Istio
Service Mesh 介绍
它是一个用于处理服务和服务之间通信的基础设施层,它负责为构建复杂的云原生应用传递可靠的网络请求,并为服务通信实现了微服务所需要的基本功能:例 如服务发现,负载均衡监控,流量管理,访问控制等。在实践中,服务网络通常实现为一组和应用程序部署在一起的轻量级的网络代理,但对应用程序来说是透明的。
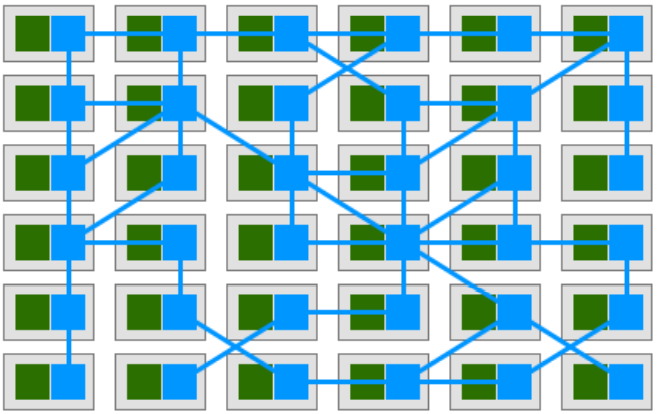
图中绿色表示应用,蓝色表示代理。访问网络中的某一个绿色的应用都需要要经过蓝色的代理转发。
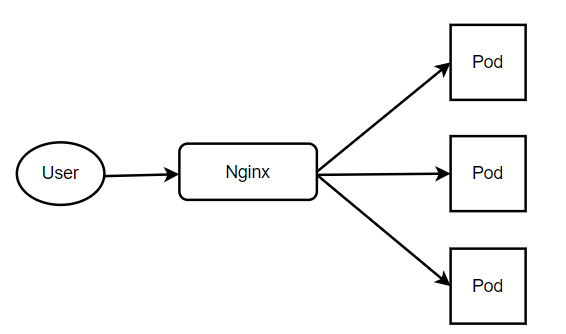
传统方式代理
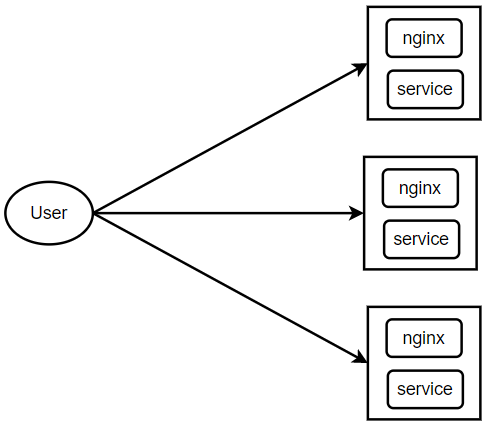
网格式代理
Servcie Mesh的架构
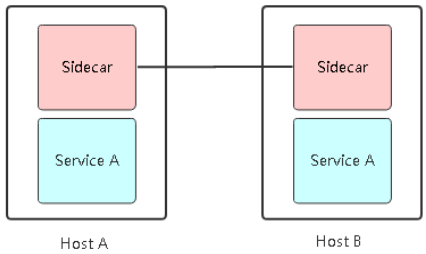
这种架构的优势:
ServiceA 相当于一个微服务,Sidecar是这个微服务的网络代理。ServiceA与外部的所有通信都由Sidercar来负责, Sidecar与ServiceA 相互独立,ServiceA感知不到Sidecar的存在,它们相当于是两个独立的容器,又在同一个Pod之中。
Istio的引入:
Istio 是ServiceMesh的产品化落地,是目前最受欢迎的服务网络,功能丰富,成熟度高。
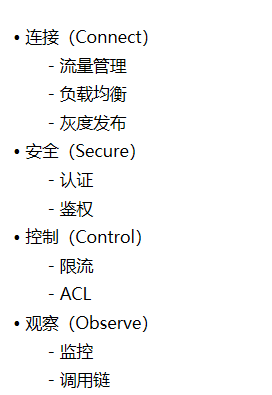
istio的主要功能:
istio与kubernetes的关系

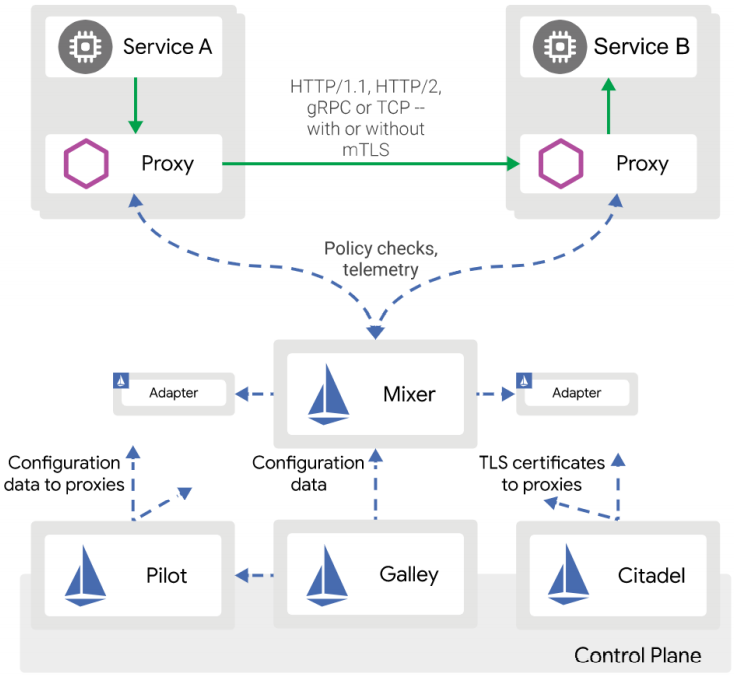
istio的架构
数据层面:(相当于k8s的node节点)由一组代理级成,代理微服务所有的网络通信,并接收和实施来自mixer的策略。
Proxy: 负责高效转发与策略实现。
控制层面:(相当于k8s的master节点)管理和代理来的路由流星。此外通过mixer实现策略与收集来自代理的数据。
Mixer: 适配组件,数据层面与控制层面通过它实现交互,为proxy提供策略和数据上报。
Pilot: 策略配置组件,为proxy提供服务发现,智能路由,错误处理等
Citadel: 安全组件,提供证书生成下发,加密通信,访问控制。
Galley: 配置管理,验证,分发。
Istio 基本概念
Istio有4个配置资源:
• VirtualService:实现服务请求路由规则的功能,相当地k8s中的service.
• DestinationRule:实现目标服务的负载均衡、服务发现、故障处理和故障注入的功能,相当于ingress.
• Gateway:让服务网格内的服务暴露出去。
• ServiceEntry :让服务网格内的服务可以访问外部
istio的安装
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 | [root@master ~]# mkdir istio[root@master ~]# cd istio/ #下载istio的版本[root@master istio]# wget https://github.com/istio/istio/releases/download/1.4.2/istio-1.4.2-linux.tar.gz[root@master istio]# lsistio-1.4.2-linux.tar.gz[root@master istio]# [root@master istio]# tar -zxvf istio-1.4.2-linux.tar.gz[root@master istio]# ls istio-1.4.2bin install LICENSE manifest.yaml README.md samples tools[root@master istio]# cd istio-1.4.2/[root@master istio-1.4.2]# ls bin/ #把istio的cli二进制文件拷贝到环境变量下istioctl[root@master istio-1.4.2]# cp bin/istioctl /usr/bin/[root@master istio-1.4.2]# #查看istio当前支持安装模式[root@master istio-1.4.2]# istioctl profile listIstio configuration profiles: default #默认安装 demo #完全安装 minimal #最小安装 remote sds[root@master istio-1.4.2]#[root@master istio-1.4.2]# istioctl manifest apply --set profile=demo |
[root@master istio-1.4.2]# kubectl get pods -n istio-system NAME READY STATUS RESTARTS AGE grafana-b64886fff-qrdg8 1/1 Running 0 8m20s istio-citadel-856f69777b-4mv7q 1/1 Running 0 8m20s istio-egressgateway-75fff48654-lczb9 1/1 Running 0 8m20s istio-galley-57f5cdf87d-blktg 1/1 Running 0 8m20s istio-pilot-85fb68b7bf-56rg2 1/1 Running 0 8m20s istio-policy-5c588db847-l9sft 1/1 Running 4 8m20s istio-sidecar-injector-578466d5fb-m8ms9 1/1 Running 0 8m20s istio-telemetry-64dc6d6cdc-hswzs 1/1 Running 4 8m20s istio-tracing-857496f799-jrgtc 1/1 Running 0 8m20s kiali-579dd86496-kzt7w 1/1 Running 0 8m19s prometheus-946f9f9d8-wlzdf 1/1 Running 0 8m20s [root@master istio-1.4.2]# kubectl get svc -n istio-system NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE grafana ClusterIP 10.96.87.251 <none> 3000/TCP 9m9s istio-citadel ClusterIP 10.101.89.27 <none> 8060/TCP,15014/TCP 9m11s istio-egressgateway ClusterIP 10.102.228.58 <none> 80/TCP,443/TCP,15443/TCP 9m8s istio-galley ClusterIP 10.108.64.59 <none> 443/TCP,15014/TCP,9901/TCP,15019/TCP 9m11s istio-pilot ClusterIP 10.99.228.174 <none> 15010/TCP,15011/TCP,8080/TCP,15014/TCP 9m9s istio-policy ClusterIP 10.105.240.99 <none> 9091/TCP,15004/TCP,15014/TCP 9m10s istio-sidecar-injector ClusterIP 10.98.138.15 <none> 443/TCP 9m11s istio-telemetry ClusterIP 10.106.146.103 <none> 9091/TCP,15004/TCP,15014/TCP,42422/TCP 9m8s jaeger-agent ClusterIP None <none> 5775/UDP,6831/UDP,6832/UDP 9m12s jaeger-collector ClusterIP 10.105.208.106 <none> 14267/TCP,14268/TCP,14250/TCP 9m12s jaeger-query ClusterIP 10.97.55.208 <none> 16686/TCP 9m11s kiali ClusterIP 10.97.143.182 <none> 20001/TCP 9m11s prometheus ClusterIP 10.96.55.150 <none> 9090/TCP 9m12s tracing ClusterIP 10.110.63.202 <none> 80/TCP 9m11s zipkin ClusterIP 10.98.209.74 <none> 9411/TCP 9m10s [root@master istio-1.4.2]#
Istio的应用案例 [root@master istio]# cd istio-1.4.2/ #安装目录下面官方已给了一些应用案例 [root@master istio-1.4.2]# pwd /root/istio/istio-1.4.2 [root@master istio-1.4.2]# ls bin install LICENSE manifest.yaml README.md samples tools [root@master istio-1.4.2]# cd samples/ [root@master samples]# ls bookinfo custom-bootstrap fortio helloworld https multicluster rawvm security tcp-echo certs external health-check httpbin kubernetes-blog operator README.md sleep websockets [root@master samples]# Httpbin的案例分析: [root@master httpbin]# kubectl apply -f httpbin-nodeport.yaml service/httpbin created deployment.apps/httpbin created [root@master httpbin]# [root@master httpbin]# kubectl get pod NAME READY STATUS RESTARTS AGE httpbin-77bfc6b755-v8szl 1/1 Running 0 112s [root@master httpbin]# [root@master httpbin]# kubectl get pod,svc NAME READY STATUS RESTARTS AGE pod/httpbin-77bfc6b755-v8szl 1/1 Running 0 2m38s NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE service/httpbin NodePort 10.97.169.216 <none> 8000:30412/TCP 2m38s service/kubernetes ClusterIP 10.96.0.1 <none> 443/TCP 239d service/servernamejava NodePort 10.100.184.91 <none> 80:32087/TCP 113d [root@master httpbin]# 访问方法:任意Node的地址+30412 NodePort访问地址:192.168.1.62:30412
以上案例是没有加入istio的,现在通过注入SideCar的方式引入istio
手动注入 kubectl apply -f <(istioctl kube-inject -f httpbin-nodeport.yaml) istioctl kube-inject -f httpbin-nodeport.yaml |kubectl apply -f - 自动注入 在namespace中添加标签后,该NS下的资源会被自动添加 kubectl label namespace default istio-injection=enabled kubectl apply -f httpbin-gateway.yaml 手动注入SideCar [root@master httpbin]# istioctl kube-inject -f httpbin-nodeport.yaml | kubectl apply -f - service/httpbin unchanged deployment.apps/httpbin configured [root@master httpbin]# #再次查看pod, istio-proxy容器已被注入 [root@master httpbin]# kubectl get pod NAME READY STATUS RESTARTS AGE httpbin-79bf7bbcd4-dsbd2 2/2 Running 0 4m14s [root@master httpbin]# [root@master httpbin]# #查看注入SideCar后的yaml文件 [root@master httpbin]# istioctl kube-inject -f httpbin-nodeport.yaml apiVersion: v1 kind: Service metadata: name: httpbin labels: app: httpbin spec: type: NodePort ports: - name: http port: 8000 targetPort: 80 selector: app: httpbin --- apiVersion: apps/v1 kind: Deployment metadata: creationTimestamp: null name: httpbin spec: replicas: 1 selector: matchLabels: app: httpbin version: v1 strategy: {} template: metadata: annotations: sidecar.istio.io/status: '{"version":"8d80e9685defcc00b0d8c9274b60071ba8810537e0ed310ea96c1de0785272c7","initContainers":["istio-init"],"containers":["istio-proxy"],"volumes":["istio-envoy","istio-certs"],"imagePullSecrets":null}' creationTimestamp: null labels: app: httpbin security.istio.io/tlsMode: istio version: v1 spec: containers: - image: docker.io/kennethreitz/httpbin imagePullPolicy: IfNotPresent name: httpbin ports: - containerPort: 80 resources: {} - args: - proxy - sidecar - --domain - $(POD_NAMESPACE).svc.cluster.local - --configPath - /etc/istio/proxy - --binaryPath - /usr/local/bin/envoy - --serviceCluster - httpbin.$(POD_NAMESPACE) - --drainDuration - 45s - --parentShutdownDuration - 1m0s - --discoveryAddress - istio-pilot.istio-system:15010 - --zipkinAddress - zipkin.istio-system:9411 - --proxyLogLevel=warning - --proxyComponentLogLevel=misc:error - --connectTimeout - 10s - --proxyAdminPort - "15000" - --concurrency - "2" - --controlPlaneAuthPolicy - NONE - --dnsRefreshRate - 300s - --statusPort - "15020" - --applicationPorts - "80" - --trust-domain=cluster.local env: - name: POD_NAME valueFrom: fieldRef: fieldPath: metadata.name - name: POD_NAMESPACE valueFrom: fieldRef: fieldPath: metadata.namespace - name: INSTANCE_IP valueFrom: fieldRef: fieldPath: status.podIP - name: SERVICE_ACCOUNT valueFrom: fieldRef: fieldPath: spec.serviceAccountName - name: HOST_IP valueFrom: fieldRef: fieldPath: status.hostIP - name: ISTIO_META_POD_PORTS value: |- [ {"containerPort":80} ] - name: ISTIO_META_CLUSTER_ID value: Kubernetes - name: ISTIO_META_POD_NAME valueFrom: fieldRef: fieldPath: metadata.name - name: ISTIO_META_CONFIG_NAMESPACE valueFrom: fieldRef: fieldPath: metadata.namespace - name: SDS_ENABLED value: "false" - name: ISTIO_META_INTERCEPTION_MODE value: REDIRECT - name: ISTIO_META_INCLUDE_INBOUND_PORTS value: "80" - name: ISTIO_METAJSON_LABELS value: | {"app":"httpbin","version":"v1"} - name: ISTIO_META_WORKLOAD_NAME value: httpbin - name: ISTIO_META_OWNER value: kubernetes://api/apps/v1/namespaces/default/deployments/httpbin - name: ISTIO_META_MESH_ID value: cluster.local image: docker.io/istio/proxyv2:1.4.2 imagePullPolicy: IfNotPresent name: istio-proxy ports: - containerPort: 15090 name: http-envoy-prom protocol: TCP readinessProbe: failureThreshold: 30 httpGet: path: /healthz/ready port: 15020 initialDelaySeconds: 1 periodSeconds: 2 resources: limits: cpu: "2" memory: 1Gi requests: cpu: 10m memory: 40Mi securityContext: readOnlyRootFilesystem: true runAsUser: 1337 volumeMounts: - mountPath: /etc/istio/proxy name: istio-envoy - mountPath: /etc/certs/ name: istio-certs readOnly: true initContainers: - command: - istio-iptables - -p - "15001" - -z - "15006" - -u - "1337" - -m - REDIRECT - -i - '*' - -x - "" - -b - '*' - -d - "15020" image: docker.io/istio/proxyv2:1.4.2 imagePullPolicy: IfNotPresent name: istio-init resources: limits: cpu: 100m memory: 50Mi requests: cpu: 10m memory: 10Mi securityContext: capabilities: add: - NET_ADMIN runAsNonRoot: false runAsUser: 0 volumes: - emptyDir: medium: Memory name: istio-envoy - name: istio-certs secret: optional: true secretName: istio.default status: {} --- [root@master httpbin]# #使用istio-gateway方式访问httpbin [root@master httpbin]# ls httpbin-gateway.yaml httpbin-nodeport.yaml httpbin-vault.yaml httpbin.yaml policy README.md sample-client [root@master httpbin]# [root@master httpbin]# cat httpbin-gateway.yaml apiVersion: networking.istio.io/v1alpha3 kind: Gateway metadata: name: httpbin-gateway spec: selector: istio: ingressgateway servers: - port: number: 80 name: http protocol: HTTP hosts: - "*" --- apiVersion: networking.istio.io/v1alpha3 kind: VirtualService metadata: name: httpbin spec: hosts: - "*" gateways: - httpbin-gateway http: - route: - destination: host: httpbin port: number: 8000 [root@master httpbin]#






【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】凌霞软件回馈社区,博客园 & 1Panel & Halo 联合会员上线
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】博客园社区专享云产品让利特惠,阿里云新客6.5折上折
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步