picoCTF login/logon 题解
login
尝试admin admin弱口令,提示Incorrect Password
输入其他用户名,提示Incorrect Username
尝试使用admin用户名,对密码进行爆破
启动burpsuite
发现抓不到包
密码信息可能保存在前端,分析js文件:
(async()=>{await new Promise((e=>window.addEventListener("load",e))),document.querySelector("form").addEventListener("submit",(e=>{e.preventDefault();const r={u:"input[name=username]",p:"input[name=password]"},t={};for(const e in r)t[e]=btoa(document.querySelector(r[e]).value).replace(/=/g,"");return"YWRtaW4"!==t.u?alert("Incorrect Username"):"cGljb0NURns1M3J2M3JfNTNydjNyXzUzcnYzcl81M3J2M3JfNTNydjNyfQ"!==t.p?alert("Incorrect Password"):void alert(`Correct Password! Your flag is ${atob(t.p)}.`)}))})();
发现base64编码:
cGljb0NURns1M3J2M3JfNTNydjNyXzUzcnYzcl81M3J2M3JfNTNydjNyfQ
解一下,居然直接得到了flag:
picoCTF{53rv3r_53rv3r_53rv3r_53rv3r_53rv3r}
呃...
这是我第一次写博客,不到一小时前刚过得博客申请.有点激动,就迫不及待地把手头正在玩的picoCTF随便找了一题发上来了.
技术含量挺低的,请大家包含.
趁热打铁写个logon
logon
这关就要用burpsuite了
打这关的时候参考/学习了:
https://blog.csdn.net/cyjmosthandsome/article/details/103067640----题解
https://www.cnblogs.com/wuguanglin/p/redirect.html--------------------重定向详解
使用burpsuite抓包,抓到四个:
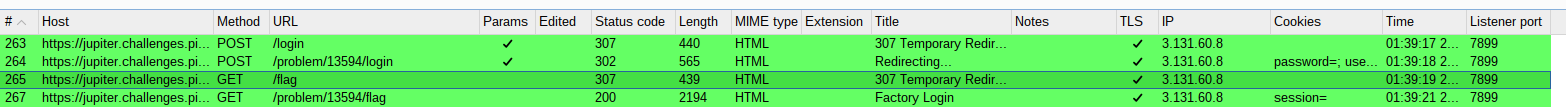
若修改前三个30x包进行发送只会显示30x的页面
所以选择最后一个200包进行修改:
Cookie: cf_clearance=EVk05gJpiBpxA2Z0aqDbgP8fbtCvqsILirklP9V_fec-1706376838-1-AUuTBtE6BaPbSs6yVG+fEyM+Nnlv0hjiiILQYD56xBl0kOGqNWq6LQN4dxVR2ySqQBsDUgglL3iyrLHg+Aq9Fh4=; _ga=GA1.2.1677435870.1706030628; _ga_L6FT52K063=GS1.2.1706374718.8.1.1706376838.0.0.0; _gid=GA1.2.1186233569.1706199335; _ga_BSZFGM3NWK=GS1.1.1706374701.1.1.1706374716.0.0.0; __cf_bm=EOotTuBYeXy.VXrzvznKOrRF7ydDc3ydJzxLkmQjKjc-1706377081-1-AVYbG1klNiTytqbNAFv/5J7ir/OGr+sx887Ix4tfkUfbYC05xbh1VOPXavq86vuCqknPe6+BR6/7JG+ghgtS2sk=; password=; username=114514; admin=False
查看cookie,admin=False有点可疑,改称True后send
成功拿到flag
本文作者:sesmof
本文链接:https://www.cnblogs.com/sesmof/p/17992374
版权声明:本作品采用知识共享署名-非商业性使用-禁止演绎 2.5 中国大陆许可协议进行许可。


 密码信息可能保存在前端,分析js文件:
密码信息可能保存在前端,分析js文件:



【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步