flask的session解读及flask_login登录过程研究
#!/usr/bin/env python # -*- coding: utf-8 -*- from itsdangerous import URLSafeTimedSerializer from flask.sessions import TaggedJSONSerializer import hashlib s=URLSafeTimedSerializer('some_random_key','cookie-session',serializer=TaggedJSONSerializer(),signer_kwargs={'key_derivation':'hmac','digest_method':hashlib.sha1}) result = s.loads('.eJytkkFv4jAQhf_KymcOxLSHReohUVg30noiUBLvuEIoCSmOY1OJQAmu-O91aFW19z1ZGr_3ed6M38jm2ZS9anoyf3ojv44fR0XmpBT3tjo_PJDr5LOSs8HgPzAJG14lNafkcfWasD8aaeHqSzQtmXHJY6QkzU_kur75vgHrWfEh_QEV4neQMKW2Nt-hLUzVRn1Ft3splrtS3P0fUDUrpn93o3p9XU_Ipt2S-adNxvWU6y6QejcDhxRdSNNMae4iAywPOC06sPkAMZ65Tc7goOVaGdDhkGboQNcUdH4GVhi0iwu62teV5QwHtHgBtwhQJ05afpeKlfW6FrPIooXWt2mlxgEcD0Ag5Y77HgrLM6-OO8rZksqY3_MsUjxejmFJ3R-eN8eXrtl_RQANejSj4xTFYpA66vxTOo3DAV2hUx9DarCoPdYZhWPc8DY70vbh1raedTycmgk59c3hi7sUq6NfwU03XuxL24wf42a4vgOsyrm7.DJDfoQ.lPf6Vla0QXeI1yOYs0riql1Lywk') print '破解后:',result
破解后: {u'username': u'admin', u'csrf_token': '1b5037f10f247e0f8076145220db705b0baaaac5', u'user_id': u'1', u'_flashes': [('info', 'Please login to access this page.'), ('success', 'You have been logged in.')], u'_fresh': True, u'isAdmin': True, u'user': 'Admin', u'_id': 'c758c876c082eb509c0d1b6cf7de18daf4bd77a1d61b10ab0e32fec6dfc2efe7594c7aae02b4f96cc887ed2f1dc4d0ba58cc8cba97205abda3944e51c44b0727'}
1、username要和user_id保持对应
2、_id是采取的真实来源IP(X-Forwarded-For)和http请求头中的User-Agent经过计算而来
1、使用上面的方法解析flask的登录过程
首次登录某个页面,跳转到登录验证界面,返回cookie内容:.eJyrVopPy0kszkgtVrKKrlZSKIFQSUpWSonhprlJ5ba2SrU6UJFQ94qcyAi_HE_3irIoo5xST4-gMk93t6xIo7Cq5Eong0T3nCpPD6eMKKPQUqXaWCAEAJf8Hr4.DJI1lQ.hSLLzh_2xt_KwRnPRdox-OubPnY
解析:{u'_flashes': [('info', 'Please login to access this page.')]}
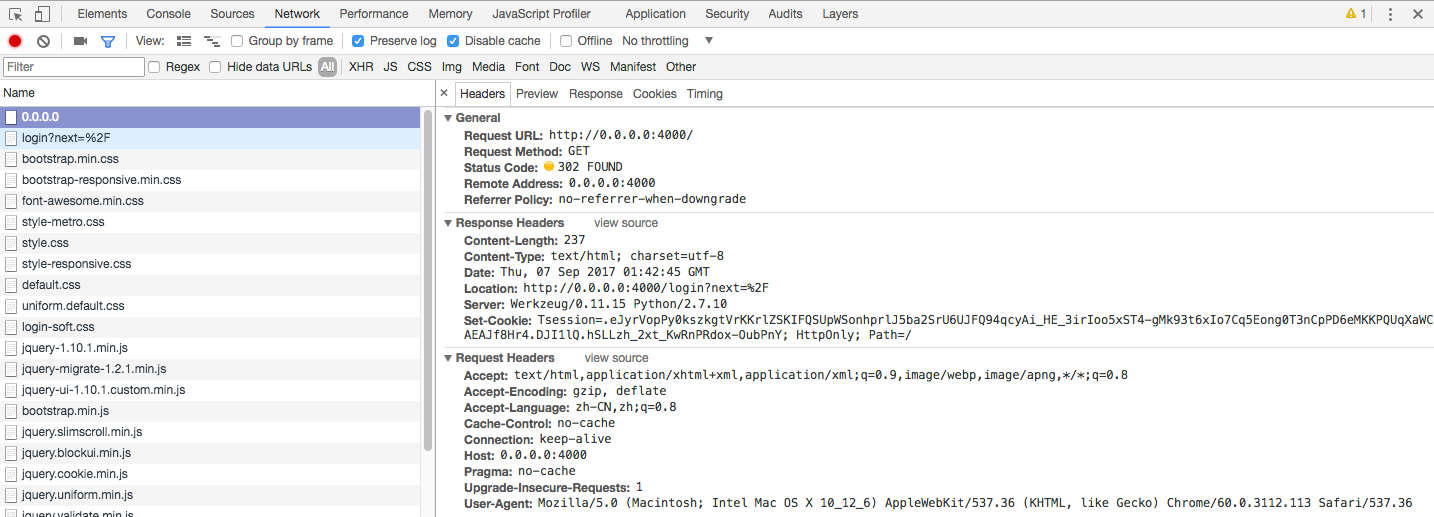
浏览器根据返回的Location地址向服务器发出申请,带上上次服务器返回的cookie值,服务器收到请求后返回响应内容,这次返回的cookie是:
.eJwtjk8LgjAcQL9K_M4ebNFF8CLm3MFBwVpbiKhoMmdB_pl_8LtX5OnBOzzeAkmp07YqWnDuC-y6PzJwIOXHJjOuC6u1GYZHLW5UEzwOEumehJeB4EAJdJ3zybNTrGcSepVErIc1XmML8vZdJt2rLp7gbJWIk33kRwepTkYqYlPEvnwYOouR-myKlFcLlRvKiRFNUAkeKHr-fawfC9Q4-A.DJI1lg.gTTZ5CnOXOokNA32I021cxkx_DA
解析:{u'csrf_token': '1b5037f10f247e0f8076145220db705b0baaaac5', u'_flashes': [('info', 'Please login to access this page.')]}
可以看到,比上一次多了个csrf_token信息,这个是用来登录校验使用的
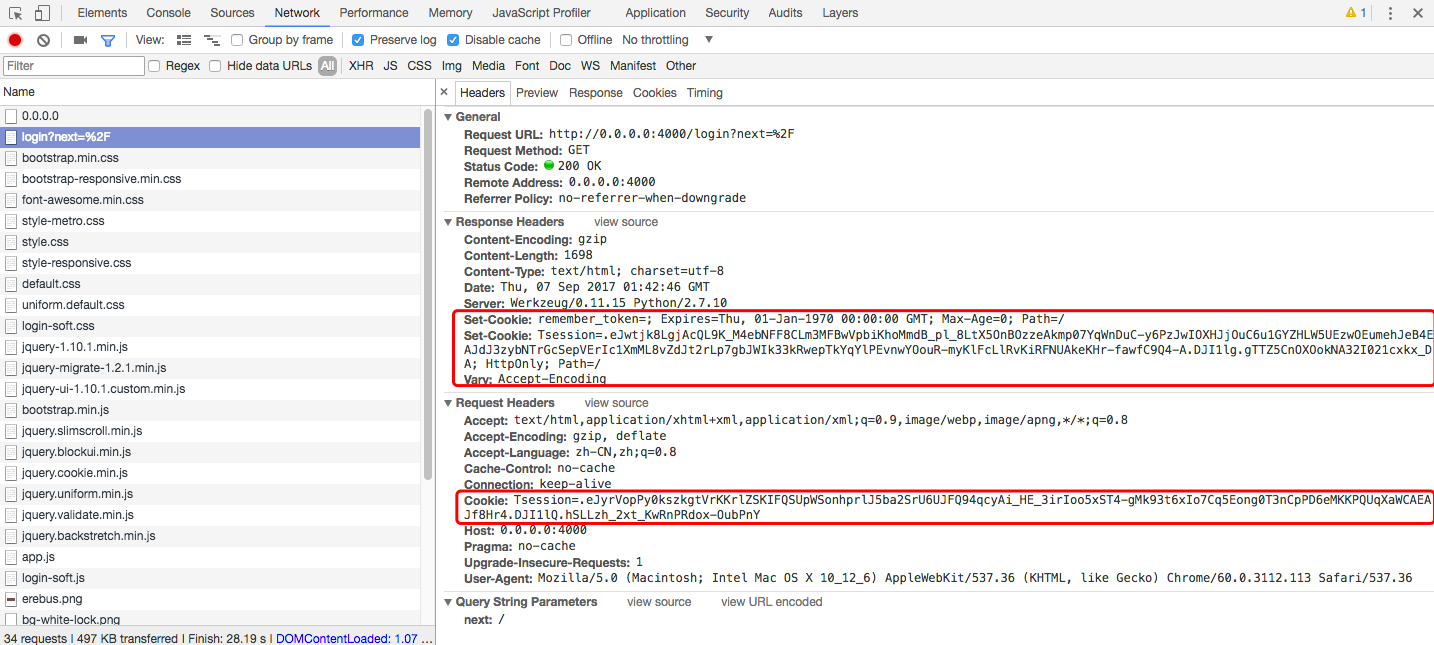
token处理过程如下:
#!/usr/bin/env python # -*- coding: utf-8 -*- from itsdangerous import URLSafeTimedSerializer,base64_decode,base64_encode from flask.sessions import TaggedJSONSerializer import hashlib s=URLSafeTimedSerializer('some_random_key','wtf-csrf-token') token='IjY2NDg0MThjZDI3ZTMxOWNhZmExOGI1Y2E5OTI5NDYzOTM1YThkYjAi.DJO3Cw.D4WB4eYBUB6LOcZxY_tur12Ay0Q' a = s.loads(token,max_age=3600) print '破解:', a
print '*'*100
token ='6648418cd27e319cafa18b5ca9929463935a8db0'
token_jiami=s.dumps(token) print '仿造token: ',token_jiami
print '#'*100 base='127.0.0.1|Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/60.0.3112.113 Safari/537.36' h=hashlib.sha512() h.update(base.encode('utf8')) print '设备指纹:',h.hexdigest()
session['_id'] = _create_identifier():使用hashlib.sha512对客户端的IP|User-agent进行hash,作为访问者设备指纹




