buuctf reverse [GUET-CTF2019]encrypt
无壳,64位程序,直接拖进ida
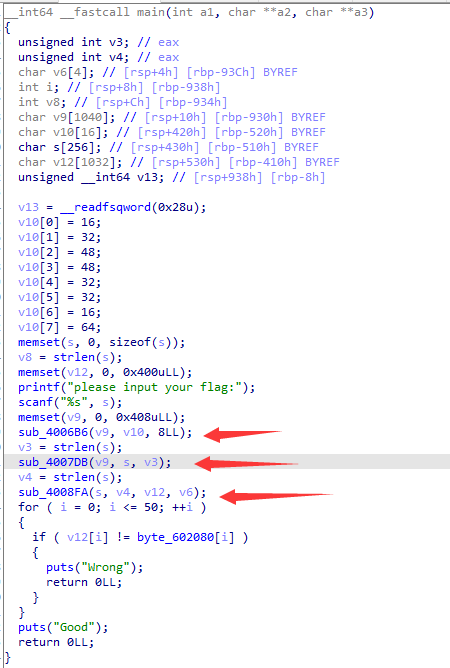
前面逻辑比较简单,就是通过rc4加密然后base64转码之后与密文进行对比。
主要看一下最后面base64加密这块,他没有给提供加密表
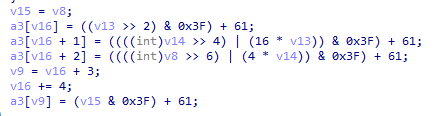
通过查看这一部分可以获取base64的加密段
data=[0x5a, 0x60, 0x54, 0x7A, 0x7A, 0x54, 0x72, 0x44,0x7C, 0x66, 0x51, 0x50, 0x5B, 0x5F, 0x56, 0x56,0x4C, 0x7C, 0x79, 0x6E, 0x65, 0x55, 0x52, 0x79,0x55, 0x6D, 0x46, 0x6B, 0x6C, 0x56, 0x4A, 0x67,0x4C, 0x61, 0x73, 0x4A, 0x72, 0x6F, 0x5A, 0x70,0x48, 0x52, 0x78, 0x49, 0x55, 0x6C, 0x48, 0x5C,0x76, 0x5A, 0x45, 0x3D] flag='' for i in range(0,len(data),4): flag+=hex((((data[i]-0x3D)&0x3F)<<2)|(((data[i+1]-0x3D)&0x30)>>4))+',' flag+=hex((((data[i+1]-0x3D)&0x0F)<<4)|(((data[i+2]-0x3D)&0x3C)>>2))+',' flag+=hex(((data[i+3]-0x3D)&0x3F)|((data[i+2]-0x3D)&0x03)<<6)+',' print(flag)
然后可以进行rc4解密了。
flag{e10adc3949ba59abbe56e057f20f883e}


 浙公网安备 33010602011771号
浙公网安备 33010602011771号