Proxifier配合burp抓包但是burp收不到响应包解决思路
作者:@11阳光
本文为作者原创,转载请注明出处:https://www.cnblogs.com/sunny11/p/17159471.html
题记
最近公司的项目比较特殊,不是传统的在web端的测试。而是客户给了一个exe,安装在电脑之后需要登录在工作台点击相关系统测试,点击相关系统后会在exe内部开一个窗口显示网站内容。后面引出我们本次发现的问题。
使用工具
1、Proxifier
2、burp
Proxifier配合burp
我们想抓exe内部的网站,第一个思路便是在proxifier开配置全局代理代理到https://127.0.0.1:8080的burp上,burp(java.exe)走直连。这种思路缺点就是会抓到大量的我们不需要的垃圾数据包。
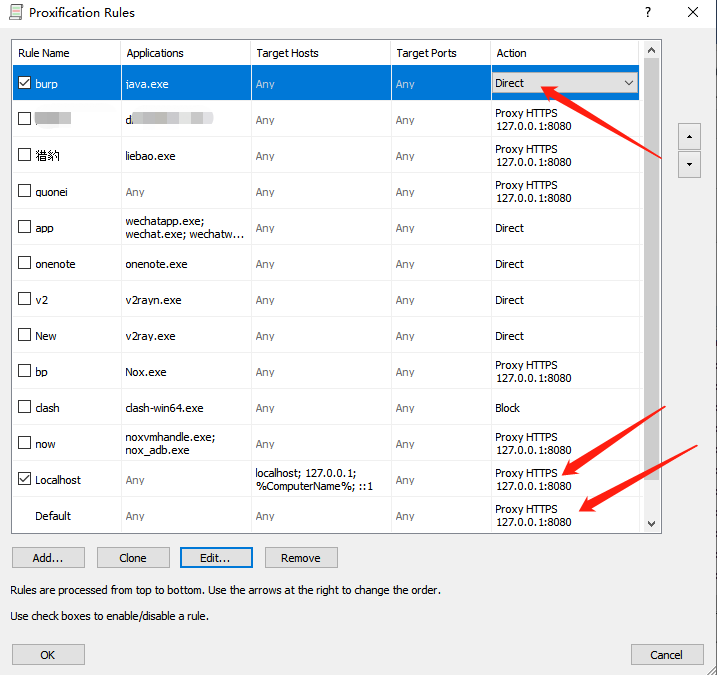
测试后发现我们所有的请求都收不到响应包,一时间陷入了难题。
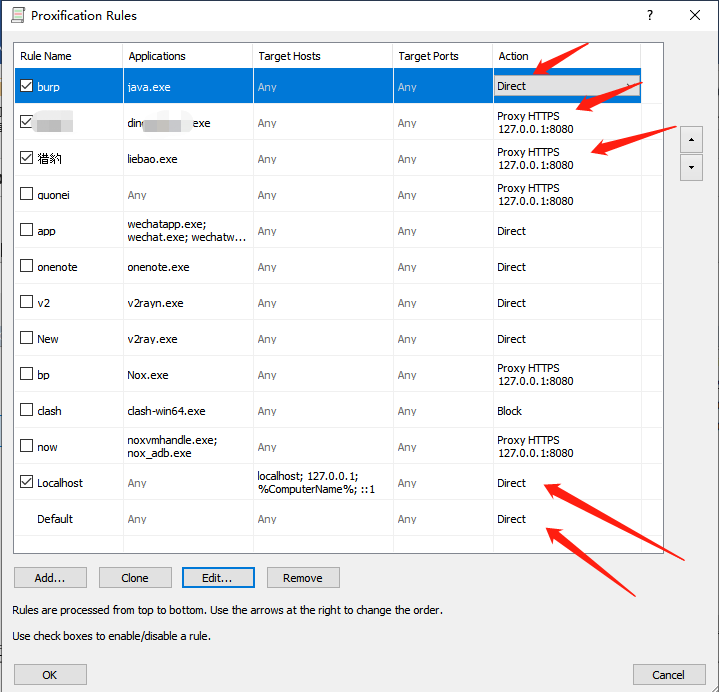
第一个思路不行我就尝试了一下第二个思路,是在proxifier开配置全局代理直连,然后把想抓包的exe单独配置代理到https://127.0.0.1:8080,这里java.exe的代理规则可关可不关。
这样配置完之后发现网络还是不通,全局代理可将所有的请求包转发到burp上但是收不到响应包,在网上搜了很多教程均不适用,测试了很多遍,大方向认为是burp相关问题。一挂全局Burp就收不到响应,怎么调整都不好。
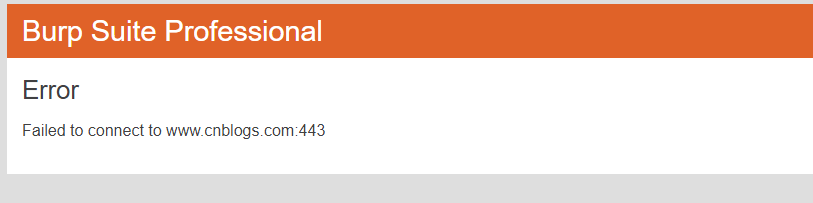
最后发现一篇文章是这么说的。
1 2 3 4 5 6 | <span class="pln"> </span><span class="pun">有一点设置通常容易被忽略,就是在</span><span class="typ">Proxifier</span><span class="pun">中,设置[</span><span class="typ">Profile</span><span class="pun">]</span><span class="pln"> </span><span class="pun">—</span><span class="pln"> </span><span class="pun">[</span><span class="typ">Name</span><span class="pln"> </span><span class="typ">Resolution</span><span class="pun">]</span><span class="pln"> </span><span class="pun">—</span><span class="pln"> </span><span class="pun">勾选</span><span class="pln"> </span><span class="pun">[</span><span class="typ">Resolve</span><span class="pln"> hostnames through proxy</span><span class="pun">],让域名解析的工作交给代理服务器,而不是在</span><span class="typ">Proxifier</span><span class="pun">上解析。</span><span class="pln"> </span><span class="pun">默认情况下</span><span class="typ">Proxifier</span><span class="pun">自行解析域名,比如</span><span class="pln">www</span><span class="pun">.</span><span class="pln">baidu</span><span class="pun">.</span><span class="pln">com</span><span class="pun">解析为</span><span class="lit">180.97</span><span class="pun">.</span><span class="lit">33.108</span><span class="pun">,然后发请求给</span><span class="typ">Fiddler</span><span class="pun">:</span><span class="pln">CONNECT </span><span class="lit">180.97</span><span class="pun">.</span><span class="lit">33.108</span><span class="pun">:</span><span class="lit">443</span><span class="pln"> HTTP</span><span class="pun">/</span><span class="lit">1.1</span><span class="pln"> </span><span class="pun">这样</span><span class="typ">Fiddler</span><span class="pun">并不知道它请求的是哪个域名,于是返回给客户端的伪造证书时,伪造的是为</span><span class="lit">180.97</span><span class="pun">.</span><span class="lit">33.108</span><span class="pun">颁发的证书,有的客户端会做校验,发现这个证书是颁发给</span><span class="lit">180.97</span><span class="pun">.</span><span class="lit">33.108</span><span class="pun">的,而不是颁发给</span><span class="pln">www</span><span class="pun">.</span><span class="pln">baidu</span><span class="pun">.</span><span class="pln">com</span><span class="pun">的,然后报错处理。</span><span class="pln"> </span><span class="pun">修改</span><span class="typ">Proxifier</span><span class="pun">设置后,把域名解析的工作交给代理服务器,</span><span class="typ">Proxifier</span><span class="pun">会直接向</span><span class="typ">Fiddler</span><span class="pun">发送请求:</span><span class="pln"> CONNECT www</span><span class="pun">.</span><span class="pln">baidu</span><span class="pun">.</span><span class="pln">com</span><span class="pun">:</span><span class="lit">443</span><span class="pln"> HTTP</span><span class="pun">/</span><span class="lit">1.1</span><span class="pln"> </span><span class="pun">这样</span><span class="typ">Fiddler</span><span class="pun">就知道客户端请求的是</span><span class="pln"> www</span><span class="pun">.</span><span class="pln">baidu</span><span class="pun">.</span><span class="pln">com</span><span class="pun">,从而返回客户端伪造的</span><span class="pln">www</span><span class="pun">.</span><span class="pln">baidu</span><span class="pun">.</span><span class="pln">com</span><span class="pun">证书,客户端不报错,</span><span class="typ">Fiddler</span><span class="pun">才能顺利抓包解密。</span> |
通过对上面的理解我们知道我们是通过Proxifier转发到burp上的,而burp是不存在域名解析的功能的,所以他找不到目标地址。因此我们不让域名解析的工作交给代理服务器,就需要关闭Resolve hostnames through proxy。
解决办法:设置[Profile] — [Name Resolution] — 取消勾选 [Resolve hostnames through proxy]
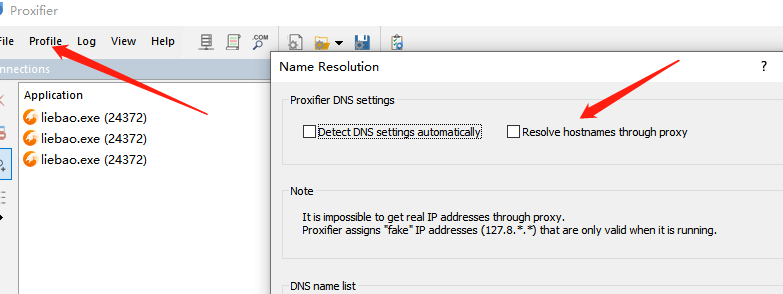
访问即可恢复正常,用fillder的时候在勾选上即可。
参考文章
Fiddler抓包指南:结合Proxifier工具:https://blog.csdn.net/china_jeffery/article/details/93000824














【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】凌霞软件回馈社区,博客园 & 1Panel & Halo 联合会员上线
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】博客园社区专享云产品让利特惠,阿里云新客6.5折上折
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· [翻译] 为什么 Tracebit 用 C# 开发
· Deepseek官网太卡,教你白嫖阿里云的Deepseek-R1满血版
· 2分钟学会 DeepSeek API,竟然比官方更好用!
· .NET 使用 DeepSeek R1 开发智能 AI 客户端
· 刚刚!百度搜索“换脑”引爆AI圈,正式接入DeepSeek R1满血版