Centos6.8配置HTTPS
HTTPS服务
http+openssl
环境要求:
CA证书: 192.168.1.103
网站服务器: 192.168.1.104
客户端: 192.168.1.107 (linux图形化界面)
内核:(客户端是centos 7图形化)
# cat /etc/centos-release
CentOS release 6.8 (Final
# uname -r
2.6.32-642.el6.x86_64
网站服务器配置:
# mkdir /opop
# cd /opop
# yum -y install openssl openssl-devel mod-ssl libcurl gcc* expat-devel pcre-devel
**********************************************************************************************
yum -y install gcc gcc-c++ autoconf libjpeg libjpeg-devel libpng libpng-devel freetype freetype-devel gd gd-devel libxml2 libxml2-devel zlib zlib-devel glibc glibc-devel glib2 glib2-devel bzip2 bzip2-devel ncurses ncurses-devel curl curl-devel e2fsprogs e2fsprogs-devel krb5 krb5-devel libidn libidn-devel openssl openssl-devel openldap openldap-devel nss_ldap openldap-clients openldap-servers 注:缺哪个依赖自己装上即可
***********************************************************************************************
注:要支持ssl加密功能就需要安装openssl openssl-devel mod_ssl
# wget http://mirrors.hust.edu.cn/apache//httpd/httpd-2.4.33.tar.gz
# wget http://mirrors.hust.edu.cn/apache//apr/apr-1.6.3.tar.gz
# wget http://mirrors.shu.edu.cn/apache//apr/apr-util-1.6.1.tar.gz
# wget https://ftp.pcre.org/pub/pcre/pcre-8.42.tar.gz // Pcre基于perl的兼容的正则表达式的支持
# wget https://github.com/nghttp2/nghttp2/releases/download/v1.24.0/nghttp2-1.24.0.tar.bz2
# wget https://curl.haxx.se/download/curl-7.60.0.tar.gz
# wget http://www.digip.org/jansson/releases/jansson-2.11.tar.gz
# wget https://jaist.dl.sourceforge.net/project/libpng/zlib/1.2.11/zlib-1.2.11.tar.gz
# for i in `ls`;do tar -zxvf $i;done
# tar -jxvf nghttp2-1.24.0.tar.bz2
# cd pcre-8.42
# ./configure && make && make install
# cd nghttp2-1.24.0
# ./configure && make && make install
# cd curl-7.60.0
# ./configure && make && make install
# cd zlib-1.2.11
# ./configure && make && make install
# cd jansson-2.11
# ./configure && make && make install
# cd ..
# cp -r apr-1.6.3 httpd-2.4.33/srclib/apr
# cp -r apr-util-1.6.1 httpd-2.4.33/srclib/apr-util
(有的需要自己装,有的可以直接发到httpd-2.4.33/srclib目录下,根据./configur时的提示进行修改)
安装Apache:
# cd httpd-2.4.33
# ./configure --prefix=/usr/local/apache2 --sysconfdir=/usr/local/apache2/etc --enable-ssl --with-crypto --with-included-apr --with-apr=/opop/httpd-2.4.33/srclib/apr --with-apr-util=/opop/httpd-2.4.33/srclib/apr-util --with-pcre=/opop/httpd-2.4.33/srclib/pcre/pcre-config --with-jansson=/opop/httpd-2.4.33/srclib/jansson --with-curl=/opop/httpd-2.4.33/srclib/curl --enable-http --enable-include --with-ldap
# make && make install
配置CA服务器端:
证书位置:cd /etc/pki/CA/
# cd /etc/pki/CA/
# (umask 077;openssl genrsa -out private/cakey.pem 2048) //这也是一条命令
注:openssl是命令,genrsa是要用rsa的算法输出(-out)一个在"当前"目录下的private目录的证书,证书长度为2048。
因为这个文件不能随意的看里面的内容才在命令的最开始用了文件的反码,077创建出来的文件权限就是700
打开证书的配置文件修改一些参数,使证书生成一些默认的值:
# vim /etc/pki/tls/openssl.cnf
[ req_distinguished_name ] //在req_distinguished_name区域内修改
countryName_default = CN //默认国家
stateOrProvinceName_default = BJ //默认省份,该条默认是注释状态
localityName_default = BJ //默认城市
0.organizationName_default = LENOVO //默认组织、公司
organizationalUnitName_default = cloud computing //默认单位名称,该条默认是注释状态,cloud computing是云计算的意思
生成证书:
# openssl req -new -x509 -key private/cakey.pem -out cacert.pem -days 3650 //因为在模板里面已经配置好所以下面只要全部回车即可
Country Name (2 letter code) [CN]: //回车
State or Province Name (full name) [BJ]: //回车
Locality Name (eg, city) [BJ]: //回车
Organization Name (eg, company) [LENOVO]: //回车
Organizational Unit Name (eg, section) [cloud computing]: //回车
Common Name (eg, your name or your server's hostname) []: //回车
Email Address []:root@djkk.com //手动输入一个邮箱地址即可
返回到网站服务器端:
# cd /usr/local/apache2/
# mkdir ssl
# cd ssl/
# (umask 077;openssl genrsa 1024 > httpd.key)
# openssl req -new -key httpd.key -out httpd.crq
Country Name (2 letter code) [XX]: CN //手动输入,要和证书服务器上的一致
State or Province Name (full name) []:BJ //手动输入,要和证书服务器上的一致
Locality Name (eg, city) [Default City]:BJ //手动输入,要和证书服务器上的一致
Organization Name (eg, company) [Default Company Ltd]:LENOVO //手动输入,要和证书服务器上的一致
Organizational Unit Name (eg, section) []:cloud computing //手动输入,要和证书服务器上的一致
Common Name (eg, your name or your server's hostname) []:www.biubiubiu.com //这里你的网站是什么域名就写什么
Email Address []:root@djkk.com //邮箱按需定即可
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []: //额外信息按需配置,会和证书一起颁发出去,我这里没写额外的信息,回车
An optional company name []: //额外信息按需配置,会和证书一起颁发出去,我这里没写额外的信息,回车
注:将生成的httpd.crq发送到CA服务器上的/tmp目录,该步一定要注意....
# scp httpd.crq 192.168.1.103:/tmp
启用虚拟主机:
# vim /usr/local/apache2/etc/httpd.conf
Include etc/extra/httpd-vhosts.conf //启用该选项,默认是关闭状态
进行虚拟主机的配置:
# cp /usr/local/apache2/etc/extra/httpd-vhosts.conf /usr/local/apache2/etc/extra/httpd-vhosts.conf.bak
# vim /usr/local/apache2/etc/extra/httpd-vhosts.conf
<VirtualHost *:80>
DocumentRoot "/usr/local/apache2/htdocs/www"
ServerName www.biubiubiu.com
</VirtualHost>
<VirtualHost *:80>
DocumentRoot "/usr/local/apache2/htdocs/edu"
ServerName edu.biubiubiu.com
</VirtualHost>
//虚拟主机区域留2个区域即可,其他全部注释并进行修改
生成主页文件:
# cd /usr/local/apache2/htdocs/
# mkdir www edu
# vim www/index.html
Finally finished.....
# vim edu/index.html
It's not easy....
打开win系统上面 C:\Windows\System32\drivers\etc 中hosts文件进行添加网站服务器进行测试:
192.168.1.104 www.biubiubiu.com
192.168.1.104 edu.biubiubiu.com
启动Apache服务:
# /usr/local/apache2/bin/apachectl start {restart | stop}
在 win 系统上访问 www.biubiubiu.com 和 edu.biubiubiu.com 域名进行测试
回到CA服务器:
[root@192 CA]# pwd
/etc/pki/CA
# touch index.txt
# echo "00" > serial //数字0
签署证书:
# openssl ca -in /tmp/httpd.crq -out /tmp/httpd.crt -days 3650 //注意:一个是crq,一个是crt。按2次y即可
# ll /tmp/ //查看证书有没成功签署
回到网站服务器:
# scp 192.168.1.103:/tmp/httpd.crt . //将CA服务器上生成的证书拿到当前/usr/local/apache2/ssl目录下,不要忘记后面的 点
//此时CA服务器上的crq和crt文件就没用了可以删除掉
证书申请成功,需要让证书在网站生效:
# vim /usr/local/apache2/etc/httpd.conf
Include etc/extra/httpd-ssl.conf //启用该项,默认是注释状态
修改ssl模板的配置文件:
# vim /usr/local/apache2/etc/extra/httpd-ssl.conf
Listen 443 //监听44端口
...........略一部分内容..............
<VirtualHost _default_:443>
# General setup for the virtual host
DocumentRoot "/usr/local/apache2/htdocs/www" //网页在什么位置
ServerName www.biubiubiu.com:443 //改成自己的域名
#ServerAdmin you@example.com //注释掉
#ErrorLog "/usr/local/apache2/logs/error_log" //注释掉
#TransferLog "/usr/local/apache2/logs/access_log" //注释掉
...........略一部分内容..............
SSLEngine on //启用加密的引擎
...........略一部分内容..............
SSLCertificateFile "/usr/local/apache2/ssl/httpd.crt" //证书位置
...........略一部分内容..............
SSLCertificateKeyFile "/usr/local/apache2/ssl/httpd.key" //秘钥位置
# /usr/local/apache2/bin/apachectl -t //检查Apache配置文件语法,这里会有一个语法错误.....
AH00526: Syntax error on line 52 of /usr/local/apache2/etc/extra/httpd-ssl.conf:
Invalid command 'SSLCipherSuite', perhaps misspelled or defined by a module not included in the server configuration
解决办法:
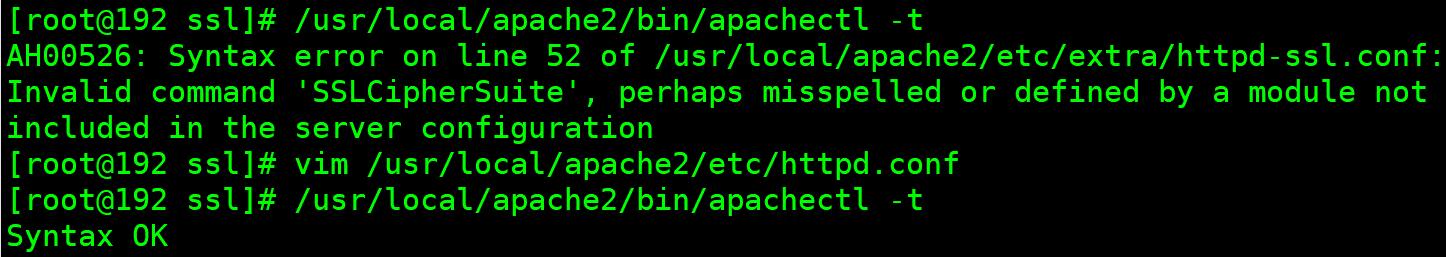
# vim /usr/local/apache2/etc/httpd.conf
LoadModule socache_shmcb_module modules/mod_socache_shmcb.so //启用该模块
...........略一部分内容..............
LoadModule ssl_module modules/mod_ssl.so //启用该模块
再来检查语法:
# /usr/local/apache2/bin/apachectl -t
Syntax OK //检查通过
重启Apache服务:
# /usr/local/apache2/bin/apachectl restart
客户端测试:
# vim /etc/hosts
192.168.1.104 www.biubiubiu.com
打开火狐浏览器访问 https://www.biubiubiu.com 和 https://edu.biubiubiu.com(会提示"您的连接不安全"字样)
高级--->添加例外--->查看--->(即能查看到我们的证书)--->确认安全例外--->即能查看到网页的具体内容--->完毕
注意:不同的浏览器显示出来的"效果"也会不同,注意访问时的"正确性"



 浙公网安备 33010602011771号
浙公网安备 33010602011771号