2b15f52fc995c3245d666cfbbba6d39c5945226af6faf31fea71327cb
result = gongmo(n, c1, c2, e1, e2)
print(result)
print(long_to_bytes(result))
运行得到EOcLid_isA_fam0us_mathEMatic1an,包裹上GUETCTF{}即可
被加密的flag
题目描述:
下载附件解压得到两个文件
看来双是RSA,用openssl提取pubkey.pem:
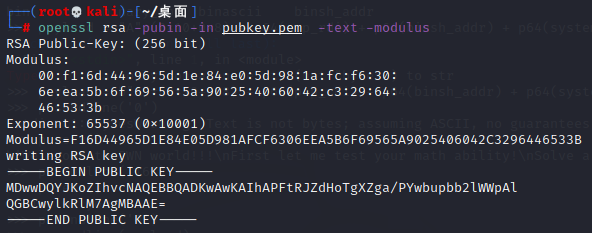
得到e与n,使用在线网站分解n得到p,q,然后运行解密脚本:
import gmpy2
from Crypto.Util.number import bytes_to_long, long_to_bytes
def Decrypt(c,e,p,q):
L=(p-1)*(q-1)
d=gmpy2.invert(e,L)
n=p*q
m=gmpy2.powmod(c,d,n)
flag=str(m)
return flag
e = 65537
c = int('D64D6679E996EC76E5B15FBA7D041E39E78D654805620BDC62A6F6739E067717',16)
p = 323004975986748856710125412204626739299
q = 338076699523223834306263480149120752969
print (Decrypt(c,e,p,q))
print(long_to_bytes(int(Decrypt(c,e,p,q))))
得到flag:flag{eszdcftg1}
Baby ECC
题目描述:
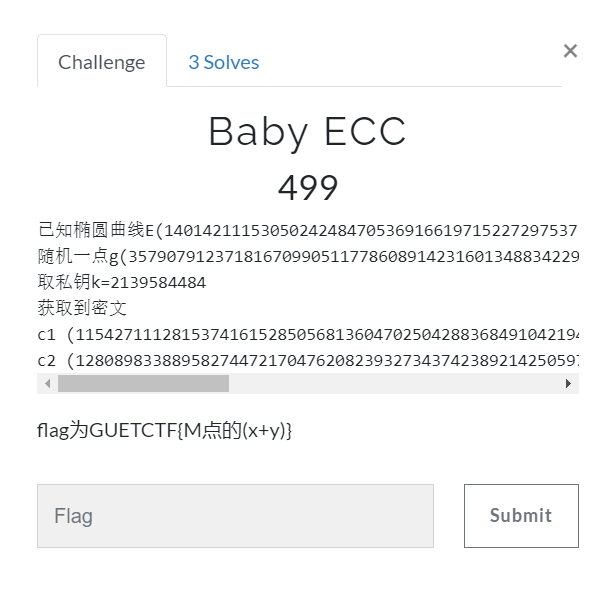
ecc加密哈(这不有手就行?)(其实是之前做题留下了脚本罢了,是🤡罢了)脚本如下:(这是SageMath的脚本)
p = 1401421115305024248470536916619715227297537105295017024196991
a = 6016276792420865932
b = 8845683521038554270
k = 2139584484
E = EllipticCurve(GF(p),[a,b]) #建立椭圆曲线E
c1 = E(1154271112815374161528505681360470250428836849104219407659553,128682657719813409877026526364025686177209391723996380707746)
c2 = E(1280898338895827447217047620823932734374238921425059778184612,813422297428564854961198345469363556433641635783360683901610)
m = c1-k*c2
print(m)
运行得到所求点,然后将x,y相加即可。结果一串数字而已,这里就不放了
写在最后
仅仅是校赛的初赛而已都比较基础,虽然写完了所有的密码题,但更多的是去套题型去做。对于脚本中的更深层次的数学原理还是不到位的,所以还需要继续加油啊。
作者:ta0tie
欢迎大家批评指正


