3.漏洞发现


内容简介
第一部分:Cisco工具
第二部分:SNMP工具
第三部分:HTTP工具
第四部分:SMB工具
第五部分:综合漏洞发现工具Nessus
第一部分
Cisco工具
Cisco工具
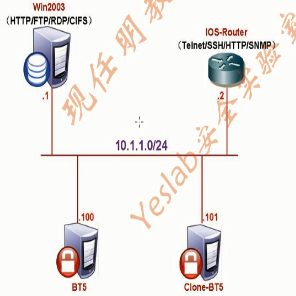
拓扑介绍

1.Cisco Auditing Tool
Cisco Auditing Tool(CAT) is a mini security auditing tool.It scans the Cisco routers for common vulnerabilities such as default passwords,SNMP community strings,and some old IOS bugs.(一个很小的安全审计工具,它扫描Cisco路由器的一般性漏洞,录入默认密码,SNMP Community字串和一些老的IOS bug)

root@bt:~# cd /pentest/cisco/cisco-auditing-tool/
root@bt:/pentest/cisco/cisco-auditing-tool# ls
CAT lib lists plugins TODO
root@bt:/pentest/cisco/cisco-auditing-tool# cd lists/
root@bt:/pentest/cisco/cisco-auditing-tool/lists# ls
community passwords
root@bt:/pentest/cisco/cisco-auditing-tool/lists# vim community
list
public
private
root@bt:/pentest/cisco/cisco-auditing-tool/lists# vim passwords
list
cisco1
cisco
smoke
root@bt:/pentest/cisco/cisco-auditing-tool# ./CAT -h
Cisco Auditing Tool - g0ne [null0]
Usage:
-h hostname (for scanning single hosts)
-f hostfile (for scanning multiple hosts)
-p port # (default port is 23)
-w wordlist (wordlist for community name guessing)
-a passlist (wordlist for password guessing)
-i [ioshist] (Check for IOS History bug)
-l logfile (file to log to, default screen)
-q quiet mode (no screen output)
root@bt:/pentest/cisco/cisco-auditing-tool# ./CAT -h 10.1.1.2 -w lists/community -a lists/passwords -i
2.Cisco Passwd Scanner
The Cisco Passwd Scanner has been developed to scan the whole bunch of IP addresses in a specific network class.This class can be represented an A,B or C in terms of netowrk computing.Each class has it own defintion for a number of hosts to be scanned.The tool is much faster and efficient in handling multiple threads in a single instance.It discovers those Cisco devices carrying default telnet password "cisco".(这个工具用于发现拥有默认telnet密码"cisco"的Cisco设备,这个工具非常快并且有效。)
./ciscos <ip network> <class> <options> we can easily scan the whole class of IP network. IN our exercise we will be using two available options,-t<connection timeout value in seconds> and -C <maximum connection threads> in order to optimize the test execution process.(命令格式介绍)

root@bt:~# cd /pentest/cisco/ciscos/
root@bt:/pentest/cisco/ciscos# ./ciscos 10.1.1 3 -t 4 -C 10
Cisco Scanner v1.3
Scanning: 10.1.1.*
output:cisco.txt
threads:10
timeout:4
第二部分
SNMP工具
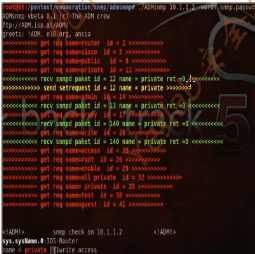
1.ADMsnmp
The ADMSnmp is a very handful audit scanner.It can brute force the SNMP community strings with a predefined set of wordlist or make guess based on the given hostname.It will scan the host for valid community strings and then check each of those valid community names for read and write access permissions to MIBs.(ADMSnmp用于暴力破解SNMP community字串,使用一个预先定义的"wordlist".)

root@bt:~# cd /pentest/enumeration/snmp/admsnmp/
root@bt:/pentest/enumeration/snmp/admsnmp# ./ADMsnmp
ADMsnmp v 0.1 (c) The ADM crew
./ADMsnmp: <host> [-g,-wordf,-out <name>, [-waitf,-sleep, -manysend,-inter <#>] ]
<hostname> : host to scan
[-guessname] : guess password with hostname
[-wordfile] : wordlist of password to try
[-outputfile] <name>: output file
[-waitfor] <mili> : time in milisecond in each send of snmprequest
[-sleep] <second> : time in second of the scan process life
[-manysend] <number>: how many paket to send by request
[-inter] <mili> : time to wait in milisecond after each request
root@bt:/pentest/enumeration/snmp/admsnmp# ls
ADMsnmp ADMsnmp.README snmp.passwd
root@bt:/pentest/enumeration/snmp/admsnmp# ./ADMsnmp 10.1.1.2 -wordf snmp.passwd
ADMsnmp vbeta 0.1 (c) The ADM crew
ftp://ADM.isp.at/ADM/
greets: !ADM, el8.org, ansia
>>>>>>>>>>> get req name=router id = 2 >>>>>>>>>>>
>>>>>>>>>>> get req name=cisco id = 5 >>>>>>>>>>>
>>>>>>>>>>> get req name=public id = 8 >>>>>>>>>>>
>>>>>>>>>>> get req name=private id = 11 >>>>>>>>>>>
<<<<<<<<<<< recv snmpd paket id = 12 name = private ret =0 <<<<<<<<<<
>>>>>>>>>>>> send setrequest id = 12 name = private >>>>>>>>
>>>>>>>>>>> get req name=admin id = 14 >>>>>>>>>>>
<<<<<<<<<<< recv snmpd paket id = 13 name = private ret =0 <<<<<<<<<<
>>>>>>>>>>> get req name=proxy id = 17 >>>>>>>>>>>
<<<<<<<<<<< recv snmpd paket id = 140 name = private ret =2 <<<<<<<<<<
>>>>>>>>>>> get req name=write id = 20 >>>>>>>>>>>
<<<<<<<<<<< recv snmpd paket id = 140 name = private ret =2 <<<<<<<<<<
>>>>>>>>>>> get req name=access id = 23 >>>>>>>>>>>
>>>>>>>>>>> get req name=root id = 26 >>>>>>>>>>>
>>>>>>>>>>> get req name=enable id = 29 >>>>>>>>>>>
>>>>>>>>>>> get req name=all private id = 32 >>>>>>>>>>>
>>>>>>>>>>> get req name= private id = 35 >>>>>>>>>>>
>>>>>>>>>>> get req name=test id = 38 >>>>>>>>>>>
>>>>>>>>>>> get req name=guest id = 41 >>>>>>>>>>>
<!ADM!> snmp check on 10.1.1.2 <!ADM!>
sys.sysName.0:R1.smoke.com
name = private readonly access
2.Snmp Enum
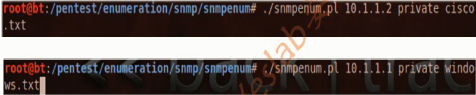
The Snmp Enum is small Perl script used to enumerate the target SNMP device to get more information about its internal system and networ.The key data retrieved may include system users,hardware information,running services,installed software,uptime,share folders,disk drives,IP addresses,network interfaces,and other useful information based on the type of SNMP device(Cisco,Windows,and Linux).(在获取community后,可以使用snmp enum获取大量有关Cisco,windows和linux的信息)

root@bt:/pentest/enumeration/snmp# cd snmpenum/
root@bt:/pentest/enumeration/snmp/snmpenum# ls
cisco.txt linux.txt README.txt snmpenum.pl windows.txt
root@bt:/pentest/enumeration/snmp/snmpenum# ./snmpenum.pl 10.1.1.2 private cisco.txt
----------------------------------------
PROCESSES
----------------------------------------
Chunk Manager
Load Meter
CEF Scanner
EDDRI_MAIN
Check heaps
Pool Manager
Timers
IPC Dynamic Cache
IPC Zone Manager
IPC Periodic Timer
IPC Deferred Port Closure
IPC Seat Manager
IPC BackPressure
OIR Handler
Crash writer
Environmental monitor
ARP Input
ATM Idle Timer
AAA high-capacity counters
AAA_SERVER_DEADTIME
Policy Manager
DDR Timers
Entity MIB API
EEM ED Syslog
HC Counter Timers
Serial Background
RO Notify Timers
SMART
GraphIt
Dialer event
SERIAL A'detect
XML Proxy Client
Inode Table Destroy
Critical Bkgnd
Net Background
IDB Work
Logger
TTY Background
Per-Second Jobs
DHCPD Timer
AggMgr Process
dev_device_inserted
dev_device_removed
mxt5100
sal_dpc_process
ARL Table Manage
ESWILPPM
Eswilp Storm Control Process
SM Monitor
VNM DSPRM MAIN
DSPFARM DSP READY
FLEX DNLD MAIN
HDV background
Ether-Switch RBCP Monitor
AAL2CPS TIMER_CU
IGMP Snooping Process
IGMP Snooping Receiving Process
Call Management
Dot11 auth Dot1x process
Dot11 Mac Auth
dot1x
DTP Protocol
PI MATM Aging Proc
EtherChnl
AAA Server
AAA ACCT Proc
ACCT Periodic Proc
AAA Dictionary Recycle
CDP Protocol
IP Input
ICMP event handler
MOP Protocols
PPP Hooks
SSS Manager
SSS Test Client
SSS Feature Manager
SSS Feature Timer
VPDN call manager
L2X Socket process
L2X SSS manager
L2TP mgmt daemon
X.25 Encaps Manage
EAPoUDP Process
IP Host Track Process
IPv6 RIB Redistribute
KRB5 AAA
PPP IP Route
PPP IPCP
IP Traceroute
IP Background
IP RIB Update
SNMP Timers
CEF process
Asy FS Helper
TCP Timer
Transport Port Agent
TCP Protocols
COPS
L2MM
MRD
IGMPSN
RLM groups Process
DDP
SCTP Main Process
IUA Main Process
RUDPV1 Main Process
bsm_timers
bsm_xmt_proc
CES Client SVC Retry Periodic
Socket Timers
DHCPD Receive
Dialer Forwarder
IP Cache Ager
Adj Manager
ATM OAM Input
ATM OAM TIMER
HTTP CORE
RARP Input
PAD InCall
X.25 Background
PPP Bind
PPP SSS
RBSCP Background
Inspect Timer
DHCPD Database
Authentication Proxy Timer
Auth-proxy AAA Bkgd
IPS Timer
SDEE Management
IPv6 Inspect Timer
URL filter proc
Crypto HW Proc
CCVPM_HDSPRM
FLEX DSPRM MAIN
FLEX DSP KEEPALIVE MAIN
CRM_CALL_UPDATE_SCAN
HDA DSPRM MAIN
ENABLE AAA
EM Background Process
Key chain livekeys
LINE AAA
LOCAL AAA
TPLUS
VSP_MGR
encrypt proc
Crypto WUI
Crypto Support
CCVPM_HTSP
VPM_MWI_BACKGROUND
CCVPM_R2
FB/KS Log HouseKeeping
EPHONE MWI BG Process
CCSWVOICE
IP SNMP
http client process
PDU DISPATCHER
QOS_MODULE_MAIN
RPMS_PROC_MAIN
VoIP AAA
crypto engine proc
Crypto CA
Crypto PKI-CRL
Crypto SSL
Crypto ACL
CRYPTO QoS process
Crypto INT
Crypto IKMP
IPSEC key engine
IPSEC manual key
Crypto PAS Proc
Crypto Delete Manager
Key Proc
PM Callback
DATA Transfer Process
DATA Collector
AAA SEND STOP EVENT
EEM ED CLI
EEM ED Counter
EEM ED Interface
EEM ED IOSWD
EEM ED Memory-threshold
EEM ED None
EM ED OIR
EEM ED SNMP
EEM ED Timer
EEM Server
Syslog Traps
trunk conditioning supervisory *
trunk conditioning supervisory *
VLAN Manager
crypto sw pk proc
EEM Policy Director
Syslog
VPDN Scal
SNMP ENGINE
Net Input
Compute load avgs
Per-minute Jobs
SSH Event handler
SNMP ConfCopyProc
SNMP Traps
----------------------------------------
IP ADDRESSES
----------------------------------------
10.1.1.2
----------------------------------------
UPTIME
----------------------------------------
1 hour, 22:17.28
----------------------------------------
HOSTNAME
----------------------------------------
R1.smoke.com
----------------------------------------
SNMPcommunities
----------------------------------------
----------------------------------------
LAST TERMINAL USERS
----------------------------------------
smoke
----------------------------------------
HARDWARE
----------------------------------------
2691 chassis
3620 Chassis Slot
c2691 Motherboard with Fast Ethernet
3620 DaughterCard Slot
3620 DaughterCard Slot
3620 DaughterCard Slot
AIM Container Slot 0
AIM Container Slot 1
3620 Chassis Slot
Gt96k FE
Gt96k FE
----------------------------------------
SYSTEM INFO
----------------------------------------
Cisco IOS Software, 2600 Software (C2691-ADVENTERPRISEK9_SNA-M), Version 12.4(13b), RELEASE SOFTWARE (fc3)
Technical Support: http://www.cisco.com/techsupport
Copyright (c) 1986-2007 by Cisco Systems, Inc.
Compiled Tue 24-Apr-07 15:33 by prod_rel_team
----------------------------------------
TACACS SERVER
----------------------------------------
10.1.1.100
----------------------------------------
SNMP TRAP SERVER
----------------------------------------
----------------------------------------
INTERFACES
----------------------------------------
FastEthernet0/0
FastEthernet0/1
Null0
----------------------------------------
INTERFACE DESCRIPTIONS
----------------------------------------
----------------------------------------
LOGMESSAGES
----------------------------------------
Configuration was modified. Issue "write memory" to save new certificate



