core的jwt使用
下载项目zradmin,参考使用jwt;官方地址:http://www.izhaorui.cn/doc/
jwt的封装修改用户基本模板就行
配置文件
"JwtSettings": { "Issuer": "ZRAdmin.NET", "Audience": "ZRAdmin.NET", "SecretKey": "SecretKey-ZRADMIN.NET-202308010121212", "Expire": 1440 //jwt登录过期时间(分) },
public class JwtSettings { /// <summary> /// token是谁颁发的 /// </summary> public string Issuer { get; set; } /// <summary> /// token可以给那些客户端使用 /// </summary> public string Audience { get; set; } /// <summary> /// 加密的key(SecretKey必须大于16个,是大于,不是大于等于) /// </summary> public string SecretKey { get; set; } /// <summary> /// token时间(分) /// </summary> public int Expire { get; set; } = 1440; }
封装的代码
public class JwtUtil { /// <summary> /// 获取用户身份信息 /// </summary> /// <param name="httpContext"></param> /// <returns></returns> public static LoginUser GetLoginUser(HttpContext httpContext) { //string token = httpContext.GetToken(); string token = httpContext.Request.Headers["Authorization"]; if (!string.IsNullOrEmpty(token)) { return ValidateJwtToken(ParseToken(token)); } return null; } /// <summary> /// 生成token /// </summary> /// <param name="claims"></param> /// <param name="jwtSettings"></param> /// <returns></returns> public static string GenerateJwtToken(List<Claim> claims, JwtSettings jwtSettings) { var authTime = DateTime.Now; var expiresAt = authTime.AddMinutes(jwtSettings.Expire); var tokenHandler = new JwtSecurityTokenHandler(); var key = Encoding.ASCII.GetBytes(jwtSettings.SecretKey); claims.Add(new Claim("Audience", jwtSettings.Audience)); claims.Add(new Claim("Issuer", jwtSettings.Issuer)); var tokenDescriptor = new SecurityTokenDescriptor { Subject = new ClaimsIdentity(claims), Issuer = jwtSettings.Issuer, Audience = jwtSettings.Audience, IssuedAt = authTime,//token生成时间 Expires = expiresAt, //NotBefore = authTime, TokenType = "Bearer", //对称秘钥,签名证书 SigningCredentials = new SigningCredentials(new SymmetricSecurityKey(key), SecurityAlgorithms.HmacSha256Signature) }; var token = tokenHandler.CreateToken(tokenDescriptor); return tokenHandler.WriteToken(token); } /// <summary> /// 验证Token /// </summary> /// <returns></returns> public static TokenValidationParameters ValidParameters() { JwtSettings jwtSettings = new(); AppSettings.Bind("JwtSettings", jwtSettings); if (jwtSettings == null || jwtSettings.SecretKey.IsNullOrEmpty()) { throw new Exception("JwtSettings获取失败"); } var key = Encoding.ASCII.GetBytes(jwtSettings.SecretKey); var tokenDescriptor = new TokenValidationParameters { ValidateIssuerSigningKey = true, ValidateIssuer = true, ValidateAudience = true, ValidIssuer = jwtSettings.Issuer, ValidAudience = jwtSettings.Audience, IssuerSigningKey = new SymmetricSecurityKey(key), ValidateLifetime = true,//是否验证Token有效期,使用当前时间与Token的Claims中的NotBefore和Expires对比 ClockSkew = TimeSpan.FromSeconds(30) //RequireExpirationTime = true,//过期时间 }; return tokenDescriptor; } /// <summary> /// 从令牌中获取数据声明 /// </summary> /// <param name="token">令牌</param> /// <returns></returns> public static IEnumerable<Claim> ParseToken(string token) { var tokenHandler = new JwtSecurityTokenHandler(); var validateParameter = ValidParameters(); token = token.Replace("Bearer ", ""); try { tokenHandler.ValidateToken(token, validateParameter, out SecurityToken validatedToken); var jwtToken = tokenHandler.ReadJwtToken(token); return jwtToken.Claims; } catch (Exception ex) { Console.WriteLine(ex.Message); // return null if validation fails return null; } } /// <summary> /// jwt token校验 /// </summary> /// <param name="jwtToken"></param> /// <returns></returns> public static LoginUser ValidateJwtToken(IEnumerable<Claim> jwtToken) { try { var userData = jwtToken.FirstOrDefault(x => x.Type == ClaimTypes.UserData).Value; var loginUser = JsonConvert.DeserializeObject<LoginUser>(userData); //var permissions = CacheService.GetUserPerms(GlobalConstant.UserPermKEY + loginUser?.UserId); //if (loginUser?.UserName == "admin") //{ // permissions = new List<string>() { GlobalConstant.AdminPerm }; //} //if (permissions == null) return null; //loginUser.Permissions = permissions; return loginUser; } catch (Exception ex) { Console.WriteLine(ex.Message); return null; } } /// <summary> ///组装Claims /// </summary> /// <param name="user"></param> /// <returns></returns> public static List<Claim> AddClaims(LoginUser user) { if (user?.Permissions.Count > 50) { user.Permissions = new List<string>(); } var claims = new List<Claim>() { new Claim(ClaimTypes.PrimarySid, user.UserId.ToString()), new Claim(ClaimTypes.Name, user.UserName), new Claim(ClaimTypes.UserData, JsonConvert.SerializeObject(user)) }; return claims; } }
启动配置加载jwt
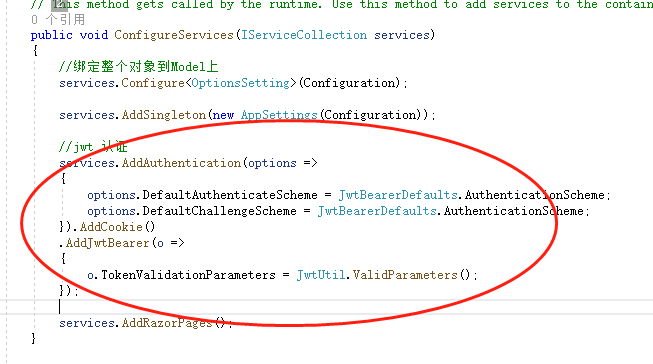
在登录的时候生成jwt
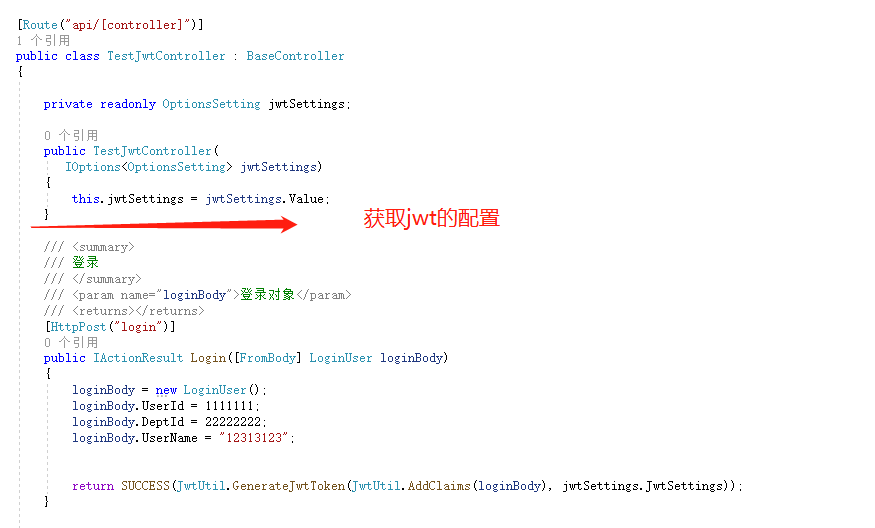
在请求路径过滤验证token
public class VerifyAttribute : Attribute, IAuthorizationFilter { //static readonly Logger logger = LogManager.GetCurrentClassLogger(); /// <summary> /// 只判断token是否正确,不判断权限 /// 如果需要判断权限的在Action上加上ApiActionPermission属性标识权限类别,ActionPermissionFilter作权限处理 /// </summary> /// <param name="context"></param> public void OnAuthorization(AuthorizationFilterContext context) { var noNeedCheck = false; if (context.ActionDescriptor is ControllerActionDescriptor controllerActionDescriptor) { noNeedCheck = controllerActionDescriptor.MethodInfo.GetCustomAttributes(inherit: true) .Any(a => a.GetType().Equals(typeof(AllowAnonymousAttribute))); } if (noNeedCheck) return; //string ip = HttpContextExtension.GetClientUserIp(context.HttpContext); string url = context.HttpContext.Request.Path; var isAuthed = context.HttpContext.User.Identity.IsAuthenticated; //使用jwt token校验2020-11-21 LoginUser info = JwtUtil.GetLoginUser(context.HttpContext); if (info == null) // || !isAuthed { string msg = $"请求访问[{url}]失败,无法访问系统资源"; //logger.Info($"{msg}"); context.Result = new JsonResult(new ApiResult((int)ResultCode.DENY, msg)); } } }
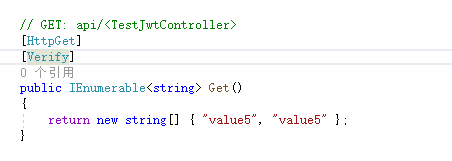
在需要验证的方法加上特性
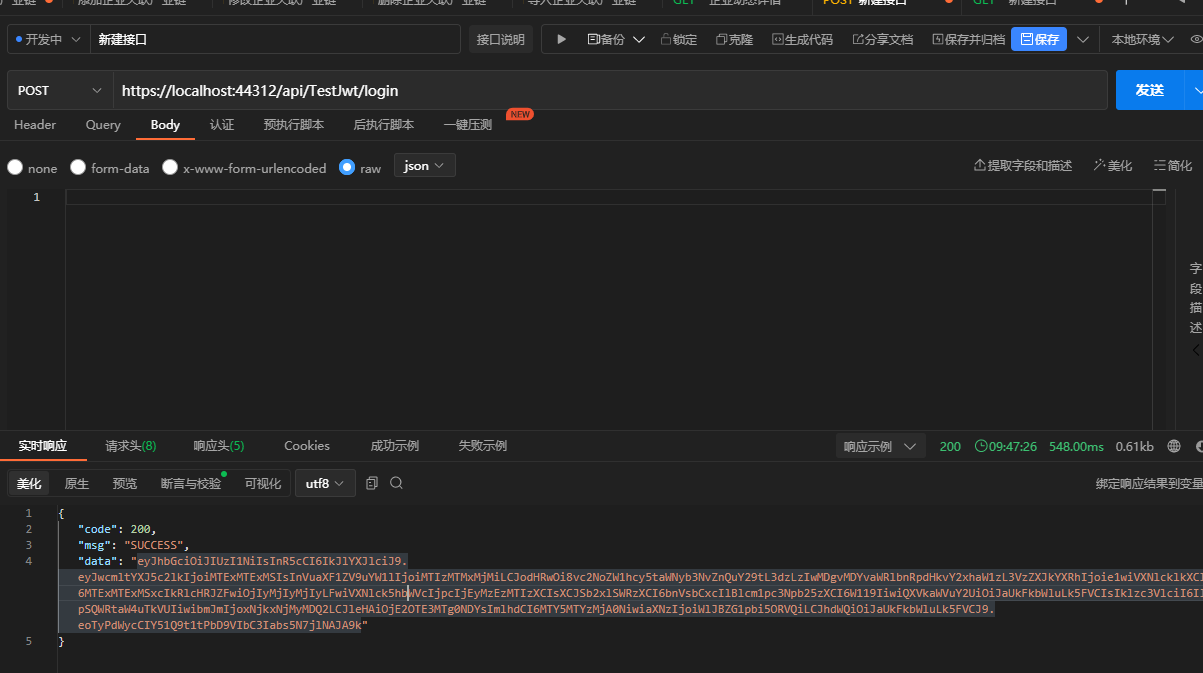
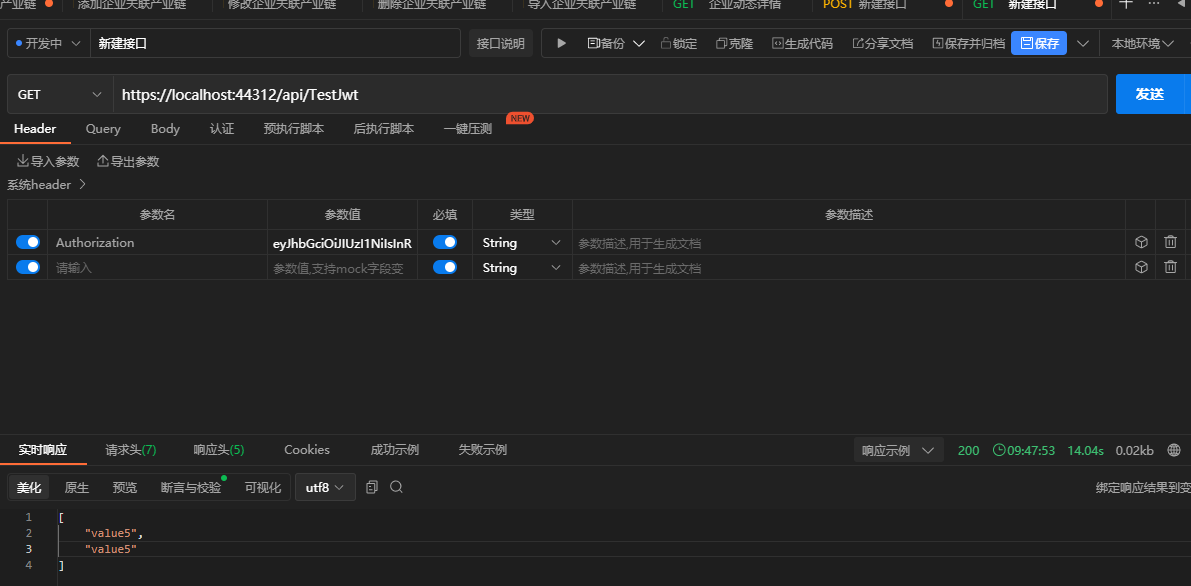
测试的结果






【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 无需6万激活码!GitHub神秘组织3小时极速复刻Manus,手把手教你使用OpenManus搭建本
· C#/.NET/.NET Core优秀项目和框架2025年2月简报
· Manus爆火,是硬核还是营销?
· 终于写完轮子一部分:tcp代理 了,记录一下
· 【杭电多校比赛记录】2025“钉耙编程”中国大学生算法设计春季联赛(1)
2020-08-10 sql的索引碎片查看和重建(转载)