2. 20141123
BASIC QUESTIONS:
What is the IP address of the Windows VM that gets infected?
将所有的http 对象导出来,再用杀毒软件查杀。
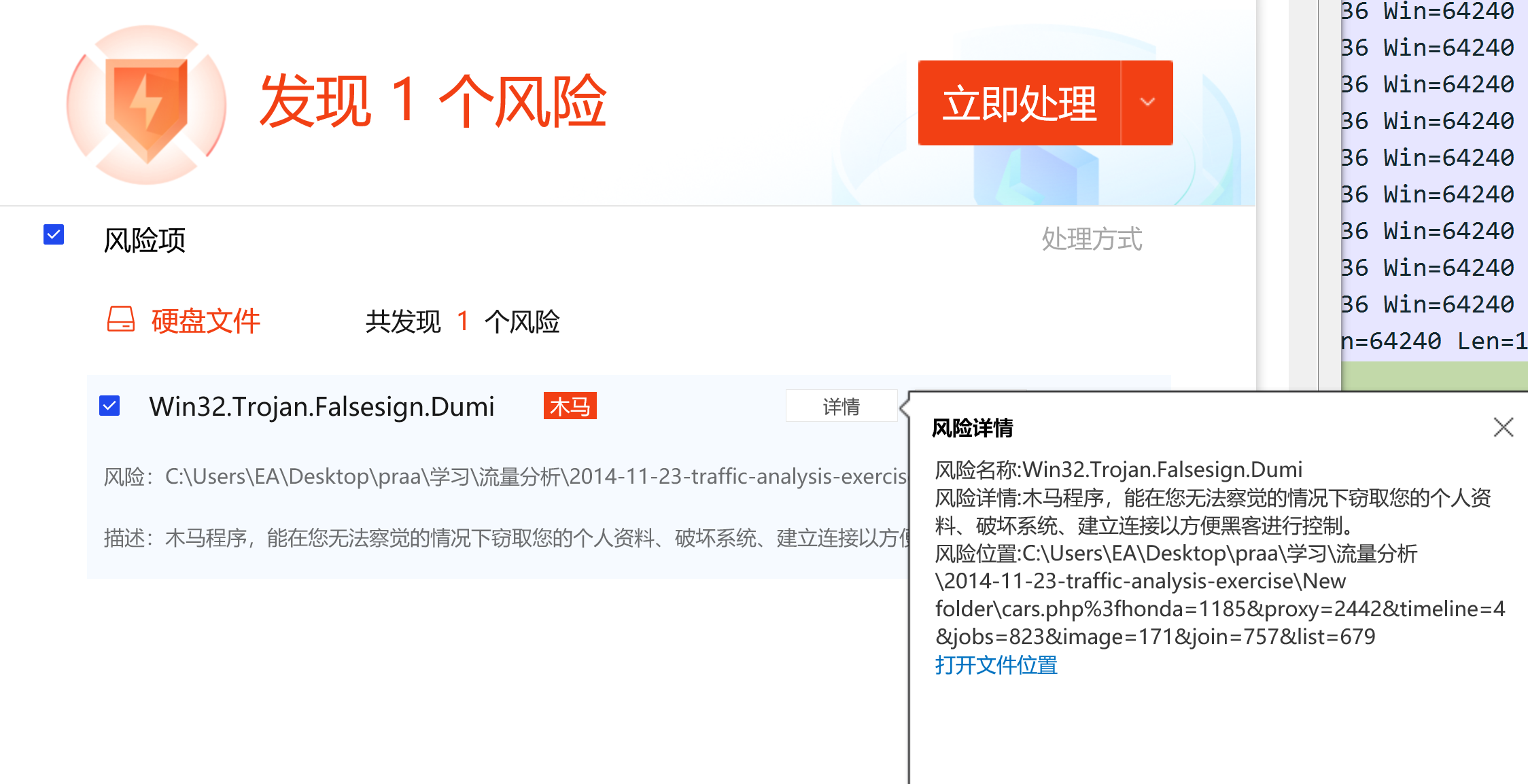
根据文件名定位到数据包
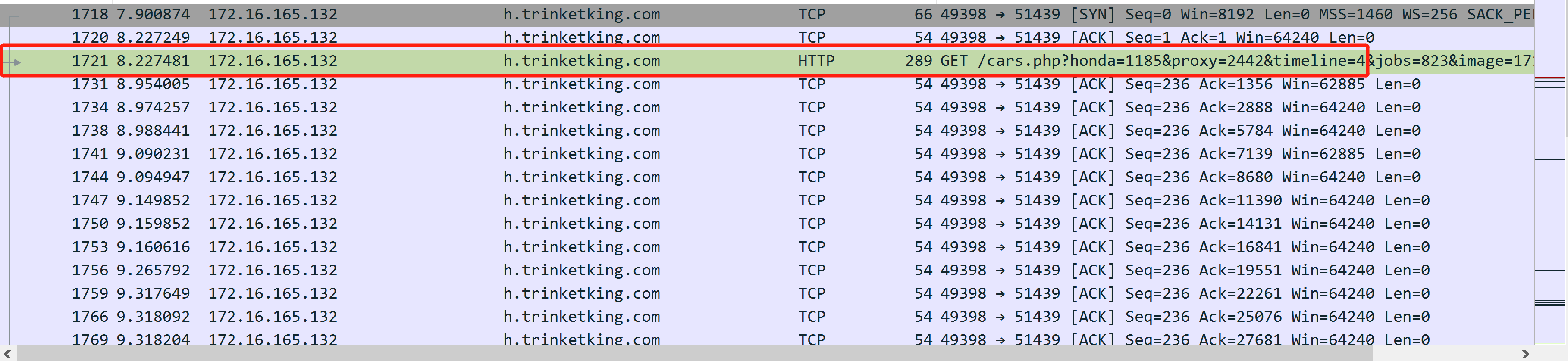
所以就是 172.16.165.132
What is the MAC address of the infected VM?
查看对应的 mac 地址即可。
What is the IP address of the compromised web site?
192.30.138.146
What is the domain name of the compromised web site?
从上题能看出
What is the IP address and domain name that delivered the exploit kit and malware?
ip.dst == 37.143.15.180
What is the domain name that delivered the exploit kit and malware?
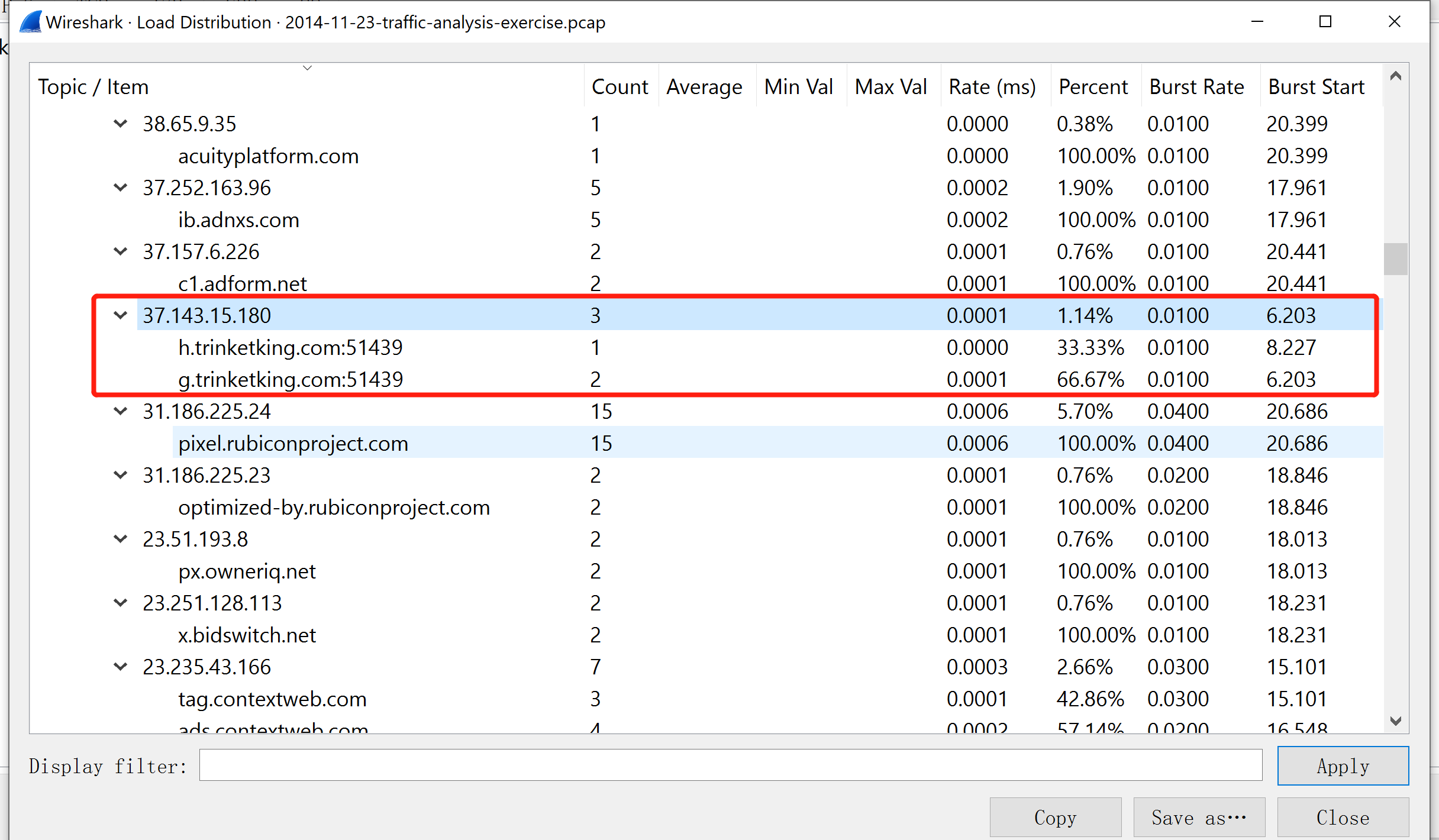
MORE ADVANCED QUESTIONS:
What is the exploit kit (EK) that delivers the malware?

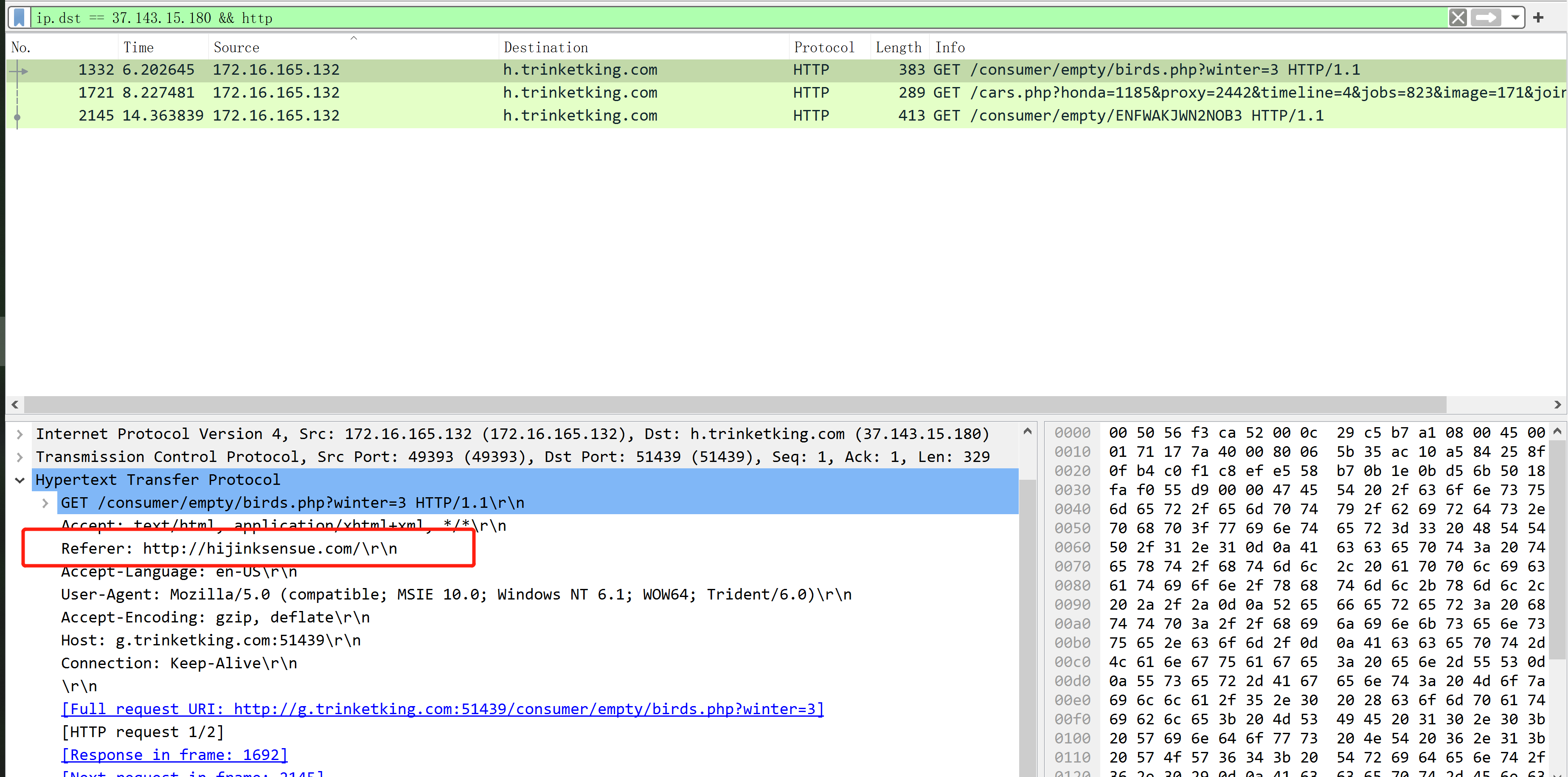
What is the redirect URL that points to the exploit kit (EK) landing page?

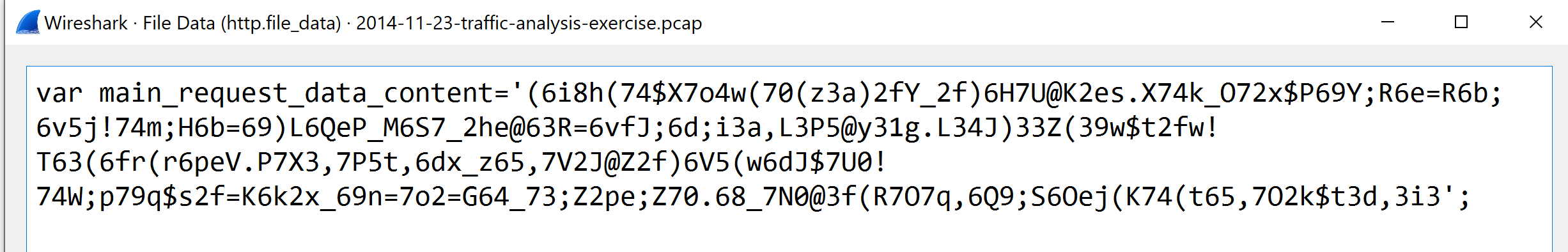
所以答案就是 http://static.charlotteretirementcommunities.com/k?tstmp=3701802802
老实说,这个 js 没有明显的跳转,国外博客上是这样解释的
There is no clear text iframe linking to the exploit kit domain. There is a bit of JavaScript at the bottom which could be assumed to be something of a referral URL.
What is the IP address of the redirect URL that points to the exploit kit (EK) landing page?
查看上一题的 ip 即可。
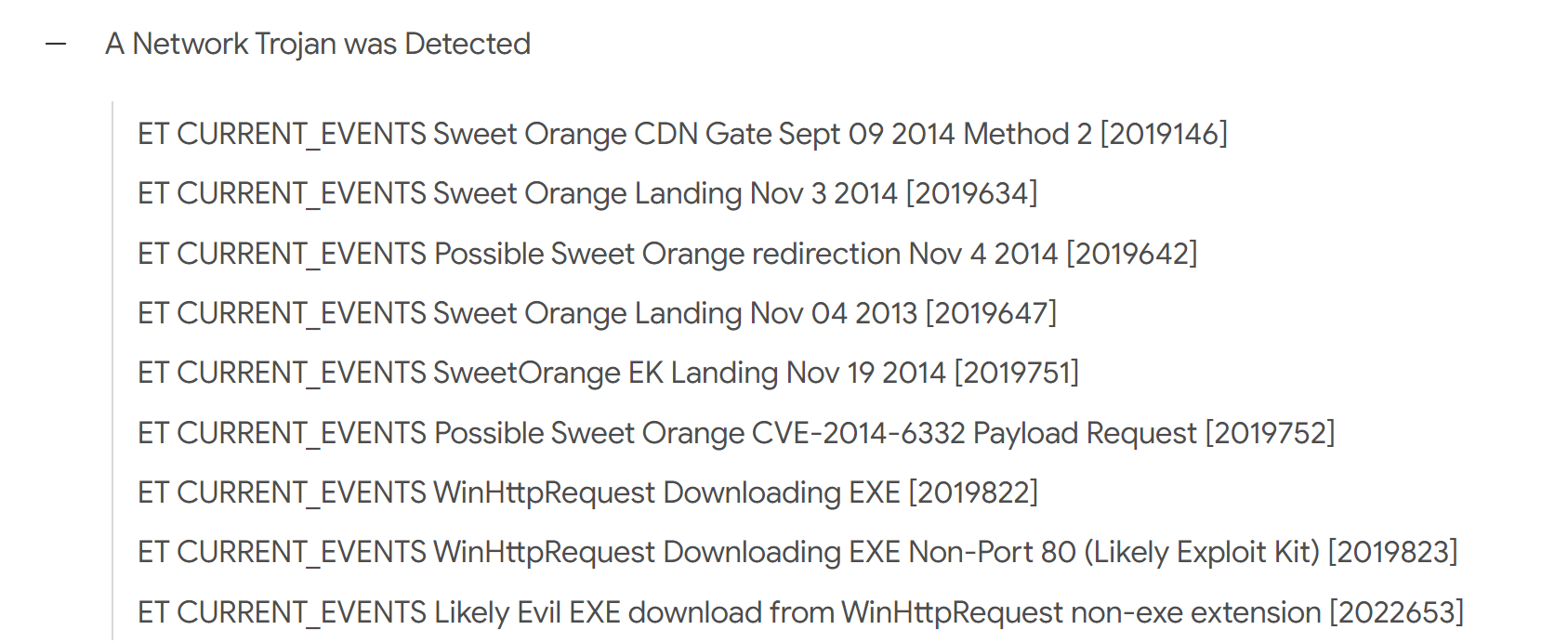
Submit the pcap to VirusTotal and find out what snort alerts triggered. Do any of the alerts indicate what this exploit kit this is?
直接将流量文件提交到 virustotal
Extract the malware payload from the pcap. What is the MD5 or SHA256 hash?
计算一下那个恶意文件的 md5 即可
EXTRA QUESTIONS:
If you use Suricata, what EmergingThreats signatures fire on the exploit kit traffic?
直接将流量文件提交到 virustotal
What exploit (which CVE) is used by this EK?
直接将流量文件提交到 virustotal ,可以看到 cve-2014-6332


 浙公网安备 33010602011771号
浙公网安备 33010602011771号