intel DCAP
Intel® Software Guard Extensions (Intel® SGX) Services (DCAP/EPID)
基于英特尔® SGX DCAP 的鉴证
An update on 3rd Party Attestation
大型企业和服务提供商希望建立自己的认证能力。
DCAP需要一项Flexible Launch Control的功能,该功能允许平台所有者(而不是英特尔)控制启动哪些enclave, 需要在BIOS中启动。
这包括授予哪些区域访问与证书检索服务一起使用的平台配置标识符(PPID)的权限。 请求访问PPID的区域可以由attestation服务提供商签名。 Launch Enclave的目的之一是防止在隐私敏感的环境中滥用PPID。
构建证明服务需要与操作系统集成,并且我们正在与Linux Kernel社区合作,以尽快将其更新。 请注意,您不需要构建自己的Quoting Enclave。
Product brief Intel®SGX Data Center Attestation Primitives (Intel®SGX DCAP)
intel-sgx-support-for-third-party-attestation
SGX 拥有远程和封印的能力,这可以用来provision 和 secure secrets. SGX 是指令集的扩展,用来再程序中建立一个可信的执行环境enclave。
enclave 创建不需要secrets. enclave实例化之后,可以再deliver secrets.
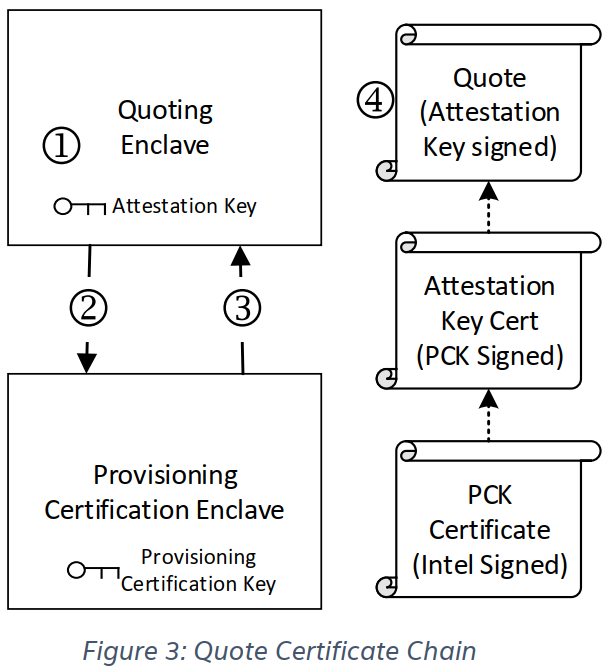
该流程,跟CA的流程类似, Intel相当于根CA,会给PCK证书签名, PCK相当于二级代理, 给其他证明证书签名。
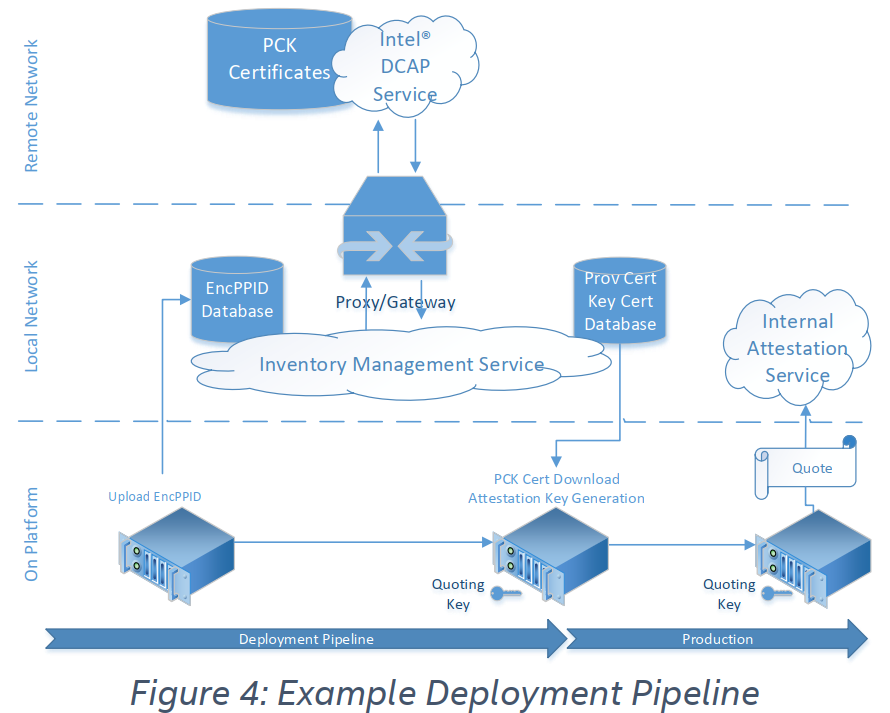
5. example attestation infrastructures for Data Center or Cloud Deployments
5. 数据中心或云部署的示例证明基础架构
This chapter describes an example deployment flow for a Cloud Service Provider(CSP) to host an Attestation Service capable of verifying Quotes created by their platforms without an "runtime" connectivity to Intel SGX DCAP or other services. This flow, shown in Figure 4, combines collection of PPIDs, creation of Attestation keys, retrieving certificates/TCB information, and attestation verification.
本章介绍了云服务提供商(CSP)托管证明服务的示例部署流程,该服务能够验证其平台创建的Quotes,而无需与英特尔SGX DCAP或其他服务进行“运行时”连接。如图4所示,该流程结合了PPID(Platform provision ID)的收集,证明密钥的创建,检索证书/ TCB信息以及证明验证。
5.1 Identifying Platforms
5.1 识别平台
During the deployment phase when the new platform is prepped, tested, and initial software loaded, the platform registers itself with the CSP's infrastructure.
The Quoting Enclave retrieves the encrypted PPID from the PCE, A software agent delivers the PPID, CPUSVNs and PCEID to a CSP-owned Inventory Management Service (IMS). The IMS can be a self-sufficient service or just a logical set of functions and databases that are part of larger, possibly pre-existing infrastructure. The IMS's role is track Intel SGX attestation identities and retrieve PCK certificates for the Attestation Service.
The Encrypted PPID is provided to the IMS to enable the service to identify the platform when requesting PCK certificates from intel. This only has to be collected once during deployment since the PPID remains constant for the lifetime of the platform.
Once registered, the platform then continues through deployment process.
在部署阶段,准备,测试新平台并加载初始软件时,该平台会在CSP的基础架构中注册自己。
Quoting Enclave 从PCE检索加密的PPID,软件代理将PPID,CPUSVN和PCEID传递给CSP拥有的库存管理服务(IMS)。 IMS可以是自给自足的服务,也可以只是功能和数据库的逻辑集,而功能和数据库则是较大的,可能预先存在的基础结构的一部分。 IMS的角色是跟踪英特尔SGX证明身份并为证明服务检索PCK证书。
加密的PPID提供给IMS,以使服务能够在从英特尔请求PCK证书时识别平台。由于PPID在平台的生命周期内保持不变,因此在部署过程中只需收集一次。
注册后,平台将继续进行部署过程。
5.2 Acquiring PCK Certificates
5.2取得PCK证书
While the platform continues through deployment process, the Inventory Management Service uses an Internet gateway to the Intel DCAP services and requests the PCK certificates for each CSP-owned platform using the interface that retrieves both current and historic certificates for each platform. This provides the Attestation Service with multiple certificates for different TCBs, providing the greatest chance that the service will have an appropriate PCK certificate for whatever attestation software their customer installs in their environment.
在平台继续进行部署过程的同时,库存管理服务使用Internet网关访问Intel DCAP服务,并使用接口检索每个平台的当前和历史证书,为每个CSP拥有的平台请求PCK证书。这为证明服务提供了针对不同TCB(Trusted Computing Base)的多个证书,从而为客户在其环境中安装的任何证明软件提供了最大的机会,使该服务具有适当的PCK证书。
5.3 Certifying Attestation Keys
5.3认证密钥
To ensure that PCE certifies the new Attestation Key with a PCK for which a certificate exists, it's recommended that before generating the attestation key, a software agent download the PCK certificate from the Inventory Management Service. The PCK certificate contains the CPUSVN value that corresponds to that PCK. After generating the Attestation key, the Quoting Enclave can specify this value when requesting the PCE to certify the Attestation public key.
为确保PCE用已存在证书的PCK认证新的证明密钥,建议在生成证明密钥之前,软件代理从库存管理服务下载PCK证书。 PCK证书包含与该PCK对应的CPUSVN值。生成证明密钥后, Quoting Enclave可以在请求PCE认证证明公钥时指定此值。
5.4 TCB Recovery
5.4 TCB恢复
After an Intel SGX TCB element is updated, the process for establishing a new attestation key depends on what type of element was updated.
if a Quoting Enclave was updated, the QE can simply be upgraded and a new attestation key can be generated and certified as described in Section 3.1.2.2. This may not require interaction with the attestation infrastructure.
if a CPU-related component, such as microcode updates or the PCE was updated, a new PCK is required for the PCE. When this occurs, in addition to the QE generating a new attestation key, the infrastructure must also acquire new PCK certificates, CRLs and TCB Info structures.
The CSP Inventory Service requests updated certificates for all CSP-owned platforms affected. If the inventory service maintains a database of encrypted PPIDs and model information for the CSP's platforms, it will have all the information necessary to request new certificates without any interaction with the platforms.
CSPs may choose to continue to use the previous Attestation Keys until all platforms are upgraded and all certificates are downloaded and provided to the CSP Attestation Service. This ensures that the Attestation Services will always have the material needed to verify a Quote and will never need to contact external services in real-time.
更新Intel SGX TCB元素后,建立新证明密钥的过程取决于更新的元素类型。
如果更新了Quoting Enclave,则可以轻松升级QE,并可以生成新的证明密钥,并按照第3.1.2.2节中的说明进行认证。这可能不需要与证明基础结构进行交互。
如果与CPU相关的组件(例如微代码更新或PCE已更新),则PCE需要新的PCK。发生这种情况时,除了QE会生成新的证明密钥外,基础架构还必须获取新的PCK证书,CRL和TCB Info结构。
CSP清单服务为受影响的所有CSP拥有的平台请求更新的证书。如果清单服务维护了用于CSP平台的加密PPID和模型信息的数据库,则它将具有请求新证书所需的所有信息,而无需与平台进行任何交互。
CSP可以选择继续使用以前的证明密钥,直到升级所有平台并下载所有证书并将其提供给CSP证明服务为止。这样可以确保证明服务始终具有核实报价所需的材料,并且永远不需要实时联系外部服务。
K8s support
目前demo提供的是DCAP
terminology
Attenstation 展示一个可执行的软件在一个平台上被正确实例化的过程。


