2.扫描工具




内容简介
第一部分:主机发现
第二部分:操作系统指纹
第三部分:端口扫描
第四部分:服务探测
第五部分:VPN探测
第一部分
主机发现
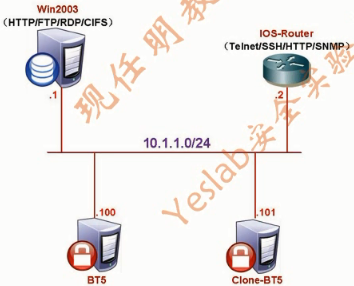
拓扑介绍

配置BT5的IP地址:
root@bt:~# ifconfig eth1 10.1.1.100 netmask 255.255.255.0
root@bt:~# ifconfig eth1
eth1 Link encap:以太网 硬件地址 00:0c:29:f8:2a:28
inet 地址:10.1.1.100 广播:10.1.1.255 掩码:255.255.255.0
inet6 地址: fe80::20c:29ff:fef8:2a28/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 跃点数:1
接收数据包:31 错误:0 丢弃:0 过载:0 帧数:0
发送数据包:12 错误:0 丢弃:0 过载:0 载波:0
碰撞:0 发送队列长度:1000
接收字节:3003 (3.0 KB) 发送字节:936 (936.0 B)
root@bt:~# ping 10.1.1.1
PING 10.1.1.1 (10.1.1.1) 56(84) bytes of data.
64 bytes from 10.1.1.1: icmp_seq=1 ttl=128 time=3.68 ms
64 bytes from 10.1.1.1: icmp_seq=2 ttl=128 time=0.419 ms
64 bytes from 10.1.1.1: icmp_seq=3 ttl=128 time=0.814 ms
^C
--- 10.1.1.1 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2000ms
rtt min/avg/max/mdev = 0.419/1.639/3.685/1.455 ms
root@bt:~# ping 10.1.1.2
PING 10.1.1.2 (10.1.1.2) 56(84) bytes of data.
64 bytes from 10.1.1.2: icmp_seq=1 ttl=255 time=46.8 ms
64 bytes from 10.1.1.2: icmp_seq=2 ttl=255 time=24.1 ms
64 bytes from 10.1.1.2: icmp_seq=3 ttl=255 time=29.2 ms
^C
--- 10.1.1.2 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2004ms
rtt min/avg/max/mdev = 24.177/33.406/46.826/9.711 ms
root@bt:~# ping 10.1.1.101
PING 10.1.1.101 (10.1.1.101) 56(84) bytes of data.
64 bytes from 10.1.1.101: icmp_seq=1 ttl=64 time=4.15 ms
64 bytes from 10.1.1.101: icmp_seq=2 ttl=64 time=0.616 ms
^C
--- 10.1.1.101 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1001ms
rtt min/avg/max/mdev = 0.616/2.387/4.158/1.771 ms
root@bt:~# route add default gw 10.1.1.254
root@bt:~# netstat -r
内核 IP 路由表
Destination Gateway Genmask Flags MSS Window irtt Iface
192.168.58.0 * 255.255.255.0 U 0 0 0 eth2
10.1.1.0 * 255.255.255.0 U 0 0 0 eth1
default 192.168.58.2 0.0.0.0 UG 0 0 0 eth2
root@bt:~# vim /etc/resolv.conf
nameserver 192.168.58.2
domain localdomain
search localdomain
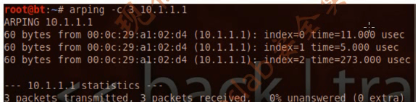
1.arping
The arping tool is used to ping a destination host in the Local Area Network (LAN) using the ARP(Address Resolution Protocol)request.The Arping is useful to test whether a particular IP address is in use in the network.(对直连网络,使用ARP request进程测试,一个特定IP是否正在被使用)


root@bt:~# arping -c 3 10.1.1.1
ARPING 10.1.1.1
60 bytes from 00:0c:29:c7:e5:c9 (10.1.1.1): index=0 time=897.000 usec
60 bytes from 00:0c:29:c7:e5:c9 (10.1.1.1): index=1 time=405.000 usec
60 bytes from 00:0c:29:c7:e5:c9 (10.1.1.1): index=2 time=1000.000 usec
--- 10.1.1.1 statistics ---
3 packets transmitted, 3 packets received, 0% unanswered (0 extra)
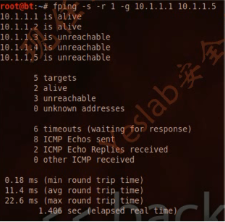
2.fping
The fping tool is used to send a ping(ICMP ECHO) request to serveral hosts at once.You can specify several targets on the command line or you can use a file containing the hosts to be pinged.(使用ICMP ECHO一次请求多个主机)

root@bt:~# fping -s -r 1 -g 10.1.1.1 10.1.1.100
10.1.1.1 is alive
10.1.1.2 is alive
ICMP Host Unreachable from 10.1.1.100 for ICMP Echo sent to 10.1.1.3
ICMP Host Unreachable from 10.1.1.100 for ICMP Echo sent to 10.1.1.4
ICMP Host Unreachable from 10.1.1.100 for ICMP Echo sent to 10.1.1.5
ICMP Host Unreachable from 10.1.1.100 for ICMP Echo sent to 10.1.1.6
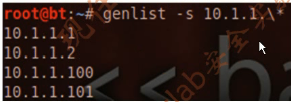
3.genlist
The genlist tool can be used to get a list of hosts that respond to the ping probes.(获取使用清单,通过ping探测的响应。)

root@bt:~# genlist -s 10.1.1.\*
10.1.1.1
10.1.1.2
10.1.1.100
10.1.1.101
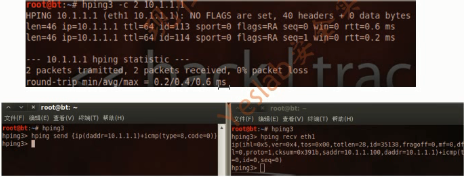
4.hping3
The hping3 tool can be used to send custom packets and to display replies from the target.it supports TCP,UDP,ICMP,and RAW-IP protocols.(支持发送自定义包和显示目标的回应,它支持TCP,UDP,ICMP和RAW.IP协议)

root@bt:~# hping3 -c 2 10.1.1.1
HPING 10.1.1.1 (eth1 10.1.1.1): NO FLAGS are set, 40 headers + 0 data bytes
len=46 ip=10.1.1.1 ttl=128 id=42705 sport=0 flags=RA seq=0 win=0 rtt=5.1 ms
len=46 ip=10.1.1.1 ttl=128 id=42706 sport=0 flags=RA seq=1 win=0 rtt=0.4 ms
--- 10.1.1.1 hping statistic ---
2 packets tramitted, 2 packets received, 0% packet loss
round-trip min/avg/max = 0.4/2.8/5.1 ms
hping3> hping3 send {ip(daaddr=10.1.1.1)+icmp(type=8,code=0)}
hping3> hping recv eth1
ip(ihl=0x5,ver=0x4,tos=0x00,totlen=28,id=45431,fragoff=0,mf=0,df=0,rf=0,ttl=0,proto=1,cksum=0x03f3,saddr=10.1.1.100,daddr=10.1.1.1)+icmp(type=8,code=0,id=0,seq=0)
5.nbtscan
The nbtscan tool can be used to scan IP addresses for the NetBIOS name information.It will produce a report which contains the IP address,NetBIOS computer name,service available,logged-in username,and MAC address of the corresponding machines.(扫描一个IP地址范围的NetBIOS名字信息,它将提供一个关于IP地址,NetBIOS计算机名,服务可用性,登录用户名和MAC地址的报告。)

root@bt:~# nbtscan 10.1.1.1-254
Doing NBT name scan for addresses from 10.1.1.1-254
IP address NetBIOS Name Server User MAC address
------------------------------------------------------------------------------
10.1.1.1 SMOKE <server> <unknown> 00-0c-29-c7-e5-c9
6.Nping(1)
The nping tool is the latest generation tool that allows users to generate network packets of a wide range of protocols (TCP,UDP,ICMP,ARP).You can also customize the fields in the protocol headers,such as-source and destination port for TCP and UDP.(nping工具允许用户产生各种网络包(TCP,UDP,ICMP,ARP),也允许用户自定义协议头部,例如:源和目的,TCP和UDP的端口号。)

6.Nping(2)

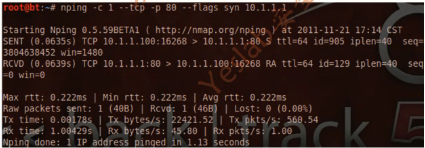
root@bt:~# nping -c 1 --tcp -p 80 --flags syn 10.1.1.1
Starting Nping 0.5.59BETA1 ( http://nmap.org/nping ) at 2015-04-10 23:02 CST
SENT (0.0584s) TCP 10.1.1.100:24920 > 10.1.1.1:80 S ttl=64 id=61628 iplen=40 seq=4027955145 win=1480
RCVD (0.0594s) TCP 10.1.1.1:80 > 10.1.1.100:24920 SA ttl=128 id=51353 iplen=44 seq=581097379 win=64240 <mss 1460>
Max rtt: 0.920ms | Min rtt: 0.920ms | Avg rtt: 0.920ms
Raw packets sent: 1 (40B) | Rcvd: 1 (46B) | Lost: 0 (0.00%)
Tx time: 0.00109s | Tx bytes/s: 36563.07 | Tx pkts/s: 914.08
Rx time: 1.00151s | Rx bytes/s: 45.93 | Rx pkts/s: 1.00
Nping done: 1 IP address pinged in 1.13 seconds
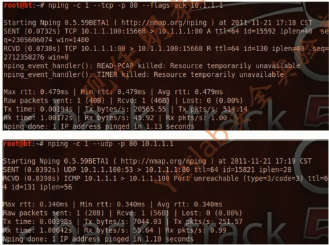
root@bt:~# nping -c 1 --tcp -p 80 --flags syn,ack 10.1.1.1
Starting Nping 0.5.59BETA1 ( http://nmap.org/nping ) at 2015-04-10 23:26 CST
SENT (0.0498s) TCP 10.1.1.100:19392 > 10.1.1.1:80 SA ttl=64 id=62844 iplen=40 seq=764399333 win=1480
RCVD (0.0504s) TCP 10.1.1.1:80 > 10.1.1.100:19392 R ttl=128 id=62933 iplen=40 seq=2375947009 win=0
Max rtt: 0.673ms | Min rtt: 0.673ms | Avg rtt: 0.673ms
Raw packets sent: 1 (40B) | Rcvd: 1 (46B) | Lost: 0 (0.00%)
Tx time: 0.00195s | Tx bytes/s: 20544.43 | Tx pkts/s: 513.61
Rx time: 1.00205s | Rx bytes/s: 45.91 | Rx pkts/s: 1.00
Nping done: 1 IP address pinged in 1.11 seconds
root@bt:~# nping -c 1 --udp -p 80 10.1.1.1
Starting Nping 0.5.59BETA1 ( http://nmap.org/nping ) at 2015-04-10 23:27 CST
SENT (0.0293s) UDP 10.1.1.100:53 > 10.1.1.1:80 ttl=64 id=29430 iplen=28
RCVD (0.0299s) ICMP 10.1.1.1 > 10.1.1.100 Port unreachable (type=3/code=3) ttl=128 id=63467 iplen=56
Max rtt: 0.555ms | Min rtt: 0.555ms | Avg rtt: 0.555ms
Raw packets sent: 1 (28B) | Rcvd: 1 (56B) | Lost: 0 (0.00%)
Tx time: 0.00275s | Tx bytes/s: 10200.36 | Tx pkts/s: 364.30
Rx time: 1.00282s | Rx bytes/s: 55.84 | Rx pkts/s: 1.00
Nping done: 1 IP address pinged in 1.08 seconds
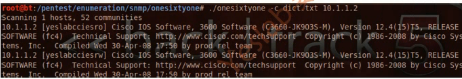
7.onesixtyone
The onesixtyone can be used as a Simple Network Monitoring Protocol (SNMP)scanner to find out if the SNMP string exists on a device. The difference with other SNMP scanners is that it sends all SNMP requests as fast as it can(10 milliseconds apart).Then it waits for responses and logs them.If the device is available,then it will send responses containing the SNMP string.(onesixtyone是一个snmp扫描工具,用于找出设备上的SNMP Community字串。Onesixtyone的扫描速度非常快。)

root@bt:~# cd /pentest/enumeration/snmp/onesixtyone/
root@bt:/pentest/enumeration/snmp/onesixtyone# ls
dict.txt onesixtyone
root@bt:/pentest/enumeration/snmp/onesixtyone# ./onesixtyone -c dict.txt 10.1.1.2
Scanning 1 hosts, 52 communities
10.1.1.2 [private] Cisco IOS Software, 2600 Software (C2691-ADVENTERPRISEK9_SNA-M), Version 12.4(13b), RELEASE SOFTWARE (fc3) Technical Support: http://www.cisco.com/techsupport Copyright (c) 1986-2007 by Cisco Systems, Inc. Compiled Tue 24-Apr-07 15:33 by prod_rel_team
10.1.1.2 [public] Cisco IOS Software, 2600 Software (C2691-ADVENTERPRISEK9_SNA-M), Version 12.4(13b), RELEASE SOFTWARE (fc3) Technical Support: http://www.cisco.com/techsupport Copyright (c) 1986-2007 by Cisco Systems, Inc. Compiled Tue 24-Apr-07 15:33 by prod_rel_team
8.protos
Protos这个软件主要用于扫描特定主机上所支持的协议。

root@bt:/pentest/enumeration/snmp/onesixtyone# cd /pentest/enumeration/irpas/
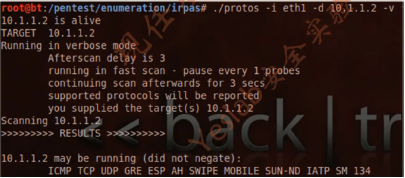
root@bt:/pentest/enumeration/irpas# ./protos -i eth1 -d 10.1.1.2 -v
10.1.1.2 is alive
TARGET 10.1.1.2
Running in verbose mode
Afterscan delay is 3
running in fast scan - pause every 1 probes
continuing scan afterwards for 3 secs
supported protocols will be reported
you supplied the target(s) 10.1.1.2
Scanning 10.1.1.2
Scanning 10.1.1.2
>>>>>>>>> RESULTS >>>>>>>>>>
10.1.1.2 may be running (did not negate):
ICMP IPenc TCP UDP IPv6 GRE ESP AH SWIPE NARP MOBILE SUN-ND ISO-IP EIGRP IPIP IATP SM 134 201
第二部分
操作系统指纹
1.p0f
The p0f tool is a tool used to fingerprint an operating system passively.It can identify an operating system on.(一个被动的操作系统指纹监控工具,Cisco IPS就是用这个程序获取目标的操作系统。)
1.Machines that connect to your box(SYN mode,this is the default mode)
2.machines you connect to (SYN+ACK mode)
3.Machine you cannot connect to(RST+mode)
4.Machines whose communications you can observe
4.Machines whose communications you can observe

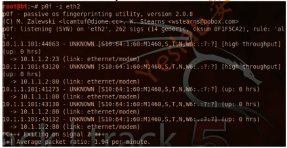
root@bt:~# p0f
p0f - passive os fingerprinting utility, version 2.0.8
(C) M. Zalewski <lcamtuf@dione.cc>, W. Stearns <wstearns@pobox.com>
p0f: listening (SYN) on 'eth1', 262 sigs (14 generic, cksum 0F1F5CA2), rule: 'all'.
10.1.1.100:50469 - UNKNOWN [S10:64:1:60:M1460,S,T,N,W6:.:?:?] [high throughput] (up: 3 hrs)
-> 10.1.1.2:23 (link: ethernet/modem)
10.1.1.100:57440 - UNKNOWN [S10:64:1:60:M1460,S,T,N,W6:.:?:?] (up: 4 hrs)
-> 10.1.1.2:80 (link: ethernet/modem)
2.Xprobe2
Xprobe2 is an active OS fingerprinting tool.It fingerprints operating systems by using fuzzy signature matching.probabilistic guesses,multiple matches simultaneously.and a signature database.(主动OS指纹探测工具)
Xprobe2 10.1.1.1

root@bt:~# xprobe2 10.1.1.2
Xprobe-ng v.2.1 Copyright (c) 2002-2009 fyodor@o0o.nu, ofir@sys-security.com, meder@o0o.nu
[+] Target is 10.1.1.2
[+] Loading modules.
[+] Following modules are loaded:
[x] ping:icmp_ping - ICMP echo discovery module
[x] ping:tcp_ping - TCP-based ping discovery module
[x] ping:udp_ping - UDP-based ping discovery module
[x] infogather:ttl_calc - TCP and UDP based TTL distance calculation
[x] infogather:portscan - TCP and UDP PortScanner
[x] fingerprint:icmp_echo - ICMP Echo request fingerprinting module
[x] fingerprint:icmp_tstamp - ICMP Timestamp request fingerprinting module
[x] fingerprint:icmp_amask - ICMP Address mask request fingerprinting module
[x] fingerprint:icmp_info - ICMP Information request fingerprinting module
[x] fingerprint:icmp_port_unreach - ICMP port unreachable fingerprinting module
[x] fingerprint:tcp_hshake - TCP Handshake fingerprinting module
[x] fingerprint:tcp_rst - TCP RST fingerprinting module
[x] app:smb - SMB fingerprinting module
[x] app:snmp - SNMPv2c fingerprinting module
[x] app:ftp - FTP fingerprinting tests
[x] app:http - HTTP fingerprinting tests
[+] 16 modules registered
[+] Initializing scan engine
[+] Running scan engine
fingerprint:icmp_tstamp has not enough data
Executing ping:icmp_ping
Executing fingerprint:icmp_port_unreach
Executing fingerprint:tcp_rst
Executing fingerprint:icmp_echo
fingerprint:tcp_hshake has not enough data
Executing fingerprint:icmp_amask
Executing fingerprint:icmp_tstamp
Executing fingerprint:icmp_info
app:smb has not enough data
Executing app:snmp
[+] SNMP [Community: public] [sysDescr.0: Cisco IOS Software, 2600 Software (C2691-ADVENTERPRISEK9_SNA-M), Version 12.4(13b), RELEASE SOFTWARE (fc3)
Technical Support: http://www.cisco.com/techsupport
Copyright (c) 1986-2007 by Cisco Systems, Inc.
Compiled Tue 24-Apr-07 15:33 by prod_rel_team]
ping:tcp_ping has not enough data
ping:udp_ping has not enough data
infogather:ttl_calc has not enough data
Executing infogather:portscan
Executing app:ftp
Executing app:http
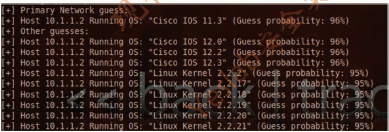
[+] Primary Network guess:
[+] Host 10.1.1.2 Running OS: "Cisco IOS 11.3" (Guess probability: 96%)
[+] Other guesses:
[+] Host 10.1.1.2 Running OS: "Cisco IOS 12.0" (Guess probability: 96%)
[+] Host 10.1.1.2 Running OS: "Cisco IOS 12.2" (Guess probability: 96%)
[+] Host 10.1.1.2 Running OS: "Cisco IOS 12.3" (Guess probability: 96%)
[+] Host 10.1.1.2 Running OS: "Cisco IOS 11.1" (Guess probability: 96%)
[+] Host 10.1.1.2 Running OS: "Cisco IOS 11.2" (Guess probability: 96%)
[+] Host 10.1.1.2 Running OS: "NetBSD 1.5.3" (Guess probability: 92%)
[+] Host 10.1.1.2 Running OS: "NetBSD 1.5.2" (Guess probability: 92%)
[+] Host 10.1.1.2 Running OS: "NetBSD 1.5.1" (Guess probability: 92%)
[+] Host 10.1.1.2 Running OS: "NetBSD 1.5" (Guess probability: 92%)
[+] Cleaning up scan engine
[+] Modules deinitialized
[+] Execution completed.
第三部分
端口扫描
1.AutoScan(1)
AutoScan is a graphical-based network scanning tool that can be used to find live hosts on a network.It also can be-used to find open ports and get information on the type of operating system used by each host.AutoScan uses an agent for the GUI to collect and fingerprint the targeted hosts and send the results to the GUI via an internal TCP connection.(图形化网络扫描工具,能够发现网络中活动主机)

1.AutoScan(2)

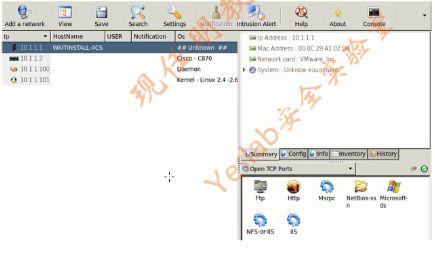
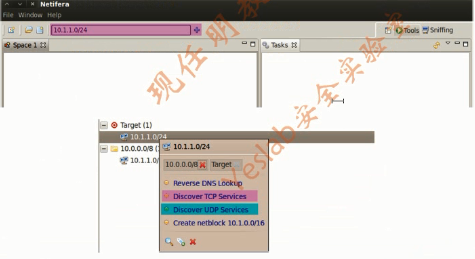
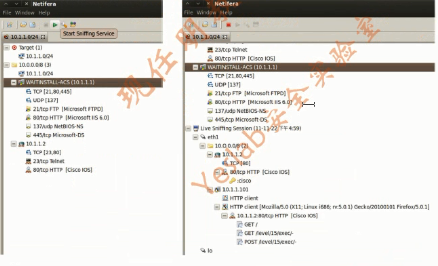
2.Netifera(1)
Netifera is a network security tool and modular platform to develop network security tools.As a modular platform.it provides Application Programming interface(API)for tasks such as:(一个图形化网络安全工具)
1.HIgh performance asynchronous socket connection and communication
2.Link level packet capture and raw socket injection
3.Network protocol header construction and analysis(Ethernet,IP,TCP,and so on)
4.Appllcation layer protocol llbraies(HTTP,DNS,FTP,and so on)
Whlle as a network security tool,It has the following capabilties;
1.Network scanning and service detection on TCP and UDP
2.Identifying operating system
3.Fully supporting IPv4 and IPv6
4.Brute-forcing DNS name
5.Carrying out DNS zone transfer
6.Discovering web applications,collecting e-mail addresses and adding the website structure to the data model
2.Netifera(2)

2.Netifera(3)

2.Netifera(4)

3.NMAP(1)
Nmap is very comprehensive.feature and fingeprints rich,and is a port scanner widely used by all of the IT security communicty.It is written and maintained by Fyodor.It is a must-have tool for a penetration tester because of its quality and flexibility.(NMAP是一个综合性的,并且特性丰富的端口扫描工具。是一个渗透测试者的必备工具)
Nmap has several other capablltles Including:(NMAP包含如下能力)
1.Host discovery(主机发现)
2.Service/version detection(服务于版本检测)
3.Operating system detection(操作系统检测)
4.Network traceroute(网络追踪)
5.Nmap Scripting Engine(NMAP脚本引擎)
3.NMAP(2)
主机发现

root@bt:~# nmap -v -n -sP 10.1.1.0/24
Starting Nmap 5.59BETA1 ( http://nmap.org ) at 2015-04-11 01:03 CST
Initiating ARP Ping Scan at 01:03
Scanning 100 hosts [1 port/host]
Completed ARP Ping Scan at 01:03, 1.58s elapsed (100 total hosts)
Nmap scan report for 10.1.1.0 [host down]
Nmap scan report for 10.1.1.1
Host is up (0.00093s latency).
MAC Address: 00:0C:29:C7:E5:C9 (VMware)
Nmap scan report for 10.1.1.2
Host is up (0.027s latency).
MAC Address: C0:01:0D:00:00:00 (Unknown)
3.NMAP(3)
综合扫描(端口扫描,服务确认,操作系统确认...)

root@bt:~# nmap -v -n -A 10.1.1.1
Starting Nmap 5.59BETA1 ( http://nmap.org ) at 2015-04-11 01:07 CST
NSE: Loaded 63 scripts for scanning.
NSE: Script Pre-scanning.
Initiating ARP Ping Scan at 01:07
Scanning 10.1.1.1 [1 port]
Completed ARP Ping Scan at 01:07, 0.07s elapsed (1 total hosts)
Initiating SYN Stealth Scan at 01:07
Scanning 10.1.1.1 [1000 ports]
Discovered open port 1025/tcp on 10.1.1.1
Discovered open port 443/tcp on 10.1.1.1
Discovered open port 135/tcp on 10.1.1.1
Discovered open port 139/tcp on 10.1.1.1
Discovered open port 445/tcp on 10.1.1.1
Discovered open port 80/tcp on 10.1.1.1
Discovered open port 49/tcp on 10.1.1.1
Discovered open port 2001/tcp on 10.1.1.1
Discovered open port 2000/tcp on 10.1.1.1
Discovered open port 2002/tcp on 10.1.1.1
Discovered open port 1433/tcp on 10.1.1.1
Completed SYN Stealth Scan at 01:07, 1.27s elapsed (1000 total ports)
Initiating Service scan at 01:07
Scanning 11 services on 10.1.1.1
Completed Service scan at 01:09, 126.29s elapsed (11 services on 1 host)
Initiating OS detection (try #1) against 10.1.1.1
NSE: Script scanning 10.1.1.1.
Initiating NSE at 01:09
Completed NSE at 01:09, 0.33s elapsed
Nmap scan report for 10.1.1.1
Host is up (0.00058s latency).
Not shown: 989 closed ports
PORT STATE SERVICE VERSION
49/tcp open tacacs?
80/tcp open http Microsoft IIS httpd 6.0
| http-methods: OPTIONS TRACE GET HEAD POST
| Potentially risky methods: TRACE
|_See http://nmap.org/nsedoc/scripts/http-methods.html
|_http-title: Site doesn't have a title (text/html).
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn
443/tcp open https?
445/tcp open microsoft-ds Microsoft Windows 2003 or 2008 microsoft-ds
1025/tcp open msrpc Microsoft Windows RPC
1433/tcp open ms-sql-s Microsoft SQL Server 2005 9.00.3042.00; SP2
2000/tcp open cisco-sccp?
2001/tcp open dc?
2002/tcp open http Cisco Secure ACS login
|_http-title: CiscoSecure ACS Login
|_http-favicon: Unknown favicon MD5: 54A4F9946686C09567569CF13CA6DD9C
MAC Address: 00:0C:29:C7:E5:C9 (VMware)
Device type: general purpose
Running: Microsoft Windows 2003
OS details: Microsoft Windows Server 2003 SP1 or SP2
Network Distance: 1 hop
TCP Sequence Prediction: Difficulty=264 (Good luck!)
IP ID Sequence Generation: Incremental
Service Info: OSs: Windows, IOS
Host script results:
| nbstat:
| NetBIOS name: SMOKE, NetBIOS user: <unknown>, NetBIOS MAC: 00:0c:29:c7:e5:c9 (VMware)
| Names
| SMOKE<00> Flags: <unique><active>
| WORKGROUP<00> Flags: <group><active>
| SMOKE<20> Flags: <unique><active>
| WORKGROUP<1e> Flags: <group><active>
| WORKGROUP<1d> Flags: <unique><active>
|_ \x01\x02__MSBROWSE__\x02<01> Flags: <group><active>
|_smbv2-enabled: Server doesn't support SMBv2 protocol
| smb-os-discovery:
| OS: Windows Server 2003 3790 Service Pack 1 (Windows Server 2003 5.2)
| Name: WORKGROUP\SMOKE
|_ System time: 2015-04-11 01:09:57 UTC+8
| ms-sql-info:
| [10.1.1.1:1433]
| Version: Microsoft SQL Server 2005 SP2
| Version number: 9.00.3042.00
| Product: Microsoft SQL Server 2005
| Service pack level: SP2
| Post-SP patches applied: No
|_ TCP port: 1433
TRACEROUTE
HOP RTT ADDRESS
1 0.58 ms 10.1.1.1
NSE: Script Post-scanning.
Read data files from: /usr/local/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at http://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 130.32 seconds
Raw packets sent: 1098 (48.740KB) | Rcvd: 1017 (40.996KB)
第四部分
服务探测
1.Amap
Amap is a tool that can be used to check the application that is running on a specific port.Amap works by sending a trigger packet to the port and comparing the response to its database;it will print out the match it finds.
(Amap是一个工具,用于检测特定端口上运行的具体运用。)

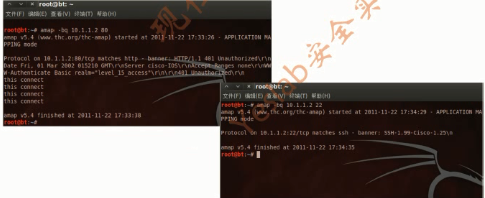
root@bt:~# amap -bq 10.1.1.1 80
amap v5.4 (www.thc.org/thc-amap) started at 2015-04-11 01:20:38 - APPLICATION MAPPING mode
Protocol on 10.1.1.1:80/tcp matches http - banner: HTTP/1.1 400 Bad Request\r\nContent-Type text/html\r\nDate Fri, 10 Apr 2015 172037 GMT\r\nConnection close\r\nContent-Length 35\r\n\r\n<h1>Bad Request (Invalid Verb)</h1>
Protocol on 10.1.1.1:80/tcp matches http-iis - banner: HTTP/1.1 200 OK\r\nContent-Length 5\r\nContent-Type text/html\r\nContent-Location http//10.1.1.1/index.html\r\nLast-Modified Fri, 10 Apr 2015 151101 GMT\r\nAccept-Ranges bytes\r\nETag "77a7448ea073d012fb"\r\nServer Microsoft-IIS/6.0\r\nDate Fri, 10 Apr 2
amap v5.4 finished at 2015-04-11 01:20:41
R1#conf t
R1(config)#line console 0
R1(config-line)#exit
R1(config)#ip domain name smoke.com
R1(config)#crypto key generate rsa general-keys modulus 1024
R1(config)#username smoke privilege 15 password smoke
R1(config)#line vty 0 15
R1(config-line)#login local
root@bt:~# amap -bq 10.1.1.2 22
amap v5.4 (www.thc.org/thc-amap) started at 2015-04-11 01:40:34 - APPLICATION MAPPING mode
Protocol on 10.1.1.2:22/tcp matches ssh - banner: SSH-1.99-Cisco-1.25\n
amap v5.4 finished at 2015-04-11 01:40:43
2.Httprint
Httprint is an application that can be used to detect an HTTP server software and version.It works by using statistical analysis combined with fuzzy logic techniques.Httpring tests the HTTP server and compares the signature it receives with a set of stored signatures,and assigns a confidence rating to each candidates signature.The potential matches for the server are the signatures with the highest confidence rating.(Httprint用于检测HTTP服务器的软件和版本)

root@bt:~# cd /pentest/enumeration/www/httprint/linux/
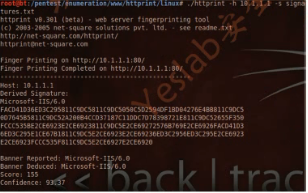
root@bt:/pentest/enumeration/www/httprint/linux# ./httprint -h 10.1.1.1 -s signatures.txt
httprint v0.301 (beta) - web server fingerprinting tool
(c) 2003-2005 net-square solutions pvt. ltd. - see readme.txt
http://net-square.com/httprint/
httprint@net-square.com
Finger Printing on http://10.1.1.1:80/
Finger Printing Completed on http://10.1.1.1:80/
--------------------------------------------------
Host: 10.1.1.1
Derived Signature:
Microsoft-IIS/6.0
FACD41D36ED3C295811C9DC5811C9DC5050C5D2594DF1BD04276E4BB811C9DC5
0D7645B5811C9DC52A200B4CCD37187C11DDC7D78398721E811C9DC52655F350
FCCC535BE2CE6923E2CE6923811C9DC5E2CE69272576B769E2CE6926FACD41D3
6ED3C295E1CE67B1811C9DC5E2CE6923E2CE69236ED3C2956ED3C295E2CE6923
E2CE6923FCCC535F811C9DC5E2CE6927E2CE6920
Banner Reported: Microsoft-IIS/6.0
Banner Deduced: Microsoft-IIS/6.0
Score: 155
Confidence: 93.37
------------------------
Scores:
Microsoft-IIS/6.0: 155 93.37
Netscape-Enterprise/6.0: 93 15.40
Microsoft-IIS/5.0: 89 13.03
Netscape-Enterprise/4.1: 88 12.47
Microsoft-IIS/5.0 ASP.NET: 84 10.40
Microsoft-IIS/5.1: 84 10.40
Lotus-Domino/6.x: 83 9.92
Agranat-EmWeb: 82 9.46
Apache/1.3.26: 79 8.14
Apache/1.3.27: 78 7.73
Apache/1.3.[4-24]: 77 7.33
Apache/1.3.[1-3]: 77 7.33
thttpd: 74 6.21
cisco-IOS: 70 4.90
Microsoft-IIS/4.0: 69 4.59
Apache/2.0.x: 69 4.59
IDS-Server/3.2.2: 68 4.31
Apache/1.2.6: 67 4.03
Netscape-Enterprise/3.5.1G: 59 2.18
RomPager/4.07 UPnP/1.0: 59 2.18
Domino-Go-Webserver/4.6.2.8: 57 1.81
HP-ChaiServer/3.0: 57 1.81
MikroTik RouterOS: 57 1.81
TUX/2.0 (Linux): 57 1.81
Zeus/4.1: 55 1.48
WebSitePro/2.3.18: 55 1.48
AkamaiGHost: 55 1.48
VisualRoute 2005 Server Edition: 54 1.33
Apache-Tomcat/4.1.29: 54 1.33
Oracle Servlet Engine: 53 1.18
Zeus/4_2: 52 1.05
Netscape-Enterprise/3.6 SP2: 51 0.92
Ipswitch-IMail/8.12: 51 0.92
SunONE WebServer 6.0: 49 0.69
Lexmark Optra Printer: 49 0.69
GWS/2.1 Google Web Server: 49 0.69
Zope/2.6.0 ZServer/1.1b1: 48 0.58
CompaqHTTPServer/1.0: 47 0.48
Microsoft-IIS/URLScan: 46 0.39
Stronghold/2.4.2-Apache/1.3.x: 28 0.34
Microsoft-IIS/5.0 Virtual Host: 26 0.34
Resin/3.0.8: 29 0.33
Lotus-Domino/5.x: 25 0.33
Microsoft ISA Server (external): 25 0.33
Adaptec ASM 1.1: 24 0.32
CompaqHTTPServer-SSL/4.2: 23 0.32
Jana Server/1.45: 31 0.31
WebLogic XMLX Module 8.1: 31 0.31
Cisco-HTTP: 22 0.31
Cisco Pix 6.2: 22 0.31
JRun Web Server: 22 0.31
MiniServ/0.01: 22 0.31
Linksys AP2: 45 0.30
Com21 Cable Modem: 45 0.30
SMC Wireless Router 7004VWBR: 45 0.30
BaseHTTP/0.3 Python/2p3.3 edna/0.4: 45 0.30
Belkin Wireless router: 45 0.30
RealVNC/4.0: 45 0.30
Netscape-Enterprise/3.6: 32 0.30
MiniServ/0.01 Webmin: 32 0.30
fnord: 32 0.30
AOLserver/3.4.2-3.5.1: 21 0.29
3Com/v1.0: 21 0.29
Snap Appliances, Inc./3.x: 21 0.29
Tanberg 880 video conf: 21 0.29
Xerver_v3: 33 0.28
CompaqHTTPServer/4.2: 20 0.28
Allied Telesyn Ethernet switch: 20 0.28
AssureLogic/2.0: 20 0.28
EHTTP/1.1: 19 0.26
Netscape-Enterprise/3.5.1: 34 0.26
AOLserver/3.5.6: 34 0.26
TightVNC: 34 0.26
Orion/2.0x: 34 0.26
dwhttpd (Sun Answerbook): 34 0.26
Jetty (unverified): 34 0.26
Linksys with Talisman firmware: 34 0.26
Surgemail webmail (DManager): 34 0.26
Intel NetportExpressPro/1.0: 35 0.23
Zeus/4.0: 44 0.22
Linksys WRTP54G: 44 0.22
JC-HTTPD/1.14.18: 44 0.22
Netscape-Enterprise/4.1: 36 0.20
Netgear MR814v2 - IP_SHARER WEB 1.0: 15 0.20
WebLogic Server 8.x: 14 0.18
WebLogic Server 8.1: 14 0.18
Tomcat Web Server/3.2.3: 14 0.18
Jetty/4.2.2: 14 0.18
ServletExec: 13 0.16
Microsoft ISA Server (internal): 12 0.14
WebSENSE/1.0: 12 0.14
Ubicom/1.1: 11 0.12
Ubicom/1.1 802.11b: 11 0.12
NetBuilderHTTPDv0.1: 10 0.10
NetPort Software 1.1: 10 0.10
MailEnable-HTTP/5.0: 10 0.10
Tcl-Webserver/3.4.2: 10 0.10
Oracle XML DB/Oracle9i: 42 0.08
squid/2.5.STABLE5: 42 0.08
Stronghold/4.0-Apache/1.3.x: 39 0.08
NetWare-Enterprise-Web-Server/5.1: 39 0.08
Hewlett Packard xjet: 40 0.03
HP Jet-Direct Print Server: 40 0.03
Boa/0.94.11: 40 0.03
Linksys Print Server: 5 0.03
EMWHTTPD/1.0: 41 0.02
RemotelyAnywhere: 0 0.00
Linksys AP1: 0 0.00
Linksys Router: 0 0.00
Linksys BEFSR41/BEFSR11/BEFSRU31: 0 0.00
--------------------------------------------------
root@bt:/pentest/enumeration/www/httprint/linux# ./httprint -h 10.1.1.2 -s signatures.txt
httprint v0.301 (beta) - web server fingerprinting tool
(c) 2003-2005 net-square solutions pvt. ltd. - see readme.txt
http://net-square.com/httprint/
httprint@net-square.com
Finger Printing on http://10.1.1.2:80/
Finger Printing Completed on http://10.1.1.2:80/
--------------------------------------------------
Host: 10.1.1.2
Derived Signature:
cisco-IOS
811C9DC5E2CE6922811C9DC5811C9DC5811C9DC5505FCFE8811C9DC5811C9DC5
0D7645B5AF7A648F811C9DC5CD37187C11DDC7D7811C9DC5811C9DC52655F350
E2CE6922E2CE6923E2CE6922811C9DC5E2CE6927811C9DC5E2CE6922811C9DC5
E2CE6926FCCC535B811C9DC5811C9DC5811C9DC5E2CE6922E2CE6922E2CE6923
E2CE6923FCCC535F811C9DC5E2CE6927E2CE6927
Banner Reported: cisco-IOS
Banner Deduced: cisco-IOS
Score: 102
Confidence: 61.45
------------------------
Scores:
cisco-IOS: 102 61.45
RomPager/4.07 UPnP/1.0: 69 15.34
Lotus-Domino/6.x: 65 12.24
Agranat-EmWeb: 63 10.85
Linksys AP2: 61 9.57
Microsoft-IIS/6.0: 60 8.96
Apache/1.3.27: 55 6.30
Apache/1.3.26: 55 6.30
Apache/2.0.x: 54 5.84
Apache/1.3.[4-24]: 54 5.84
Apache/1.3.[1-3]: 54 5.84
Oracle XML DB/Oracle9i: 51 4.57
Netscape-Enterprise/6.0: 49 3.83
Cisco-HTTP: 48 3.49
Cisco Pix 6.2: 48 3.49
Linksys with Talisman firmware: 48 3.49
Com21 Cable Modem: 47 3.16
Apache/1.2.6: 44 2.30
TUX/2.0 (Linux): 44 2.30
MiniServ/0.01: 44 2.30
WebSitePro/2.3.18: 44 2.30
HP-ChaiServer/3.0: 43 2.05
Ipswitch-IMail/8.12: 43 2.05
EHTTP/1.1: 42 1.81
MikroTik RouterOS: 41 1.59
EMWHTTPD/1.0: 36 0.70
Snap Appliances, Inc./3.x: 36 0.70
Netscape-Enterprise/4.1: 34 0.43
Jana Server/1.45: 34 0.43
Orion/2.0x: 34 0.43
CompaqHTTPServer/1.0: 34 0.43
thttpd: 34 0.43
Oracle Servlet Engine: 34 0.43
Boa/0.94.11: 34 0.43
Tcl-Webserver/3.4.2: 34 0.43
Apache-Tomcat/4.1.29: 34 0.43
Netscape-Enterprise/3.6 SP2: 33 0.32
3Com/v1.0: 33 0.32
NetBuilderHTTPDv0.1: 33 0.32
Microsoft-IIS/4.0: 20 0.31
Zeus/4.0: 20 0.31
CompaqHTTPServer/4.2: 20 0.31
CompaqHTTPServer-SSL/4.2: 20 0.31
AssureLogic/2.0: 20 0.31
Jetty/4.2.2: 19 0.31
Resin/3.0.8: 19 0.31
Jetty (unverified): 19 0.31
Stronghold/2.4.2-Apache/1.3.x: 21 0.30
AOLserver/3.4.2-3.5.1: 21 0.30
Xerver_v3: 21 0.30
MiniServ/0.01 Webmin: 21 0.30
fnord: 21 0.30
Zope/2.6.0 ZServer/1.1b1: 21 0.30
AkamaiGHost: 21 0.30
squid/2.5.STABLE5: 21 0.30
Microsoft-IIS/5.0 Virtual Host: 18 0.30
Netscape-Enterprise/3.5.1: 17 0.29
Linksys AP1: 17 0.29
TightVNC: 17 0.29
BaseHTTP/0.3 Python/2p3.3 edna/0.4: 17 0.29
Linksys BEFSR41/BEFSR11/BEFSRU31: 17 0.29
Adaptec ASM 1.1: 17 0.29
MailEnable-HTTP/5.0: 17 0.29
VisualRoute 2005 Server Edition: 17 0.29
Tanberg 880 video conf: 23 0.27
AOLserver/3.5.6: 24 0.25
NetWare-Enterprise-Web-Server/5.1: 24 0.25
WebLogic XMLX Module 8.1: 24 0.25
Lotus-Domino/5.x: 14 0.25
Domino-Go-Webserver/4.6.2.8: 14 0.25
Tomcat Web Server/3.2.3: 14 0.25
Linksys WRTP54G: 14 0.25
NetPort Software 1.1: 13 0.23
SunONE WebServer 6.0: 25 0.22
Netscape-Enterprise/4.1: 25 0.22
Microsoft-IIS/URLScan: 12 0.20
Linksys Router: 12 0.20
Ubicom/1.1: 26 0.19
Ubicom/1.1 802.11b: 26 0.19
Microsoft ISA Server (internal): 11 0.18
Microsoft ISA Server (external): 11 0.18
WebSENSE/1.0: 11 0.18
RemotelyAnywhere: 10 0.16
JRun Web Server: 10 0.16
Netscape-Enterprise/3.5.1G: 27 0.14
WebLogic Server 8.x: 27 0.14
dwhttpd (Sun Answerbook): 27 0.14
WebLogic Server 8.1: 27 0.14
SMC Wireless Router 7004VWBR: 27 0.14
IDS-Server/3.2.2: 27 0.14
Belkin Wireless router: 27 0.14
JC-HTTPD/1.14.18: 27 0.14
GWS/2.1 Google Web Server: 27 0.14
Netscape-Enterprise/3.6: 31 0.13
Zeus/4.1: 31 0.13
Zeus/4_2: 31 0.13
Stronghold/4.0-Apache/1.3.x: 31 0.13
Microsoft-IIS/5.0: 30 0.04
Microsoft-IIS/5.0 ASP.NET: 30 0.04
Microsoft-IIS/5.1: 30 0.04
Hewlett Packard xjet: 30 0.04
Intel NetportExpressPro/1.0: 30 0.04
HP Jet-Direct Print Server: 30 0.04
RealVNC/4.0: 30 0.04
Lexmark Optra Printer: 29 0.03
ServletExec: 0 0.00
Linksys Print Server: 0 0.00
Allied Telesyn Ethernet switch: 0 0.00
Netgear MR814v2 - IP_SHARER WEB 1.0: 0 0.00
Surgemail webmail (DManager): 0 0.00
--------------------------------------------------
3.Httsquash
Httsquash is a tool to scan the HTTP server.grab banner,and retrieve data.It supports IPV6,custom request types,and custom request URL.(Httsquash是扫描HTTP服务器的工具,收集banner和获取数据。)

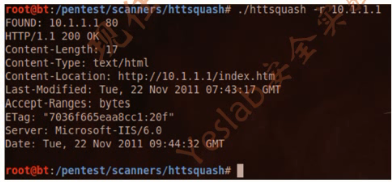
root@bt:~# cd /pentest/scanners/httsquash/
root@bt:/pentest/scanners/httsquash# ./httsquash -r 10.1.1.1
FOUND: 10.1.1.1 80
HTTP/1.1 200 OK
Content-Length: 5
Content-Type: text/html
Content-Location: http://10.1.1.1/index.html
Last-Modified: Fri, 10 Apr 2015 15:11:01 GMT
Accept-Ranges: bytes
ETag: "77a7448ea073d01:301"
Server: Microsoft-IIS/6.0
Date: Fri, 10 Apr 2015 17:49:56 GMT
root@bt:/pentest/scanners/httsquash# ./httsquash -r 10.1.1.2
FOUND: 10.1.1.2 80
HTTP/1.1 401 Unauthorized
Date: Fri, 01 Mar 2002 01:13:29 GMT
Server: cisco-IOS
Connection: close
Accept-Ranges: none
WWW-Authenticate: Basic realm="level_15 or view_access"
第五部分
VPN探测
1.ike-scan
ike-scan is a security tool that can be used to discover,fingerprint,and test IPSec VPN systems.It works by sending IKE phase-1 packets to the VPN servers and displaying any responses it received.Internet Key Exchange(IKE) is the key exchange and authentication mechanism used by IPsec.(ike-scan是一个IKE扫描工具,主要用于探测IPSec VPN服务器支持的策略。)

R1#conf t
R1(config)#crypto isakmp policy 10
R1(config-isakmp)#authentication pre-share
R1(config-isakmp)#exit
R1(config)#crypto isakmp key 0 smoke address 0.0.0.0 0.0.0.0
R1(config)#crypto ipsec transform-set smoke esp-des
R1(cfg-crypto-trans)#exit
R1(config)#crypto dynamic-map dymap 10
R1(config-crypto-map)#set transform-set smoke
R1(config)#crypto map smoke 10 ipsec-isakmp dynamic dymap
R1(config-if)#crypto map smoke
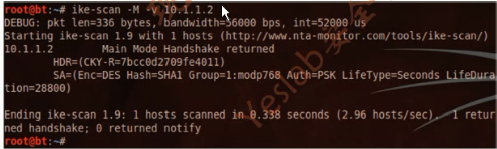
root@bt:~# ike-scan -M -v 10.1.1.2
DEBUG: pkt len=336 bytes, bandwidth=56000 bps, int=52000 us
Starting ike-scan 1.9 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
10.1.1.2 Main Mode Handshake returned
HDR=(CKY-R=e408852fe2107d63)
SA=(Enc=DES Hash=SHA1 Group=1:modp768 Auth=PSK LifeType=Seconds LifeDuration=28800)
Ending ike-scan 1.9: 1 hosts scanned in 0.138 seconds (7.25 hosts/sec). 1 returned handshake; 0 returned notify
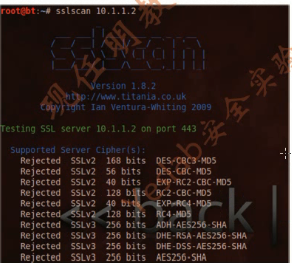
2.sslscan

R1(config)#ip http secure-server
R1(config)#ip http secure-ciphersuite rc4-128-sha
root@bt:~# sslscan 10.1.1.2
_
___ ___| |___ ___ __ _ _ __
/ __/ __| / __|/ __/ _` | '_ \
\__ \__ \ \__ \ (_| (_| | | | |
|___/___/_|___/\___\__,_|_| |_|
Version 1.8.2
http://www.titania.co.uk
Copyright Ian Ventura-Whiting 2009
Testing SSL server 10.1.1.2 on port 443
Supported Server Cipher(s):
Rejected SSLv2 168 bits DES-CBC3-MD5
Rejected SSLv2 56 bits DES-CBC-MD5
Rejected SSLv2 40 bits EXP-RC2-CBC-MD5
Rejected SSLv2 128 bits RC2-CBC-MD5
Rejected SSLv2 40 bits EXP-RC4-MD5
Rejected SSLv2 128 bits RC4-MD5
Rejected SSLv3 256 bits ADH-AES256-SHA
Rejected SSLv3 256 bits DHE-RSA-AES256-SHA
Rejected SSLv3 256 bits DHE-DSS-AES256-SHA
Rejected SSLv3 256 bits AES256-SHA
Rejected SSLv3 128 bits ADH-AES128-SHA
Rejected SSLv3 128 bits DHE-RSA-AES128-SHA
Rejected SSLv3 128 bits DHE-DSS-AES128-SHA
Rejected SSLv3 128 bits AES128-SHA
Rejected SSLv3 168 bits ADH-DES-CBC3-SHA
Rejected SSLv3 56 bits ADH-DES-CBC-SHA
Rejected SSLv3 40 bits EXP-ADH-DES-CBC-SHA
Rejected SSLv3 128 bits ADH-RC4-MD5
Rejected SSLv3 40 bits EXP-ADH-RC4-MD5
Rejected SSLv3 168 bits EDH-RSA-DES-CBC3-SHA
Rejected SSLv3 56 bits EDH-RSA-DES-CBC-SHA
Rejected SSLv3 40 bits EXP-EDH-RSA-DES-CBC-SHA
Rejected SSLv3 168 bits EDH-DSS-DES-CBC3-SHA
Rejected SSLv3 56 bits EDH-DSS-DES-CBC-SHA
Rejected SSLv3 40 bits EXP-EDH-DSS-DES-CBC-SHA
Rejected SSLv3 168 bits DES-CBC3-SHA
Rejected SSLv3 56 bits DES-CBC-SHA
Rejected SSLv3 40 bits EXP-DES-CBC-SHA
Rejected SSLv3 40 bits EXP-RC2-CBC-MD5
Accepted SSLv3 128 bits RC4-SHA
Rejected SSLv3 128 bits RC4-MD5
Rejected SSLv3 40 bits EXP-RC4-MD5
Rejected SSLv3 0 bits NULL-SHA
Rejected SSLv3 0 bits NULL-MD5
Rejected TLSv1 256 bits ADH-AES256-SHA
Rejected TLSv1 256 bits DHE-RSA-AES256-SHA
Rejected TLSv1 256 bits DHE-DSS-AES256-SHA
Rejected TLSv1 256 bits AES256-SHA
Rejected TLSv1 128 bits ADH-AES128-SHA
Rejected TLSv1 128 bits DHE-RSA-AES128-SHA
Rejected TLSv1 128 bits DHE-DSS-AES128-SHA
Rejected TLSv1 128 bits AES128-SHA
Rejected TLSv1 168 bits ADH-DES-CBC3-SHA
Rejected TLSv1 56 bits ADH-DES-CBC-SHA
Rejected TLSv1 40 bits EXP-ADH-DES-CBC-SHA
Rejected TLSv1 128 bits ADH-RC4-MD5
Rejected TLSv1 40 bits EXP-ADH-RC4-MD5
Rejected TLSv1 168 bits EDH-RSA-DES-CBC3-SHA
Rejected TLSv1 56 bits EDH-RSA-DES-CBC-SHA
Rejected TLSv1 40 bits EXP-EDH-RSA-DES-CBC-SHA
Rejected TLSv1 168 bits EDH-DSS-DES-CBC3-SHA
Rejected TLSv1 56 bits EDH-DSS-DES-CBC-SHA
Rejected TLSv1 40 bits EXP-EDH-DSS-DES-CBC-SHA
Rejected TLSv1 168 bits DES-CBC3-SHA
Rejected TLSv1 56 bits DES-CBC-SHA
Rejected TLSv1 40 bits EXP-DES-CBC-SHA
Rejected TLSv1 40 bits EXP-RC2-CBC-MD5
Failed TLSv1 128 bits RC4-SHA
Rejected TLSv1 128 bits RC4-MD5
Rejected TLSv1 40 bits EXP-RC4-MD5
Rejected TLSv1 0 bits NULL-SHA
Rejected TLSv1 0 bits NULL-MD5
Prefered Server Cipher(s):
SSLv3 128 bits RC4-SHA
SSL Certificate:
Version: 2
Serial Number: 1
Signature Algorithm: md5WithRSAEncryption
Issuer: /CN=IOS-Self-Signed-Certificate-998521732
Not valid before: Mar 1 01:25:10 2002 GMT
Not valid after: Jan 1 00:00:00 2020 GMT
Subject: /CN=IOS-Self-Signed-Certificate-998521732
Public Key Algorithm: rsaEncryption
RSA Public Key: (1024 bit)
Modulus (1024 bit):
00:e8:ad:d7:d1:95:f9:5c:5b:83:0a:21:3b:44:9b:
95:79:84:76:0f:cf:57:cd:e2:0e:44:d2:34:cc:d9:
0f:3b:05:0a:e7:c1:77:a2:eb:1f:60:52:9e:81:fa:
cb:86:86:74:95:a2:ac:b3:cc:d0:b1:1d:9d:88:c8:
fa:fe:c2:1d:ac:d7:0b:ef:fa:90:6e:b6:d2:26:51:
4e:13:11:e9:92:0c:f9:72:5b:fc:91:8c:0d:13:a8:
39:38:97:a5:4e:18:75:c5:1a:bc:dc:51:3a:ac:b7:
27:0a:85:a5:82:bf:70:94:4a:77:3f:f5:20:95:0b:
4c:0a:62:88:d6:3e:44:b4:6d
Exponent: 65537 (0x10001)
X509v3 Extensions:
X509v3 Basic Constraints: critical
CA:TRUE
X509v3 Subject Alternative Name:
DNS:R1.smoke.com
X509v3 Authority Key Identifier:
keyid:92:CD:40:DA:F6:C2:B2:C4:B8:F5:3D:A8:A0:80:0E:D9:36:8F:E8:03
X509v3 Subject Key Identifier:
92:CD:40:DA:F6:C2:B2:C4:B8:F5:3D:A8:A0:80:0E:D9:36:8F:E8:03
Verify Certificate:
self signed certificate



