第三部分
HTTP工具
1.Burp Suite(1)
Burp Suite is a combination of powerful web application security tools.These tools demonstrate the real-world capabilities of an attacker penetrating the web applications.It can scan,analyze,and exploit the web applications using manual and automated techniques.The integration facility between the interfaces of these tools provides a complete attack platform to share information between one or more tools altogether.This makes the burp Suite a very effective and easy-to-use web application attack framework.(Burp Suite是一个功能强大的web运用安全工具,它能够扫描,分析和攻击web运用,通过手动和自动技术。)
2.Burp Suite(2)
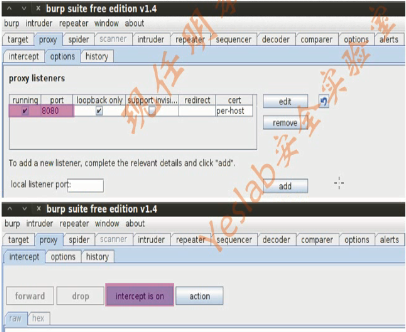

1.Burp Suite(3)

1.Burp Suite(4)

1.Burp Suite(5)
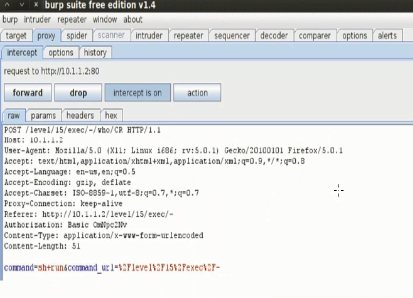
1.Burp Suite(6)
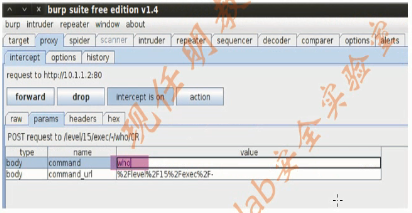
1.Burp Suite(7)
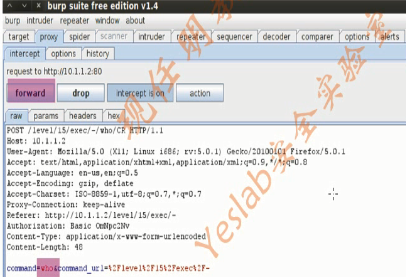
1.Burp Suite(8)
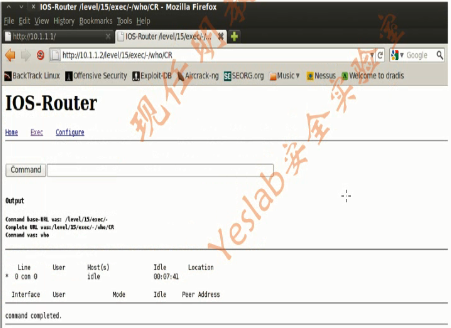
root@bt:~# cd /pentest/web/burpsuite/
root@bt:/pentest/web/burpsuite# java -jar burpsuite_v1.4.jar
Your JRE appears to be OpenJDK.
Burp has not been fully tested on this platform and you may experience problems.
Deleting temporary files - please wait ... done.
2.Grendel Scan(1)
The Grendel Scan is an automated web application Security assessment tool.It scans,detects,and exploits the common web application vulnerabillities and presents the final results in a single comprehensive report.This kind of tool is very useful where the penetration tester is given a short period for an application security testing assignment.(一个自动web运用安全评估工具,它扫描,检测,攻击普通web运用的脆弱性,并且把扫描结果生成一个报告。)

2.Grendel Scan (2)
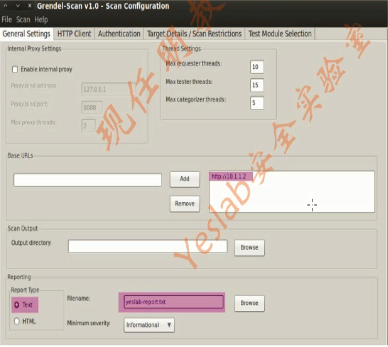
3.Grendel Scan(3)
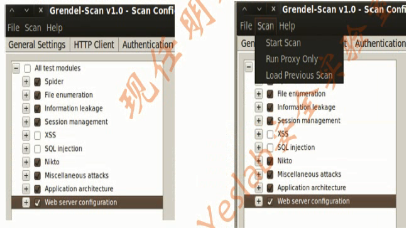
2.Grendel Scan(4)
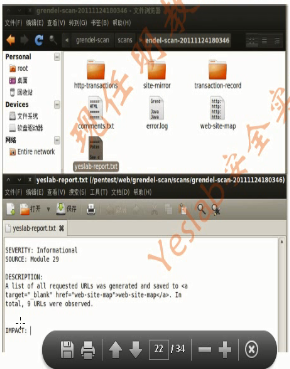
root@bt:~# cd /pentest/web/grendel-scan/
root@bt:/pentest/web/grendel-scan# ./grendel.sh
3.Nikto2
Nikto2is an advanced web server security scanner.It scans and detects the security vulnerabilities caused by server misconfiguration,default and insecure files,and outdated server application.Nikto2 purely buillt on LibWhisker2,and thus supports cross-platform deployment,SSL,host authentication methods (NTLM/Basic),proxies,and serveral IDS evasion techniques,It also support sub-domain enumeration,application security check(XSS,SQL injection,and so on)and is capable of guessing the authorization credentials using the dictionary-based attack method.(Nikto2是一个高级web服务器安全扫描攻击,它扫描并检测,由于服务器配置失误而造成的安全隐患。)
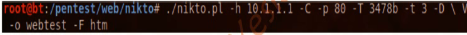
root@bt:/pentest/web# cd nikto/
root@bt:/pentest/web/nikto# ./nikto.pl -h 10.1.1.1 -C -p 80 -T 3478b -t 3 -D \ V-o webtest -F htm
4.W3AF(1)
The W3AF is a feature-rich web application attack and audit framework that aims to detect and exploit the web vulnerabilies.The whole application security assessment process is automated and the framework is designed to follow three major steps,which are discovery,audit,and attack.Each of these steps includes serveral plugins which may help the auditor to focus on specific testing criteria,All these plugins can communicate and share test data in order to achieve the required goal.It supports the detection and exploitation of multiple web application vulnerabilities including SQL injection,cross-site scripting,remote and local file inclusion,buffer overflows,XPath injections,OS commanding,application misconfiguration,and so on.To get more information about each available plugin,go to:http://w3af.sourceforge.net/plugin-descriptions.php.(W3AF是一个特性丰富的web运用攻击和审计的框架,他协助检测和攻击web的脆弱性。)
4.W3AF(2)

root@bt:~# cd /pentest/web/w3af/
root@bt:/pentest/web/w3af# ./w3af_console
w3af>>> plugins
w3af/plugins>>> help
|-----------------------------------------------------------------------------|
| list | List available plugins. |
|-----------------------------------------------------------------------------|
| back | Go to the previous menu. |
| exit | Exit w3af. |
| assert | Check assertion. |
|-----------------------------------------------------------------------------|
| grep | View, configure and enable grep plugins |
| output | View, configure and enable output plugins |
| audit | View, configure and enable audit plugins |
| discovery | View, configure and enable discovery plugins |
| bruteforce | View, configure and enable bruteforce plugins |
| evasion | View, configure and enable evasion plugins |
| mangle | View, configure and enable mangle plugins |
|-----------------------------------------------------------------------------|
w3af/plugins>>> output
|----------------------------------------------------------------------------|
| Plugin name | Status | Conf | Description |
|----------------------------------------------------------------------------|
| console | Enabled | Yes | Print messages to the console. |
| emailReport | | Yes | Email report to specified addresses. |
| gtkOutput | | | Saves messages to |
| | | | kb.kb.getData('gtkOutput', 'queue'), |
| | | | messages are saved in the form of objects. |
| htmlFile | | Yes | Print all messages to a HTML file. |
| textFile | | Yes | Prints all messages to a text file. |
| xmlFile | | Yes | Print all messages to a xml file. |
|----------------------------------------------------------------------------|
w3af/plugins>>> output console htmlFile
w3af/plugins>>> output config htmlFile
w3af/plugins/output/config:htmlFile>>> help
|-----------------------------------------------------------------------------|
| view | List the available options and their values. |
| set | Set a parameter value. |
|-----------------------------------------------------------------------------|
| back | Go to the previous menu. |
| exit | Exit w3af. |
| assert | Check assertion. |
|-----------------------------------------------------------------------------|
w3af/plugins/output/config:htmlFile>>> view
|-----------------------------------------------------------------------------|
| Setting | Value | Description |
|-----------------------------------------------------------------------------|
| verbose | False | True if debug information will be appended to the |
| | | report. |
| fileName | report.html | File name where this plugin will write to |
|-----------------------------------------------------------------------------|
w3af/plugins/output/config:htmlFile>>> set verbose True
w3af/plugins/output/config:htmlFile>>> set fileName testreport.html
w3af/plugins/output/config:htmlFile>>> back
w3af/plugins>>> output config console
w3af/plugins/output/config:console>>> help
|-----------------------------------------------------------------------------|
| view | List the available options and their values. |
| set | Set a parameter value. |
|-----------------------------------------------------------------------------|
| back | Go to the previous menu. |
| exit | Exit w3af. |
| assert | Check assertion. |
|-----------------------------------------------------------------------------|
w3af/plugins/output/config:console>>> help
|-----------------------------------------------------------------------------|
| view | List the available options and their values. |
| set | Set a parameter value. |
|-----------------------------------------------------------------------------|
| back | Go to the previous menu. |
| exit | Exit w3af. |
| assert | Check assertion. |
|-----------------------------------------------------------------------------|
w3af/plugins/output/config:console>>> view
|----------------------------------------------------------------------------|
| Setting | Value | Description |
|----------------------------------------------------------------------------|
| verbose | False | Enable if verbose output is needed |
|----------------------------------------------------------------------------|
af/plugins/output/config:console>>> set verbose False
w3af/plugins/output/config:console>>> back
4.W3AF(3)


w3af/plugins>>> audit
|----------------------------------------------------------------------------|
| Plugin name | Status | Conf | Description |
|----------------------------------------------------------------------------|
| LDAPi | | | Find LDAP injection bugs. |
| blindSqli | | Yes | Find blind SQL injection |
| | | | vulnerabilities. |
| buffOverflow | | | Find buffer overflow vulnerabilities. |
| dav | | | Verify if the WebDAV module is |
| | | | properly configured. |
| eval | | Yes | Find insecure eval() usage. |
| fileUpload | | Yes | Uploads a file and then searches for |
| | | | the file inside all known directories. |
| formatString | | | Find format string vulnerabilities. |
| frontpage | | Yes | Tries to upload a file using frontpage |
| | | | extensions (author.dll). |
| generic | | Yes | Find all kind of bugs without using a |
| | | | fixed database of errors. |
| globalRedirect | | | Find scripts that redirect the browser |
| | | | to any site. |
| htaccessMethods | | | Find misconfigurations in the |
| | | | "<LIMIT>" configuration of Apache. |
| localFileInclude | | | Find local file inclusion |
| | | | vulnerabilities. |
| mxInjection | | | Find MX injection vulnerabilities. |
| osCommanding | | | Find OS Commanding vulnerabilities. |
| phishingVector | | | Find phishing vectors. |
| preg_replace | | | Find unsafe usage of PHPs |
| | | | preg_replace. |
| redos | | | Find ReDoS vulnerabilities. |
| remoteFileInclude | | Yes | Find remote file inclusion |
| | | | vulnerabilities. |
| responseSplitting | | | Find response splitting |
| | | | vulnerabilities. |
| sqli | | | Find SQL injection bugs. |
| ssi | | | Find server side inclusion |
| | | | vulnerabilities. |
| sslCertificate | | | Check the SSL certificate validity( if |
| | | | https is being used ). |
| unSSL | | | Find out if secure content can also be |
| | | | fetched using http. |
| xpath | | | Find XPATH injection vulnerabilities. |
| xsrf | | | Find the easiest to exploit xsrf |
| | | | vulnerabilities. |
| xss | | Yes | Find cross site scripting |
| | | | vulnerabilities. |
| xst | | | Find Cross Site Tracing |
| | | | vulnerabilities. |
|----------------------------------------------------------------------------|
w3af/plugins>>> audit htaccessMethods,osCommanding,sqli,xss
w3af/plugins>>> back
w3af>>> target
w3af/config:target>>> help
|-----------------------------------------------------------------------------|
| view | List the available options and their values. |
| set | Set a parameter value. |
|-----------------------------------------------------------------------------|
| back | Go to the previous menu. |
| exit | Exit w3af. |
| assert | Check assertion. |
|-----------------------------------------------------------------------------|
w3af/config:target>>> view
|----------------------------------------------------------------------------|
| Setting | Value | Description |
|----------------------------------------------------------------------------|
| targetOS | unknown | Target operating system (unknown/unix/windows) |
| targetFramework | unknown | Target programming framework |
| | | (unknown/php/asp/asp.net/java/jsp/cfm/ruby/perl) |
| target | | A comma separated list of URLs |
|----------------------------------------------------------------------------|
w3af/config:target>>> set target http://10.1.1.1/
w3af/config:target>>> back
w3af>>> start
5.WAFW00F
The WafW00f is a very useful python script capable of detecting the web application firewall (WAF).This tool is particularly useful where the penertration tester wants to inspect the target application server and may get fallback with certain vulnerability assessment techniques for which the web application is actively protected by frewall.Thus,detecting the frewall sitting in between an application server and internet traffic not only improves the testing strategy but also puts exceptional challenges for the penetration tester to develop the advance evasion techniques.(WAFW00F是一个用来探测WAF的工具)
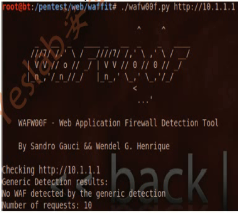
root@bt:~# cd /pentest/web/waffit/
root@bt:/pentest/web/waffit# ./wafw00f.py http://10.1.1.1
^ ^
_ __ _ ____ _ __ _ _ ____
///7/ /.' \ / __////7/ /,' \ ,' \ / __/
| V V // o // _/ | V V // 0 // 0 // _/
|_n_,'/_n_//_/ |_n_,' \_,' \_,'/_/
<
...'
WAFW00F - Web Application Firewall Detection Tool
By Sandro Gauci && Wendel G. Henrique
Checking http://10.1.1.1
Generic Detection results:
No WAF detected by the generic detection
Number of requests: 10



