CASB主要厂商分析(一) Bitglass
2020-08-19 15:31 宋海宾 阅读(1006) 评论(0) 编辑 收藏 举报1.厂商列表
Bitglass
CipherCloud
Cisco Cloudlock
Forcepoint CASB
IBM Managed Cloud Services
ManagedMethods
Masergy
McAfee/Skyhigh Security Cloud
Microsoft Cloud App Security
Netskope
Oracle CASB Cloud Service
Palo Alto Networks Aperture
Proofpoint CASB
Symantec/Skycure

CASB看起来即像是上网行为管理+威胁分析+DLP+防火墙+堡垒机+身份认证产品的合集,但它究竟如何部署呢? 总体来说,分为3种部署模式:
- 纯网关型模式。在用户的网络出口处放置一套CASB网关设备,对所有的需要处理的SaaS服务进行代理,相应的移动设备需要配置相关的Profile文件或者安装客户端,使此类SaaS流量也指向CASB网关。
- 控制器+云端能力中心模式。与第一种方案不同之处在于,用户网络内只有一个轻型的控制器用于策略执行。但是对于风险分析、数据加密、安全评估、策略生成、初始化数据格式等工作都在云端完成。而第一种方案中所有工作都有CASB网关完成。
- 客户端+云模式。在所有SaaS终端使用设备上装上CASB客户端APP。
CASB公司,在关注的业务层面既有交叉,也各有不同,都是在SaaS业务的过程中的身份识别、访问权限、操作权限、数据及文件生命周期、数据资产加密、数据迁移、数据备份、以及审查回溯等各个环节提供保护。从技术角度上来看,CASB的实现并不是什么难题,但是如何实现对大量SaaS服务适配,SaaS业务云端历史数据与新数据的全局发现与整理,对SaaS业务过程的无缝干预与用户无感体验,这些工程性问题恰恰是CASB产品的真正难点。
CASB的出现依然是解决身份、控制、审查、防泄密、完整性等这些老生常谈的问题,但是面向的基础架构环境已经从传统盒子堆,变成了云。
1. Bitglass
Bitglass 是一家专注于保护企业数据的云安全初创公司,该公司成立于 2013 年,总部位于加州,现任首席执行官 Nat Kausik 是一位 IT 行业的老兵,曾在 1989-1997 年之间在惠普公司担任首席科学家,之后他创立了一系列初创公司,也获得成功退出。值得一提的是,Nat Kausik 早在 1991 年还著作了一本关于机器学习的书。
官网链接:https://www.bitglass.com/
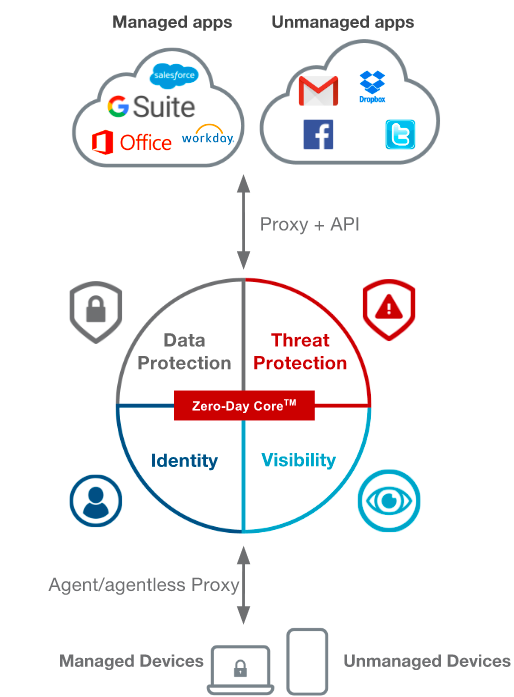
Correspondingly there are three types of CASB
- API-only CASB that deliver only management. Such CASB use API access to SaaS apps to remediate after data-leakage events.
- Multi-mode First-Gen CASB that deliver management and security, but not Zero-Day protection. Such CASB offer signature-based protection for known data leakage paths and a fixed set of applications
- Multi-mode Next-Gen CASB that deliver management, security and Zero-Day protection. Such CASB dynamically adapt to deliver protection for known and unknown data leakage risks and malware threats, on any app.
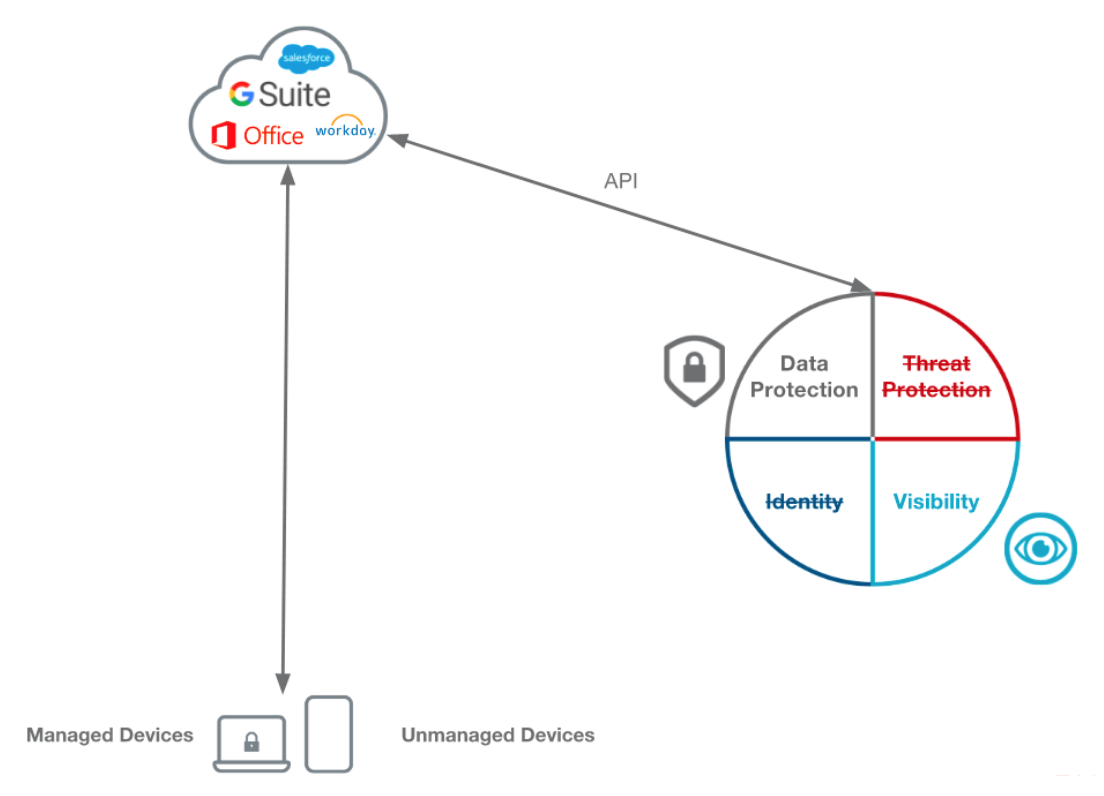
1.1 API-only CASB
API-only CASB offer management capabilities by remediating data-leakage events after the fact via the APIs provided by some applications.
API CASB operate “out-of-band” not real-time. Users directly access cloud apps and data from any device, managed or unmanaged, without restriction or control. API CASB use the applications’ API to analyze the data-at-rest in the cloud. Based on policies set by the administrator, files that are in violation may trigger visibility logging alerts. Alternatively, files that are in violation may be quarantined, or have sharing permissions revoked.
Strengths:- Visibility & DLP remediation on data at rest after breach & compliance violations
Weaknesses:
- No Real-time protection
- No Mobile data protection
- No Threat protection
- No Zero-day App Control
- No Zero-Day threat protection
- No Identity control
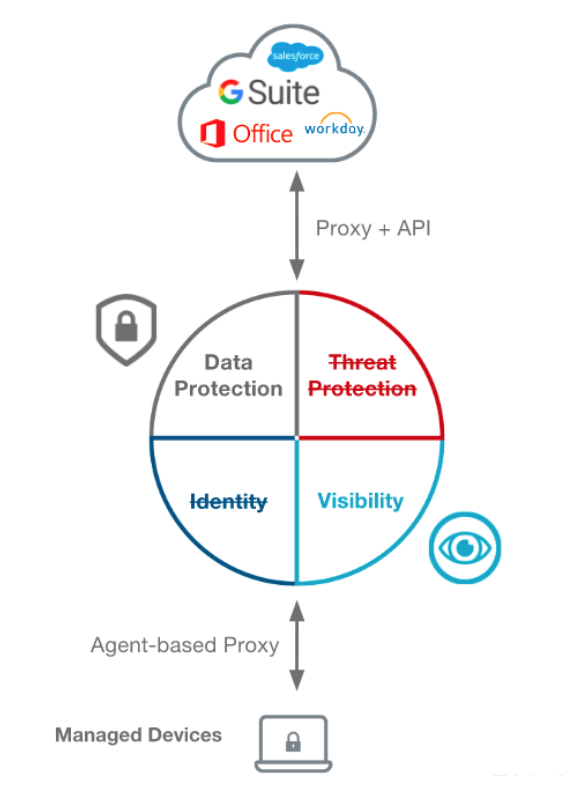
1.2 Multi-mode First-Gen CASB
Mult-mode first-Gen CASB offer both API mode and proxy mode. Operating in proxy mode typically requires an agent on every device, and is not suitable for unmanaged personal devices. Proxy agents may also interfere with existing infrastructure such as Secure Web Gateway proxies. Multi-mode first-gen CASB can also identify “ShadowIT” cloud applications used in the enterprise, by checking against a manually curated index of cloud applications.
Strengths:ShadowIT analysis with manual index
- Requires proxy agents on every device
- No agentless mode
- No Mobile Data Protection
- No Zero-day App Control
- No Zero-Day threat protection
- No Identity control
1.3 Multi-mode Next-Gen CASB
- API+Forward proxy + Reverse-Proxy + Active-Sync Proxy + SAML Proxy
- Zero-Day real-time control of any managed app
- Zero-Day read-only control of any umanaged app
- Zero-Day real-time agentless AJAX-VM on any device
- Zero-Day threat protection
- Searchable, sortable cloud encryption
- Custom app support
- API visibility and control of data-at-rest
- Agentless Mobile security
- Integrated identity control
- Automated ShadowIT Analysis w/ 100K+ apps