SGX KMRA
Key Management Reference Application (KMRA)
Intel® Software Guard Extensions (Intel® SGX) - NGINX Private Key on 3rd Generation Intel® Xeon® Scalable Processor (pdf)
Intel® Security Libraries for Data Center (Intel® SecL-DC)
Intel® Security Libraries for Datacenter Current Release
The very first place to study Intel SGX. (推荐)
Secure Programming with Intel SGX and Novel Applications pdf
Quoting
现在的英特尔CPU不能在硬件层面实现如此复杂的用于数字签名的密码原语。于是,英特尔采用了软件的方式来实现。但是普通的软件有被黑的可能,于是就有了Quoting Enclave (QE),顾名思义它是一个特殊的enclave程序,它能够安全地执行“数字签名”的逻辑计算,目的是用于remote attestation的数字前面。
用户不能获取enclave SGX CPU的密钥。
QE 验证 application enclave 采用MAC。 密钥就是CPU的密钥吗?
如果Application是被黑客篡改的,会有什么问题? 那他发给application enclave 也就是不可信,发给QE的也不可信。
引用是修辞手法的一种,援用名人的话,或名人的事、物、诗文、典故、寓言、成语、俗语、格言、谚语等,来支持作者的立场,以达到证明和加强自己所说的理论,让文章的内容更为充实
这我们这里面,通过 引用enclave 来证明 application enclave的真实性。
KMRA
Enclave Attestation using KMRA Key Server
The following list provides a detailed key flow sequence:
• Client generates RSA key pair (rsa_pub, rsa_priv) out-of-band on service node (key server).
• Client generates customer public/private key pair (cust_pub/cust_priv) as a session object on the compute node. An attestation quote sgx_quote_t is generated using Crypto API Toolkit for Intel SGX and attests the hash of cust_pub and the enclave. Client sends REST API request containing a (cust_pub) to AppHSM to trigger the Intel SGX quote verification library.
• The quote provides proof to the service node that the client’s enclave is running with Intel SGX protections on a trusted Intel SGX-enabled platform, with a valid TCB. If quote is correct, the hash of cust_pub is verified with sgx_quote_t, cust_pub is imported into the HSM as a session object, and a symmetric wrapping key (aes_swk) is generated as a session object. 在serivce node上,证明引用的有效性,并产生一个wrapping的对称key。
• AppHSM creates wrapped_priv_key by wrapping RSA private key (rsa_priv) with SWK (aes_swk) using CKM_AES_KEY_WRAP_PAD. AppHSM also creates wrapped_swk by wrapping SWK (aes_swk) with the imported customer public key (cust_pub) using RSA OAEP. Wrapped keys wrapped_priv_key and wrapped_swk are returned to the client on the compute node. 在serivce node上,会用对称key加密RSA private key。而对称key会被用户的public 加密。 RSA private key 和 对称key 都会返回给计算节点上的client。
• Client unwraps keys into Crypto API Toolkit for Intel SGX using cust_priv secured in the enclave. Cust_pub and cust_priv are destroyed after unwrapping when the session ends. OpenSSL on the client node is configured to retrieve protected key using Libp11 engine and provide it to NGINX workload.
SGX for NGINX
Intel® Software Guard Extensions (Intel® SGX) asymmetric key capability with a hardware security model (HSM) on a centralized key server
The goal of this document is to outline the steps to set up an NGINX workload to access the private key in an Intel® SGX enclave on a 3rd Generation Intel® Xeon® Scalable processor, using the Public-Key Cryptography Standard (PKCS) #11 interface and OpenSSL
密钥管理参考应用程序 (KMRA) 是一种概念验证软件,旨在展示英特尔® Software Guard Extensions(英特尔® SGX)非对称密钥功能与集中式密钥服务器上的硬件安全模型 (HSM) 的集成.
本文档目的是概述使用公钥加密标准 (PKCS) #11 设置 NGINX 工作负载以访问第三代英特尔® 至强® 可扩展处理器上英特尔® SGX 飞地中的私钥的步骤接口和 OpenSSL.
The Crypto API Toolkit for Intel® Software Guard Extensions (Crypto API Toolkit for Intel® SGX) is an SDK for using the cryptographic capabilities within an Intel SGX. It aims to enhance the security of ISVs’ and OEMs’ data protection applications by exposing enhanced and optimized interfaces that run the cryptographic operations more securely within Intel SGX. The operations are exposed and supported via the PKCS#11 interface for Linux. This universal interface helps security applications to access and work with the key servers and HSM. In this case, the PKCS#11 interface is used by the NGINX application to access keys in the Crypto API Toolkit for Intel SGX enclave.
英特尔® Software Guard Extensions 加密 API 工具包(英特尔® SGX 加密 API 工具包)是一个 SDK,用于在英特尔 SGX 中使用加密功能。它旨在通过公开增强和优化的接口来增强 ISV 和 OEM 数据保护应用程序的安全性,从而在英特尔 SGX 中更安全地运行加密操作。这些操作通过 Linux 的 PKCS#11 接口公开和支持。这个通用接口有助于安全应用程序访问和使用密钥服务器和 HSM。在这种情况下,NGINX 应用程序使用 PKCS#11 接口来访问 Intel SGX enclave 的 Crypto API 工具包中的密钥。
RSA keypairs can be generated into tokens where each token is stored in an Intel SGX enclave. The private key object can only be used to perform cryptographic operations with the correct credentials, without leaving the Intel SGX enclave. This provides more security to the private key and prevents it from being exposed and compromised.
RSA 密钥对可以生成为令牌,其中每个令牌都存储在英特尔 SGX 飞地中。私钥对象只能用于使用正确的凭据执行加密操作,而无需离开英特尔 SGX 飞地。这为私钥提供了更高的安全性,并防止它被暴露和泄露。
Quote generation and verification libraries from Intel® Software Guard Extensions Data Center Attestation Primitives (Intel® SGX DCAP) are used to attest an Intel SGX platform. The KMRA client generates an Intel SGX quote using the Crypto API Toolkit for Intel SGX. The KMRA server verifies the quote before wrapping and extracting the encrypted keys from the HSM for use inside the compute server’s Intel SGX enclave.
来自英特尔® Software Guard Extensions Data Center Attestation Primitives(英特尔® SGX DCAP)的Quote生成和验证库用于证明英特尔 SGX 平台。 KMRA 客户端使用适用于英特尔 SGX 的 Crypto API 工具包生成英特尔 SGX Quote。 KMRA 服务器在包装和从 HSM 提取加密密钥以在计算服务器的英特尔 SGX 飞地内使用之前验证报价。
This document details the setup of each component, such as Intel SGX, NGINX, Crypto API Toolkit for Intel SGX, PKCS#11 engine, and OpenSSL. Each section contains the necessary commands and instructions to configure and install the component using Ansible scripts. Reference documents and links to source code are provided for more information outside the scope of this document.
本文档详细介绍了每个组件的设置,例如 Intel SGX、NGINX、Intel SGX 的 Crypto API Toolkit、PKCS#11 引擎和 OpenSSL。每个部分都包含使用 Ansible 脚本配置和安装组件所需的命令和说明。提供了参考文档和源代码链接以获取本文档范围之外的更多信息。
This document is targeted at development engineers, validation teams, benchmarking teams, and application engineers who are interested in configuring NGINX on a platform to use Intel® SGX enclaves to help secure the private key.
本文档面向有兴趣在平台上配置 NGINX 以使用英特尔® SGX 飞地来帮助保护私钥的开发工程师、验证团队、基准测试团队和应用工程师。
This document is part of the Network Transformation Experience Kit, which is available at https://networkbuilders.intel.com/network-technologies/network-transformation-expkits.
本文档是网络转型体验工具包的一部分,可从 https://networkbuilders.intel.com/network-technologies/network-transformation-expkits 获取。
REF:
Terminology
Quote verification library (QVL)
Provisioning Certificate Cashing Service (PCCS)
Platform Certification Key (PCK)
Provisioning Certification Service (PCS)
PKCS #11 is one of the Public-Key Cryptography Standards
Crypto API Toolkit for Intel(R) SGX (CTK)
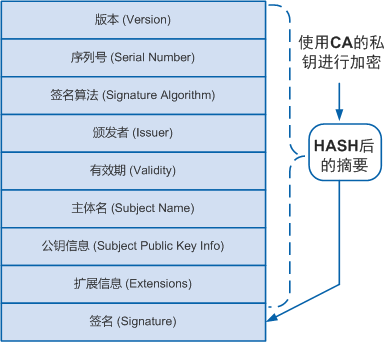
数字证书叫做「公钥的数字签名」
引入证书机构后,我们使用证书机构而不是证书拥有者的私钥来对数字证书进行签名。数字证书原理
假设Alice要发送一个电子商务合同给Bob,为了向Bob表明合同是Alice发送的,Alice使用自己的证书对该合同进行数字签名后再发送,证书的签发、使用和验证过程是这样的:
2. Alice使用该CSR向证书机构发起数字证书申请。 2. 证书机构验证Alice的身份后,使用CSR中的信息生成数字证书,并使用自己的CA根证书对应的私钥对该证书签名。
3. Alice使用自己的Private Key对合同进行签名,然后将签名后的合同和自己的证书一起并发送给Bob。
4. Bob使用操作系统中自带的证书机构根证书中的公钥来验证Alice证书中的签名,以确认Alice的身份和公钥。
5. Alice的证书验证成功后,Bob使用Alice证书中的公钥来验证合同中数字签名。
6. 合同数字签名通过验证,可以证明该合同为Alice本人发送,并且中间未被第三方篡改过。


 浙公网安备 33010602011771号
浙公网安备 33010602011771号