Python2之nmap扫描端口与服务开启情况和服务扫描和扫描目标系统
题记
元旦看电影的时候发现自己在微信抽中了一台kali服务器,真是需要什么来什么,有时候觉得自己是一个不坚定的唯物主义者,总在特定的时候看到特定的事。接下来一个月我要把持住这个机会,把自己的想法的实现了。

nmap扫描端口与服务开启情况
import sys
import nmap
if len(sys.argv) != 3 :
print ("usage:PortScanner \n eg:192.168.0.1 80-554")
sys.exit(1)
target=sys.argv[1]
port=sys.argv[2]
nm=nmap.PortScanner()
nm.scan(target,port)
for host in nm.all_hosts():
print("----------------------------------------------")
print('host:{0}({1})'.format(host,nm[host].hostname()))
print("state:{0}".format(nm[host].state()))
for proto in nm[host].all_protocols():
print ("-----------------------------")
print("proto:{0}".format(proto))
lport=list(nm[host][proto].keys()) #获取协议的所有扫描端口
lport.sort()
for port in lport:
print("port:{0}\t state:{1}".format(port,nm[host][proto][port]))
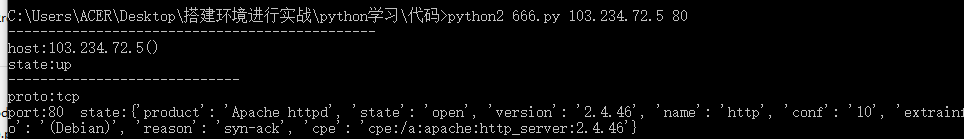
服务扫描
import sys
import nmap
if len(sys.argv) != 3 :
print ("usage:ServiceScan \n eg:192.168.0.1 80-554")
sys.exit(1)
target=sys.argv[1]
port=sys.argv[2]
nm=nmap.PortScanner()
nm.scan(target,port,"-sV")
for host in nm.all_hosts():
for proto in nm[host].all_protocols():
lport=list(nm[host][proto].keys())
lport.sort()
for port in lport:
print("port:{0}\t product:{1}".format(port,nm[host][proto][port]['product']))

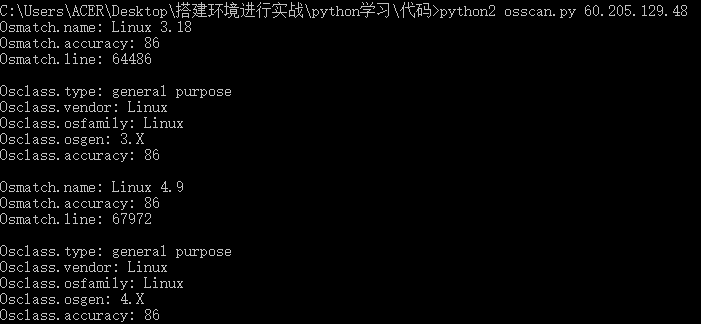
目标系统扫描
import sys
import nmap
if len(sys.argv) != 2:
print('usage:osscan \n eg:192.168.0.1 ')
sys.exit(1)
target=sys.argv[1]
nm=nmap.PortScanner()
nm.scan(target,arguments="-O")
if 'osmatch' in nm[target]:
for osmatch in nm[target]['osmatch']:
print ('Osmatch.name: {0}'.format(osmatch['name']))
print ('Osmatch.accuracy: {0}'.format(osmatch['accuracy']))
print ('Osmatch.line: {0}'.format(osmatch['line']))
print ('')
if 'osclass' in osmatch:
for osclass in osmatch['osclass']:
print ('Osclass.type: {0}'.format(osclass['type']))
print ('Osclass.vendor: {0}'.format(osclass['vendor']))
print ('Osclass.osfamily: {0}'.format(osclass['osfamily']))
print ('Osclass.osgen: {0}'.format(osclass['osgen']))
print ('Osclass.accuracy: {0}'.format(osclass['accuracy']))
print ('')