MISC刷题9
[MoeCTF 2022]cccrrc
题目提示crc爆破
下载得到cccccrc.zip,有密码
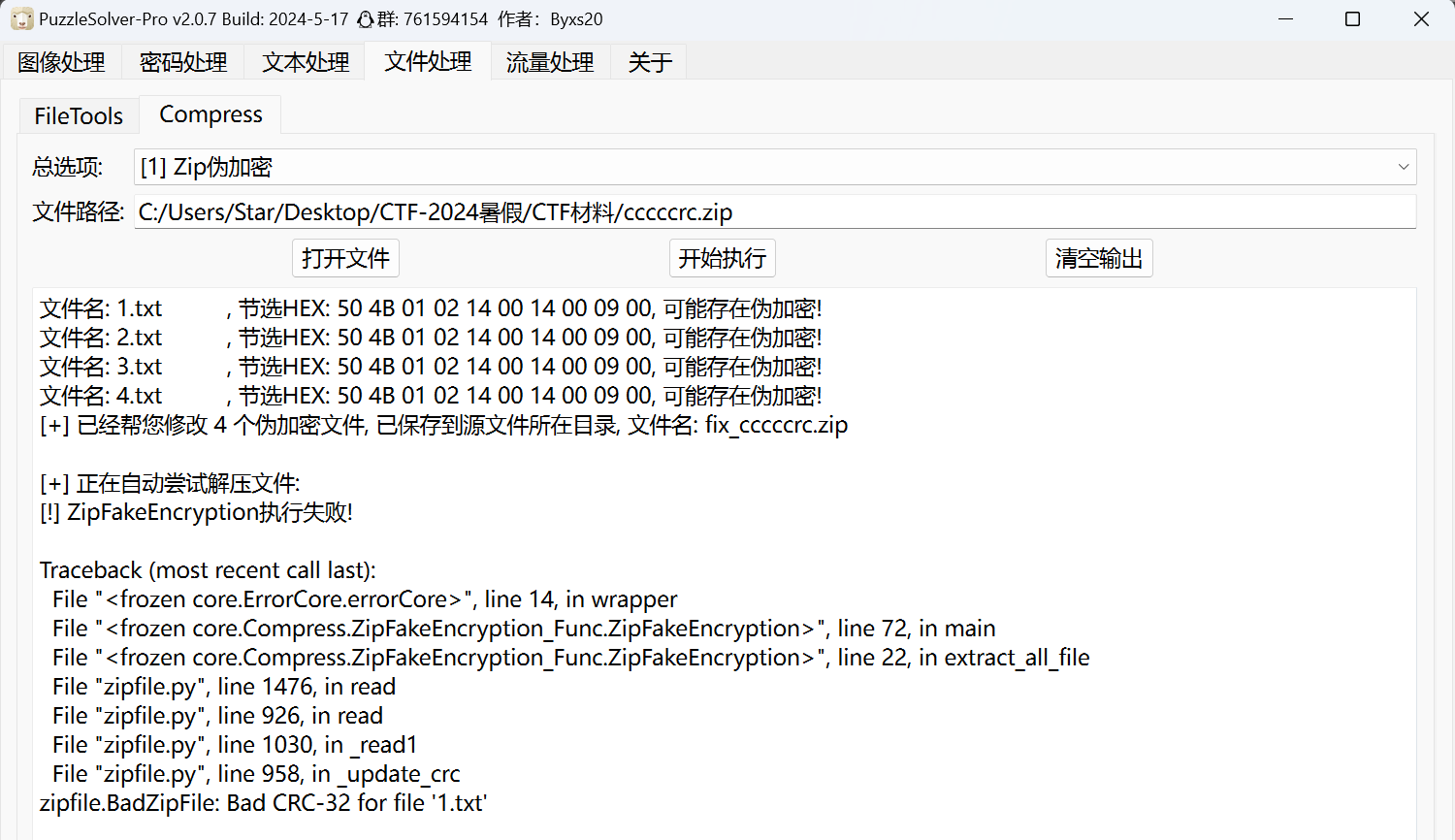
出现报错
使用末初大佬脚本:https://blog.csdn.net/mochu7777777/article/details/110206427
import binascii
import string
def crack_crc():
print('-------------Start Crack CRC-------------')
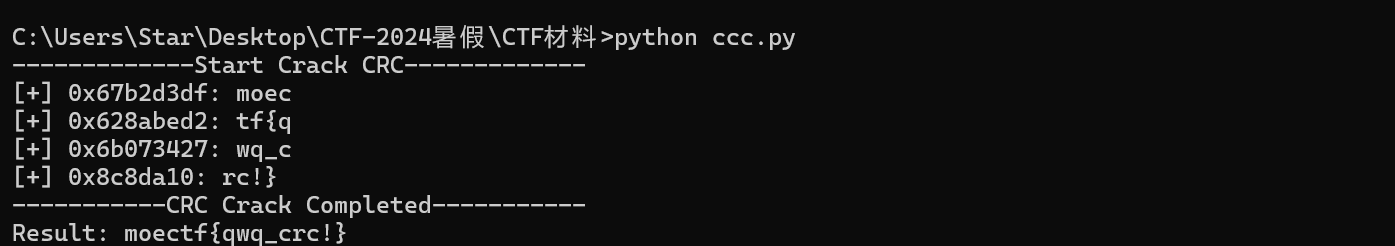
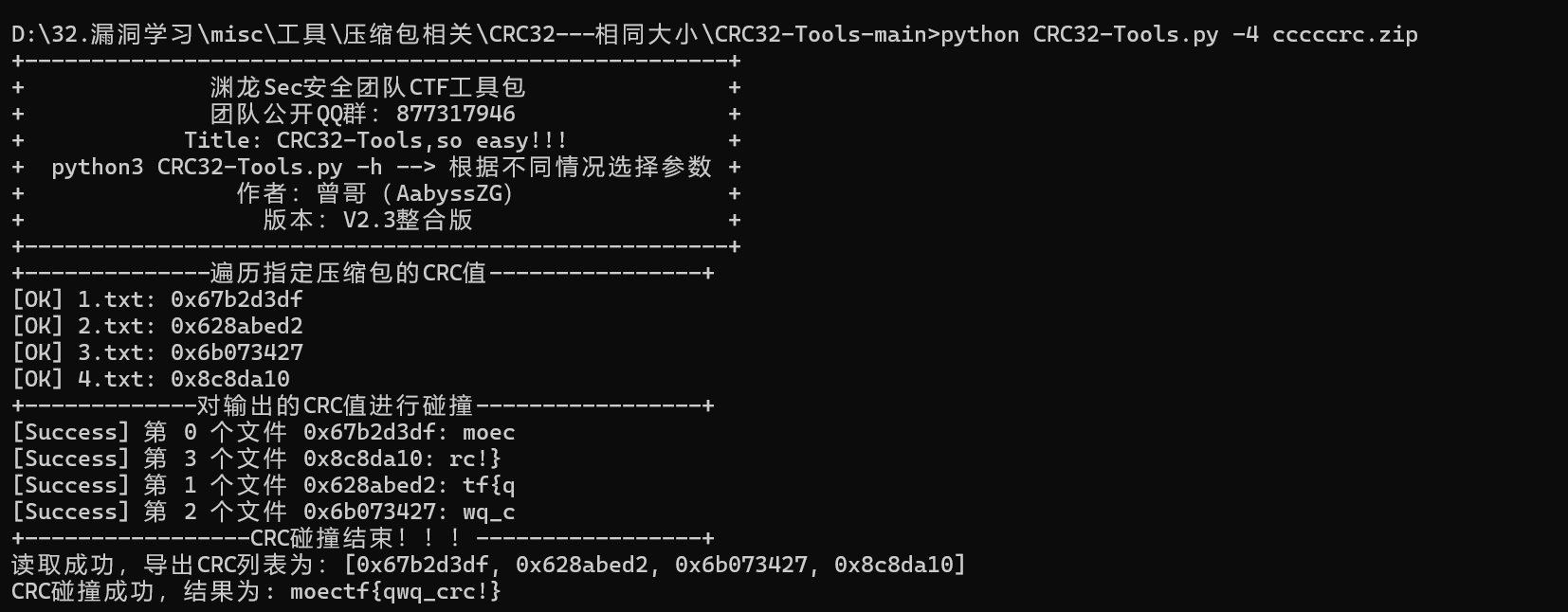
crc_list = [0xc0a3a573, 0x3cb6ab1c, 0x85bb0ad4, 0xf4fde00b]#文件的CRC32值列表,注意顺序
comment = ''
chars = string.printable
for crc_value in crc_list:
for char1 in chars:
for char2 in chars:
for char3 in chars:
for char4 in chars:
res_char = char1 + char2 + char3 + char4#获取遍历的任意4Byte字符
char_crc = binascii.crc32(res_char.encode())#获取遍历字符的CRC32值
calc_crc = char_crc & 0xffffffff#将遍历的字符的CRC32值与0xffffffff进行与运算
if calc_crc == crc_value:#将获取字符的CRC32值与每个文件的CRC32值进行匹配
print('[+] {}: {}'.format(hex(crc_value),res_char))
comment += res_char
print('-----------CRC Crack Completed-----------')
print('Result: {}'.format(comment))
if __name__ == '__main__':
crack_crc()
最终可得:
[GKCTF 2021]你知道apng吗
下载得到:girl.apng
用浏览器将其打开,打开后的效果有点像gif,是动态的
使用工具将其分为静态的几张图片:http://www.downcc.com/soft/40902.html
有几张图有明显二维码:
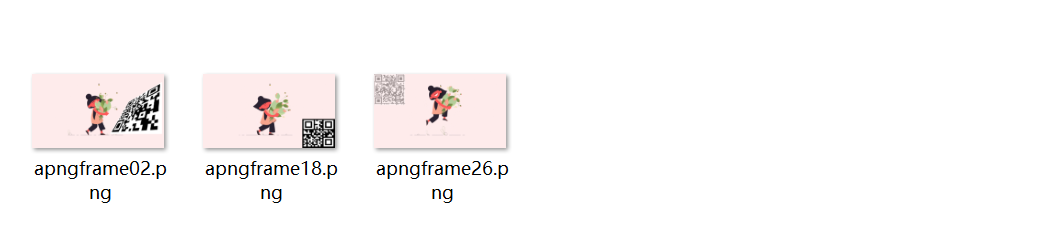


还有个需要用ps扭曲一下二维码:
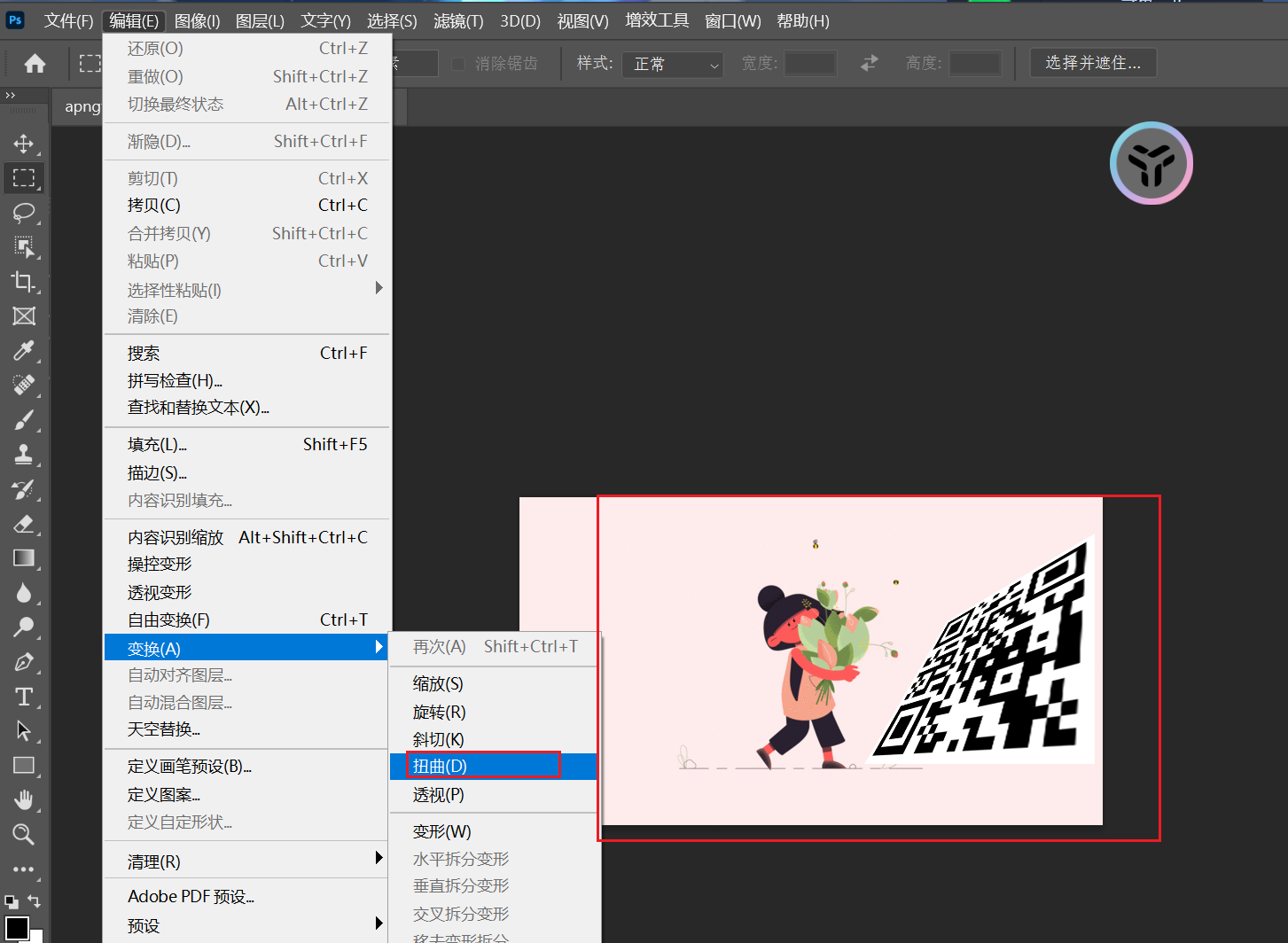
调整一下,然后QR识别即可
还有一个要用stegsolve:

QR扫描
最后拼接为 flag{a3c7e4e5-9b9d-ad20-0327-288a235370ea}
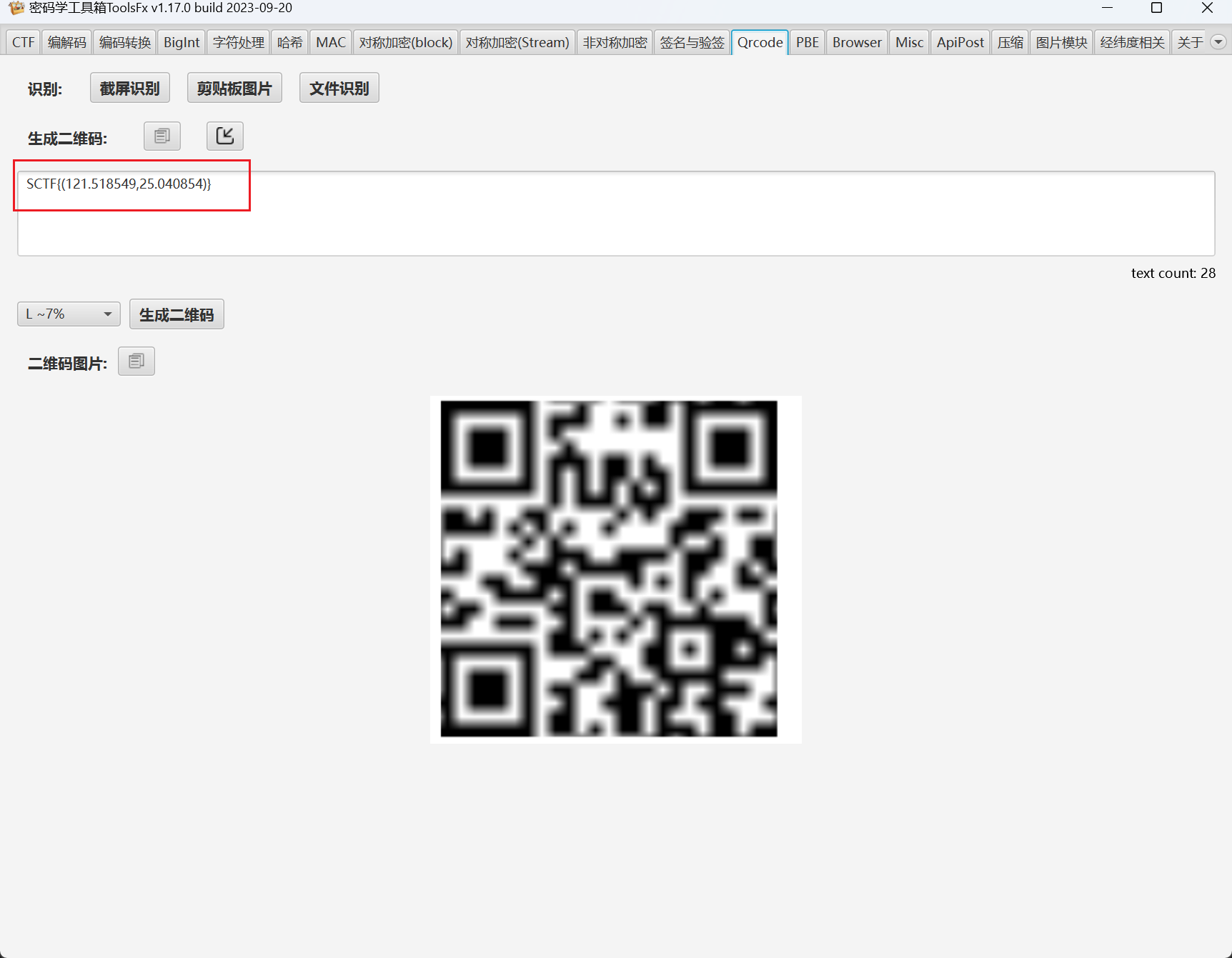
[SCTF 2014]misc400
下载得到附件--sctf.png
思路:
- 宽高改写
- lsb隐写
- 010
- exif信息查看
- binwalk
binwalk sctf.png
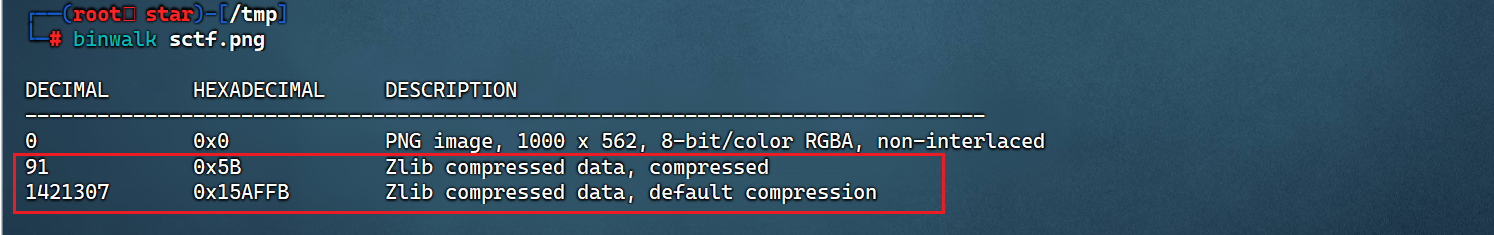
发现存在两个数据块
应该是数据块出现了人为的修改
然后使用pngcheck
https://github.com/wkliu19/pngcheck
make -f Makefile.unx cp pngcheck /usr/local/bin/pngcheck然后就可以在任意目录下执行pngcheck命令了
pngcheck -v sctf.png
详细查看每个数据块的情况
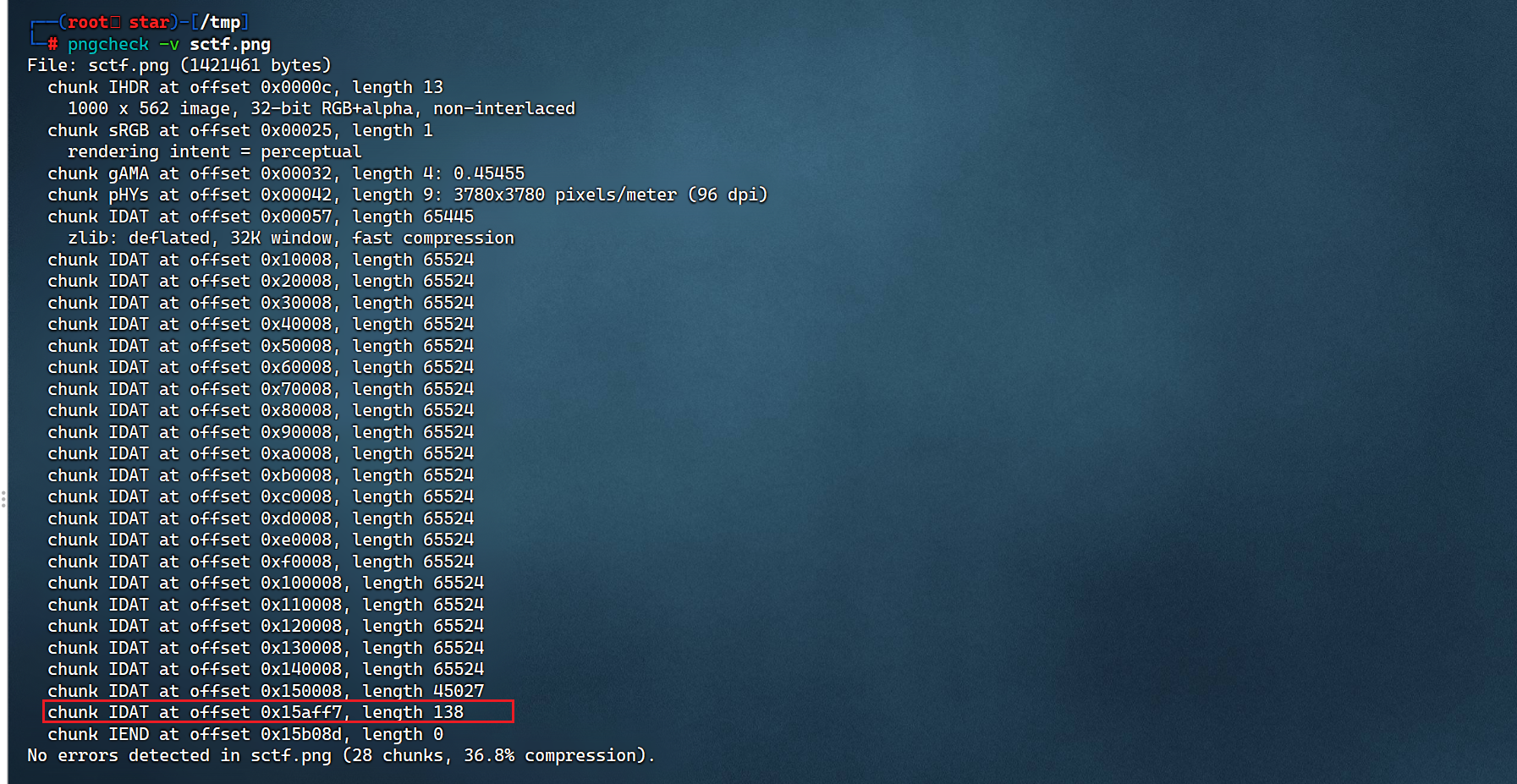
发现最后的数据块没有填满(45027没到65524),之后又出现了138字节,证明是人为添加了数据块
接下来分离sctf.png,查看IDAT的数据块:
binwalk -e sctf.png --run-as=root
查看较小的文件,发现15AFFB文件中有二进制: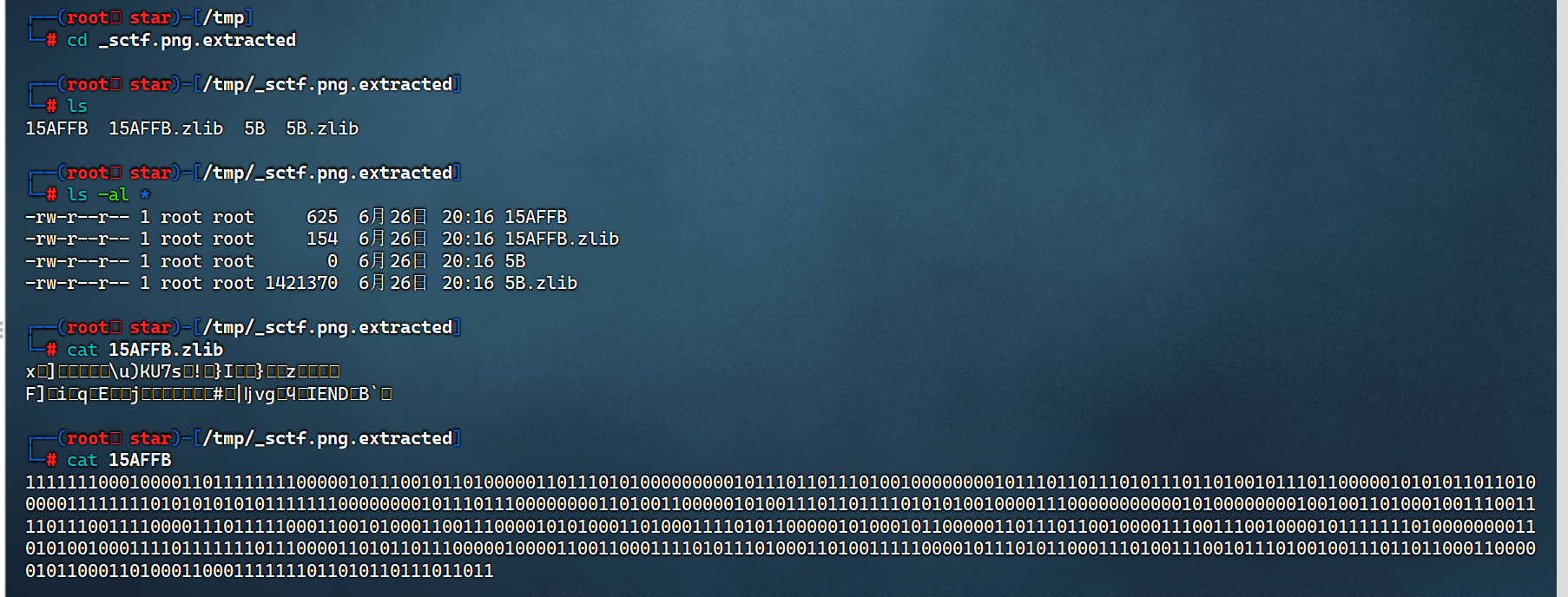
1111111000100001101111111100000101110010110100000110111010100000000010111011011101001000000001011101101110101110110100101110110000010101011011010000011111111010101010101111111000000001011101110000000011010011000001010011101101111010101001000011100000000000101000000001001001101000100111001111011100111100001110111110001100101000110011100001010100011010001111010110000010100010110000011011101100100001110011100100001011111110100000000110101001000111101111111011100001101011011100000100001100110001111010111010001101001111100001011101011000111010011100101110100100111011011000110000010110001101000110001111111011010110111011011
猜测有可能是01转二维码
脚本:
from PIL import Image
MAX = 25
pic = Image.new("RGB", (MAX, MAX))
str = "1111111000100001101111111100000101110010110100000110111010100000000010111011011101001000000001011101101110101110110100101110110000010101011011010000011111111010101010101111111000000001011101110000000011010011000001010011101101111010101001000011100000000000101000000001001001101000100111001111011100111100001110111110001100101000110011100001010100011010001111010110000010100010110000011011101100100001110011100100001011111110100000000110101001000111101111111011100001101011011100000100001100110001111010111010001101001111100001011101011000111010011100101110100100111011011000110000010110001101000110001111111011010110111011011"
i = 0
for y in range (0,MAX):
for x in range(0, MAX):
if(str[i] == '1'):
pic.putpixel([x,y],(0,0,0))
else:
pic.putpixel([x,y],(255, 255, 255))
i = i+1
pic.show()
pic.save("flag.png")
ToolsFx:



【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· DeepSeek 开源周回顾「GitHub 热点速览」
· 物流快递公司核心技术能力-地址解析分单基础技术分享
· .NET 10首个预览版发布:重大改进与新特性概览!
· AI与.NET技术实操系列(二):开始使用ML.NET
· .NET10 - 预览版1新功能体验(一)