BT5 0211

1.信息收集
2.扫描工具
3.漏洞发现
4.设备工程学工具
5.运用层攻击MSF
6.局域网攻击
7.密码破解
8.维持访问
内容简介
第一部分:DNS信息收集
第二部分:路由信息收集
第三部分:All-in-one智能收集
第一部分
DNS信息收集
1.Dnsmap介绍
1.Get extra names and subdomains utilizing the Google search engine.(使用google搜索引擎获取额外的名字与子域名)
2.Find out subdomain names by brute forcing the names from the text file.The dnsenum included in BackTrack comes with a file (dns.txt) containing 95 subdomain names.(使用一个TXT文件暴力破解子域名)
3.Carry out Whois queries on C-class domain network ranges and calculate its network ranges.(使用Whois查询C类网络范围,并且计算网络范围)
4.Carry out reverse lookup on network ranges.(反向查询)
5.Use threads to do different queries.(支持多重查询)
1.Dnsenum命令
root@bt:pentest/enumeration/dns/dnsenum#./dnsenum.pl -f dns.txt -dnsserver 8.8.8.8 cisco.com -o cisco.txt
1.-f dns.txt指定暴力破解文件,可以换ns-big.txt
2.-dnsserver指定dns服务器
3.cisco.com为目标域
4.-o cisco.txt输出到文件cisco.txt
root@bt:~# cd /pentest/enumeration/dns/dnsenum/
root@bt:/pentest/enumeration/dns/dnsenum# ls
cisco.com_ips.txt dnsenum.pl README.txt
cisco.txt dns.txt yeslab-cisco.txt
dns-big.txt output-yeslab.txt yeslab.net_ips.txt
dns.txt是暴力破解字典,比较小,dns-big.txt字典文件,比较大;
root@bt:/pentest/enumeration/dns/dnsenum# vim dns.txt
root@bt:/pentest/enumeration/dns/dnsenum# ./dnsenum.pl cisco.com
root@bt:/pentest/enumeration/dns/dnsenum# ./dnsenum.pl -f dns.txt --dnsserver ns1.cisco.com cisco.com -o output-smoke.txt
区域传送,主被DNS同步数据库,就会做区域传送,一般非信任服务器不允许你跟它去做区域传送;
DNS有两个协议UDP53和TCP53,为什么防火墙放的时候放UDP的53,不放TCP的53,因为正常询问都是UDP的,TCP53用于在两个服务器间做区域传送;
2.Dnsmap介绍
The dnsmap tool uses an approach similar to that of dnsenum to find out subdomains.It comes with a built-in wordlist for brute forcing,and it can also use a user-supplied wordlist.Additional features provided by dnsmap are that the results can be saved in the Comma Separated Value(CSV) format for further processing and it doesn't need a root privilege to run.
(非常类似于dnsenum,可以使用内建的"wordlist"来暴力破解子域,也可以使用用户自定义的"wordlist"。Dnsmap支持把结果输出为CSV格式。并且运行时不需要root选项。
2.Dnsmap命令
root@bt:/pentest/enumeration/dns/dnsmap#./dnsmap cisco.com -w wordlist_TLAs.txt -c cisco.csv
1.-w wordlist_TLAs.txt指定暴力破解文件
2.-c cisco.csv 输出文件
3.cisco.com 为目标域
root@bt:~# cd /pentest/enumeration/dns/dnsmap/
root@bt:/pentest/enumeration/dns/dnsmap# ./dnsmap cisco.com -w wordlist_TLAs.txt -c smoke.csv
第二部分
路由信息收集
1.tcptraceroute介绍(1)
The tcptraceroute can be used as a complement to the traditional traceroute command.While the traceroute is using UDP or ICMP ECHO to send out the packet with a Time To Live(TTL) of one,and incrementing it until reaching the target,the tcptraceroute is using TCP SYN to send out the packet to the target.
(传统traceroute技术发送UDP或者ICMP ECHO,但是tcptraceroute发送TCP SYN包到目标。)
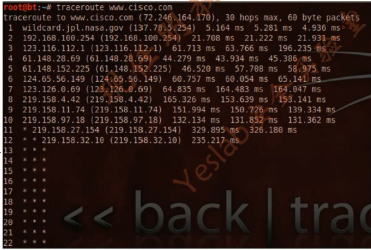
root@bt:~# traceroute www.cisco.com
传统traceroute技术在穿越防火墙效果并不是很好;
传统traceroute工作方式:
从发起方发一个包,这个包是UDP的包,目的端口是一个高端口,cisco的traceroute目的端口号是33434,第一个包TTL=1,到达第一跳TTL会超时,第二台路由器会向第一台路由器发送ICMP超时包,源IP地址是第二跳路由器,目的IP地址是第一台路由器,告诉源说TTL超时,源收到这个包会读取源IP地址,然后打印到屏幕上,这时候就知道第一跳是什么地址,第二个包是UDP的33435,在原来基础上端口号加1,TTL=2,TTL加1,同样在第二跳回ICMP超时包,中间路由器都是同样操作,但最后一台路由器,会回送ICMP超时,只是类型是端口不可达;
微软tracert工作方式:
直接发送echo request,中间设备也是回复ICMp超时包,到达目的地收到echo reply表示;
root@bt:~# tcptraceroute www.cisco.com
1.tcptraceroute介绍(2)
The advantage of using tcptraceroute that if there is a firewall sitting between the penetration tester and the target and it's blocking traceroute it still allows incoming TCP packet to certain TCP ports,and so by using tcptraceroute we will still be able to reach the target behind the firewall.
(使用tcptraceroute的好处在于,就算在目标之前存在防火墙,它阻止了普通的traceroute的流量,但是适当TCP端口的流量,防火墙是放行的,所以tcptraceroute能够穿越防火墙抵达目标)
tcptracetoute will receive a SYN/ACK packet if the port is open,and it will receive a RST packet if the port is closed.
(tcptraceroute收到SYN/ACK表示端口是开发的,收到RST表示端口是关闭的)
传统traceroute效果

Tcptraceroute效果

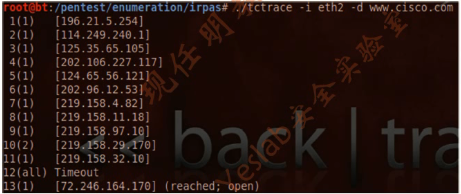
2.tctrace介绍
The tctrace tool is similar to tcptraceroute,but instead of using ICMP ECHO it uses the TCP SYN packet.
(tctrace工具非常类似于tcptraceroute,它不使用ICMP ECHO而是使用TCP SYN数据包)
Tctrace效果

root@bt:~# cd /pentest/enumeration/irpas/
root@bt:/pentest/enumeration/irpas# ./tctrace -i eth2 -d www.cisco.com
第三部分
All-in-one智能收集
Maltego介绍(1)
Maltego is an open source intelligence and forensics application.It allows you to mine and gather information,and represent the information in a meaningful way.
(Maltego是一个开发源的智能信息收集工具)
Maltego allows you to enumerate Internet infrastructure information,such as:
1.Domain names(域名)
2.DNS names(DNS名)
3.Whois information (Whois信息)
4.Network blocks(网段)
5.IP addresses(IP地址)
Maltego介绍(2)
It can also be used to gather information about people,such as:(还能够收集人的信息)
1.Companies and organizations related to the person(公司或者组织关联到的人)
2.E-mail address related to the person(电邮地址关联到的人)
3.Websites related to the person(网站关联到的人)
4.Social networks related to the person(社区网络关联到的人)
5.Phone numbers related to the person(电话号码关联到的人)
5.Phone numbers related to the person(电话号码关联到的人)
选择应用程序--BackTrack--Information Gathering--Network Analysis--DNS Analysis--maltego打开Maltego程序;



