MISC刷题12
[安洵杯 2020]BeCare4
附件:带密码的flag.7z和npmtxt
将npmtxt拖入010,发现:
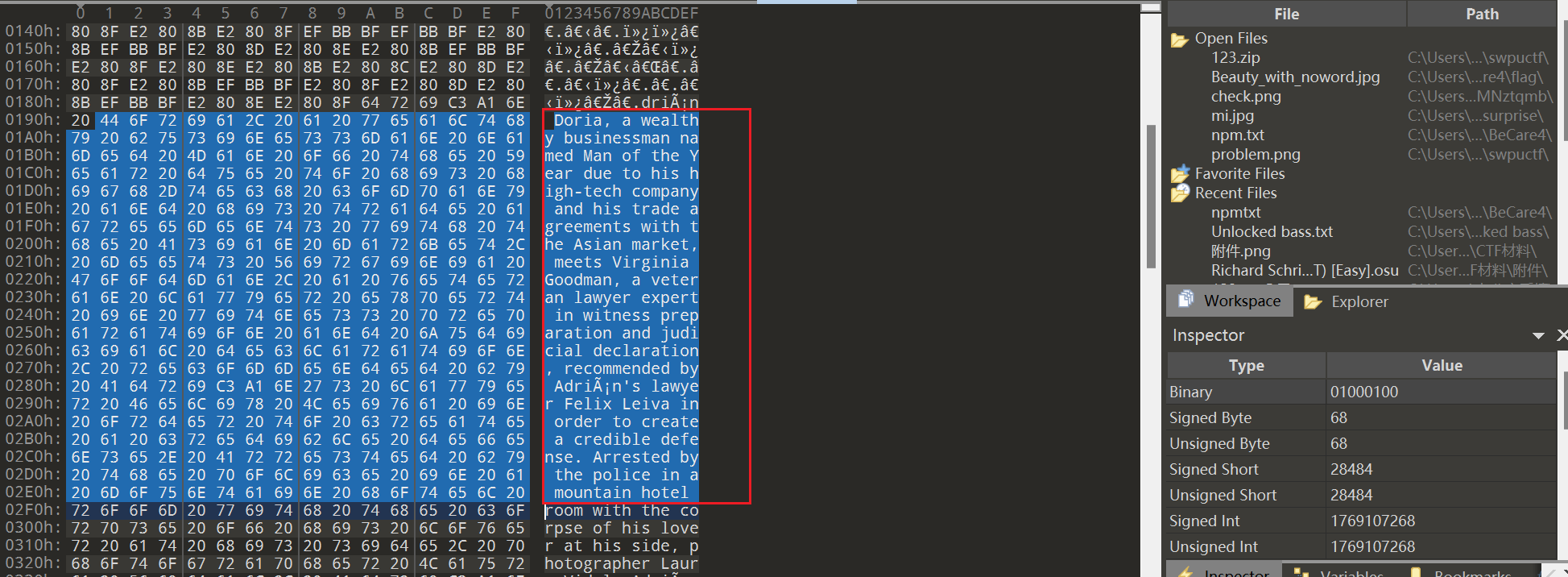
有一段故事,但故事之中有隐写
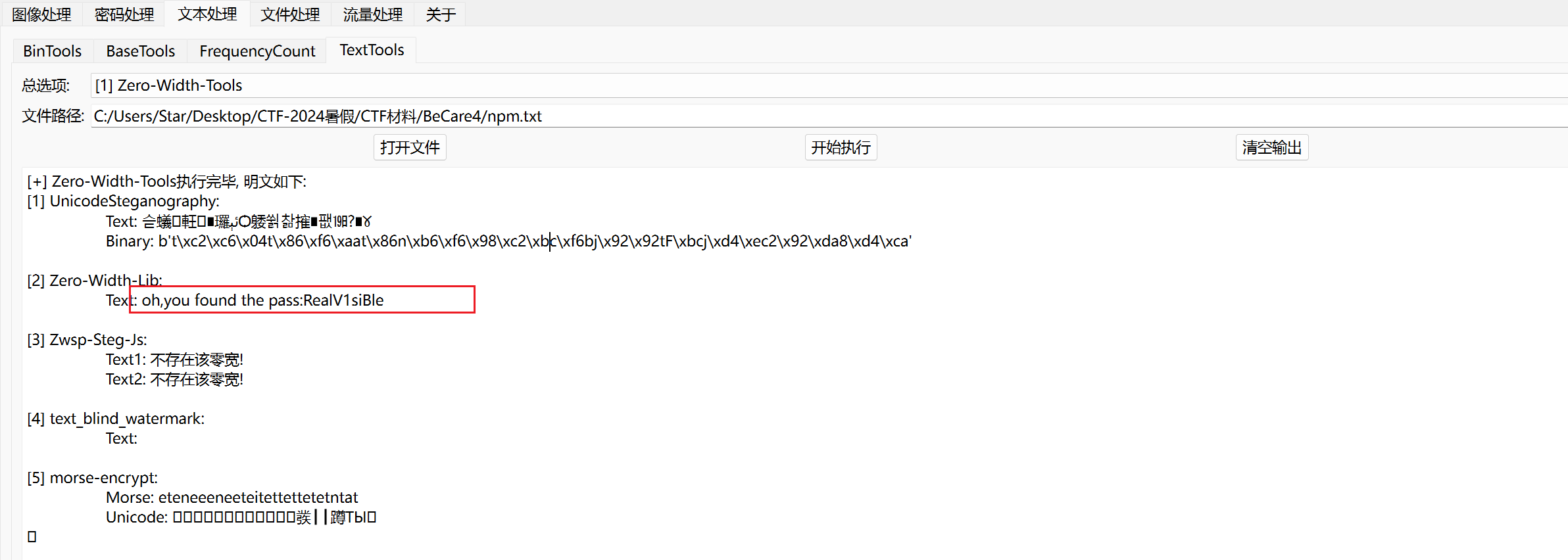
密码为RealV1siBle
以此密码解压flag.7z,得到Beauty_with_noword.jpg
使用silentEye解密:
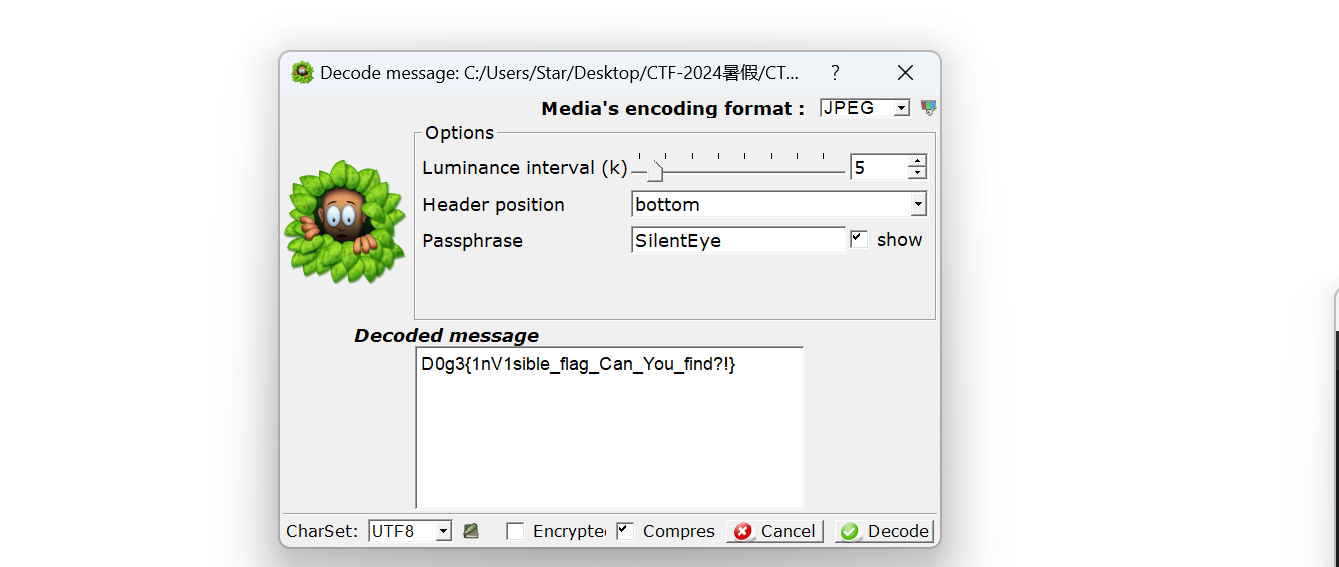
[NSSRound#3 Team]funnypng
https://blog.csdn.net/gou1791241251/article/details/124809703
附件---funnypng.png
先使用stegsolve打开查看每个通道展示的图片情况:
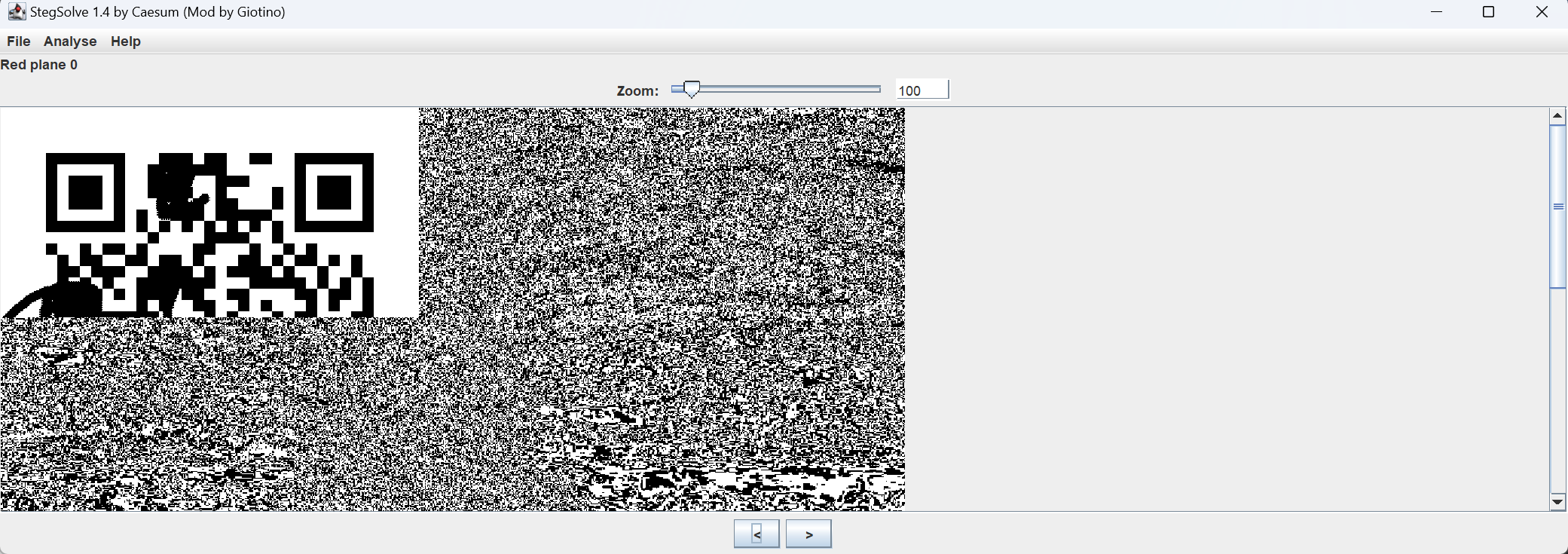
得到一半的二维码,接下来就是找另一半二维码
使用Data Extract查看是否有LSB隐写或者MSB隐写(一般是低位隐写),但是并没有发现奇怪的地方
接着查看图片属性:
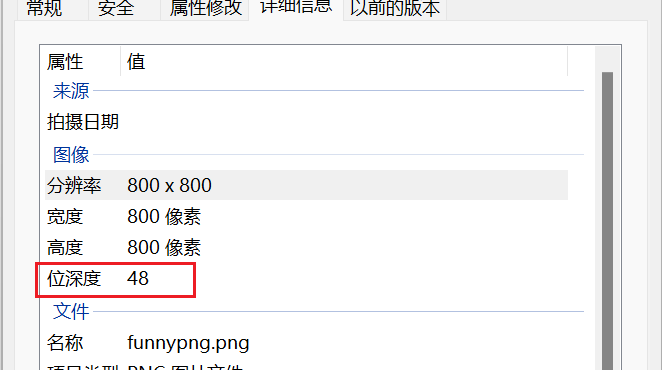
位深度为48,比较大
加上使用stegsolve时发现A通道其实是空白,说明该图片只有三个通道RGB,那么每个通道深度为48/3=16bit,说明该图片隐藏了另外的8bit的信息
把原来的图片所有像素点修改之后,将深度改为8bit:
import png # pip install pypng
import time
img = png.Reader('funnypng.png')
imginfo = img.read()
w, h, imgdata = imginfo[:3]
data = []
for linedata in imgdata:
line = []
for d in linedata:
line.append(d%(2**8))
data.append(line)
with open('front2.png', 'wb') as f:
img2 = png.Writer(width=w, height=h, greyscale=False, bitdepth=8)
img2.write(f, data)
kali上运行
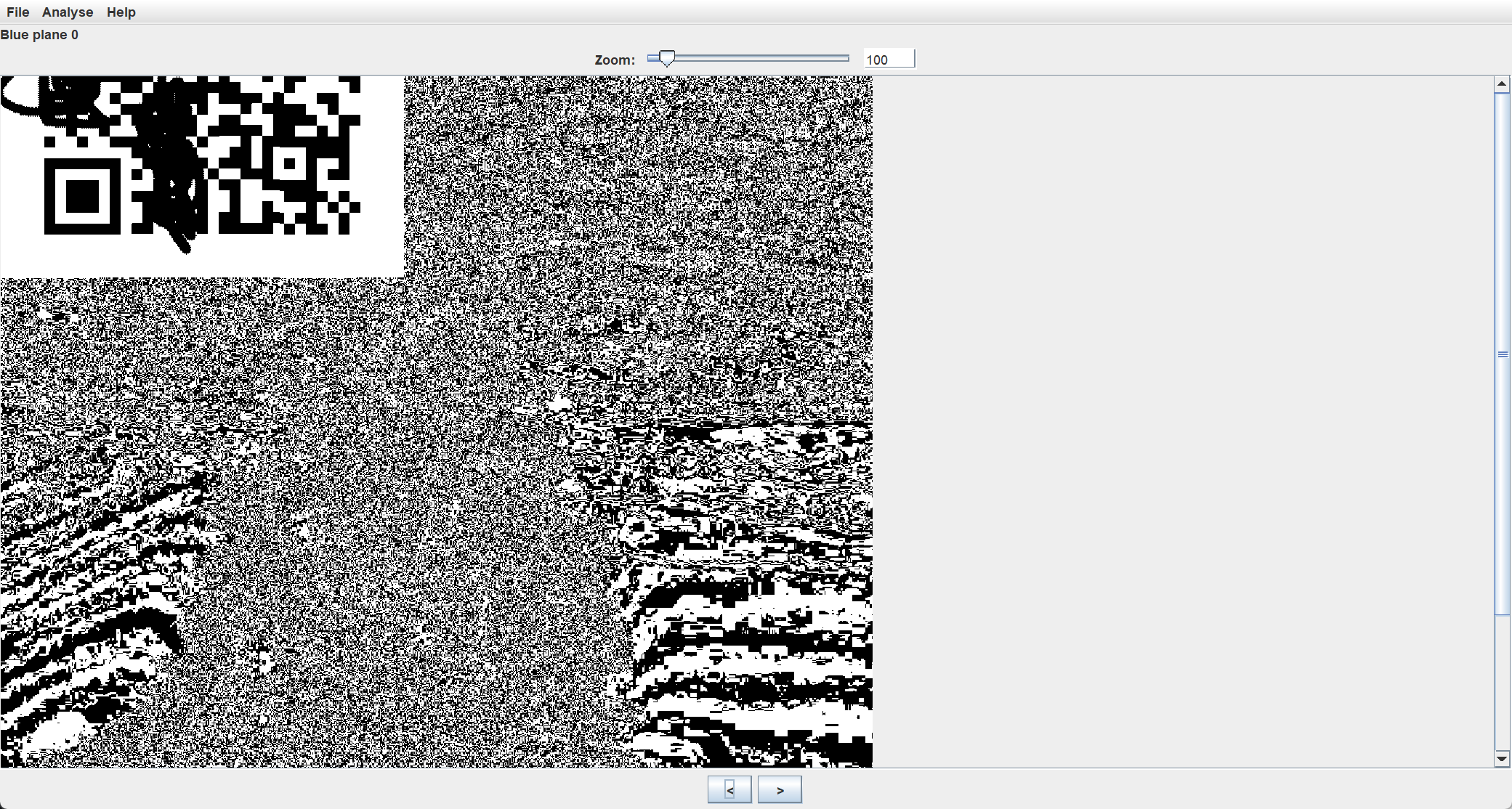
再用stegsolve打开生成的front2.png,在Blue plane 0通道发现另一半二维码:
将两张二维码进行拼接 553*278



对于这种有涂鸦的:QRazyBox----https://merri.cx/qrazybox/

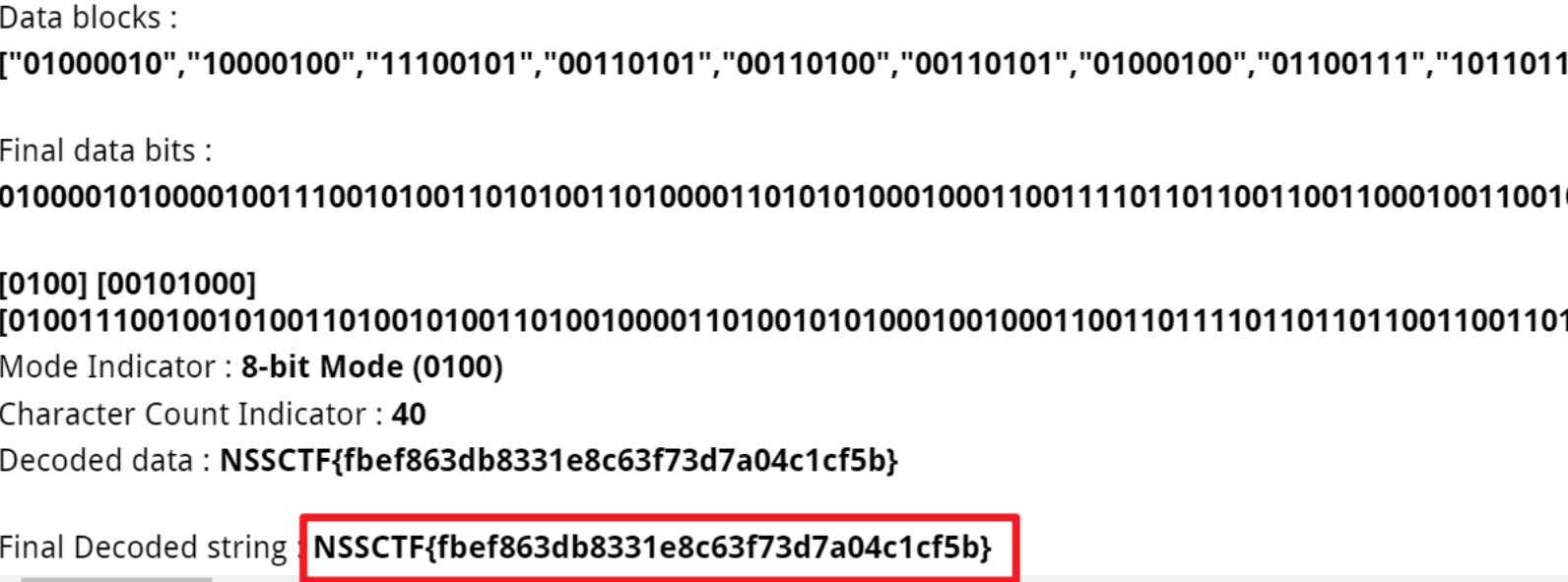
NSSCTF{fbef863db8331e8c63f73d7a04c1cf5b}
[NSSRound#4 SWPU]Type Message
附件---D.wav、F.wav、M.wav、T.wav
通过dtmf2num解密:
D:\32.漏洞学习\misc\工具\音频隐写\dtmf2num>dtmf2num.exe F.wav
DTMF2NUM 0.2
by Luigi Auriemma
e-mail: aluigi@autistici.org
web: aluigi.org
- open F.wav
wave size 89600
format tag 1
channels: 1
samples/sec: 16000
avg/bytes/sec: 32000
block align: 2
bits: 16
samples: 44800
bias adjust: 1
volume peaks: -32766 32766
normalize: 1
resampling to: 8000hz
- MF numbers: 7447
- DTMF numbers: 322217493
D:\32.漏洞学习\misc\工具\音频隐写\dtmf2num>dtmf2num.exe M.wav
DTMF2NUM 0.2
by Luigi Auriemma
e-mail: aluigi@autistici.org
web: aluigi.org
- open M.wav
wave size 134400
format tag 1
channels: 1
samples/sec: 16000
avg/bytes/sec: 32000
block align: 2
bits: 16
samples: 67200
bias adjust: 0
volume peaks: -32764 32765
normalize: 2
resampling to: 8000hz
- MF numbers: 7744777
- DTMF numbers: 7333221535393
D:\32.漏洞学习\misc\工具\音频隐写\dtmf2num>dtmf2num.exe T.wav
DTMF2NUM 0.2
by Luigi Auriemma
e-mail: aluigi@autistici.org
web: aluigi.org
- open T.wav
wave size 134400
format tag 1
channels: 1
samples/sec: 16000
avg/bytes/sec: 32000
block align: 2
bits: 16
samples: 67200
bias adjust: -2
volume peaks: -32765 32764
normalize: 3
resampling to: 8000hz
- MF numbers: 7777
- DTMF numbers: 3118161334374
即
627474238133
322217493
7333221535393
3118161334374
实际上是:(第3位是多余的)
627474238133
32217493
733221535393
318161334374
其他WP提到的网站:http://dialabc.com/sound/detect/index.html
发现是手机键盘:
62 74 74 23 81 33 NSSCTF
32 21 74 93 EASY
73 32 21 53 53 93 REALLY
31 81 61 33 43 74 DTMFIS
即NSSCTF{DTMFISREALLYEASY}
[西湖论剑 2022]mp3
附件---cipher.mp3
foremost后得到一张png
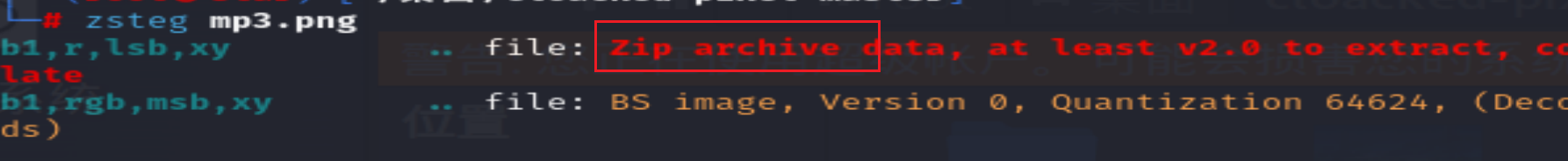
然后使用zsteg:
zsteg mp3.png # 发现有
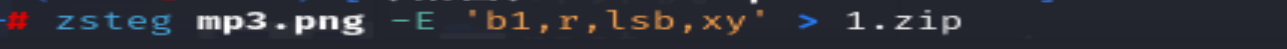
zsteg mp3.png -E 'b1,r,lsb,xy' > 1.zip # 提取压缩包
获得1.zip,但需要密码
使用MP3Stego解密(默认无密码即可),获得cipher.mp3.txt
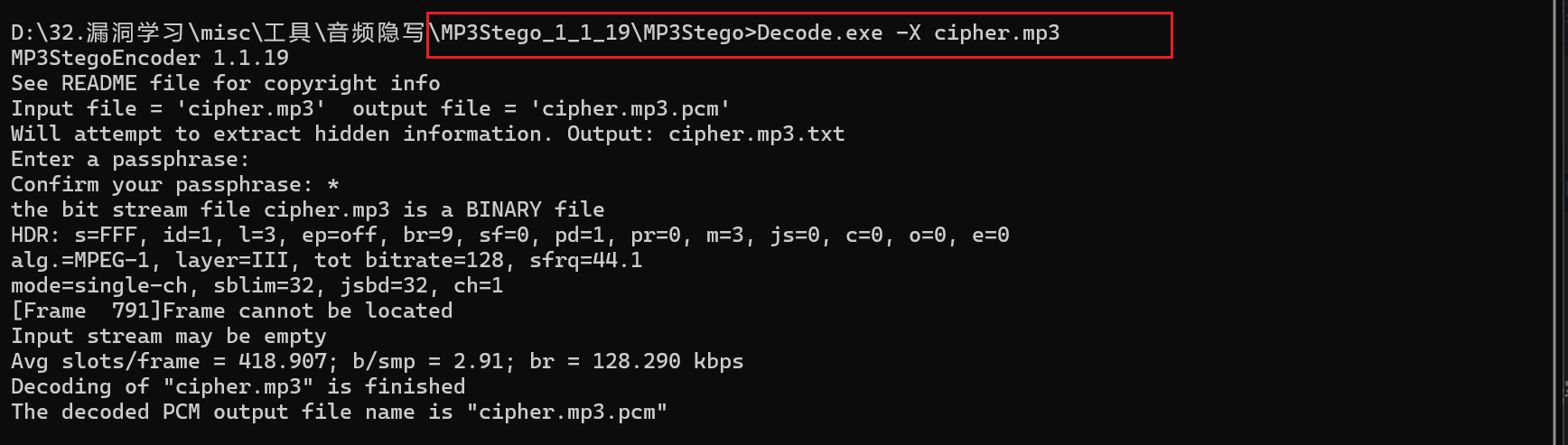
cipher.mp3.txt:
8750d5109208213f
用此密码去解压缩zip得47.txt
47.txt:
2lO,.j2lL000iZZ2[2222iWP,.ZQQX,2.[002iZZ2[2020iWP,.ZQQX,2.[020iZZ2[2022iWLNZQQX,2.[2202iW2,2.ZQQX,2.[022iZZ2[2220iWPQQZQQX,2.[200iZZ2[202iZZ2[2200iWLNZQQX,2.[220iZZ2[222iZZ2[2000iZZ2[2002iZZ2Nj2]20lW2]20l2ZQQX,2]202.ZW2]02l2]20,2]002.XZW2]22lW2]2ZQQX,2]002.XZWWP2XZQQX,2]022.ZW2]00l2]20,2]220.XZW2]2lWPQQZQQX,2]002.XZW2]0lWPQQZQQX,2]020.XZ2]20,2]202.Z2]00Z2]02Z2]2j2]22l2]2ZWPQQZQQX,2]022.Z2]00Z2]0Z2]2Z2]22j2]2lW2]000X,2]20.,2]20.j2]2W2]2W2]22ZQ-QQZ2]2020ZWP,.ZQQX,2]020.Z2]2220ZQ--QZ2]002Z2]220Z2]020Z2]00ZQW---Q--QZ2]002Z2]000Z2]200ZQ--QZ2]002Z2]000Z2]002ZQ--QZ2]002Z2]020Z2]022ZQ--QZ2]002Z2]000Z2]022ZQ--QZ2]002Z2]020Z2]200ZQ--QZ2]002Z2]000Z2]220ZQLQZ2]2222Z2]2000Z2]000Z2]2002Z2]222Z2]020Z2]202Z2]222Z2]2202Z2]220Z2]2002Z2]2002Z2]2202Z2]222Z2]2222Z2]2202Z2]2022Z2]2020Z2]222Z2]2220Z2]2002Z2]222Z2]2020Z2]002Z2]202Z2]2200Z2]200Z2]2222Z2]2002Z2]200Z2]2022Z2]200ZQN---Q--QZ2]200Z2]000ZQXjQZQ-QQXWXXWXj
由众多相同的数字字母,猜测是需要rot
经尝试,rot47后得到:
a=~[];a={___:++a,aaaa:(![]+"")[a],__a:++a,a_a_:(![]+"")[a],_a_:++a,a_aa:({}+"")[a],aa_a:(a[a]+"")[a],_aa:++a,aaa_:(!""+"")[a],a__:++a,a_a:++a,aa__:({}+"")[a],aa_:++a,aaa:++a,a___:++a,a__a:++a};a.a_=(a.a_=a+"")[a.a_a]+(a._a=a.a_[a.__a])+(a.aa=(a.a+"")[a.__a])+((!a)+"")[a._aa]+(a.__=a.a_[a.aa_])+(a.a=(!""+"")[a.__a])+(a._=(!""+"")[a._a_])+a.a_[a.a_a]+a.__+a._a+a.a;a.aa=a.a+(!""+"")[a._aa]+a.__+a._+a.a+a.aa;a.a=(a.___)[a.a_][a.a_];a.a(a.a(a.aa+"\""+a.a_a_+(![]+"")[a._a_]+a.aaa_+"\\"+a.__a+a.aa_+a._a_+a.__+"(\\\"\\"+a.__a+a.___+a.a__+"\\"+a.__a+a.___+a.__a+"\\"+a.__a+a._a_+a._aa+"\\"+a.__a+a.___+a._aa+"\\"+a.__a+a._a_+a.a__+"\\"+a.__a+a.___+a.aa_+"{"+a.aaaa+a.a___+a.___+a.a__a+a.aaa+a._a_+a.a_a+a.aaa+a.aa_a+a.aa_+a.a__a+a.a__a+a.aa_a+a.aaa+a.aaaa+a.aa_a+a.a_aa+a.a_a_+a.aaa+a.aaa_+a.a__a+a.aaa+a.a_a_+a.__a+a.a_a+a.aa__+a.a__+a.aaaa+a.a__a+a.a__+a.a_aa+a.a__+"}\\\"\\"+a.a__+a.___+");"+"\"")())();
放到控制台运行即可得DASCTF{f8097257d699d7fdba7e97a15c4f94b4}
[GKCTF 2021]excel骚操作
附件---flag.xlsx
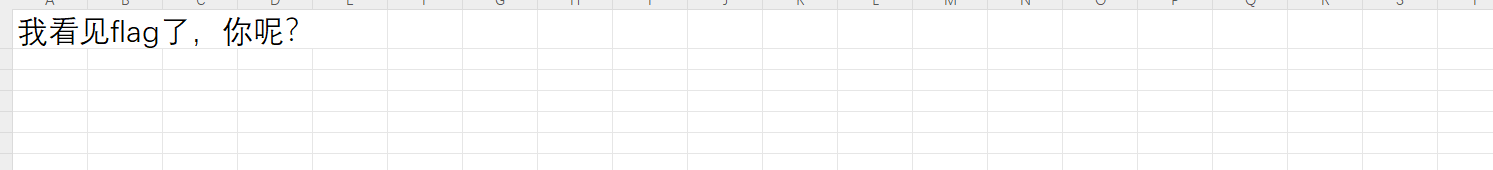
随便点几个单元格发现有些单元格为1,有些为空:
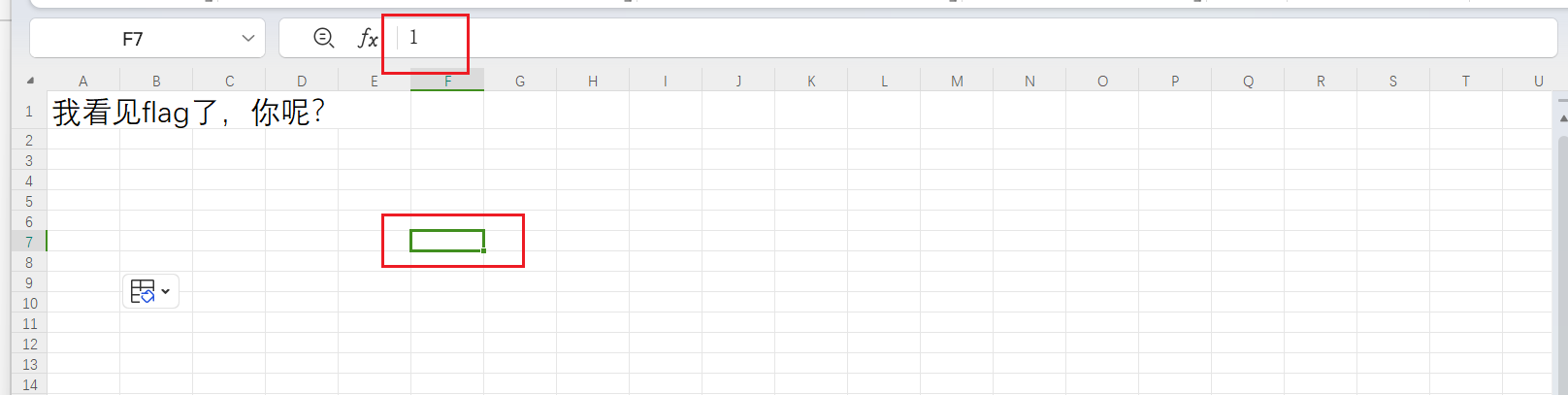
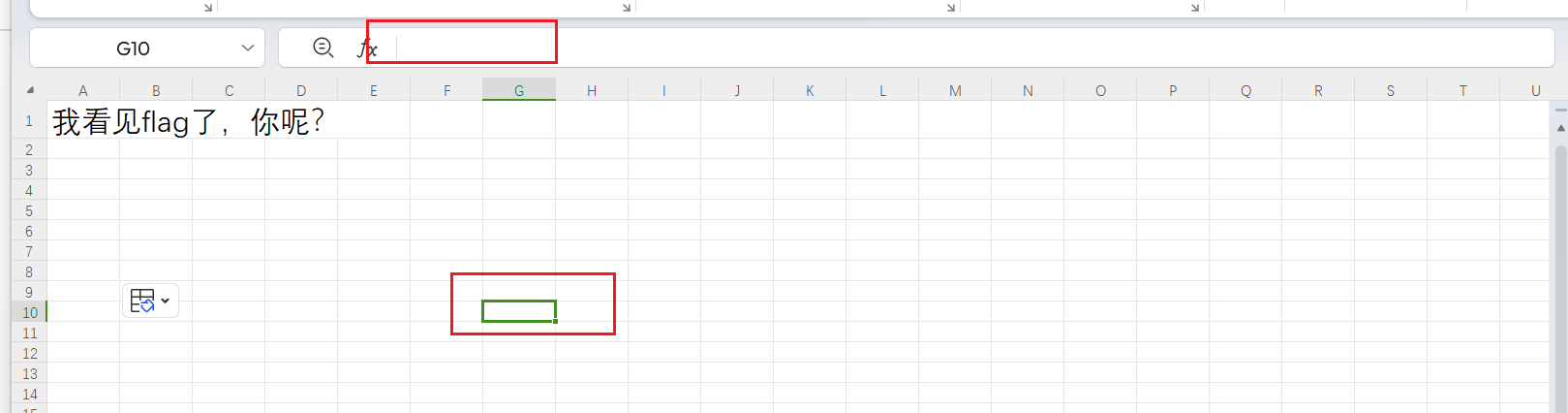
选中一个有1的单元格后进行替换:
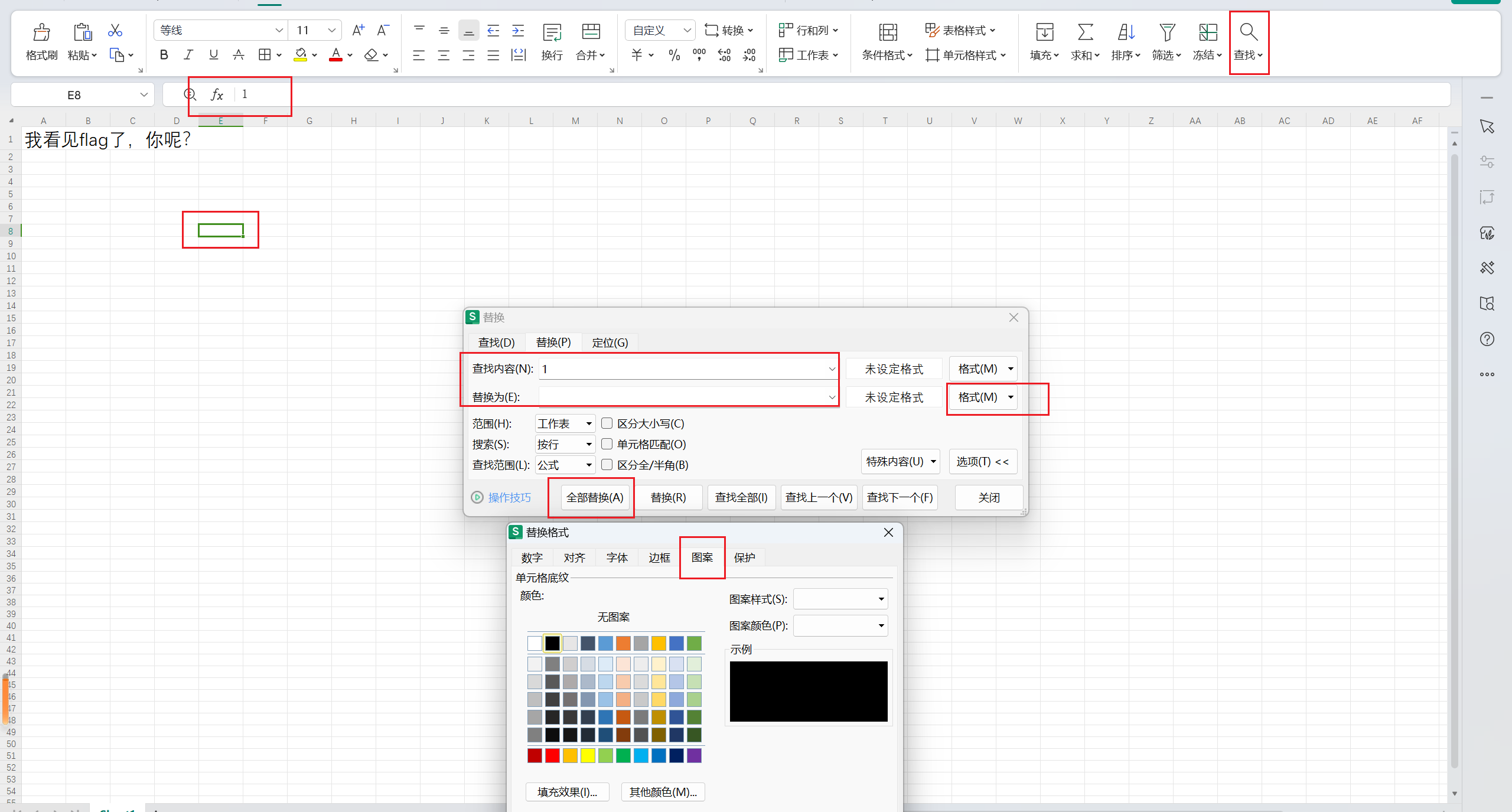
生成:
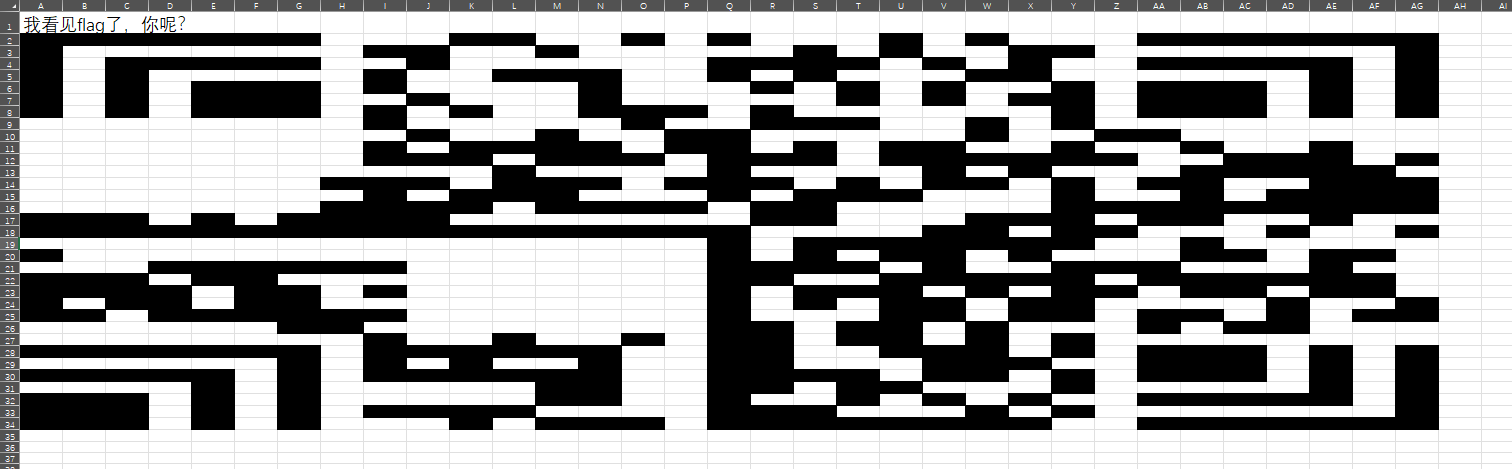
修改列宽:

长得有些奇怪的二维码---汉信码
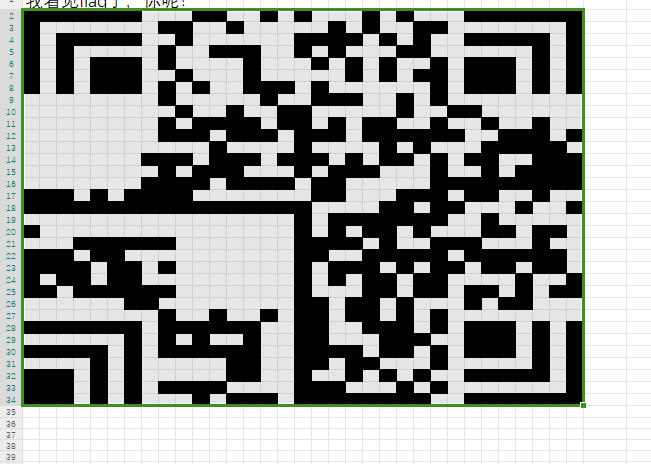
在线汉信码识别:https://tuzim.net/hxdecode/



【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】凌霞软件回馈社区,博客园 & 1Panel & Halo 联合会员上线
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】博客园社区专享云产品让利特惠,阿里云新客6.5折上折
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步