Kubernetes V1.17集群部署并部署Metrics Server插件(一)无坑!!!
环境信息:
| 操作系统 | 主机名 | IP地址 |
|---|---|---|
| CentOS 7.6 | k8s-master | 9.110.187.20 |
| CentOS 7.6 | k8s-node1 | 9.110.187.23 |
| CentOS 7.6 | k8s-node2 | 9.110.187.24 |
1. 安装环境
在开始之前,部署Kubernetes集群机器需要满足以下几个条件:
- 操作系统 CentOS7.7-86_x64
- 硬件配置:4GB内存,4个CPU,硬盘50GB
- 集群中所有机器之间网络互通
- 可以访问外网,需要拉取镜像
- 禁止swap分区
2. 学习目标
- 在所有节点上安装Docker和kubeadm
- 部署Kubernetes Master
- 部署容器网络插件
- 部署 Kubernetes Node,将节点加入Kubernetes集群中
- 部署Dashboard Web页面,可视化查看Kubernetes资源
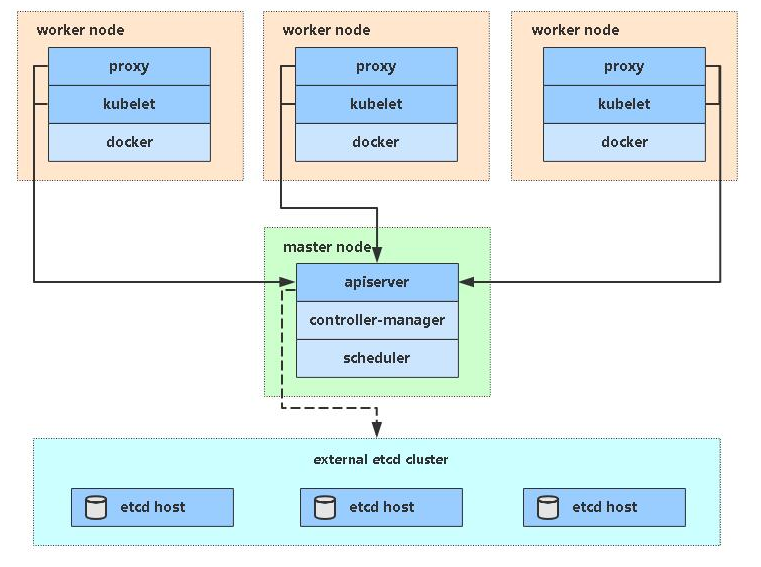
3. 准备环境
关闭防火墙: $ systemctl stop firewalld $ systemctl disable firewalld 关闭selinux: $ sed -i 's/enforcing/disabled/' /etc/selinux/config $ setenforce 0 关闭swap: $ swapoff -a 临时 $ sed -i '/ swap / s/^\(.*\)$/#\1/g' /etc/fstab 永久 添加主机名与IP对应关系(记得设置主机名): $ cat >> /etc/hosts << EOF 9.110.187.20 k8s-master 9.110.187.23 k8s-node1 9.110.187.24 k8s-node2 EOF 将桥接的IPv4流量传递到iptables的链: $ cat > /etc/sysctl.d/kubernetes.conf << EOF net.bridge.bridge-nf-call-iptables=1 net.bridge.bridge-nf-call-ip6tables=1 net.ipv4.ip_forward=1 net.ipv4.tcp_tw_recycle=0 vm.swappiness=0 vm.overcommit_memory=1 vm.panic_on_oom=0 fs.inotify.max_user_instances=8192 fs.inotify.max_user_watches=1048576 fs.file-max=52706963 fs.nr_open=52706963 net.ipv6.conf.all.disable_ipv6=1 net.netfilter.nf_conntrack_max=2310720 EOF $ sysctl -p /etc/sysctl.d/kubernetes.conf
时间同步:
$ yum install ntpdate -y $ ntpdate time.windows.com $ echo "time.windows.com" >> /etc/rc.d/rc.local $ chmod +x /etc/rc.d/rc.local
4. 所有节点安装Docker/kubeadm/kubelet
4.1 安装Docker
$ wget https://mirrors.aliyun.com/docker-ce/linux/centos/docker-ce.repo -O /etc/yum.repos.d/docker-ce.repo $ yum -y install docker-ce-18.06.1.ce-3.el7 #指定版本安装 $ systemctl enable docker && systemctl start docker $ docker --version Docker version 18.06.1-ce, build e68fc7a $ cat > /etc/docker/daemon.json << EOF { "registry-mirrors": ["https://b9pmyelo.mirror.aliyuncs.com"], # "insecure-registries": ["9.110.187.200"], # 内网镜像仓库 "exec-opts": ["native.cgroupdriver=systemd"], "log-driver": "json-file", "log-opts": { "max-size": "100m" }, "storage-driver": "overlay2" } EOF $ systemctl start docker && systemctl enable docker
4.2 添加阿里云YUM软件源
$ cat > /etc/yum.repos.d/kubernetes.repo << EOF [kubernetes] name=Kubernetes baseurl=https://mirrors.aliyun.com/kubernetes/yum/repos/kubernetes-el7-x86_64 enabled=1 gpgcheck=0 repo_gpgcheck=0 gpgkey=https://mirrors.aliyun.com/kubernetes/yum/doc/yum-key.gpg https://mirrors.aliyun.com/kubernetes/yum/doc/rpm-package-key.gpg EOF
4.3 安装kubeadm,kubelet和kubectl
指定版本号部署:
$ yum install -y kubelet-1.17.0 kubeadm-1.17.0 kubectl-1.17.0 $ systemctl enable kubelet
5. 部署Kubernetes Master
在192.168.31.63(Master)执行。
$ kubeadm init \ --apiserver-advertise-address=9.110.187.20 \ --image-repository registry.aliyuncs.com/google_containers \ --kubernetes-version v1.17.0 \ --service-cidr=10.96.0.0/12 \ --pod-network-cidr=10.244.0.0/16
由于默认拉取镜像地址k8s.gcr.io国内无法访问,这里指定阿里云镜像仓库地址。
使用kubectl工具:
$ mkdir -p $HOME/.kube $ sudo cp -i /etc/kubernetes/admin.conf $HOME/.kube/config $ sudo chown $(id -u):$(id -g) $HOME/.kube/config $ kubectl get nodes kubectl自动补全 # yum -y install bash-completion $ source <(kubectl completion bash) $ echo "source <(kubectl completion bash)" >> ~/.bashrc
6. 安装Pod网络插件(CNI)
$ kubectl apply -f https://raw.githubusercontent.com/coreos/flannel/a70459be0084506e4ec919aa1c114638878db11b/Documentation/kube-flannel.yml
确保能够访问到quay.io这个registery。
如果下载失败,可以改成这个镜像地址:lizhenliang/flannel:v0.11.0-amd64
7. 加入Kubernetes Node
在9.110.187.23/24(Node)执行。
向集群添加新节点,执行在kubeadm init输出的kubeadm join命令:
$ kubeadm join 9.110.187.20:6443 --token vbuwrx.cebhdl5aasy2072f \ > --discovery-token-ca-cert-hash sha256:960cfddc695e71edcc7c2ea3b3def734f737ec15d357c1382d5dda362fe37f21
8. 测试kubernetes集群
在Kubernetes集群中创建一个pod,验证是否正常运行:
$ kubectl create deployment nginx --image=nginx $ kubectl expose deployment nginx --port=80 --type=NodePort $ kubectl get pod,svc
9. 部署 Dashboard
$ wget https://raw.githubusercontent.com/kubernetes/dashboard/v2.0.0-beta5/aio/deploy/recommended.yaml
修改recommended.yaml文件内容(vi recommended.yaml):
#增加直接访问端口 kind: Service apiVersion: v1 metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard namespace: kubernetes-dashboard spec: type: NodePort #增加 ports: - port: 443 targetPort: 8443 nodePort: 30001 #增加 selector: k8s-app: kubernetes-dashboard #因为自动生成的证书很多浏览器无法使用,所以我们自己创建,注释掉kubernetes-dashboard-certs对象声明 #apiVersion: v1 #kind: Secret #metadata: # labels: # k8s-app: kubernetes-dashboard # name: kubernetes-dashboard-certs # namespace: kubernetes-dashboard #type: Opaque
####创建证书 $ mkdir dashboard-certs $ cd dashboard-certs/ #创建命名空间 $ kubectl create namespace kubernetes-dashboard #yaml里会自动创建,可以不用单独创建 # 创建key文件 $ openssl genrsa -out dashboard.key 2048 #证书请求 $ openssl req -days 36000 -new -out dashboard.csr -key dashboard.key -subj '/CN=dashboard-cert' #自签证书 $ openssl x509 -req -in dashboard.csr -signkey dashboard.key -out dashboard.crt #创建kubernetes-dashboard-certs对象 $ kubectl create secret generic kubernetes-dashboard-certs --from-file=dashboard.key --from-file=dashboard.crt -n kubernetes-dashboard 部署Dashboard 涉及到的两个镜像可以先下载下来 #安装 $ kubectl create -f ~/recommended.yaml #检查结果 $ kubectl get pods -A -o wide $ kubectl get service -n kubernetes-dashboard -o wide 9.创建dashboard管理员 $ cat >> dashboard-admin.yaml<<EOF apiVersion: v1 kind: ServiceAccount metadata: labels: k8s-app: kubernetes-dashboard name: dashboard-admin namespace: kubernetes-dashboard EOF $ kubectl create -f dashboard-admin.yaml 为用户分配权限: $ cat >>dashboard-admin-bind-cluster-role.yaml<<EOF apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRoleBinding metadata: name: dashboard-admin-bind-cluster-role labels: k8s-app: kubernetes-dashboard roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: cluster-admin subjects: - kind: ServiceAccount name: dashboard-admin namespace: kubernetes-dashboard EOF $ kubectl create -f dashboard-admin-bind-cluster-role.yaml
访问地址:http://NodeIP:30001
创建service account并绑定默认cluster-admin管理员集群角色:
$ kubectl create serviceaccount dashboard-admin -n kube-system
$ kubectl create clusterrolebinding dashboard-admin --clusterrole=cluster-admin --serviceaccount=kube-system:dashboard-admin
$ kubectl describe secrets -n kube-system $(kubectl -n kube-system get secret | awk '/dashboard-admin/{print $1}')
使用输出的token登录Dashboard。
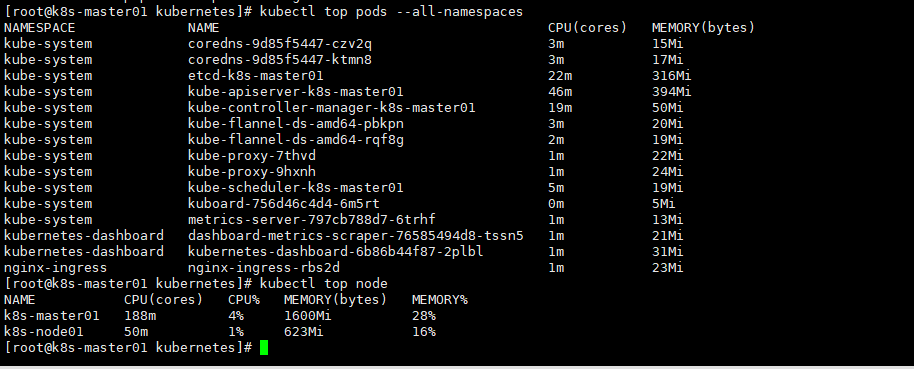
10.安装metrics-server
在Node1/Node2上下载镜像文件:
$ docker pull bluersw/metrics-server-amd64:v0.3.6 $ docker tag bluersw/metrics-server-amd64:v0.3.6 k8s.gcr.io/metrics-server-amd64:v0.3.6
在Master上执行安装:
$ git clone https://github.com/kubernetes-incubator/metrics-server.git $ cd /metrics-server/deploy/kubernetes
修改metrics-server-deployment.yaml
spec: hostNetwork: true # 新增 serviceAccountName: metrics-server volumes: # mount in tmp so we can safely use from-scratch images and/or read-only containers - name: tmp-dir emptyDir: {} containers: - name: metrics-server image: k8s.gcr.io/metrics-server-amd64:v0.3.6 args: - --cert-dir=/tmp - --secure-port=4443 - --kubelet-insecure-tls # 新增 - --kubelet-preferred-address-types=InternalIP,Hostname,InternalDNS,ExternalDNS,ExternalIP # 新增 imagePullPolicy: IfNotPresent # 修改
$ kubectl create -f . 如果不能不能FQ拉取不到镜像可以更改image: registry.cn-hangzhou.aliyuncs.com/google_containers/metrics-server-amd64:v0.3.6
参考李振良老师的博客:https://blog.51cto.com/lizhenliang/2296100
作者:一毛
本博客所有文章仅用于学习、研究和交流目的,欢迎非商业性质转载。
不管遇到了什么烦心事,都不要自己为难自己;无论今天发生多么糟糕的事,都不应该感到悲伤。记住一句话:越努力,越幸运。





【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· Linux系列:如何用heaptrack跟踪.NET程序的非托管内存泄露
· 开发者必知的日志记录最佳实践
· SQL Server 2025 AI相关能力初探
· Linux系列:如何用 C#调用 C方法造成内存泄露
· AI与.NET技术实操系列(二):开始使用ML.NET
· 无需6万激活码!GitHub神秘组织3小时极速复刻Manus,手把手教你使用OpenManus搭建本
· C#/.NET/.NET Core优秀项目和框架2025年2月简报
· 什么是nginx的强缓存和协商缓存
· 一文读懂知识蒸馏
· Manus爆火,是硬核还是营销?