12、kubernetes之 RBAC
第十一部分 RBAC
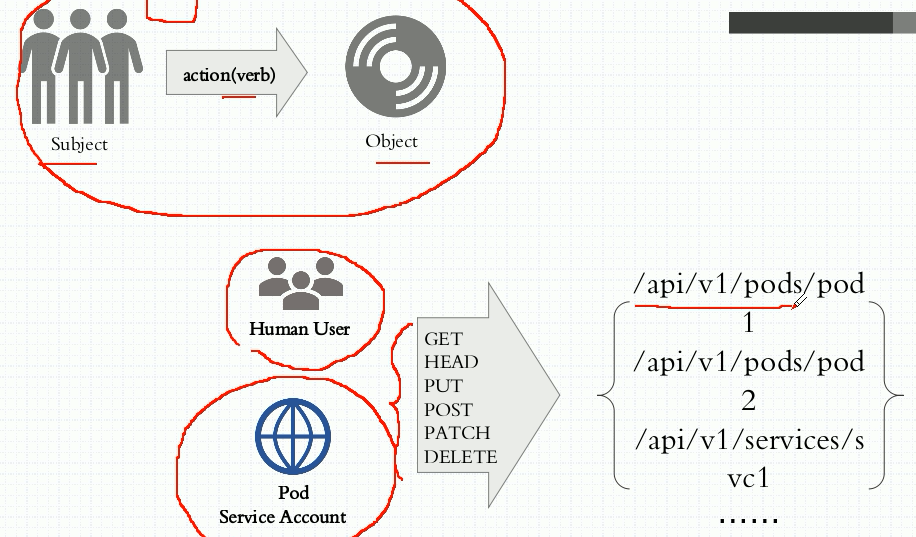
restful操作对象:许可授权都作用于角色,用户是什么角色,就拥有什么操作权限
授权插件:Node、ABAC、RBAC、Webhook RBAC:Role-based AC 角色:Role 许可:permission
关联图示
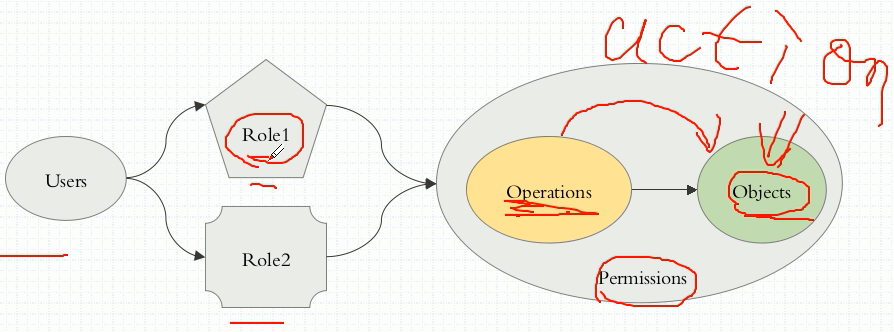
客户端访问示意图:
role: operations:许可 object: rolebinging: user account or service account role
授权:定义标准的。
Role、RoleBinding:命名空间内级别
ClusterRole、ClusterRoleBinding:集群角色、集群角色绑定
视图:

RoleBinding限制在ns范围内,即使绑定了clusterRole,也只在ns内生效。
RoleBinding:只作用于当前名称空间。
clusterrolebindings:作用集群内所有ns。
Role、RoleBinding、clusterrole、clusterrolebindings都是标准的kubernetes资源。。
示例:为每个ns配置一个管理员,可配置一个clusterrole,RoleBinding绑定(这样角色可以作用于集群,用户管理各自的ns,互不干扰)。
[root@k8s-master ~]# kubectl create role pods-reader --verb=get,list,watch --resource=pods --dry-run -o yaml # 查看创建信息
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
...
[root@k8s-master rbac]# cat role-demo.yaml
[root@k8s-master rbac]# cat role-demo.yaml apiVersion: rbac.authorization.k8s.io/v1 kind: Role metadata: name: pods-reader namespace: default rules: - apiGroups: - "" resources: - pods verbs: - get - list - watch
[root@k8s-master rbac]# kubectl create -f role-demo.yaml
role.rbac.authorization.k8s.io/pods-reader created
[root@k8s-master rbac]# kubectl get role
NAME AGE
pods-reader 10s
[root@k8s-master rbac]# kubectl describe role pods-reader
Name: pods-reader
Labels: <none>
Annotations: <none>
PolicyRule:
Resources Non-Resource URLs Resource Names Verbs
--------- ----------------- -------------- -----
pods [] [] [get list watch]
开始绑定用户:
前面章节创建过sunny用户
[root@k8s-master rbac]# kubectl create rolebinding sunny-read-pods --role=pods-reader --user=sunny --dry-run -o yaml
[root@k8s-master rbac]# kubectl create rolebinding sunny-read-pods --role=pods-reader --user=sunny --dry-run -o yaml >rolebinding-demo.yaml

[root@k8s-master rbac]# cat rolebinding-demo.yaml apiVersion: rbac.authorization.k8s.io/v1 kind: RoleBinding metadata: name: sunny-read-pods roleRef: apiGroup: rbac.authorization.k8s.io kind: Role name: pods-reader subjects: - apiGroup: rbac.authorization.k8s.io kind: User name: sunny
[root@k8s-master rbac]# kubectl create -f rolebinding-demo.yaml
rolebinding.rbac.authorization.k8s.io/sunny-read-pods created
[root@k8s-master rbac]# kubectl get rolebinding NAME AGE sunny-read-pods 12s [root@k8s-master rbac]# kubectl describe rolebinding Name: sunny-read-pods Labels: <none> Annotations: <none> Role: Kind: Role Name: pods-reader Subjects: Kind Name Namespace ---- ---- --------- User sunny
验证测试:切换用户
[root@master ~]# kubectl config view 查看用户
[root@master ~]# kubectl config use-context sunny@kubernetes(切换用户,查看权限。切换后,影响同一个客户端)
[root@k8s-master rbac]# kubectl get pods -n kube-system
Error from server (Forbidden): pods is forbidden: User "sunny" cannot list resource "pods" in API group "" in the namespace "kube-system"
[root@k8s-master rbac]# kubectl get pods -A
Error from server (Forbidden): pods is forbidden: User "sunny" cannot list resource "pods" in API group "" at the cluster scope
[root@k8s-master rbac]# kubectl get pods -n default (rolebinding只对当前ns生效)
NAME READY STATUS RESTARTS AGE
myapp-0 1/1 Running 0 28h
...
[root@k8s-master rbac]# kubectl delete pods myapp-0
Error from server (Forbidden): pods "myapp-0" is forbidden: User "sunny" cannot delete resource "pods" in API group "" in the namespace "default"
假设需要授予所有权限,咱们可以使用*来代替。
避免账户切换后,影响统一客户端多窗口切换,可创建普通账户。
[root@k8s-master ~]# useradd ik8s
[root@k8s-master ~]# cp -rp .kube/ /home/ik8s
[root@k8s-master ~]# chown -R ik8s.ik8s /home/ik8s/
[root@k8s-master ~]# su - ik8s
[ik8s@k8s-master ~]$ kubectl config use-context sunny@kubernetes
Switched to context "sunny@kubernetes".
[ik8s@k8s-master ~]$ kubectl config view
[root@k8s-master rbac]# kubectl delete rolebinding sunny-read-pods 删除rolebinding,切换用户,立马没有操作权限了。
[root@k8s-master rbac]# kubectl config use-context sunny@kubernetes
Switched to context "sunny@kubernetes".
[root@k8s-master rbac]# kubectl get pods
Error from server (Forbidden): pods is forbidden: User "sunny" cannot list resource "pods" in API group "" in the namespace "default"
下面介绍ClusterRole
配置clusterrole,rolebinding晋级模式
ClusterRolebinding只能绑定ClusterRole
RoleBinding可以绑定ClusterRole、Role。
创建clusterrole
[root@k8s-master ~]# kubectl create clusterrole cluster-reader --verb=get,list,watch --resource=pods --dry-run -o yaml > clusterrole-demo.yaml
编辑配置文件,

[root@k8s-master rbac]# cat clusterrole-demo.yaml apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRole metadata: name: cluster-reader rules: - apiGroups: - "" resources: - pods verbs: - get - list - watch
创建clusterrolebinding
[root@k8s-master rbac]# kubectl create clusterrolebinding sunny-read-all-pods --clusterrole=cluster-read --user=sunny --dry-run -oyaml> clusterrolebinding-demo.yaml
[root@k8s-master rbac]# vim clusterrolebinding-demo.yaml

[root@k8s-master rbac]# cat clusterrolebinding-demo.yaml apiVersion: rbac.authorization.k8s.io/v1beta1 kind: ClusterRoleBinding metadata: name: sunny-read-all-pods roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: cluster-read subjects: - apiGroup: rbac.authorization.k8s.io kind: User name: sunny
[root@k8s-master rbac]# kubectl create -f clusterrolebinding-demo.yaml
clusterrolebinding.rbac.authorization.k8s.io/sunny-read-all-pods created
[ik8s@k8s-master ~]$ kubectl get clusterrolebinding |grep sunn
sunny-read-all-pods 10s
[ik8s@k8s-master ~]$ kubectl describe clusterrolebinding sunny-read-all-pods
验证测试:切换用户验证读权限ok,没有授权删除,故没有删除权限
换成cluster服务,只授予读权限,在全集群内都可生效。
ClusterRole绑定RoleBinding会降级,由集群权限变成RoleBinding单个ns范围内。
不妨使用rolebing绑定clusterrole试试,
换成cluster服务,只授予读权限,在全集群内都可生效。
RoleBinding绑定ClusterRole会降级,由集群权限变成RoleBinding单个ns范围内。这部分自行演示下。
[root@k8s-master ~]# kubectl get clusterrole admin -oyaml
aggregationRule:
clusterRoleSelectors:
- matchLabels:
rbac.authorization.k8s.io/aggregate-to-admin: "true"
...
可以通过github官网查看flannel yaml配置文件。加深理解四个RBAC含义。
自此,完成了RABC的学习过程。






【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 无需6万激活码!GitHub神秘组织3小时极速复刻Manus,手把手教你使用OpenManus搭建本
· Manus爆火,是硬核还是营销?
· 终于写完轮子一部分:tcp代理 了,记录一下
· 别再用vector<bool>了!Google高级工程师:这可能是STL最大的设计失误
· 单元测试从入门到精通
2019-07-15 linux下安装jboss