RSA解密(CTF)
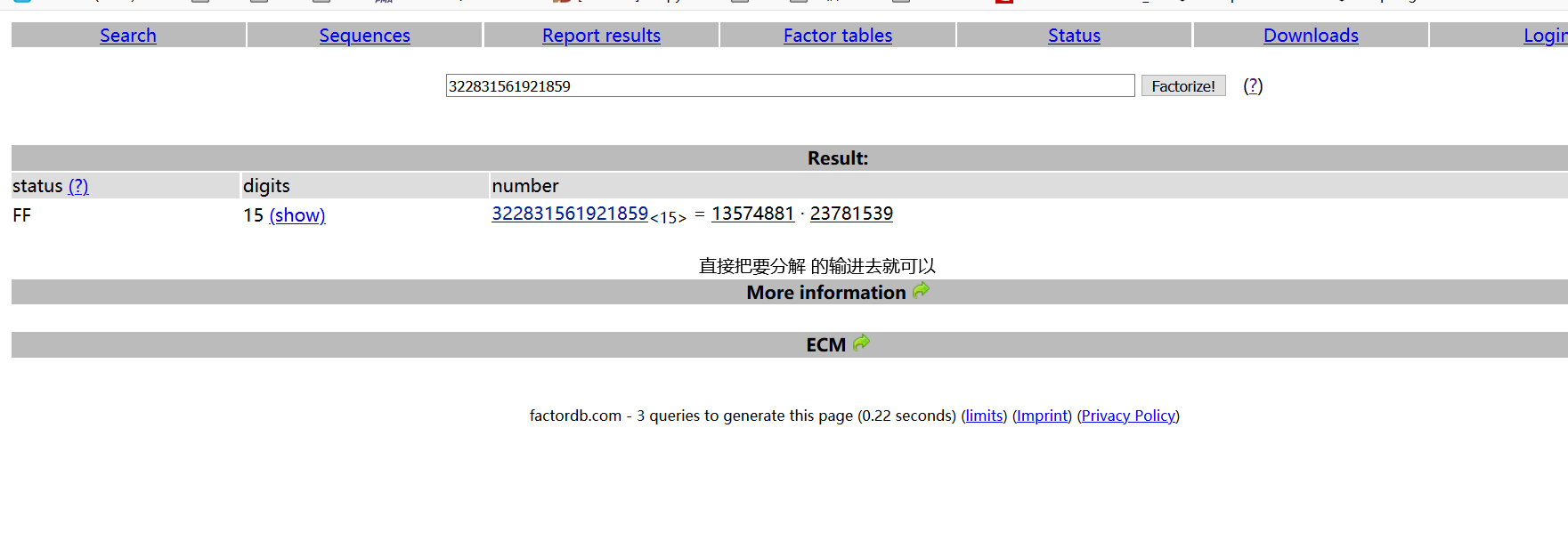
http://www.factordb.com/
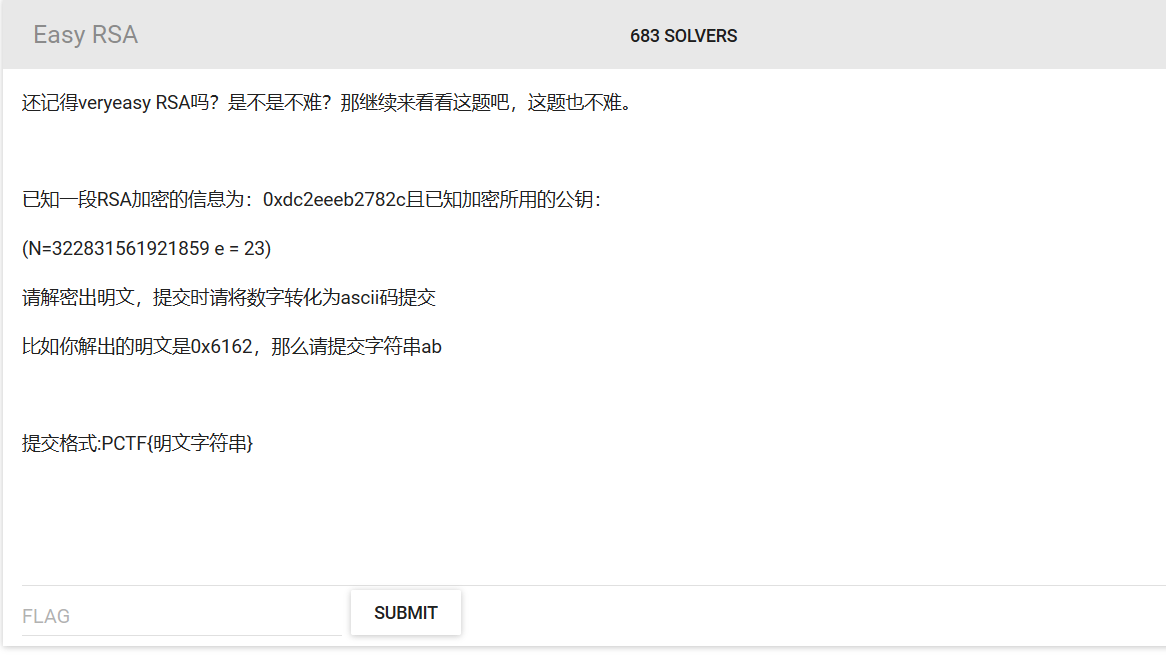
求解D:
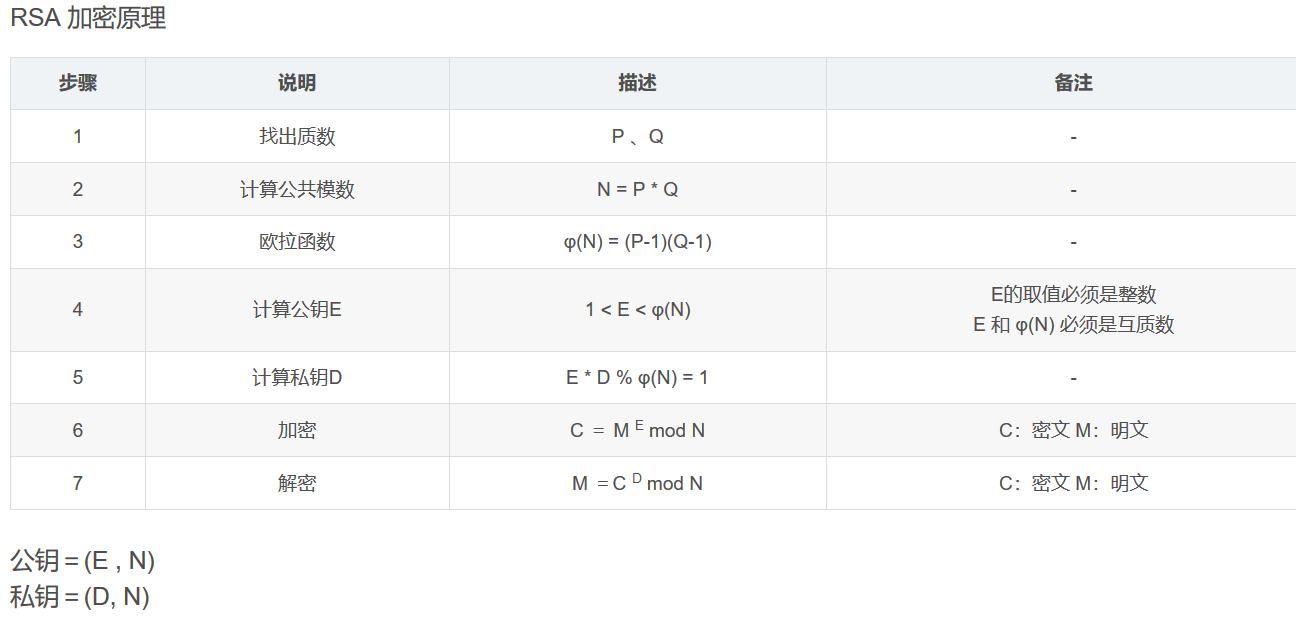
解密脚本
# N = 322831561921859
# e = 23
# N = P*Q
# φ(N) = (P-1)(Q-1)
# M =C的D次方 mod N
# C = 0xdc2eeeb2782c
import gmpy2
P = 13574881
Q = 23781539
e = 23
C = 0xdc2eeeb2782c
N = 322831561921859
# invert是求乘法逆元
D = gmpy2.invert(e,(P-1)*(Q-1))
print (hex(pow(C,D,N)))


 posted on
posted on

